Social media accounts are a favorite target for hackers, and the most effective tactics for attacking accounts on websites like Facebook, Instagram, and Twitter are often based on phishing. These password-stealing attacks rely on tricking users into entering their passwords into a convincing fake webpage, and they have become increasingly easy to make thanks to tools like BlackEye.

Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible.

Whether it's a short road trip or an 18-hour flight, our phones are now essential travel companions. No longer do we need a GPS unit, maps, cameras, camcorders, or even boarding passes. However, not all phones are created equal in this regard. Some are more suited for traveling, no matter the duration.
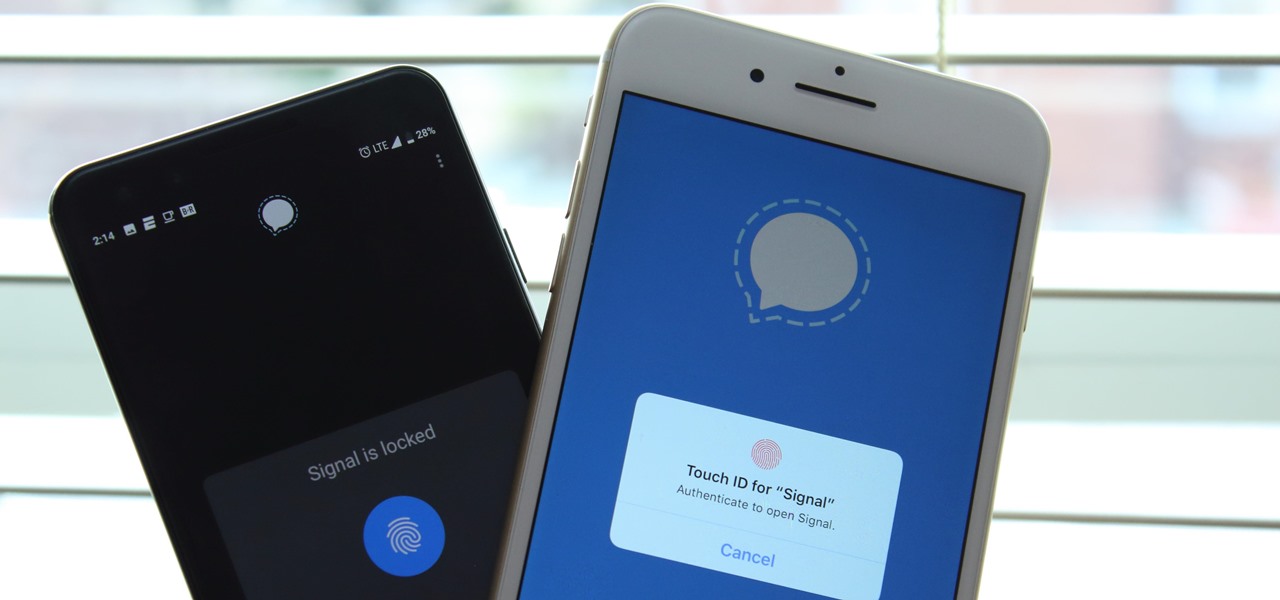
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through the process.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alternative that could provide some sense of security and trust.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

The devices in the new iPhone 16 series lineup have one feature no other iPhone models have: a physical Camera Control button. If you use your iPhone to take photos or record videos, the Camera Control speeds up the process and gives you immediate control over adjusting settings and values using intuitive gestures. But what exactly can you do with it?

Many of the iPhone 15, 15 Plus, 15 Pro, and 15 Pro Max features were carried over from last year's models. Still, quite a few capabilities are exclusive to the 2023 lineup, and some may be worth the upgrade.

Apple's latest big software update includes an entirely new Apple app, a controversial change in the TV app, better Siri control, an improved Shortcuts app, interesting Safari upgrades, Apple Music Sing, and more. Keep reading to see what iOS 16.2 has to offer your iPhone.

Apple's Siri is well-versed in the spells of the Wizarding World of Harry Potter, but it's not like Android users are Muggles. Google Assistant, Android's virtual concierge, can cast a few spells out of the box, and it can learn the spells it doesn't know quicker than a year of studying at Hogwarts.

