You can add USB ports to your PS3 at home. Put two new ports onto the back of your PS3 for a total of six ports to get even more out of your machine. You will need a basic knowledge of circuitry and some electrician equipment to do this the right way. This video will show you how to add USB ports to your PS3. Keep in mind that this video does not show you how to reassemble it so be sure to keep track of your work.

Southwest Yard and Garden teaches viewers how to prepare garden soil for planting. You can use compost to work this into your soil. You can make your own compost and you can also buy compost. First, you can use a flat bladed spade or a sharp shooter spade to double dig your garden soil. First, you should dig double deep into the soil and turn the soil to the side. What you want to do is dig a trench. Go back to the beginning of the trench and dig a second depth. You will want to get below the...

This video on typhoon preparedness comes from Andersen Air Force Base in Guam, where typhoons are common. The key to surviving a typhoon or other disaster is preparation. Stock up on enough food and supplies to last your family for about a week. Routinely check expiration dates on food, water and batteries and rotate your stock. Be sure window screens are in place and in good condition in the event the power is off for several days.

Master Gardener Rosamarie Maddox asks John White, Doña Ana County Extension Agent, about problems facing her pecans, grapevines, and native shrubs. An unidentified insect found on her pecan tree is identified by John White as a Twice Stabbed Ladybug. This ladybug is a useful insect that often over-winters on the tree and helps takes care of the aphid problems faced by pecans. Pink fuzzy coating on pecan nuts is also brought up. The coating is normal for pecan and contains bitter tannin. Too m...

Blue corn is a special variety of corn which can be differentiated by the majority of the corn species by looking at the unusual top growth of the corn. It is a hybrid and grows very uniformly throughout. Now take a corn from the field and peel it off. You shall notice that it has a blue color corns. Blue color corns are hard from outside but they are very soft and tender in the middle. You can use these blue corns in making commercial products like blue corn chips, tortillas, and atole ’,‘ c...

This video tutorial demonstrates tips for how to organize your home office when you are visually impaired. Here a rehabilitation specialist is helping a visually impaired person. The person who is visually impaired should know what is visually important to him/her. Mostly these people obviously need to know where every thing is because they don’t have their eyes to depend anymore. Here visually impaired person is 66 year old Deanne Jackson. She has wet macular degeneration. In order to set up...

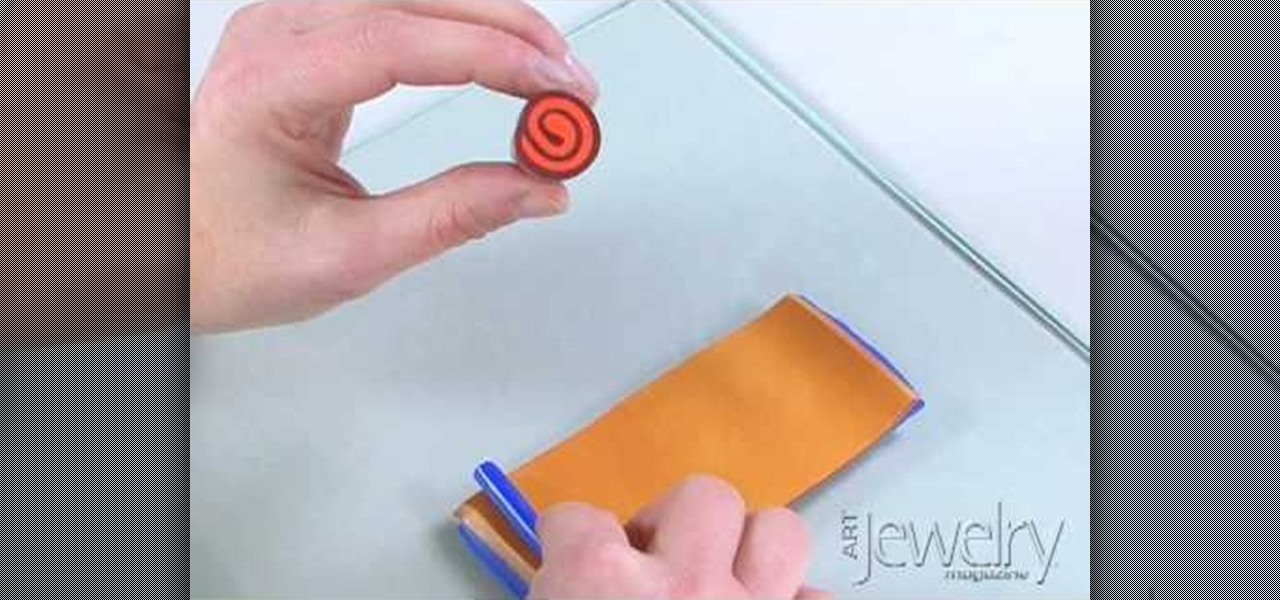
Jill Erickson from Art Jewelry Magazine demonstrates how to make a Jellyroll cane with polymer clay. Condition two different colors of clay by running them through a pasta machine set on medium. Then, trim off any rough edges. Stack the clay on top of each other and place a little bit of pressure on it to confirm the two layers. Using a blade slightly bevel the edges. Slide the blade underneath the two layers of clay for easier handling. Place a think snake of clay in the contrasting color on...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.

