Glitches can be extremely annoying when playing some of your favorite games, but sometimes, only sometimes, there are glitches in the game that give you an unprecedented advantage against the computer or other players online.

It's really no wonder why Christmas is the most popular and widely celebrated holiday of the year. Your whole family gets a chance to spend some much needed quality time together—and not just gorging on food like at Thanksgiving. But in all seriousness, that's not the reason at all... we're talking Christmas presents here.

Even if you're not a hipster with your own self-sufficient garden, making your own edibles at home can be pretty cool. And while it's obviously easier to pick up a bottle of 7-Up at the store, there's something undoubtedly fun about making your own. For those addicted to their fizzy drinks, DIY soda is a great way to save some cash and make their drinks healthier with natural flavors and sweeteners, instead of something like corn syrup or aspartame.

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

With the release of Windows 8 right around the corner, if you plan on buying it (or just want to see what it's all about), it's a good idea to take advantage of the free trial before you shell out any money. If you're an Apple user who doesn't have a deep-seated disdain for Microsoft products, this tutorial will show you how to install the Windows 8 preview to try it out on your MacBook. First things first, you'll want to download the Release Preview on Microsoft's website (make sure to save ...

Hello! Today I would like to write a few lines about making a simple bed for your pet, for example, your cat or a bunny, using your old fabric. All interested can stir up a bit in the closet. I am sure there's an old towel or a blanket just waiting to be reused. Or some old clothes, made out of fleece, etc...

If you've got more than one computer, it can be a huge pain to switch form one to the other. Between files, settings and apps, it can take a while to transfer everything—and if you're running different operating systems, it's even worse. Image by Onion

Mountain Lion (OS X 10.8) is out today, available in the Mac App Store for just $20. Unfortunately, installing Mountain Lion requires that you already have a Mac running Snow Leopard (OS X 10.6) or Lion (OS X 10.7). If you're currently running a Leopard system, you're out of luck, and need to pay $29 to upgrade to Snow Leopard, and then an additional $20 to upgrade again to Mountain Lion. That sounds like way to much trouble to me. But why exactly is Leopard incompatible? Turns out it's not—m...

If you want to play a prank, why not do it to people you don't know. Not only will they not suspect a thing, but their reactions can be very funny to watch.

In this video tutorial, viewers learn how to refurnish hardwood floors. Using a drum or belt sander, begin by cutting 36 grit abrasive. Then remove all the old finish marks and scratches from the main body of the floor. Using an edge sander, do the same thing. Now vacuum the floor and then repeat the process once again with both sanding machines, except use 50 grit abrasive this time. For the third time, use 80 grit abrasive and 100 grit abrasive for the fourth time. Remember to vacuum each t...

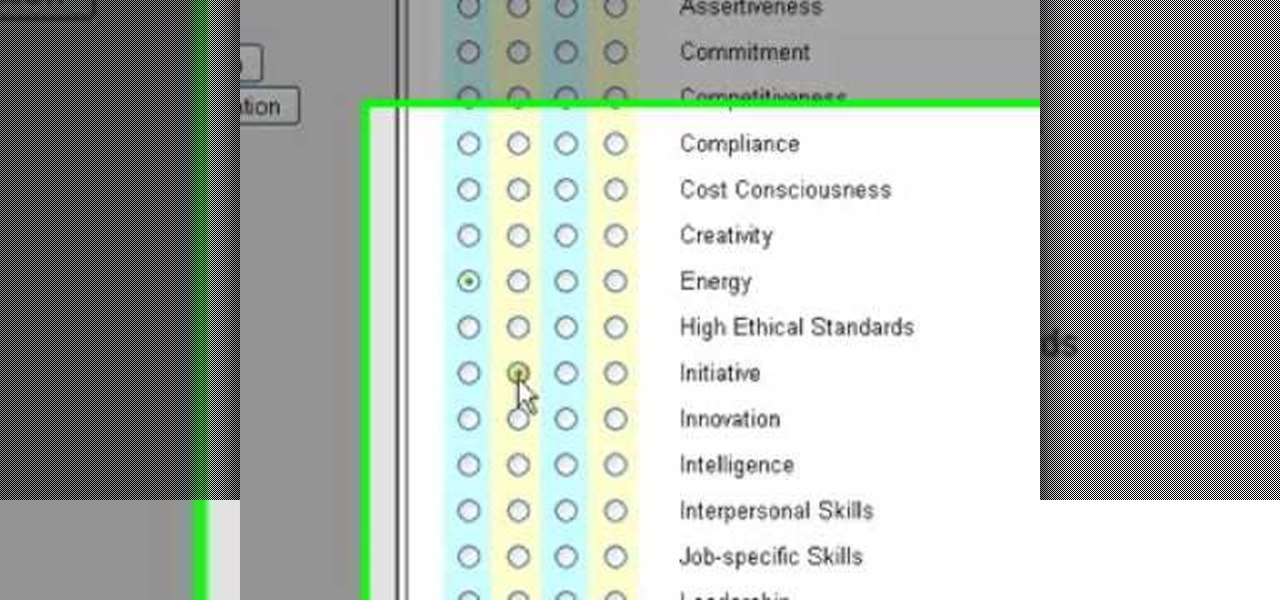
Letters of recommendation are important in the business world. If you have been asked to write about a coworker, student or friend, check out this tutorial. Takes you through a step-by-step process you can use to produce a professional-looking and highly effective letter of recommendation. Includes how to structure your letter, how to personalize it for your candidate, and how to make it convincing to the recipient.

