Check out this video to learn how to build a rapid fire egg dispenser in Minecraft. You can also load this machine with arros, snowballs, and other goodies and watch them fly. This machine fires a lot of items in a little time.

Check out this video for an elegant solution to the problem of sugar cane harvesting. Streamline your harvesting with this clever, effective, machine. Watch the video to learn how to replicate this design and build your own sugar cane harvesting machine in Minecraft.

In this sewing tutorial, you'll need a sewing machine to make a blind hem stitch. The sewing machine used is a Brother LX-1325 compact and lightweight model, but you can use a similar brand and model. To make a blind stitch, you'll need to fold the fabric the way you normally would when sewing a hem stitch, then you'll pin it in place on the inside. Watch and see how it's done! Then you start sewing. This stitch will be hardly noticeable.

In this clip, you'll learn how to install Microsoft Windows 7 on a virtual machine with VirtualBox. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.

Everyone loves ice cream, no matter what age they are. So why not try making a little homemade ice cream instead of hitting up Ben & Jerry's? You'll enjoy it, and most of all, you're kids will love it. With this recipe and an ice cream maker, you can create your own sundaes, shakes and ice cream cones at home.

Before cutting the rotors select a centering cone that fits about halfway through the center hole of hub-less rotor or bearing spacer to center the rotor to the spindle. After select two identical clamps that fit the rotor without interfering with the machined surfaces of the rotor. Slide one clamp onto lathe shaft, open end out Slide spring, followed by centering cone. Slide on the rotor and outer clamp followed by the bushing, spacer, and nut. Tighten nut and Install damping strap. Adjust t...

Playing your favorite songs by Rage Against the Machine on the guitar is not as difficult as it seems. With this tutorial you can learn how to play "Know Your Enemy" by Rage Against the Machine on the acoustic guitar. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Marty Schwartz covers the finger picking as well as the chord structure for "Know Your Enemy." Watch this how to video and you will be able to sing and play "Know Your Ene...

This instructional knitting video provides tips for making interesting patterns using a knitting machine. Use a two prong tool to twist a stitch. Once you set the twist, you can knit an entire stretch of fabric with an elegant twisted stitch pattern.

This instructional knitting video demonstrates how to how to change to a different yarn on a circular knitting machine. Simply cut the yarn when you want to switch to a different color an tie a slipknot to the next type of yarn. It's easy!

Watch this instructional quilting video to quilt a tendril or "C" background fill with a longarm sewing machine. This pattern is a simple and convenient way to create an elegant background fill on many kinds of quilts. It helps to draw the tendril pattern with pen before trying it with the longarm sewing machine. Customers love it.

Check out this how-to video to learn the correct way to operate a popcorn machine. Make sure you always unplug your popcorn machine before you do any kind of cleaning. It will take about three or four minutes before your pop corn is finished popping. When the corn is almost done popping, grab the handle and dump the kettle. You will want to dump in twice to make sure all the popcorn has fallen out of the kettle.

Watch this how-to video to operate a kettle corn machine called the 2575 Pappy's kettle corn cooker. First, you must use a one-hundred pound liquid propane gas tank. You will only use three kernels of kettle corn for your first batch.

This video tutorial shows how to use Nestabilities molds and the Cuttlebug embossing machine to cut out shapes. Learn how to multi-task with the Cuttlebug embosser, and cut out paper shapes that would be difficult to create evenly by hand.

A tutorial on how to "break in" to your Windows machine after you have lost the password. This works in Windows NT, 2000, and XP machines without an encrypted file system. I then show you how to wipe a hard disk to assure no one can gain access to your data once the drive is sold or discarded.

A router table is a stationary woodworking machine in which a vertical spindle of a woodworking machine projects from the table, allowing you to cut wood at many different speeds. Different cutter heads or drill bits may be mounted on the router depending on the material you're working with.

Watch this video to learn how to make chewy cinnamon raisin bagel from a bread machine. Enjoy!

Learn how to con a vending Pepsi machine and access a secret (but benign) debug menu with this hack how-to video. While this hack won't get you any free soda, you might, at the very least, impress your friends with it. For complete instructions for this simple, pushbutton hack, take a look at this instructional video!

Build a machine that will cool beer in as fast as 6 seconds using an Airduster can of compressed air.

This video provides you with information on how to set up the Omni Stitch machine.

Sandy shows you how to make a candle centerpiece and use a pick machine.

Sample different types of threads and sewing machine settings to learn the best combinations for varying sewing projects and effects.

This video demonstrates how to work out your quadricep muscles using a leg extension machine. The video walks you through adjusting the machine to your body type and explains how to perform the exercises correctly.

Bob Seguin demonstrates how to carve and assemble a mini sewing machine out of basswood. The video walks your through preparing the wood, carving it, painting, and putting the pieces together.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

As we have seen previously with the likes of SethBling's Mar I/O videos and other examples, video games seem to be a great source for training AI neural networks. Augmented reality and machine learning are part of a collection of technologies that seem to be growing toward a point of maturity, and that will likely cause them to be intertwined for the foreseeable future. As developers, machine learning will definitely change the way we create software in the coming future. Instead of going lin...

