When alcohol tastes bad, there's little you can do to save it—or so you think. While it might seem easier to toss your entire bottle of old, opened wine, or to give up and drink crappy vodka anyway, there are creative ways to turn a spoiled or just plain bad boozy beverage into one you actually want to drink.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.

Cookbook author, celebrity chef, television personality, and former White House nuclear policy analyst Ina Garten is familiar to many as the queen of foolproof cooking. Also known as the Barefoot Contessa, Ina hones in on techniques and tips that make time in the kitchen far less intimidating to folks of all skill sets. We've rounded up 8 of Ina's most useful cooking tips to help you out—from dinner parties to everyday cooking. Her philosophy is that it's always easier than you think!

Once again, you've found yourself inviting comrades, companions, and compatriots over for beverages on a Friday evening whim... but alas, your alcohol cabinet is looking rather meager, and your skills are lacking. No worries—just utilize these 10 tricks and spice up your at-home mixology game. Your friends will be none the wiser (and swear that you are a cocktail-concocting genius).

Pickles come in all shapes, sizes, and names (gherkins in the UK, cornichons in France). There are even crazy flavors such as koolickles—dill pickles soaked in a mixture of Kool-Aid and brine, an American South favorite. Whatever sort of pickle tickles your fancy, you can count on one thing: there's always leftover juice once they've been eaten and enjoyed.

Welcome back, my neophyte hackers! In the world of information security, the most common intrusion detection system (IDS) you will ever encounter is Snort. As you probably already know, an IDS works similarly to antivirus (AV) software on your desktop; It attempts to identify malicious software on your network and warns you of its presence.

Home cooks are often quite intimidated when trying to reproduce the delicious ethnic dishes they enjoy at various restaurants. Thankfully, there are definite flavor profiles and spice/seasoning/herb combos that are very specific to various regional cuisines and cultures; with a little guidance, you can create dishes that are tasty homages to the cuisines you love to eat. In this two-part article (second part here), I'll cover both categories and sub-categories of some of the most popular ethn...

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments.

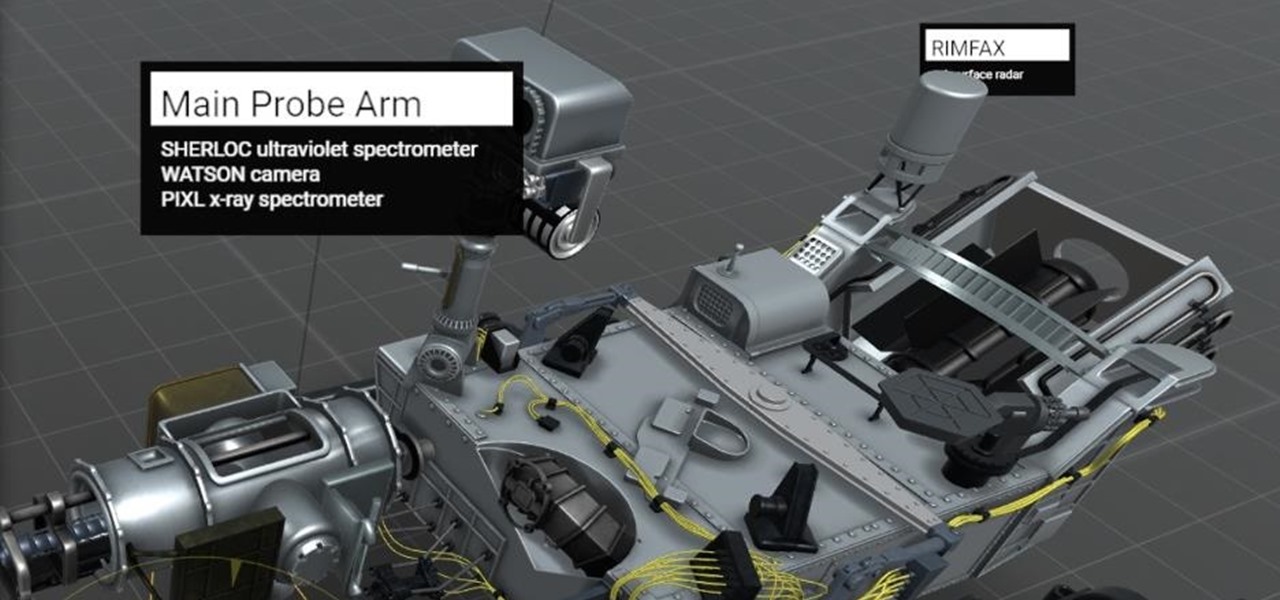
Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Your waffle maker might just be the most underutilized tool in your kitchen. This one appliance can make bacon, eggs, hash browns, cupcakes, falafel, mac and cheese, and cinnamon rolls much more quickly and with less mess than traditional methods. Plus, the results all come out waffle-shaped—what's not to love?

