
How To: Make an Iodine Clock Reaction at Home
In this video, I'll be demonstrating how anyone can make their own iodine clock reaction with simple over-the-counter chemicals.


In this video, I'll be demonstrating how anyone can make their own iodine clock reaction with simple over-the-counter chemicals.

Enjoy hot chocolate during the stifling summer months by putting it on ice. To make iced hot chocolate, you will need:

Make sure and watch this episode as we tackle another heavily requested effect... making someone look blown in half! Jam packed with cheap special effects, Frisbee fun, and a Test Film guest directed by Maniacal Rage!

The SATs are a very valuable college entrance test and could determine if you're accepted or denied to your favorite university. So, once you've learned to ace the SATs and have already taken your test, get your scores as soon as they're out! Don't sit in dreaded anticipation— go to College Board and get your SAT test results now!

Don't you just love Lucy? I know I do, especially that hair of hers. This video will show you exactly how to get that "I Love Lucy" signature hairstyle.
In this video tutorial, Chris Pels will show how to determine what capabilities a user’s browser has when viewing pages in an ASP.NET web site. First, learn how to access an instance of the HttpBrowserCapabilities object from the ASP.NET Request object associated with the web page request. Next, see the different information available in the HttpBrowserCapabilities object such as the type of browser and whether the user’s browser supports JavaScript and Cookies. Then see an example of how to ...

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.
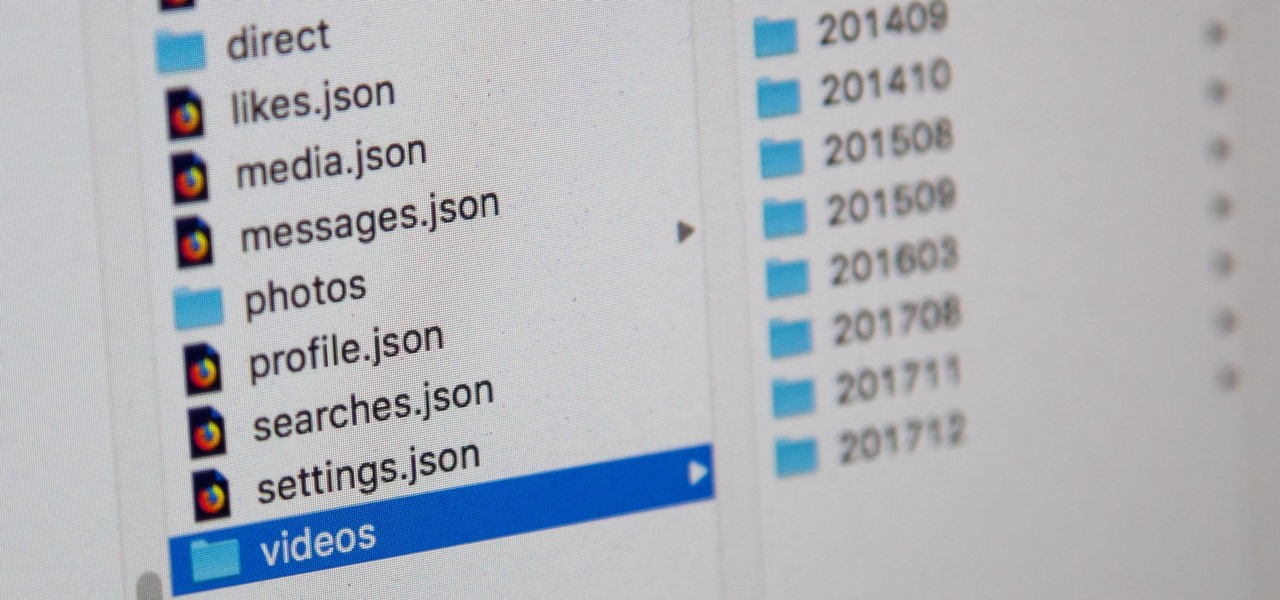
Facebook, parent company of Instagram, has allowed you to download photos and other account data for some time now, but the data request feature is also now available on Instagram to meet the GDPR data portability requirement in the EU — and it's available worldwide, not just in Europe.
While Animal Crossing's emphasis has always been on making friends with the animals that populate your world, each subsequent game following its initial release has stressed relationships with human players more and more. In Animal Crossing: Pocket Camp, making human friends is a crucial part of the process with the inclusion of market boxes, Shovelstrike Quarry, and giving "kudos."

