When you send an emoji from your Android device to someone that uses an iPhone, they don't see the same smiley that you do. And while there is a cross-platform standard for emojis, these don't work the same way as unicode-based smilies or dongers, so not every operating system displays these little guys the same way.

A four-digit passcode is what protects your iPhone, and the sensitive material within it, from strangers or nosey friends. Four digits are the only thing preventing someone from snooping through your pictures and posting them online for the public to see, and that's if you even have passcode security enabled.
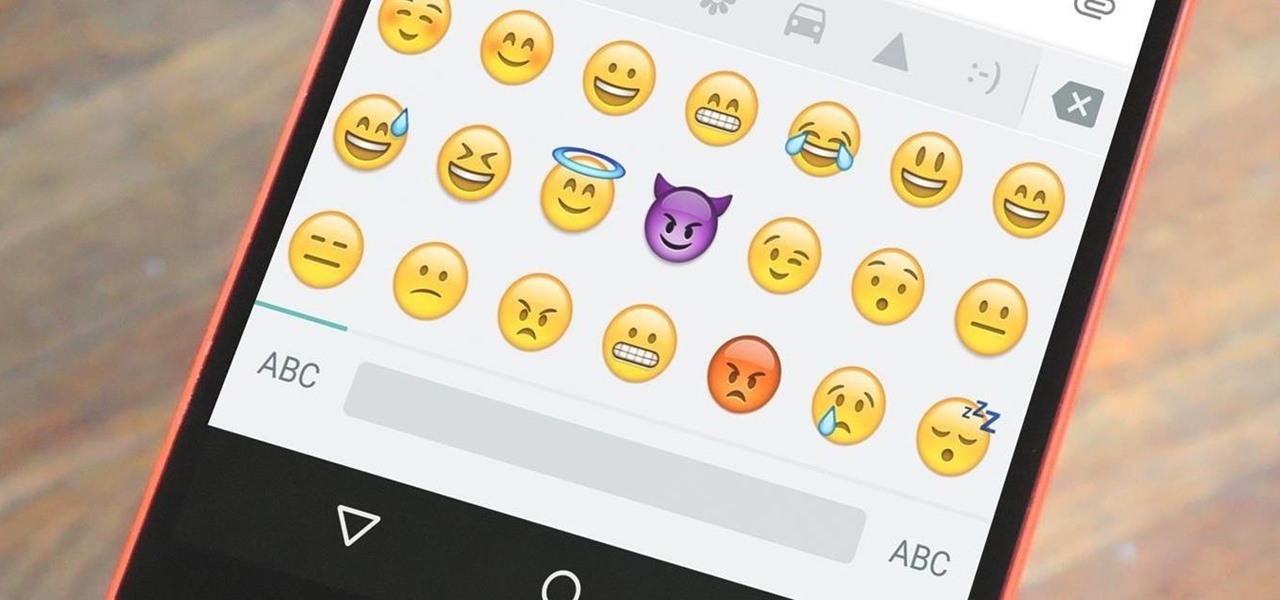
Emojis are a huge part of communication these days. In fact, I'm beginning to think that in a thousand years, historians will come across our then-ancient texts and speculate that we used a writing system that evolved from hieroglyphics.