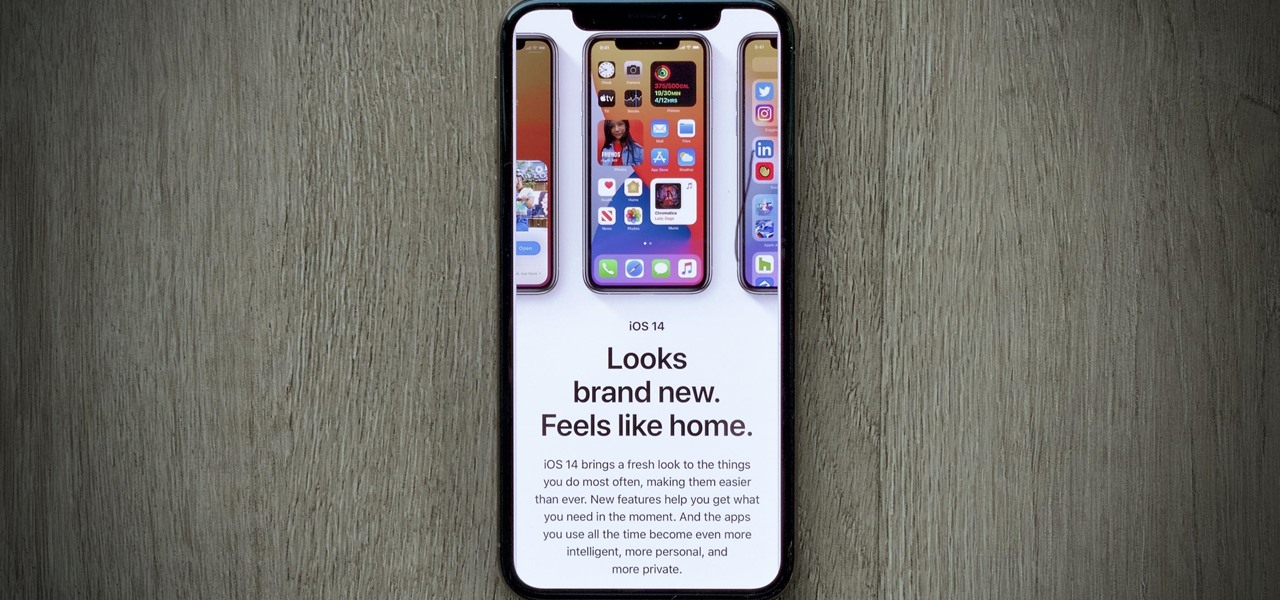
Apple's iOS 14 is here. With it, you'll see over 200 new features and changes hit your iPhone, including home screen widgets, inline replies in Messages, and cycling routes in Maps. Here's how you can get your hands on the brand new update.

Apple just seeded developers and public beta testers the GM (golden master) for iOS 14 on Tuesday, Sept 15. The update (18A373) comes just after Apple's "Time Flies" event, and six days after Apple released iOS 14 beta 8 for both developers and public testers.

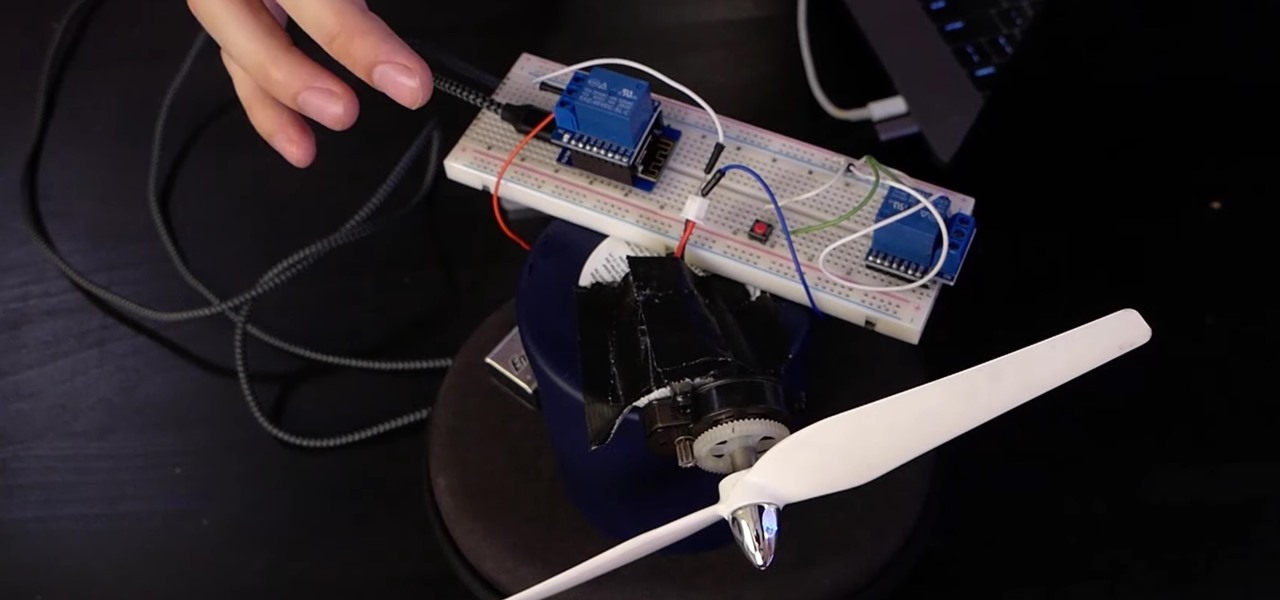
If you want to control electronic devices, such as a relay or motor, you can do so using MicroPython with an ESP8266 and web browser. Usually, you'd program an ESP8266 using Arduino, but C++, which Arduino uses, is not always the easiest programming language for beginners to learn.