In this Diet & Health video tutorial you will learn how to check your own blood pressure. Checking blood pressure is a very important part of your personal health routine. Using machines that are widely available, you can easily and quickly check your blood pressure. The target figure will be 140 over 90. The other parameter is the pulse rate. If you are higher than these figures, you need to take a second opinion and consult your GP. Wrap the arm band around the upper arm above the elbow. Pl...

Already an impressive gaming machine, the Xbox 360 can be modified to play a wider variety of games. This instructional video demonstrates how to flash your Xbox 360 to play downloadable games from the Internet. This method only works on the Hitachi v0078fk drive and will void your warranty, but think of how cool it would be to pull this off.

How to make an overall style tank top: To make an overall style tank top, find a tank top you like. Make an incision in the strap to where the overall strap would be. Take a buckle and sew it on. You may also use a desired fabric by tracing your tank top shape onto the fabric, cut it out and sew it all together. For a shortcut, cut an extra piece of fabric and sew it directly onto the tank top strap, before you sew the shoulder seams, and attach the button accordingly. Sew the overall tank to...

This is a video good for people who have problems with their Apple iPod. It uses simple steps in order to tell you how to successfully reset the iPod to its default state. Though it works primarily on the older models, viewers will learn which buttons on the machine allow you to completely reset the system in case of a system freeze or other problems. These easy to follow instructions will allow even people who have problems with technology to clean their system and get the iPod back to full ...

This glitch is a simple one on Killzone 2 for PS3. To do this glitch, you'll need to perform the medic technique Just watch the whole video walkthrough to find out how to find the Radec Academy Glitch.

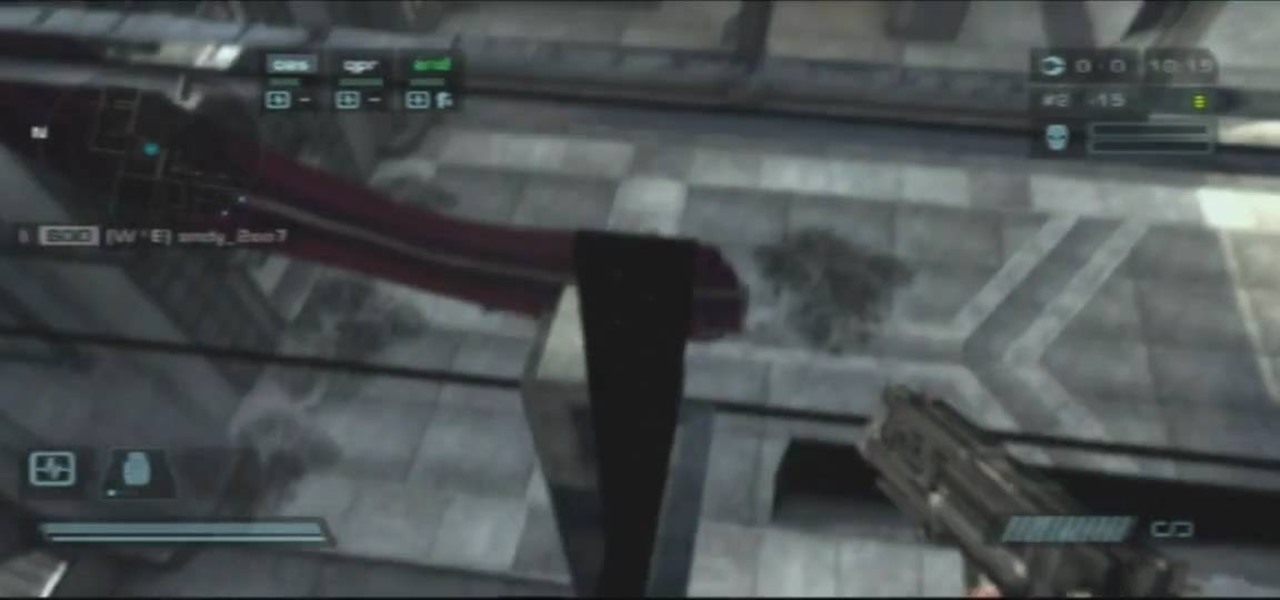
On this map, you can do this great glitch on Killzone 2 for PS3. There's a lot to do on this map, so there's sure to be many more glitches, but you'll have to figure that out yourself. Just watch the whole video walkthrough to find out how to find the Outside Pyrrhus Rise Glitch.