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

Many people drink green tea for health reasons, and it's no wonder. This beverage is a superstar when it comes to antioxidant levels, and is being studied for its potentially curative properties on multiple health concerns, whether it's staving off the aging process or fighting cancer.

Unless your work clothes require dry cleaning, you probably only go to the cleaner a few times a year. And for those few items in your closet for which you do, you have to then find the time and extra budget to make a trip all the way to the cleaners and back again. In the end, it can be quite the hassle.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

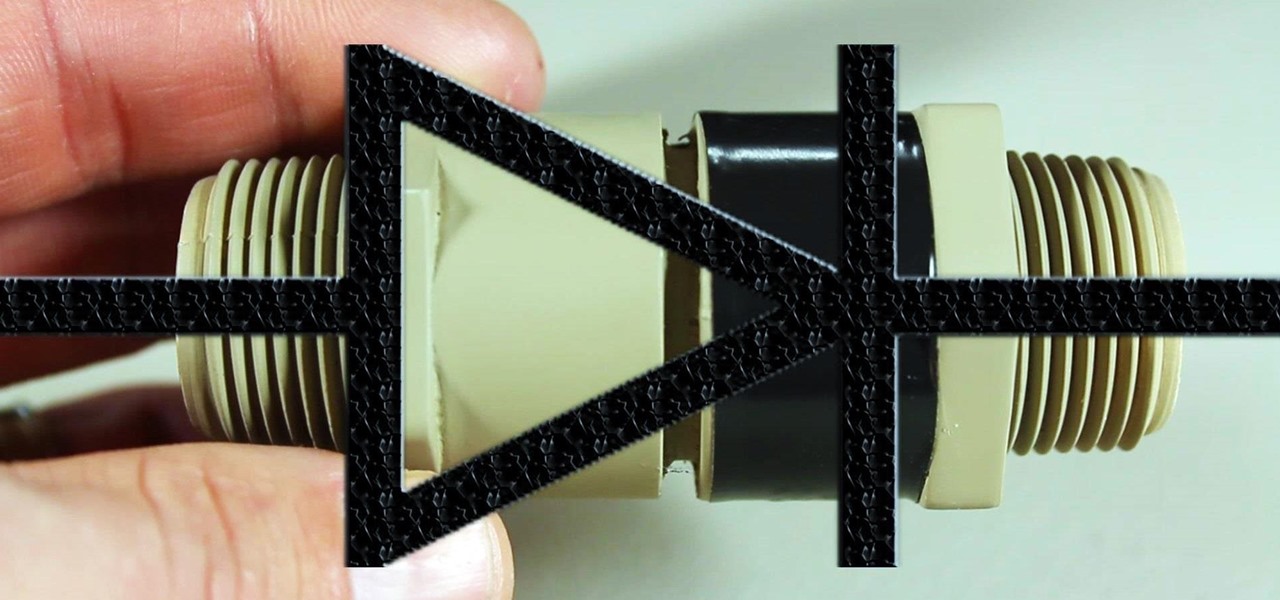
If you're going to build yourself a water gun to cool down this summer, or maybe just a useful water pump, you'll need some check valves. However, the most expensive parts of a water pump or DIY super soaker are usually the check valves. So, let's make some from scratch for as little as $0.35 each.