Remember concerts? Those were fun. While gathering in large groups to listen to live music might not be allowed at the moment, the live music part still is. Thanks to the internet, more and more musicians are taking the stage each day to perform for those of us stuck in social isolation due to the new coronavirus. The best part? Many of these concerts are 100% free.

Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But there are several methods to brute-force FTP credentials and gain server access.

In the case of Apple Watch v. Fitbit, the winner comes down to the judge at hand. Apple currently offers two smartwatches — the Series 5 and the Series 3 — while Fitbit offers three models — the Fitbit Versa 2, Fitbit Ionic, and Fitbit Versa Lite. Whatever your assumptions about these devices are, throw them out the window, as each has something unique to bring to the table.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we could find so you know exactly what to expect when updating to iOS 12 on your iPhone.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

There's a lot more to your iPhone's dialer screen than just entering phone numbers and hitting the green call button. It's not very obvious, but there are secret codes that you can enter on the dialer to find out information about your device, help troubleshoot issues, and mask outgoing calls, to name just a few things.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

Will the predicted apocalyptic date — December 21st, 2012 — really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyberwars, earthquakes, or aliens actually destroyed our planet — and how you might survive.

To do this "curtsy lunge" exercise is a great for a leg workout. But you should first be completely competent with the lunge and split squat exercises first. This lunge exercises is brought to you by Men's Health.

This ten-part series on machining skills for prototype development comes straight from MIT & Erik Vaaler. It's one of the most extensive video tutorials available on the web for machining. MIT's artificial intelligence laboratory's primary work is done for their robotics group. And most of their equipment is unavailable to the public because they're machines that MIT have built directly in their machine shop, or items that came into the shop needing repair. But if you can get your hands on so...

This instructional video will show you how to get all of the change out of a vending machine! Who needs Coke or Pepsi when you can have coins? Then, you can get all of the soda you want out of that vending machine.

To use your washing machine you will need washing powder and fabric softener. Load the washing into the machine making sure you've separated whites from colors. Choose a low heat for delicates and a high heat for badly stained clothes. Use your washing machine.

This video demonstrates how to make a fart machine. Here is a simple step by step instructions how to make your very own Mega Fart Machine. From XL-2000 farts to F-9000 Bombs. It's so simple, even your grandma can do it! Why wait, go out and make your own Mega Fat Machine. Use this as inspiration for one of your April Fools Day pranks! Make a fart machine.

Dovetails are an extremely old and effective wood joint. There are three types of dovetails, through dovetails (the most popular), half blind dovetails, and sliding dovetails. In this woodworking video tutorial, you will learn how to do a machine cut through dovetail. Cut through dovetails with a machine.

We happen to use an 802.11n AirPort Extreme as our router, so we put today's new firmware upgrade to the test to see if TIme Machine really does work with AirPort Disk. As expected, it works and only requires a few simple steps...

So your washing machine is on the blink? Dirty clothes piling up? You're embarrassed of your smalls and can't face the launderette? Watch this video tutorial to save your blushes and get your machine up and running again in no time...

In this video tutorial you will create a VMware virtual machine. This trick will save you from spending a crazy amount of cash for a workstation. Watch this video, and learn how to play around with the numerous settings involved! Create a VMware virtual machine.

You can learn how to make a rumble pipe sound effect machine and you need to cut a pvc pipe to seven inches. Glue a piece of drum skin to the end of the pvc pipe and then check it out. Video is brought to you by KipKay. Make a rumble pipe sound effect machine.

From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Mac for Dummies. Just watch this video tutorial to learn how to back up files with Time Machine, For Dummies.
I've struggled for a long time trying to set up a virtual network between my KVM virtual machines. I tried several forums and tutorials on the web, but still on my system it just wouldn't work. I eventually got it owrking, so I've decided to make some notes of my own. Hopefully it will be helpful to you as a reader as well.

So very pointless, yet unquestionably spectacular. The best kind of "art" performs no other function than to delight the viewer, and Japanese YouTube user Denha's complex marble machines do just that. But are marble machines art? You can call them that—or toys, scientific contraptions, engineering feats—but however you choose to label them, the best marble machines are complicated, skillfully crafted, and driven by the principles of potential energy, kinetic energy and gravity.
Nothing sucks more than when you discover your thread is feeding incorrectly, or your machine just isn't working properly.