It's no secret that Google is all about AI. In their eyes, machine learning is the future of software development, and you can see evidence of this all over the last couple Android updates. They've used it to power all sorts of features in their Pixel phones, and they've even donated some of their AI smarts to AOSP for all Android manufacturers to share. But it looks like Samsung isn't exactly on board.

Every step in the evolution of computing brings an in-kind leap forward in user input technology. The personal computer had the mouse, touchscreens made smartphones mainstream consumer devices, and AR headsets like the HoloLens and the Magic Leap One have leveraged gesture recognition.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Now that its first developer conference is in the rearview mirror, Magic Leap continues to nurture its content development community, this time with an assist from strategic investor and retail partner AT&T.

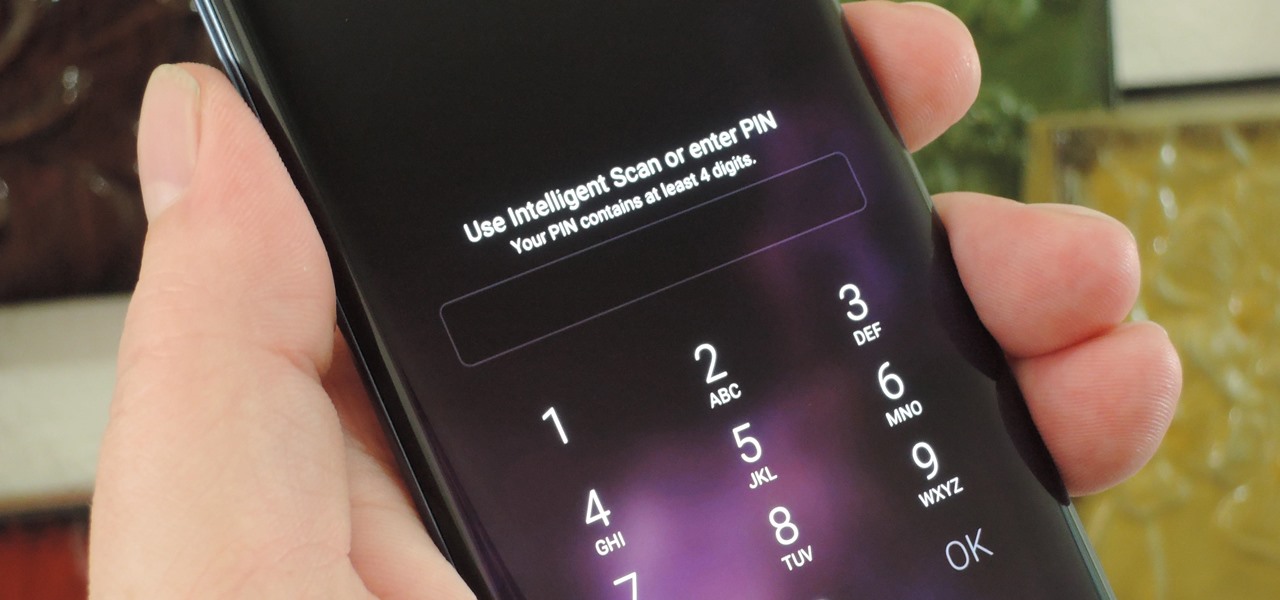
The Galaxy S9 is full of minor improvements and revisions that come together to make it a worthy upgrade over the Galaxy S8. One such improvement is facial recognition, which Samsung has fortified with machine learning and the inclusion of another sensor. The result of these efforts is called Intelligent Scan.

Google's new AI-powered camera, Google Clips, seems to be targeted at parents of young children in its current form, but the idea itself has unique potential. Just set it up somewhere, then you'll never miss a moment trying to capture the moment — you'll have a robot photographer taking care of that stuff for you.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

Tesla hopes high-level personnel changes will help it gain an edge in neural network knowhow for its models' self-drive features, following the replacement of its Autopilot chief and the appointment of a recent Stanford grad to head its AI and Autopilot vision research.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

The largest and arguably most widely known event of its type, especially in the US, the Sundance Film Festival is an annual celebration of independent film—ones made outside the Hollywood system. This year, a new type of experience appeared at the Sundance Film Festival in an installation called "The Journey to the Center of the Natural Machine." This mixed reality presentation offered the user the newest type of storytelling in a long and important line—continuation of the species kind of im...

