See how to vote in York County in PA by watching this video tutorial. With the new touchscreen electronic voting machines in Pennsylvania, you'll need to check out this video to make sure your ballot gets counted. So, if you want to get out this year and vote for Hillary or Obama, then make sure you do it right, don't screw up! This video is a must for you old folks with no computers skills at all, so get up to date and vote electronically in your county election.

In order to make a large hair bow, you will need the following: a headband, fabric, thread, scissors, thread, and a needle.

The most used and most washed articles of clothing are undergarments. Underwear, specifically bras and panties, are in desperate need of attention after each and every use. They're not like a pair of jeans, wearing them twice in a row is not a good idea, nor clean. Shabby’s not chic when it comes to lingerie. Use a little extra care to keep your lace and silk bras and panties looking good.

Aging paper is a great way incorporate learning about antiquities from the past while doing a fun hands on project in the classroom. It's easy and really adds something special to projects or even to do just for fun in your spare time.
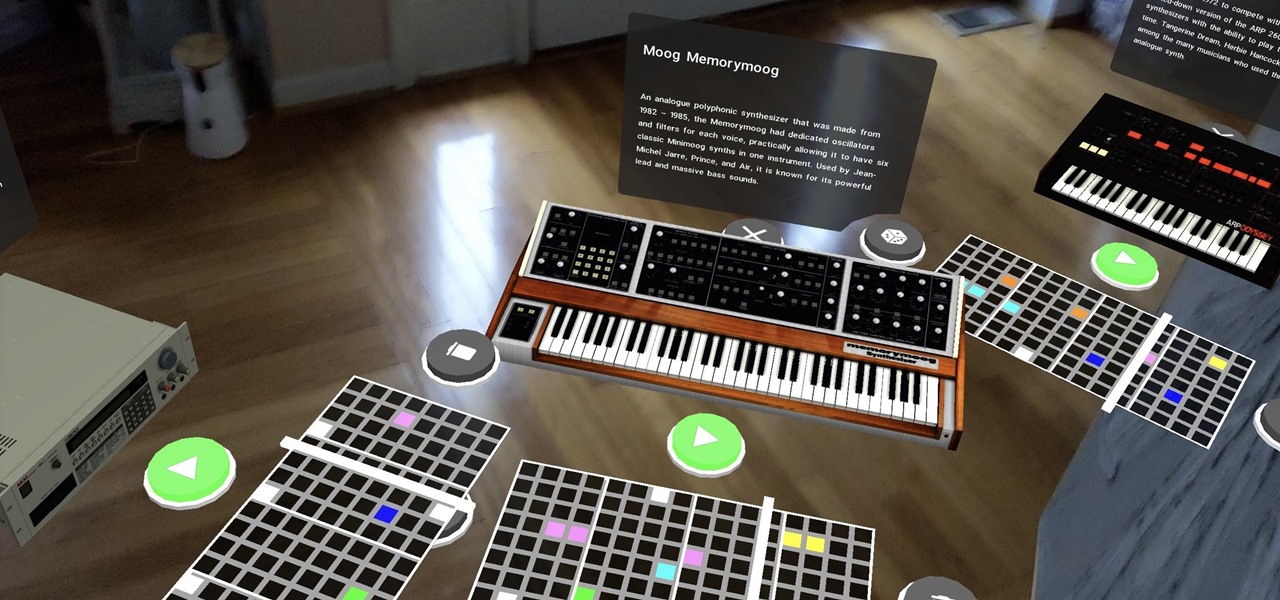
Museum curators typically frown upon visitors touching paintings, sculptures, and artifacts, but not when those exhibits are displayed in augmented reality.

Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

Songs new and old are given a fresh purpose through the TikTok meme machine, but it can be tricky to figure out where a track originally comes from. Sure, you can tap the name of the song to see the source on TikTok, but if it were a snippet uploaded by someone other than the track's creator, the song title likely wouldn't be listed. Luckily, there is an easy way to figure it out.

Less than a month after the worldwide launch of HoloLens 2, call center consultant BellSystem24 has already prepared an augmented reality solution for one of its clients.