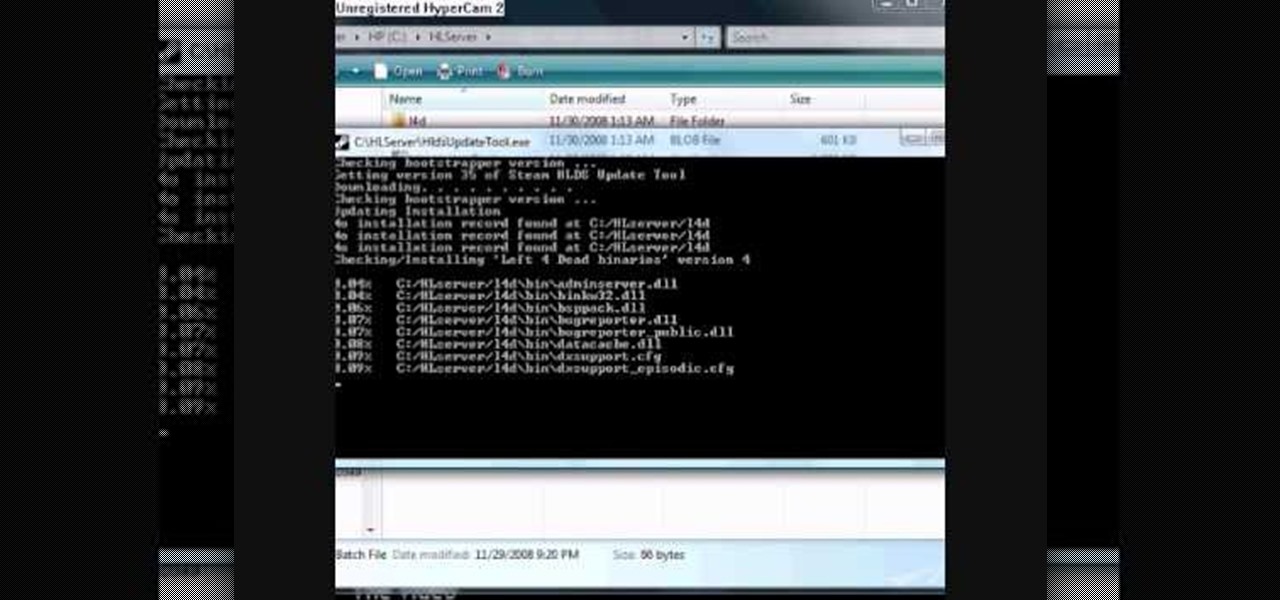
If you don't want to shell out the money to rent a dedicated server in order to host a Left 4 Dead game server, follow this tutorial on how to create one on your home computer. Keep in mind that if you intend on letting other people play it, you will need a fast connection to prevent lag.

This truck repair video shows you how to remove the bed from a Chevrolet C1500 W/T truck. This needs to be done to fix certain problems, in this case the fuel lines. Whatever reason you need to remove the bed from your Chevy, this video shows you how to do it properly.

Here is a tutorial on getting a perfect 1/4" seam allowance for quilt piecing. The sewing machine foot will sometimes have a groove to allow you to make a perfect quarter inch seam automatically. If you don't have one of these, there are a few ways to make your own quarter inch seam guide.

This video will show you the proper technique for getting your snowmobile out of the snow after it falls and gets stuck in a snowdrift. Snowmobile safety is important and this video will show you just how you can keep your machine out of the snow.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

With the success of Iron Man in 2008, a video game adaption quickly hit the market, so it's no surprise that when Iron Man 2 came out this year, that a video game would follow close behind. Sega released Iron Man 2 in a variety of gaming formats, including the Xbox 360, PlayStation 3, PlayStation Portable, Nintendo Wii, Nintendo DS, along with iPhone and other mobile devices. The story of the game takes place after the plot of the film, except the iPhone game, which mimics the movie's plot.

The Mad Hatter from Tim Burton's Alice in Wonderland not only makes a great costume but a great project. The hour-glass shaped hat, the striped pants, the fingerless gloves, and the Hatter's signature scarf are the most important components in this costume. If you're fairly skilled with costuming already, this shouldn't take more than four or so hours.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Mobile World Congress is a four-day event that is both a showcase and conference starring prominent figures in the mobile industry. Oftentimes, OEMs will use this event to announce new products for the upcoming year — and this year shouldn't be any different. Here are all the phones we expect to be announced.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.

In the past, to see a pre-constructed state of the house that you would one day live in, you had to be able to read blueprints or hire an artist to sketch it out. Later came the ability to have a 3D rendering of that house on a screen, but you'd still have to work hard to envision it in real life.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.