I was just 16 when I poured my first beer. It was my first restaurant job and a customer ordered a pint while the bartender was busy. I'd seen her do it hundreds of times, and she made it look so easy. Besides, it couldn't be that different from filling a cup from the soda machine, right?

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

A very large aspect of minecraft is redstone. Infact, redstone is probably what keeps me playing minecraft today. Ever since the piston update of beta 1.7, redstone has taken minecraft to a whole new level, with the ability to manipulate the entire world around you with the flick of a switch. In this guide I'm going to quickly cover a few great redstone tips you probably did not know!

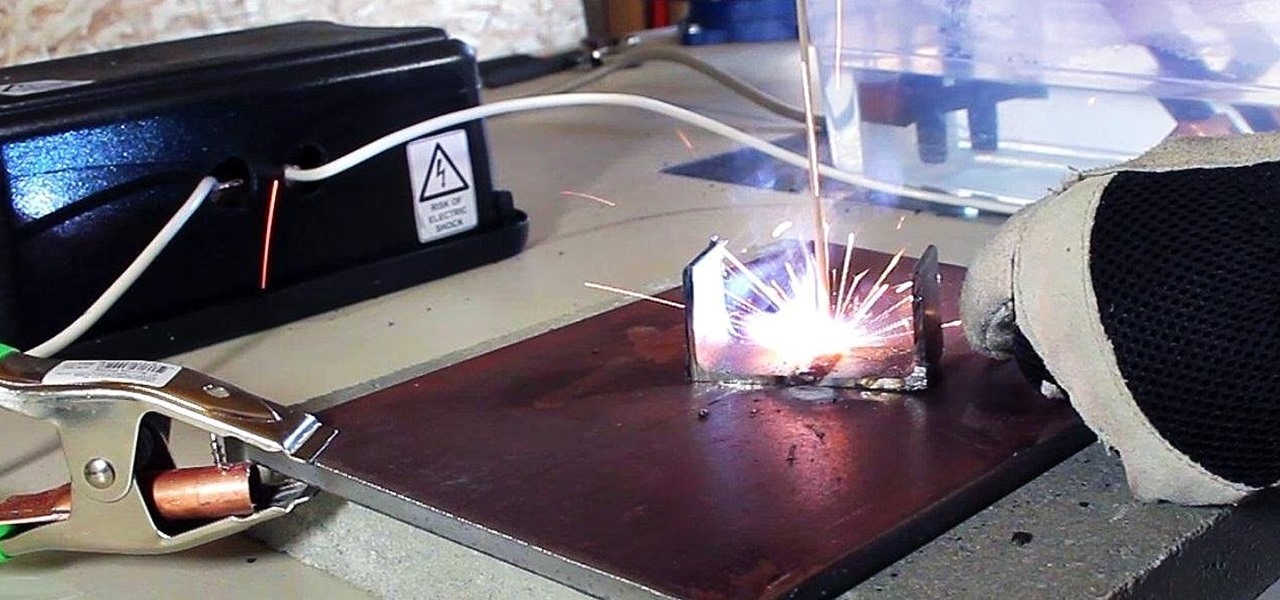
In a previous article, I demonstrated an Arc Welder made using parts from old microwave ovens. Video: .

I was kinda disappointed with last year's James Bond movie, Skyfall. Don't get me wrong, it was a solid flick, but only made me jealous with all its super spy hacker stuff.

Like a computer, your brain can store and process large amounts of information. It can remember names, solve math problems, and save tips that you might need at a later time.

Say whatever you want, but Steampunk is primarily a maker culture. Consider that Steampunk has existed since the 1960s and yet more or less languished in obscurity until approximately 2005, which is when it made the leap to costuming. That costuming was what provided the leap to the tangible, despite the fact that Steampunk art had also existed for years.

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the communities. But don't wait—start submitting your own projects to the most appropriate World now!

First off—Happy Independence Day! Since it's the 4th of July, let's make this week's roundup short and sweet, so you can all get back to your holiday festivities.