Ever wanted to communicate with another driver on the road, but just didn't know how? Sure, you could flag them down by waving or honking at them, but that assumes that they're in close proximity, that you have a unobscured path, and that they're paying attention. And if you're in a fit of road rage, flagging them down probably isn't the best idea for either of you.
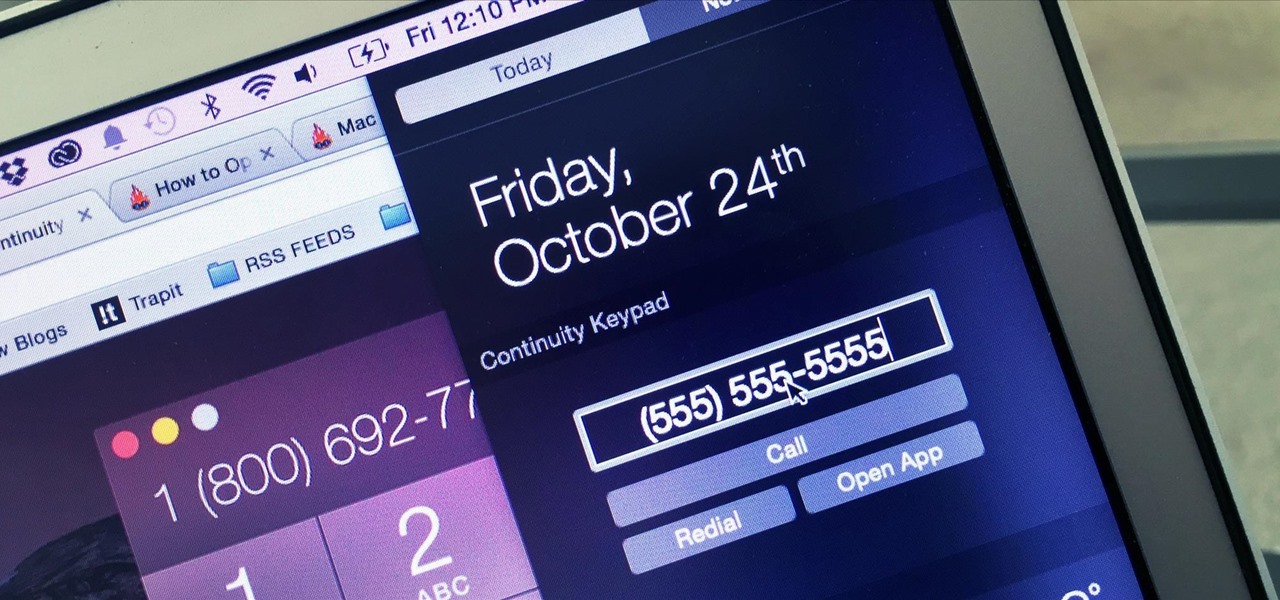
Thanks to Apple's implementation of Continuity on Mac OS X Yosemite and iOS 8, communication is truly a seamless thing. Without even looking at my iPhone, I can message or call friends comfortably from my computer or iPad.

Sometimes, when it comes to Halloween costumes, the easiest ones to make are the best. They require little effort, but can pack a punch and look even more authentic than complex character replications.

We're a little citrus-obsessed, and with good reason: lemons, limes, oranges, grapefruit: Mother Nature really packed those babies with flavor, from peel (which you can zest without special tools) to juice. Now executive chef Amanda Freitag of Empire Diner has come up with a way to make those lemons and limes give up even more flavor by applying a lot of heat.

Does it seem like everybody you know is declaring that they're gluten-free? Some wonder if the number of people with celiac disease are on the rise or if it's the latest fad diet. And it even goes beyond food: now there are beauty products that tout themselves as being free of gluten.

While text messaging has become one of the most frequent ways we communicate with our friends, the missing body language, tone of voice, and eye contact can make it difficult to tell when someone is being dishonest. That said, it's not impossible. There are a number of subtle hints you can train yourself to recognize that will to help you detect written lies hiding in your SMS and iMessages. Here's what you should look out for.

Sprint and T-Mobile have agreed to a $31.6 billion deal that, if it gets through federal regulators—which is far from a sure bet—would create a formidable carrier to really compete against AT&T and Verizon. The deal comes packaged with a $1 billion "breakup" fee that Sprint would have to pay T-Mobile in the event the deal does not go through. After the deal, Deutsche Telekom, which owns about 67% of T-Mobile, would maintain a 20% ownership stake.

Look through the dessert recipes on any food blog and there's a pretty good chance you'll find something with chocolate and peanut butter. It's one of the most common combinations in candy bars and other sweets (not that I'm complaining).

Caramelized onions are one of those ingredients you can add that immediately makes any dish feel a little fancier. They have that delicious savory-sweet combination, they're great in almost anything, and they're surprisingly easy to pull off at home. So why don't more people make them?