There's something special about Laika Inc.'s Paranorman... Hey! Did you love Coraline? Are you interested at all in stop-motion animation? Well, watch this feature on Laika Inc.’s new film, Paranorman.

Firstly, let me say a few quick things: Once built, this is a lazy (one button) way to harvest melons, but this is going to be a complex and lengthy build.

AppleScript is quite an easy scripting language to use. In this guide, I will be showing you several commands. Near the end, I will show how these can be used to create a fake virus that actually does no harm.

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

Jazz guitar music, in particular, is rooted in minor 7th chords and diminished 3rds; its sound is as distinctive as any in the jazz family. Advanced jazz guitarist will also need to know their 9, 11 and 13 chords as well, popular chords in Bossa Nova style jazz. In this series of instructional video lessons for advanced jazz guitarists, you’ll learn how to play these more complex chords, as well as some popular songs that use these chords, like Girl From Ipanema, Blue Bossa Nova, and Georgia ...

All fields of study have their own language. For people interested in learning about microbes, the language can sometimes be downright difficult — but it doesn't need to be. From antibiotics to xerophiles, we have you covered in an easy-to-understand glossary.

As brands and content makers create more augmented reality experiences, the demand for tools to create 3D content grows in kind.

San Francisco-based augmented reality company Scope AR has made building AR instructional content for mobile devices and AR wearables as easy as throwing together a PowerPoint deck, primarily via its WorkLink platform.

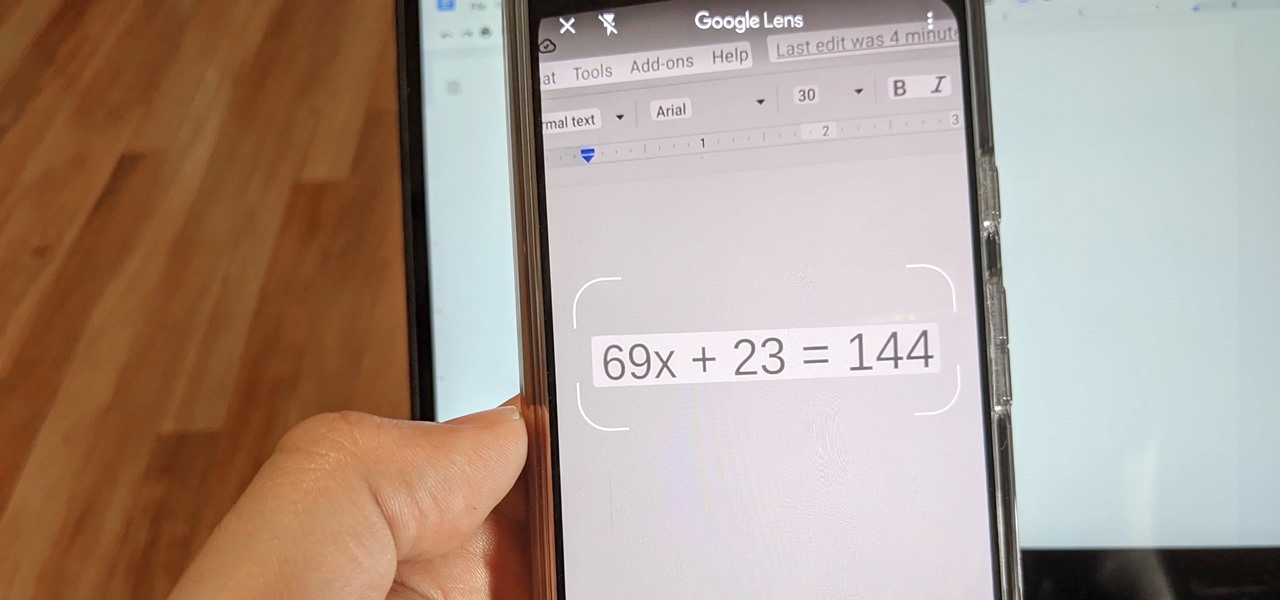
Since launching Google Lens as a a Pixel-exclusive feature in 2017, Google has not only expanded the availability of the tool to Android and iOS, but also built upon its functionality. Now, in addition to translator, tip calculator, personal shopper, and tour guide, Google has added math tutor to the job description for Google Lens.