After drawing attention from nostalgic Gen Xers for its Motorola Razr reboot with a foldable screen, Lenovo has a new augmented reality smartglasses concept that the company hopes will also turn some heads.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

The marketing team for Marvel Studios is doing "whatever it takes" to make sure you see Avengers: Endgame when it hits theaters in a couple of weeks, including offering an updated set of augmented reality Playmoji for the Playground app on Google Pixel.

Although Apple's Animoji game is strong, as recently exampled by its Ariana Grande collaboration, Google isn't slacking either, unleashing a far more immersive music experience for smartphone users.

Despite the popularity of Pokémon GO, augmented reality gaming hasn't quite caught on yet. The makers of the popular World of Tanks game aren't taking a shot at Niantic's crown yet, but they are looking at giving spectators a new way to watch the game.

Now that the cat's out of the bag, Magic Leap has published videos of a pair of apps that will be available to Magic Leap One early adopters.

With the official launch of Magic Leap One expected by the end of summer (translation: days from now), Magic Leap's hype machine just took a big hit with the sudden loss of a key marketing executive.

Space might be the final frontier, but NASA is making a detour into augmented reality first. The Spacecraft AR app, developed by NASA's Jet Propulsion Laboratory (JPL) in collaboration with Google, debuted exclusively for Android this week (an iOS version is also in the works).

It looks like the Huawei P20 has moved from rumor to all but confirmed. Thanks to a series of YouTube videos released by Huawei Mobile Netherlands, we now have a few confirmations about the latest entries in the flagship series.

Researchers have developed a new method that harnesses the power of augmented reality to detect a patient's heart rate using a Microsoft HoloLens and computer vision.

A very low-key update to the ARCore developer's site has expanded the universe of officially-supported devices for Google's augmented reality toolkit to include the Samsung Galaxy S7, S8+, and Note 8 handsets.

While augmented reality headset makers are faced with tackling numerous challenges before the category is truly ready for prime time, a start-up comprised of former Microsoft engineers may have nailed fast and precise tracking of hand gestures and full-body locomotion.

So you want to do Kendrick Lamar's "HUMBLE." in Animoji Karaoke, but you need the lyrics. Well, now you can see those rhymes spit out in augmented reality.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Do you know when you're going to die? Your iPhone or iPad does. That's the premise behind Death Mask, an experimental app developed by Or Fleisher and Anastasis Germanidis.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Apple has billed ARKit as a means to turn millions of iPhones and iPads into augmented reality devices. The refrain is similar for Kaon Interactive, a developer of product catalog apps for businesses.

Aura, a highly rated app for mindfulness and mental health, just became available on Android and is currently on sale.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

A new feature of Google's Gboard for Android lets users doodle an emoji in order to find it. The change was part of a few updates introduced earlier today.

You would think most people would agree that you shouldn't use your smartphone while driving. Apparently, most people would be liars, according to recent data from the National Safety Council (NSC) and Zendrive.

Dual cameras are increasingly popular right now for smartphones, but so far, Samsung has steered clear of all the hype. However, a new patent application shows that Samsung has been working on a dual camera system of their own, featuring tech potentially more advanced than what is currently on the market.

At the WinHEC Shenzen 2016 Keynote, Microsoft showed off a system running Windows 10 smoothly on an ARM processor. This could be great news for developers of mixed reality software.