I may be a bit weird, but I enjoy listening to music at night as I fall asleep. Sure, you could create a playlist of songs so that it stopped after all the songs finished playing, but I have a rather extensive database of music and I enjoy listening to them randomly. Also, I like to ensure it terminates after a specific amount of time (I don't want it playing all night). Or sometimes I use it when I am cooking so that when the music stops, I know I need to check on my food, etc.

I have owned quite the plethora of electronics in my life. A commonality between most of these devices' screens is frozen or dead pixels. This is probably the most annoying thing about buying new hardware—your LCD, or worse, LED display has one or more pixels that continues to stay lit. Most of the time, this will appear in the form of a brightly colored pixel that never changes, or a pixel that never displays the right color. Once you notice it's there, you just can't stop staring at it. It ...

This article is a guide for making Chainmail Armor from start (simple wire) to finish (a finished chainmail shirt). We will be using the European 4 in 1 weave, as this is the most common weave. This is the weave that you usually see in movies. There are several sections to this guide: Materials, Making the Rings, Weaving the Rings, and Making the shirt.

PowerShell is an essential component of any Windows environment and can be a powerful tool in the hands of a hacker. During post-exploitation, PowerShell scripts can make privilege escalation and pivoting a breeze, but its execution policy can put a damper on even the best-laid plans. There are a variety of methods, however, that can be used to bypass PowerShell execution policy.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

There are many ways to jailbreak the iPhone, found all over the internet. This method explains how to jailbreak the iPhone or iPod touch using Quickfreedom 2.0 BETA on a machine running Windows Vista.

Expert tattoo artist Rick Wyckoff offers a wealth of knowledge on the history of tattoos, explains how the tattoo machine works, and offers tips on how to care for a new tattoo, how to preserve the pigment, and how to deal with the pain that comes with being tattooed.

In this series of online video tutorials you'll learn how to use Reason 3.0 music recording software. Expert Jerus Arte demonstrates how to use the program, from installing it on your computer and setting it up with the right preferences, how to control the master volume, and how to use features like the NN-19, the NN-XT, the Dr, Rex loop player, and the Redrum machine. He shows you how to use effects like the compressor and reverb, and how to mix down your song into a format that can be burn...

Mosaics are a cool type of art. You can use mosaics to liven up your home or garden and they are cheap and fun to make. Check out this video for tips and instructions for making mosaics.

It’s easy to gain a little extra weight in college but there are ways to defy this weight gain trend. It won’t work without will power but you can limit your unhealthy food intake and sneak in some unconventional exercise routines.

In these music studio recording and production videos, learn how to use a 4-track reel to reel tape recorder to capture your vocals, guitar parts, drums, record songs, or even make a demo CD. Our expert will walk you through the operation of a fairly simple reel to reel machine in several steps, including the basic and advanced functions, rear components, using mics and connecting to other mixing boards, recording on four different tracks, mixdown, bouncing tracks, and final tips for masterin...

In this tutorial video, learn how to use the audio sampling features of the Akai MPC 4000 drum machine. Our expert music producer will give you a tour of the basic interface for the MPC, and then show you how to load, chop, and slice samples, use the sequencer, and create your own samples and sequences for your music.

In this informative video clip series, our expert seamstress will show you everything you need to begin a sewing project either by machine or by hand. Learn how to measure fabric and what types of measuring devices are available, see the types of scissors, rulers, thimbles and pins are available to choose from, and get pointers on fray checkers and seam rippers. Everything you'll need to begin a sewing project is right here!

In this DIY home improvement video series, learn how to pressure wash the exterior of your house—as well as the sidewalks, driveway and deck. Our expert will show you where to get a pressure washing machine, how to hook it up, what wands and tips to use, and how to start the pressure washer. Then follow him as he takes you around the house—from roof, to eaves, to windows, to exterior walls—showing you the proper pressure washing techniques for cleaning. After watching these videos, you should...

In this series of expert videos, you will learn more about lawnmower maintenance. Watch these videos to see how easy do-it-yourself lawnmower maintenance can be! You will learn how to clean your lawn mowing machine, and keep it free of dirt, rust, and grass clippings. Get tips on changing the oil and air filter on your lawnmower. Learn how to mix two-stroke fuel for your mower. Watch as our expert removes gas, foam filters, and dirty spark plugs from a lawnmower. When changing the blades of y...