Your smartphone is likely full of COVID-19 news and coronavirus panic. These are scary days, and there doesn't seem to be any end in sight. If you're having trouble coping with the stress and anxiety the virus brings with it, know that your iPhone or Android device can actually help you, rather than just bring you further down.

When Apple acquired the popular Workflow app in 2017, many were worried that it would either get replaced with something much worse, or just disappear entirely. Thankfully, Apple put these concerns to rest with the launch of Shortcuts. In iOS 13, Shortcuts is becoming more powerful than ever, providing functionality on the iPhone that the original Workflow team could only dream of.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Can lightning strike twice? Niantic is betting that it can with its latest augmented reality game based on the best-selling multimedia franchise Harry Potter.

OnePlus always seems to offer affordable yet powerful tools for videographers of all kinds. The camera hardware itself is crucial, but what's hardware without good software to highlight its real potential? It doesn't matter which version of the smartphone you have, they're all powered by the very same OnePlus camera app.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.

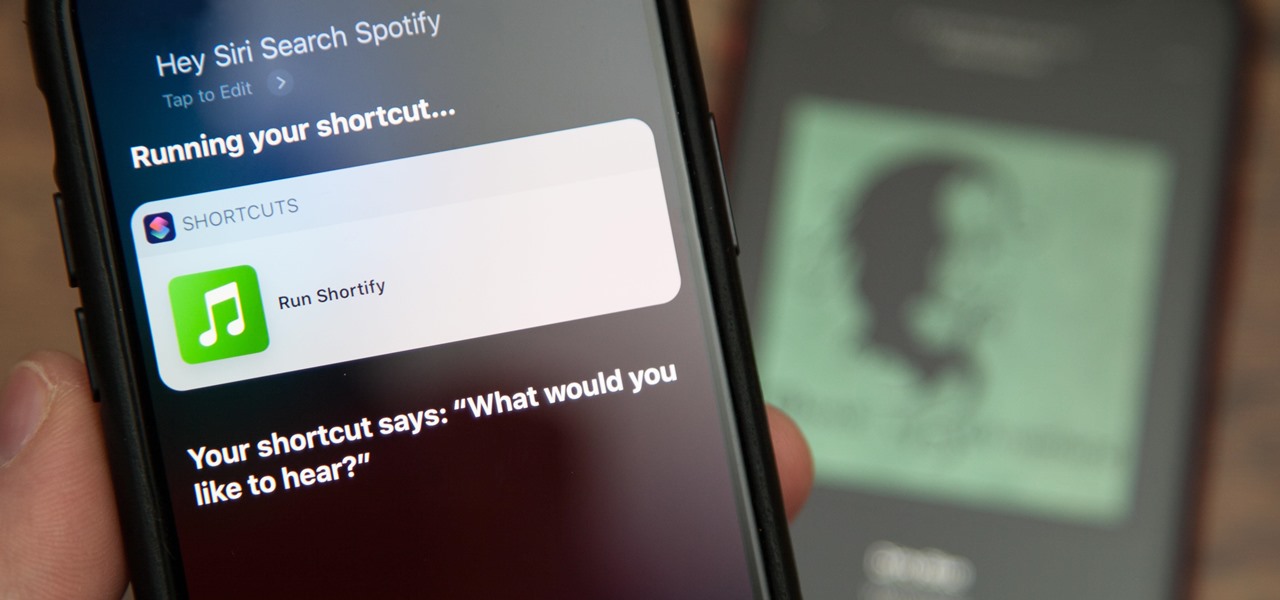
In iOS 13 and later, Spotify supports Siri commands, something we've wanted ever since Siri and Spotify were things. But if you're on iOS 12 still, you're missing out. All you can do is open the Spotify app, then pause and skip tracks with Siri after you start playing a song manually. There is a workaround, however.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.