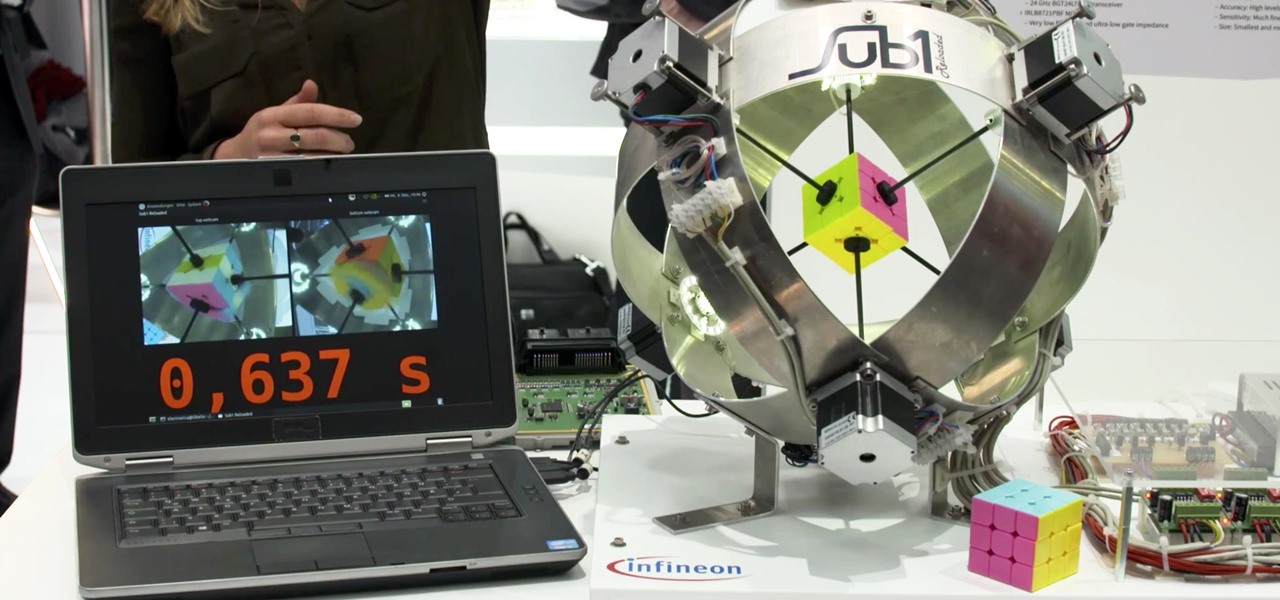
In December of last year, Australian Feliks Zemdegs broke the human world record for solving a Rubik's Cube with a time of 4.737 seconds. Well, this robot did it way, way faster by solving one in under 1 second. Don't tell me a robot takeover isn't real possibility.

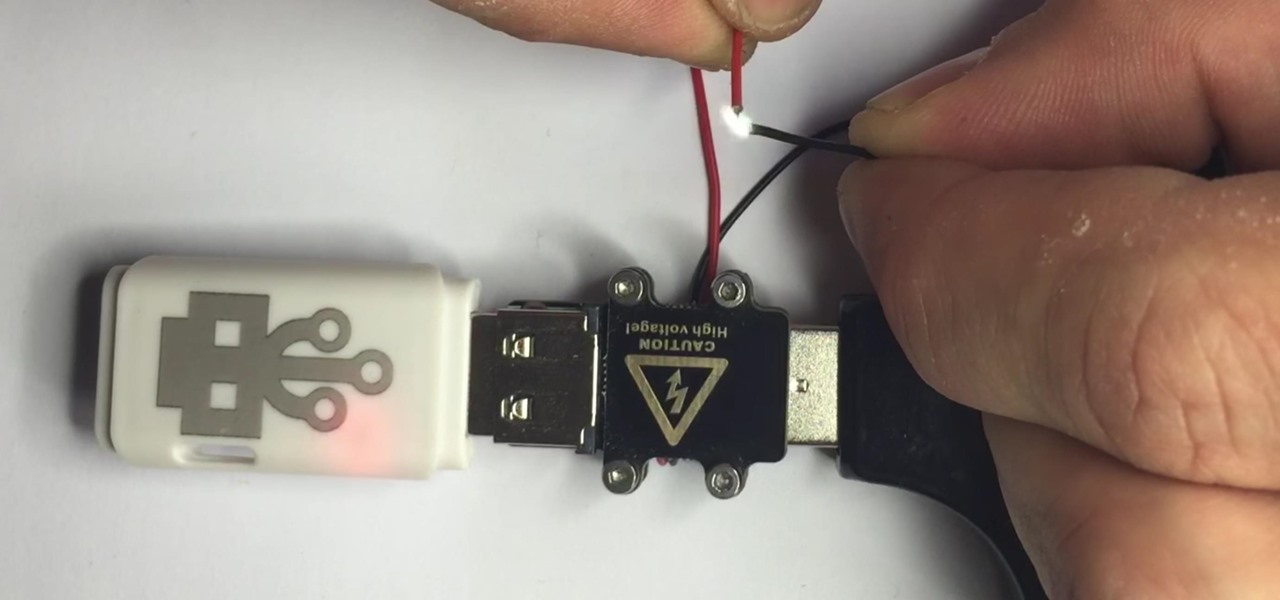
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.