On Wednesday, Scope AR, makers of Remote AR, the augmented reality video conference calling and remote assistance solution, announced that the app is finally available for HoloLens. Next Reality had a chance to talk with the founder and CEO/CTO of Scope AR, Scott Montgomerie, inside this new version of Remote AR.
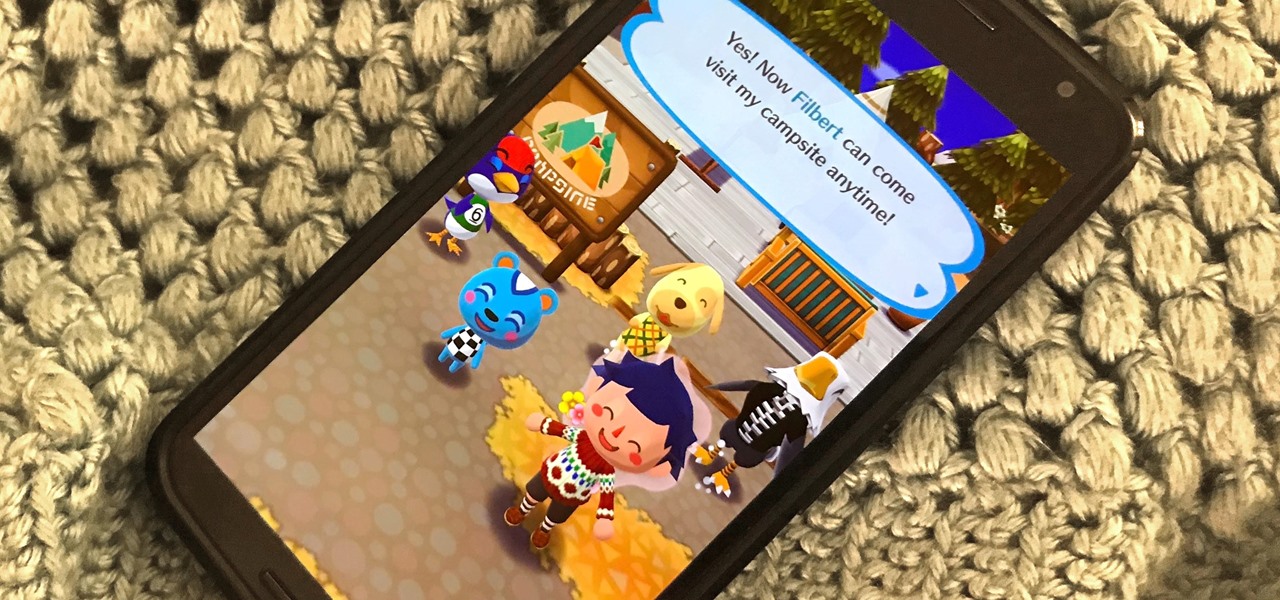
Friendship has always been a staple of Animal Crossing games, and Animal Crossing: Pocket Camp makes no exceptions. Check out this guide if you're interested in how to maximize time with your furry friends.

Even before we are born, our immune system is hard at work. New research shows how the developing fetal immune system takes advantage of the time and opportunity of gestation — in the presence of mom's cells and tissues — to develop a sense of self.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

A group of researchers from Stanford University and Princeton University has put together the largest RGB-D video dataset to date with over 1,500 scans of over 700 different locations across the world, for a total of 2.5 million views.

Koji is a culture made up of a certain fungus (mold) called Aspergillus oryzae, which has been used to ferment rice and soybeans in Japanese, Chinese, and Korean kitchens for centuries. Koji can actually have other involved fungi, but Aspergillus oryzae is the most common, and therefore the names can be used interchangeably. Its end purpose is to enhance the flavor of items like soy sauce, sake, and miso.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

One of my favorite things is finding an easy way to make what is normally a complex dish. Case in point: pasta sauce. Usually its depth of flavor is the result of fresh herbs, shallots, tomatoes, seasonings, olive oil, and a touch of dairy being cooked and added in stages. Long simmering mellows out each component's inherent character and turns pasta sauce into something that is far greater than the sum of its parts.
This video series takes you through every step of building a building in SketchUp and is taken from chapter 4 of "Google SketchUp for Dummies" in case you want to follow along. PART 1 explains how to switch to a 2D view to get you ready to build the floor plan. It's a good idea to have accurate measurements of everything you want to build before starting this project. PART 2 familiarizes you with the tools available in SketchUp to help you create your floorplan. PART 3 shows you how to draw t...

Maybe you're tired of receiving annoying messages from apps or people on Facebook? Why not block them so you don't have to deal with them ever again? Take a look at this guide for information on how to block online games and apps on Facebook from sending you notifications, requests, or other information. You can even stop people on Facebook from sending you event notifications or posting on your page by blocking them too.

Embed Facebook directly into your Internet Explorer or Mozilla Firefox browser's toolbar using this nifty new add-on directly from the people at Facebook themselves. This addon shows you on the toolbar the number of pokes, friend requests, unread messages and upcoming events that you have, in addition to quick links to various sections of the Facebook site. In this demo video, Patrick from Tekzilla explains the cool new features and details.

In this clip, learn how to get amazing amounts of goodies in the mail for free! Kitty, the coupon diva, will show you how to request things like free samples and manufacturer coupons from companies so you can stock pile them and save. Get extra freebies every time you open up your mailbox with these awesome tips.

A cranberry glaze can be used to make your turkey look scrumptously sexy and polished to a Midas glow. The glaze also adds succulent tart flavor to the richness and density of your turkey meat.