Skulls. What spooky Halloween décor or staging of Hamlet is complete without a skull or two popping up? For ghoulish special effect and/or setting a dramatic scene, skulls are absolutely integral. Well, with some artistry, hardware supplies, and a good dose of patience, you can create your own inexpensive prop skulls for use however you please.

These are some tricks for advanced computer use. These are PC only and meant for use on Windows XP machines.

Apple's Live Voicemail lets you preview what an incoming caller is speaking to your voicemail system in real time. It's a revolutionary feature like Visual Voicemail on the original iPhone, only better since it helps you screen calls to quickly decide whether to answer or ignore callers. It's similar to answering machines, whose popularity peaked in the mid-90s, but you quietly read transcribed messages instead.

If you use Goals in Google Calendar, you've probably already received the notification that Google, in typical executioner fashion, has marked the feature for death. As of November 2022, you can't create new goals, and your current goals won't repeat anymore. Google suggests switching to repeating events or tasks, but there's a better option to use on your Android and iOS device.

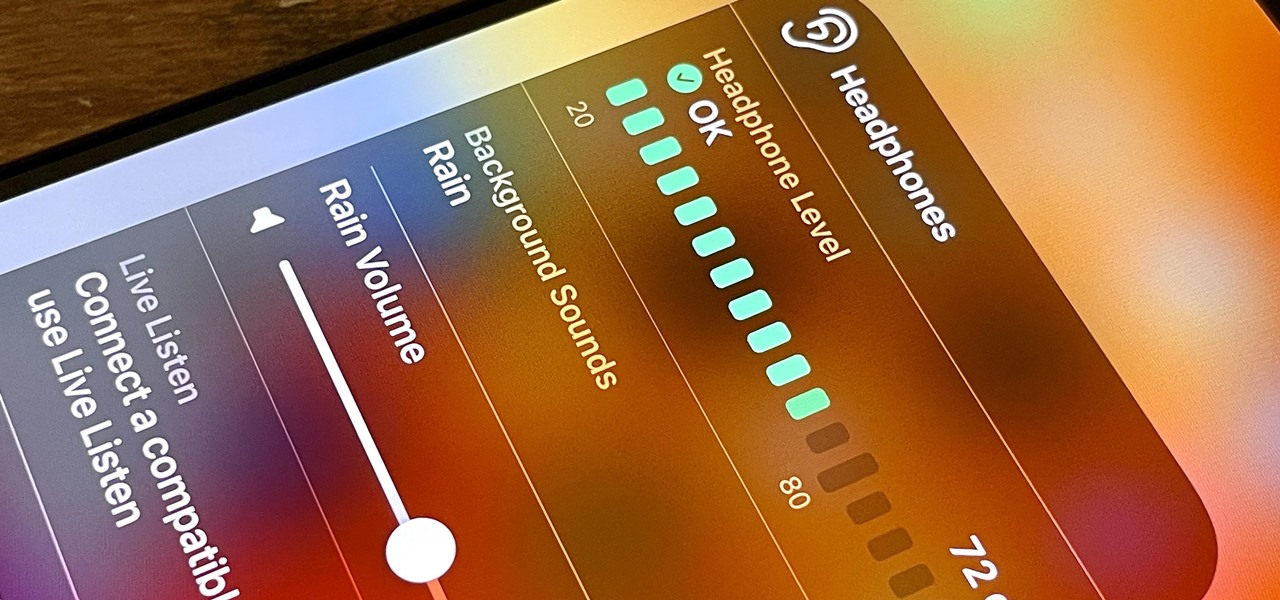
If you get distracted or stressed out easily, your iPhone might be able to help you focus or calm you down. It can even help you fall asleep with white noise, and you don't have to install a third-party app or buy an audio track to turn your iPhone into a personal sound machine.

We usually focus on augmented reality here, but when something important in VR happens, we highlight it as part of the overall immersive computing story.

After tapping Nvidia for its first AR headset, Magic Leap is calling in reinforcement for its future enterprise-focused efforts.

Linux is a diverse and powerful operating system that virtually every IT professional must learn and know well. Whether you realize it or not, you have likely already used a Linux device, and learning to design things for it is a key step in any Data Science career path.