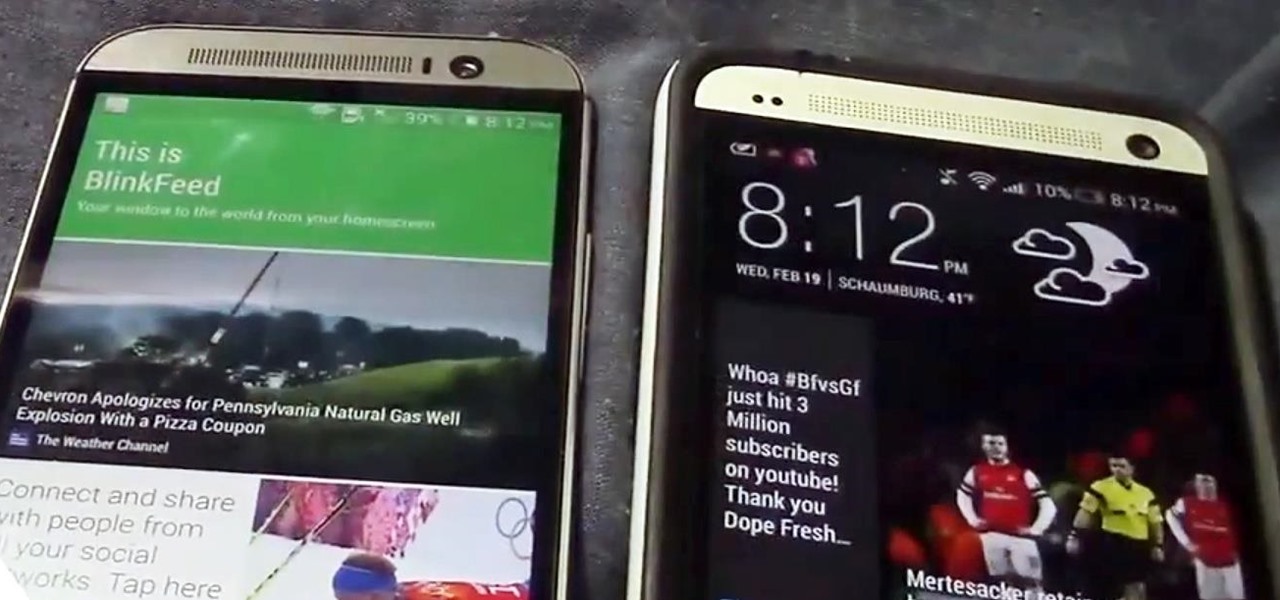
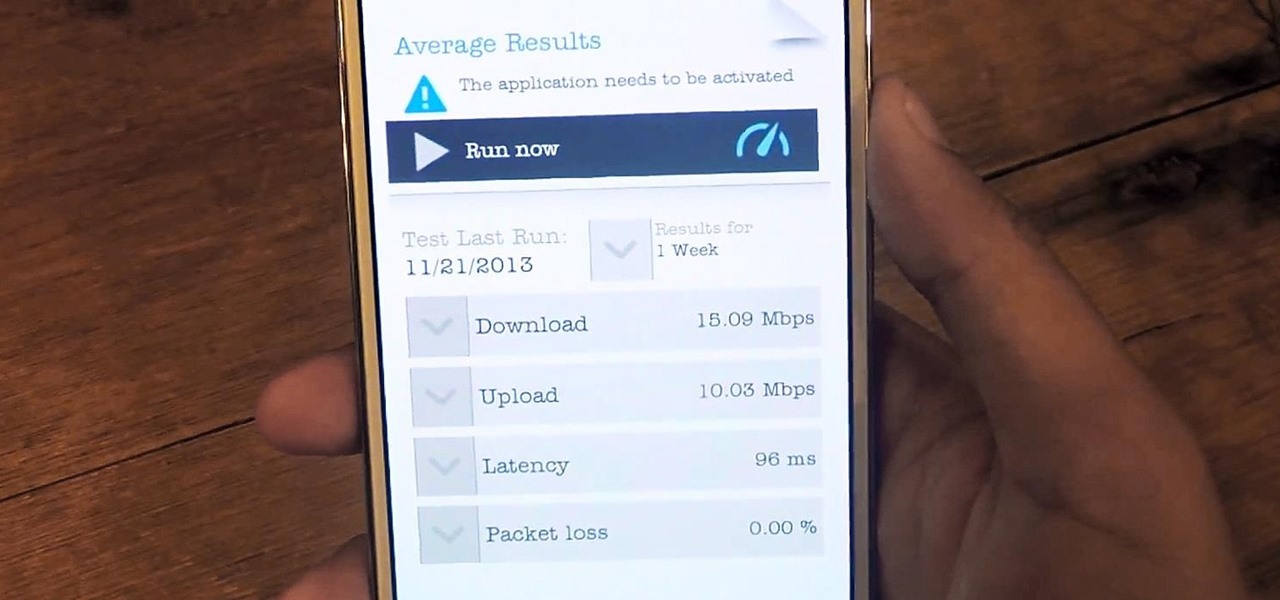
Confirming a lot of what we already knew, now we have a physical walkthrough video on HTC's new flagship, the M8. Or, maybe the "New HTC One", but let's hope that's not the name of the final product. Before we get to the video, here's what we already know:

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

If you look at the label on your favorite processed snack, there's a good chance you have no idea what half the ingredients are. It's nothing new, but with natural and organic foods becoming huge trends, we're hyper-aware of all the "chemicals" we eat.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

Instagram recently released their new Instagram Direct messaging feature in their Android and iOS apps, which lets users share private photos and videos directly with individuals or groups of up to 15 users. However, there are no restrictions on who you can send private photos or videos to.

If you want to raise your children in a Christian way, it is very significant to make them understand what Jesus' sacrifice did for them.

As the protectors of all things good, the Federal Communications Commission is usually busy behind the scenes pissing off Slim Shady, giving out fines for indecent nipple exposure at certain halftime events, and warning the NSA about losing any "confidential" phone information they steal from us.

Communication is the key to any healthy relationship, and when I say any, I mean human and non-human. Previously, one of the biggest culprits for not understanding what you meant was Siri, but now it looks like it has some competition with the new Kinect system, which can control practically everything on your Xbox One—if it can understand you.

Welcome back my precious hackerians. Today i would like to promote an OS which i have been using for the past couple months. I'm not talking about Backtrack 5 or Kali Linux. Something even more promising:

Pringles are just as well known for their cylindrical packaging as for their suspiciously addictive fried crisps. Yes, that's crisps—not chips.

Learn to Zoom to page, drawing, selection, previous, 100% and scale by numerical factor using zoom tool in Xara Web Designer. The zoom to page option is great for when you need to see all the web design elements that are shown on your web page at once.

While the pope himself may not be Steampunk, you might be amazed at what is: the coronation stove. For those who don't know, it's been a tradition for a very long time to signal the election of a new pope (or the lack of a new pope) via colored smoke. More specifically, once the cardinals have all voted for the new pope during the conclave, the ballots are burned in a special stove in the Sistine Chapel, and the smoke is visible in St. Peter's square.

As you have no doubt observed, brothers and sisters do not mate. While they may find one another attractive, they find the notion of sex with one another repulsive. This is because a child produced by siblings has a high probability of sharing the same recessive genes, and recessive genes are often harmful unless coupled with dominant genes.

When it comes to live wallpaper for your Android device, the choices are pretty much limitless. Anything from a planet's elliptical orbit around the sun to a school of fish swimming across your screen are just a click and a download away. With the advancement of smartphones, live wallpapers have greatly improved. What once used to be a bit of snow falling down the screen has now evolved into very complex animations, with some that are even susceptible to your interaction with them.

Do you guys remember those things you hold with your fingers to write stuff down? I think they're called pens, or something like that...

Social media is where we post our thoughts for the world to see, but sometimes a little more exclusivity is needed. And that's where Scrambls comes in.

LEGO has not attempted a blimp, zeppelin, or similar airship since 1999, the 5956 Expedition Balloon which used highly specialized parts. This is unfortunate as these vessels are well and truly part of the pulpy adventure and steampunk scene.

Solving long and extensively complicated equations in grade school was tough to do by hand. Keeping track of which part of the equation to solve first took time, training, and lots of bad grades.