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Whether it's the start, middle, or end of summer, it's prime-time grilling season. If you find yourself without a grill, however, it may seem as if half your summer plans of swimming by the pool while stuffing hot dogs in your face could be ruined.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Watch this instructional knitting video to hang a cast on comb on a knitting machine. Watch this video a few times to master this little trick. You may want to reference some written knitting instructions in addition to following these visual guidelines.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. Use a three prong tool to twist a stitch. Once you set the twist, you can knit an entire stretch of fabric with an elegant twisted stitch pattern. This creates a light knit with open spaces for a warm yet breathable garment.

If you use a knitting machine to knit your projects, follow this simple example to knit ribbing. This instructional knitting video demonstrates how to e-wrap for double bed knitting and transfer the carriage. You may want to reference some written instructions in addition to watching this knitting video. With a little practice, you can make it look as easy as this.

While any form of gambling is set up to make you lose, there are some tips and tricks, shown in this how-to video, to help even the playing field. Penny arcade slots are a reasonable place to start, as the stakes aren't too high, so neither side (you or the arcade) has that much to lose. Watch this video conning tutorial and learn how to beat an arcade penny slot machine.

Watch this video sewing tutorial and learn how to use a ruffler attachment on a sewing machine. Use a ruffler attachment to sew small individually adjustable tucks.

An important part of sewing involves knowing how to make button holes. This sewing how-to video demonstrates how to cut a button hole and insert a button footer on a vintage Kenmore sewing machine. Watch and learn how easy it is use a Kenmore sewing machine to make button holes.

This video tutorial shows how to use the Cuttlebug paper embosser. Learn how to make embossed designs in paper projects with a Cuttlebug paper embossing machine.

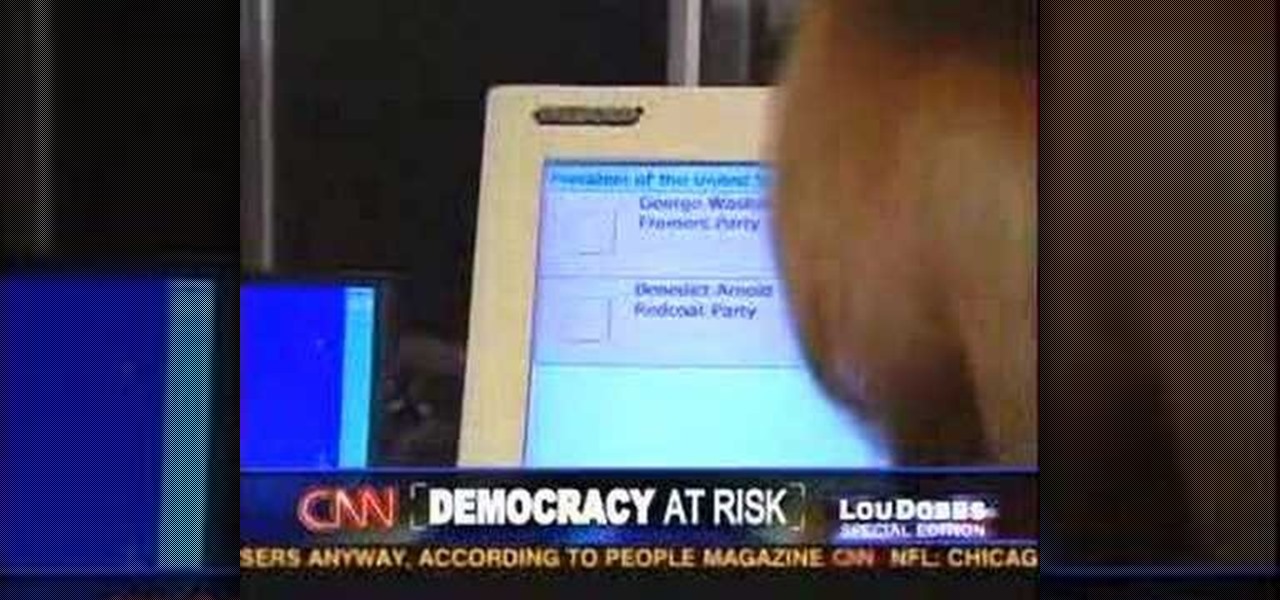
It only takes a minute to steal a U.S. Election!

Learn how to use the Miller Concrete Landscape Curbing Machine. You will also learn the basics of making curbing mix.

You can learn how to use the stock market as your own ATM machine. You can make 500 dollars in less than 15 minutes. Then you can take that 500 dollars and use it to get professional advice.