An electric mandrel spinner is a tool that grips materials to be spun or machined. Watch this instructional lampworking video to see how molten glass may be shaped with a mandrel spinner. Mandrels are commonly used to shape beads of glass into a desired size and shape for jewelry manufacturing. This video shows you how burnish silver leaf using a lampwork torch and an electric mandrel spinner.

An electric mandrel spinner is a tool that grips materials to be spun or machined. Watch this instructional lampworking video to see how molten glass may be shaped with a mandrel spinner. Mandrels are commonly used to shape beads of glass into a desired size and shape for jewelry manufacturing. The rheostat dial on your power box will control your "set" spinning rate.

General Pipe Cleaners Easy Rooter Junior is the right machine to clear washtubs, small floor drains, roof vents and other medium-size drains. This video will give you a general overview of the operating instructions and safety procedures for the easy Rooter Junior. Take a look.

To calm our 8 week old baby Logan, the hair dryer is the foolproof white noise machine. Baby quiets down instantly. (But if he is hungry, then nothing works but milk.)

This video welding tutorial shows two arc or stick welding machines and explains how to connect the leads and hook it up ready for welding. Those interested in welding for metalwork will learn the proper machinery and equipment needed for welding and how to use the equipment correctly. Watch this instructional video and start welding.

This how to video tutorial demonstrates how to sew a straight stitch by hand, just in case you don't have a sewing machine. The straight stitch is excellent for simple hems, decorative stitching and gathering fabric.

Learn how to make a green, eco-friendly grocery bag. This is a great fashionable way to cut down on paper or plastic bags. All you need is some pretty fabric and a sewing machine. Remember this bag the next time you are going shopping.

In this how to video, Allyce King steps up to the sewing machine to make a quick, stylish bed for pets to coordinate with any decor. Then get some notion know-how. Check out this list of the supplies every creative chick should have in her sewing kit. Watch this how to video and you will be able to sew your pet a bed in no time.

Lawn mowers and lawn tractors are great machines and the latest models have some features worth checking out. New, fancy zero turn mowers, and four wheel steer mowers can make mowing your lawn quicker and easier. Tim Carter of Ask the Builder takes you through some of those new lawn mower features.

Learn Pat's tips for using the 1/4 inch foot on your sewing machine.

This video, by Garden of Imagination, shows you how to make a polymer clay pizza. To begin with, have a small piece of wood to act as a tray for your pizza. Take off-white clay for the crust and warm it up between your hands. Roll it out on your pasta machine on the number one setting. Using a circle cutter, push down on the clay to create a circle. Use an object that is a bit smaller of a circle to create the inside area of the pizza by pushing down. While doing that, blunt the edges of the ...

Learn how to remove red wine stains. Thinking of switching to white wine just to avoid stains? Memorize these cleaning tips instead.

Learn how to do single leg cable curls. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do single-dumbbell front lunge and power row at bottom. Presented by Real Jock Gay Fitness Health & Life.

You won't have to ask Santa for holiday-themed augmented reality experiences, because practically any social and shopping app that offers AR effects has them available now.

Cloud computing has come a long way since the days of simple online storage and server networking. Virtually every major company in the world now relies on complex cloud computing infrastructures to reach customers, innovate products, and streamline communications. Their reliance on advanced cloud computing platforms is only going to grow in the coming years.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