We can't be in two places at once, but with virtual touch interfaces we can theoretically use a machine to act as our second body in a remote location. Over at MIT, Daniel Leithinger and Sean Follmer, with the advisement of Hiroshi Ishii, created an interface that makes this possible.

Augmented reality has a variety of applications, but lately the face has been a major point of concentration for many companies. We're all pretty familiar with face swapping by now, but ModiFace employs similar technologies for more practical purposes.

Facebook announced at its F8 Developer's Conference on April 12th that, in addition to the VR-ready Oculus Rift we have today, it plans to bring Augmented Reality (AR) into the fold of their social machine.

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

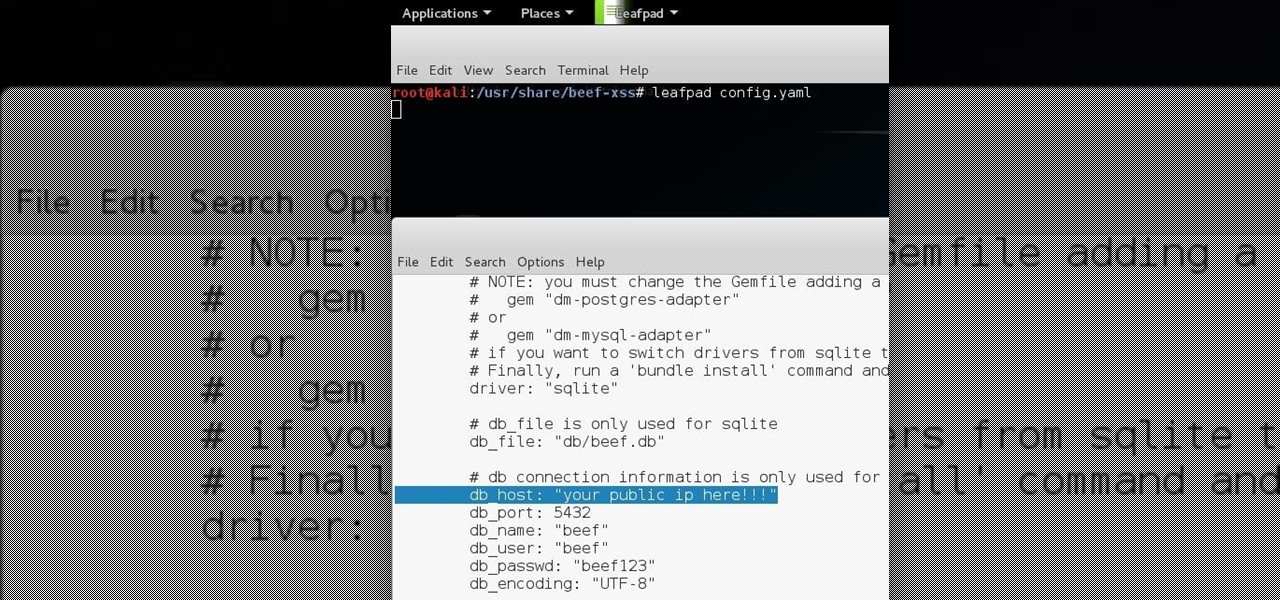
Hello all Just thought id share how ive managed to get beef working over the internet.

The title might not be in harmony with the post, but thinking a good title that perfectly matches your post... isn't that easy. Especially for this post.