We've already highlighted the importance of learning Microsoft Excel from a hacker's standpoint, but it's also just a good skill to have as you'll likely come across the number-crunching powerhouse at school and work, as well as in other areas of your life, such as budgeting.

Communication is an essential skill for successfully launching products. Whether you're developing the latest and greatest app or trying to get ahead of a large data science project, effective communicators are always in high demand.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Businesses that have adopted enterprise-grade wearables for their workforces now have a new option among the multitude of AR productivity apps that can help their team members communicate in AR.

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.

The latest business move by Magic Leap could result in a significant boost to its spatial computing platform's performance and headset design.

A new app for iPhones and iPads gives developers a sandbox for testing their AR experiences and sharing them with the world.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Another entrant into the do-it-yourself AR content creation market has emerged, as Zappar has updated its ZapWorks Studio software to include features for development newbies.
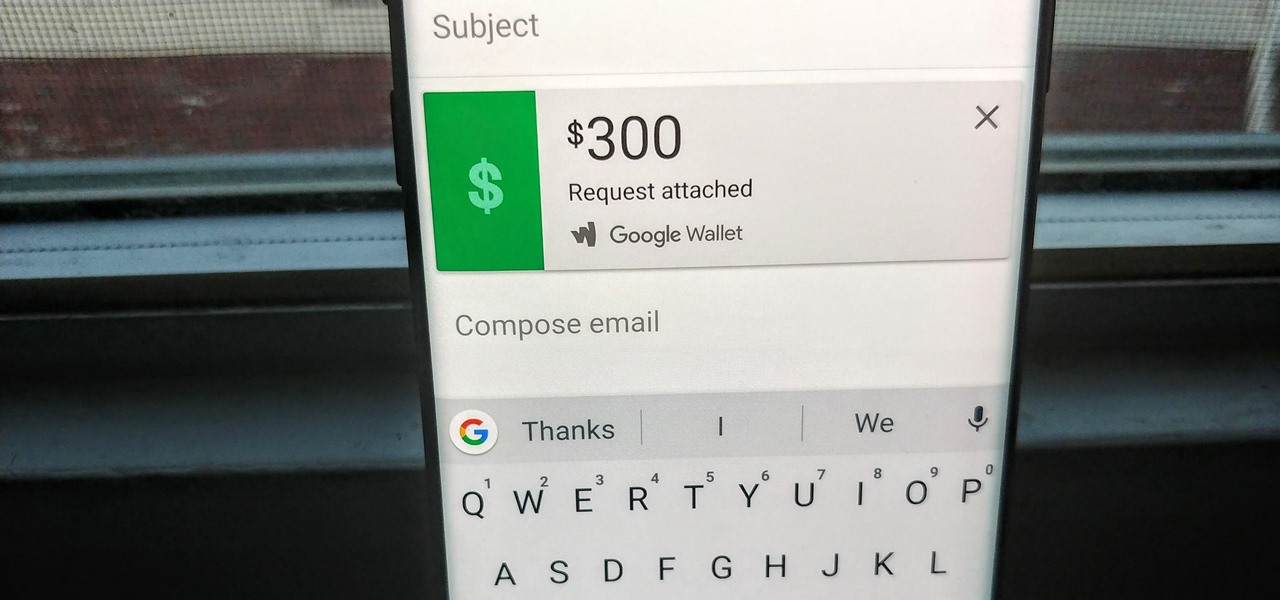
Since its debut in 2004, Gmail has become the go-to email service for the internet at large. Over 1.2 billion people use it, so Google has wisely continued to add features that address the needs and wants of its diverse user base. For US and UK users, one of these new features is the ability to transfer money.

Today at Microsoft Build 2017 in Seattle, Washington, ScopeAR announced that their mixed reality smart instruction development platform, Worklink, will now work with the Microsoft HoloLens in addition to the mobile devices that are currently supported.

While there are many uses for augmented reality in the automotive industry, adoption has been slow. With the plethora of makes and models on the road today and rolling off assembly lines tomorrow, developing and deploying knowledge bases that utilize augmented reality to dealerships and garages can be costly and difficult to scale.

If you've ever built a piece of IKEA furniture, you're familiar with the confusion that some 2D instruction booklets can create. But neuroscience suggests that they're cognitively overloading, as our brains have to translate their basic flatness into physical reality and that's pretty hard to do. Fortunately, augmented reality has come to the rescue.
While Leap Motion and Microsoft are looking to capture natural human motion with cameras, Enflux figured out how to do it with a shirt and pants that feel completely natural.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.
All the files you need are in a free download on DevelopPHP. PHP has to be on a server. It will not run on a local machine. Type your name. There are two variables which show up in the dialog boxes (which are stacked.) You can change the user name. It sets up a URL request and a URL loader and sends some URL variables and are placed into the value of names and pairs. They get posted to the PHP file. Place the URL reference location of where the PHP files are on your server in the line that sa...