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

Custom ring and text tones are great for knowing who's attempting to contact you without having to actually look at your iPhone. However, this feature is useless when your device is in silent/vibrate-only mode.

Unless you're living in some weird parallel universe where plug-in light bulbs are the norm for household lighting, chances are you've had to unscrew a light bulb every now and then.

Video: . » Iran Threatens to Block Tankers in Response to Oil Import Embargo Alex Jones' Infowars: There's a war on for your mind!.

Not a social butterfly? You can go out into the world while ignoring a particular person or just not get caught up in a conversation with anyone at all. With the use of some distracting devices and a little acting you can be on your way.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

The stuffed pepper is one of the most many-splendoured dishes that southwestern cooking has given the world. No matter what pepper or what stuffing material you use, they are almost always delicious as long as you avoid overcooking them and allowing them to become soggy. Guy Fieri would never let something like that happen, and here teaches us how to make a chorizo and shrimp version that is hearty, complex, and delicious.

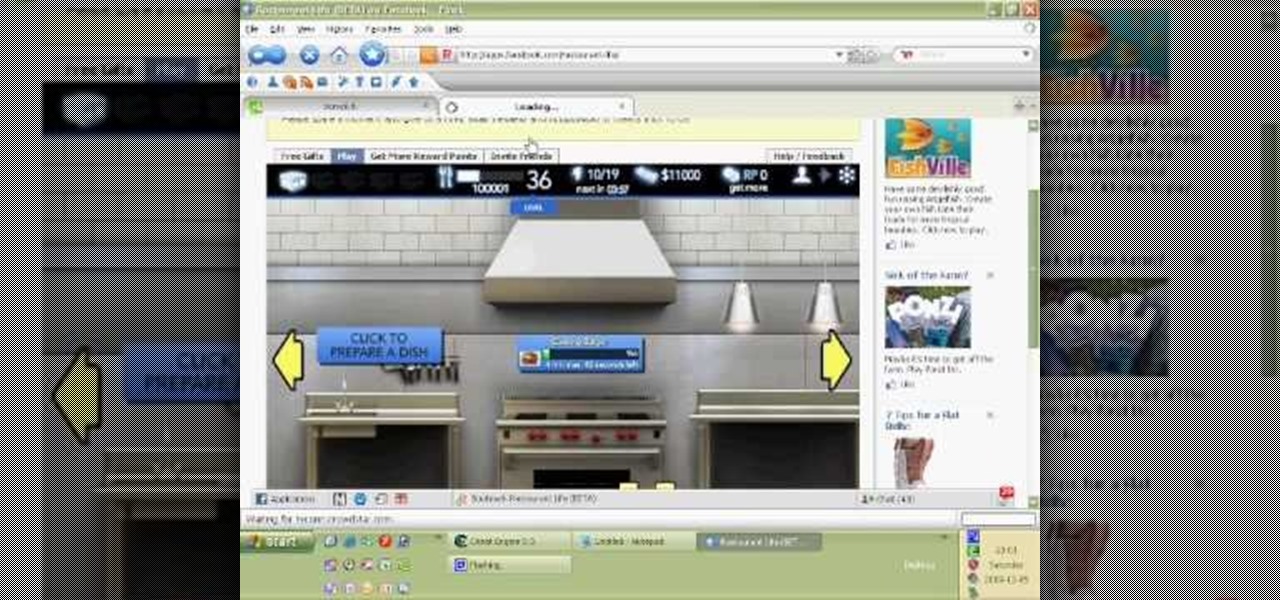
Watch this video tutorial to learn how to level hack Restaurant Life (12/05/09). 1. Open RL and Cheat Engine 5.5, then point CE 5.5 to the process of your browser.

Writing agendas are necessary to keep meetings organized and on schedule. Get tips on writing an agenda from a communications and public speaking expert in this free instructional video series.

This MS Office software tutorial shows you how to use some tips and tricks for the coolest features of Microsoft One Note. OneNote 2007 is great for notetaking during meetings or as a project communication tool at the office. Whatever you may need to keep track of, the tips and tricks in this OneNote tutorial will help you get started.