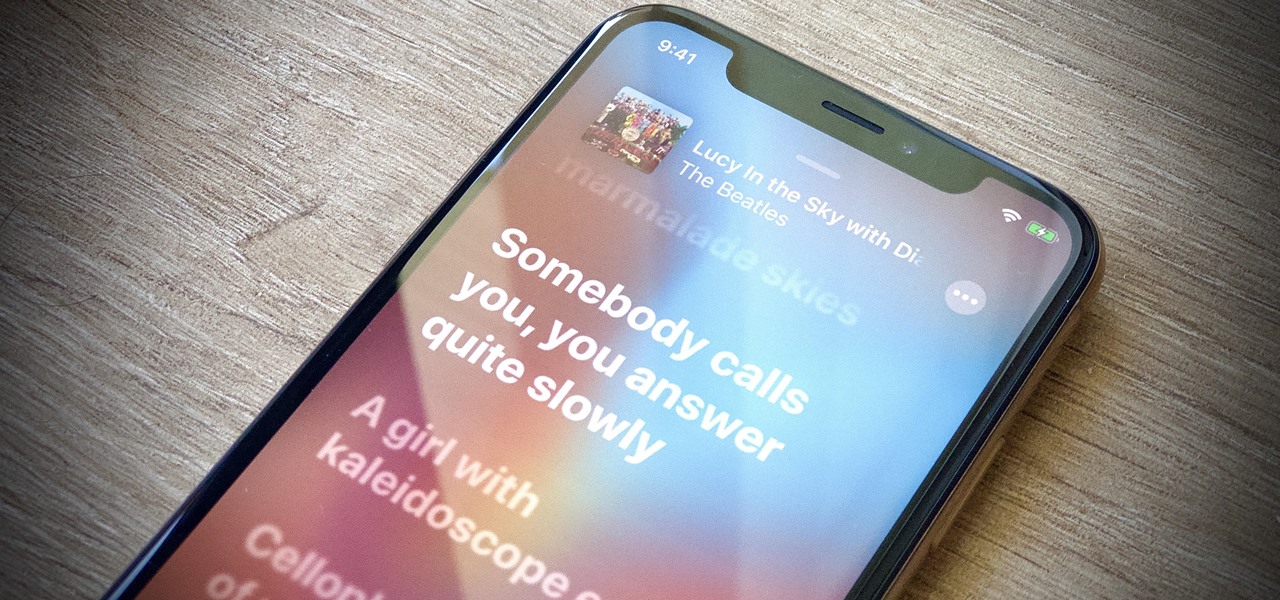
There are a lot of songs out there, so it's tough to remember all of the words to every song you like. If you're like me and have a less-than-perfect memory, visual aids will ensure your Apple Music jams aren't interrupted with incorrect or forgotten lyrics. That's why Apple's update with time-synced lyrics is so cool, essentially turning your iPhone into a portable karaoke machine.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

With the growing list of products Apple offers, the number of devices connected to your Apple ID can get quite extensive. Having all those devices connected to your Apple ID helps you keep track of them, but when it comes time to part ways with an Apple TV or Apple Watch, those devices can still be attached to your Apple ID. In some cases, this could affect the overall security of your account.

It's confession time. Through a couple of sources, I managed to get an early look at the HoloLens 2. But I was sworn to secrecy, and I take my tech oaths seriously (shame on you, leakers).

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

Despite Huawei's ongoing battle with the US government, the Chinese company has continued to release phones in the US under its Honor brand. The Honor X series has been consistently released for several years, offering midrange specs at ridiculously low pricing, and the Honor 8X is no exception.

Apple often cites its tight integration of hardware and software for its success. Startup Illumix is looking to do the same thing for AR gaming by building an AR platform for its apps.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

When you drive along the deceptively sedate streets of Silicon Valley, there are few hints that all those nondescript office parks and low-rise buildings contain the very future of the planet, but they really do. On a recent trip to tech's epicenter, I found that out firsthand when I got to visit the offices of Meta, the startup that produced the Meta 2 augmented reality headset.

The Galaxy S9 and S9+ have a new camera feature that Samsung is calling "Dual Aperture." On the surface, that may sound like your typical techno-jargon, but it actually has some significant implications for the future of smartphone photography.

The latest and greatest in Qualcomm's long line of mobile processors, the Snapdragon 845, is now set to touch down along with the Galaxy S9 and S9+. And as gorgeous as Samsung's newest flagships are, the processor that powers them under the hood is just as highly anticipated.

Thanks to iCloud and AirDrop, it's really easy to sync photos between an iPhone and a Mac. But if you have an Apple phone and a Windows computer, this process isn't quite as simple. Thankfully, Microsoft has just released a new iPhone app that makes it a breeze to move photos and videos from your iPhone to your PC.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

When a firm like Techstars believes that augmented reality is an attractive industry to invest in, there's a high probability that it's right.

Apple demonstrated their continued interest and investment into the awesome world of augmented reality during their Sept. 12 event, highlighting a few new AR games that will appear on iPhones thanks to ARKit. But that's not all you can expect — as long as you have an iPhone with an A9 chip or later, there will be a ton of cool new AR tools, games, and other apps to play around from the App Store.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

The launch of the Audi A8 marks the world's first Level 3 car on offer in retail channels, except there is one catch: it can only take full control of driving at speeds of 37.3 mph or less.

More bad news for patients who have undergone heart surgery in the past five years. A new study suggests about one-third of heater-cooler units used in cardiac procedures remain contaminated with a slow-growing, potentially fatal bacteria.