You just sat down, coffee in hand, and the day is ready to start. Now that you have taken a few sips, let me pose a question: What is living in that coffeemaker of yours? The answer might make you dump that coffee down the drain pronto.

We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

Automated tattoos are now a reality, with 3D printers being hacked into tattoo machines. Multiple people have posted videos of their 3D printer that can "print" tattoos, with one of the more impressive ones shown in the two videos below.

This video will show you how to fix, repair, replace a broken agitator in your wash machine. If the agitator stopped turning, this is an easy way to fix it.

lubuntu is a is a lightweight Linux/Ubuntu that makes it suitable to virtual environments, that you run with VirtualBox to add a secondary machine to your computer or laptop. With this program you can run a number of operating systems upon the same platform.

C.R.E.A.M., aka Cash Rules Everything Around Me. There have never been truer words spoken in real life, or even in a video game. After playing BioShock: Infinite for a few days know, I wish I came across this little glitch a little earlier.

A sous-vide is an "under vacuum," a method of cooking food sealed in plastic bags and then dipped into a water bath that typically takes up to 72 hours to complete. Why cook your food in plastic baggies, you ask? To make sure all the ingredients come out pure and unadulterated.

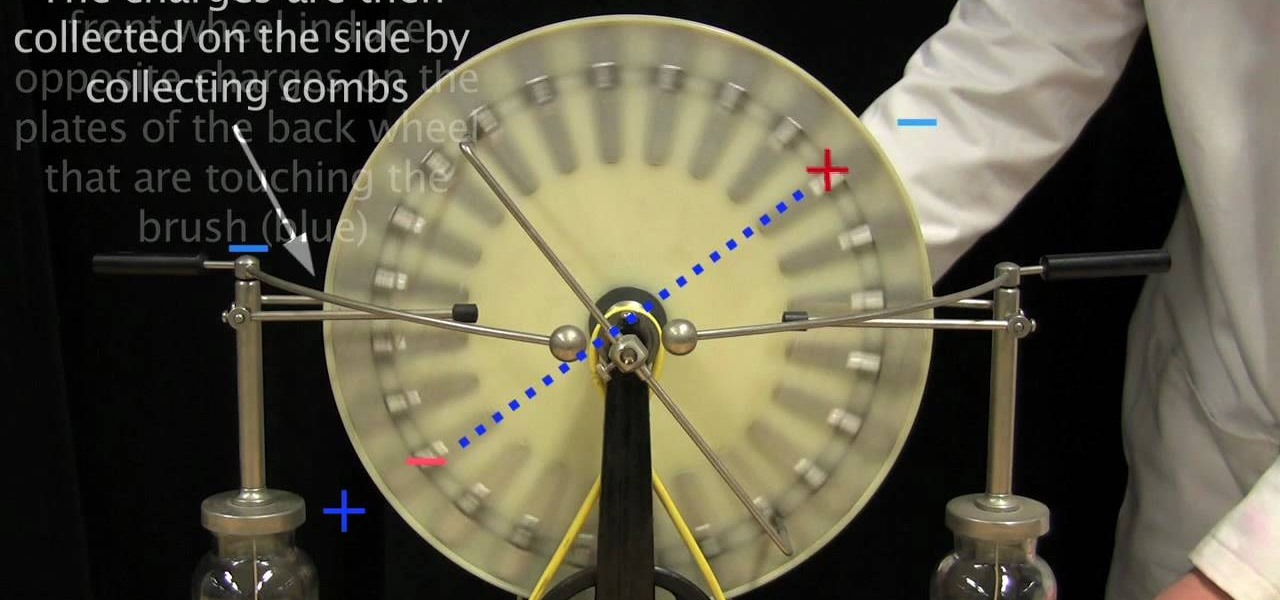
In this video, we learn how to use high voltages using the Wimhurst machine. First, you must have a spinning wheel, double ended brushes, collecting combs, leyden jars, adjustable electrodes, and small metal plates. Once you connect all these together, you will notice the brushes on either side are perpendicular to each other and the wheel spin in opposite directions. Spin the wheel and then listen to the sound it makes. The plate will then charge with different electrons and create positive ...

You want to know the real reason people don't exercise? Often, it comes down to having bulky exercise machines. Every time you look at them you get a reminder of how much pain you'll have to go through to get those perfect abs or sculpted butt. So for many of us we simply choose not to do anything.

At the end of last year Google released Chromium OS, the source code to their soon-to-be-released operating system Google Chrome OS. This has allowed millions of people to preview the new OS and make suggestions. Do you want in on that action? This video will show you how to install and run Google Chrome OS on a Mac using a virtual machine like VMWare or Virtual Box. Now you can be a part of the future of operating systems. Maybe.

If you're having a problem with your vacuum's clutch and need it replace, don't go pay someone for their service, do it yourself. Not only will you be saving yourself an arm and a leg, but you'll be able to understand how your machine works and what to do next time it breaks.

Back in the olden days, whenever we desired a nicely embroidered hankerchief or gown we'd sit by the fire with a flickering oil lamp, whittling our fingers away until the breaking hours of dawn. But nowadays, thanks to the genius of sewing machines, embroidery, even the most intricate kinds, takes far less time and midnight oil.