It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.
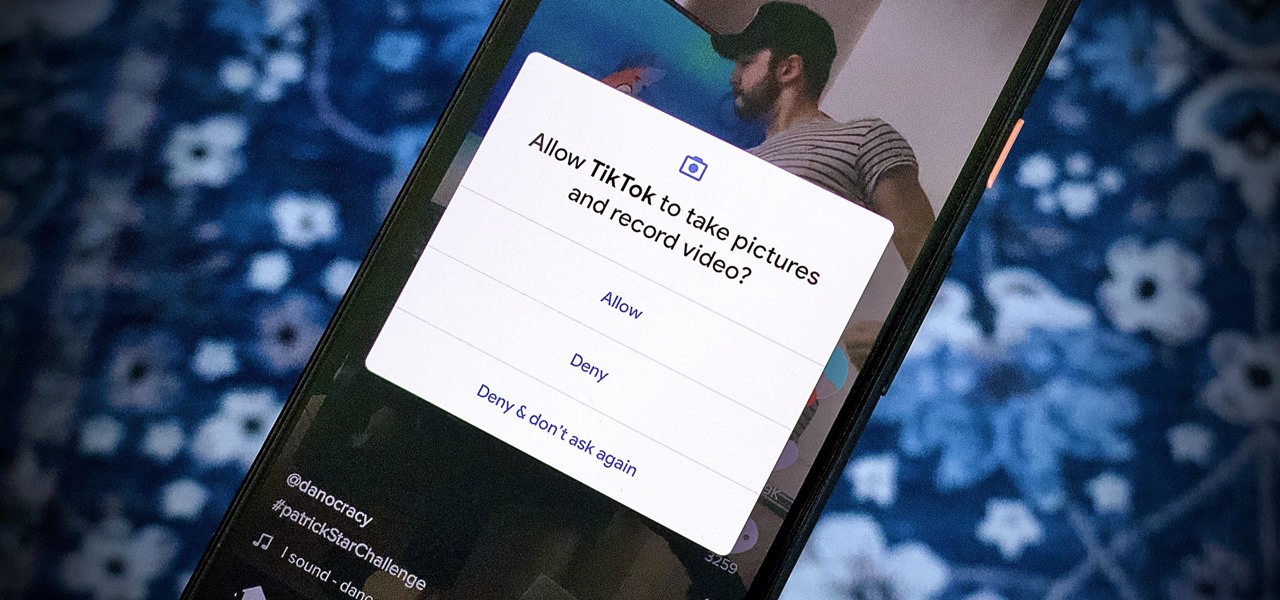
We're thinking more and more about our digital privacy these days. When we first started using smartphones, we'd download apps with reckless abandon, allowing permissions lists as long as novels in order to play free games. Now, we know that apps have access to things like our cameras and microphones, even when they shouldn't. Luckily, taking away these permissions is easy.

Augmented reality's status as a new storytelling medium has already led to the reinvention of filmmaking and journalism.
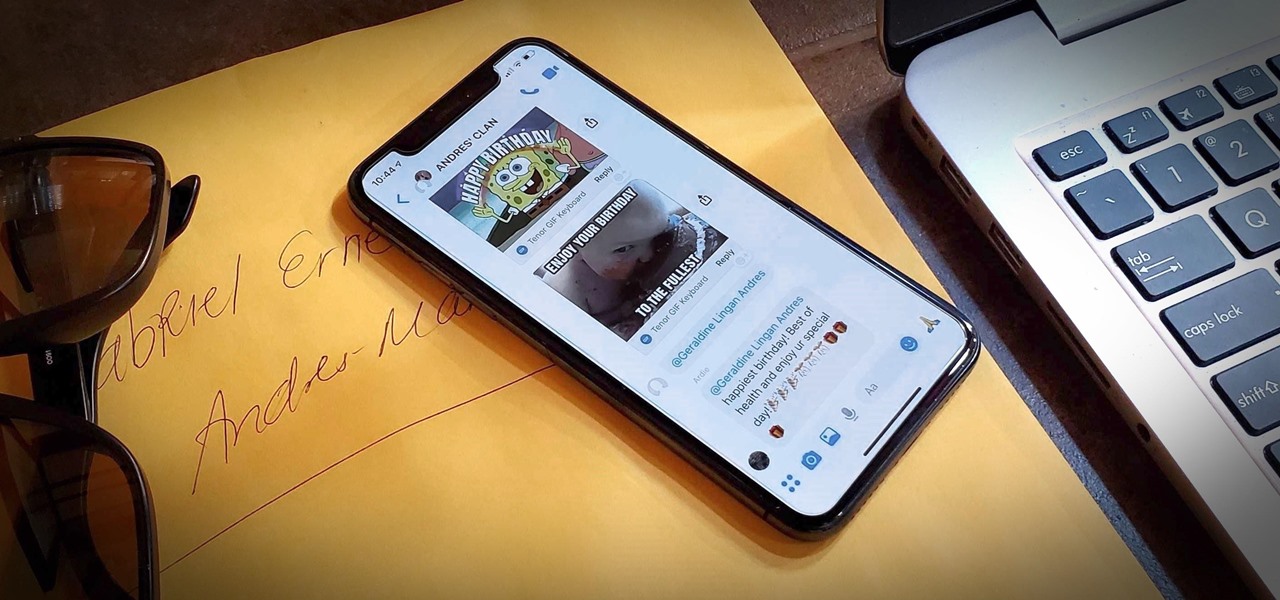
Group chats in Facebook Messenger can devolve into outright noise pollution as people chit chat randomly and bombard you with distracting notifications. Unfortunately, leaving the group outright alerts everyone inside, so if you want to get out of the thread unnoticed, what exactly can you do?
Apple's iOS 13 for iPhone includes new features in Safari that make browsing the web a little bit better when compared to iOS 12. Some changes are small while others add functionality that just wasn't there before. Plus, there are more security enhancements.

For Snapchat users wondering if that selfie is ready to send to their crush, independent Lens Studio creator Andrew Mendez created a handy tool called the Smile Rater.

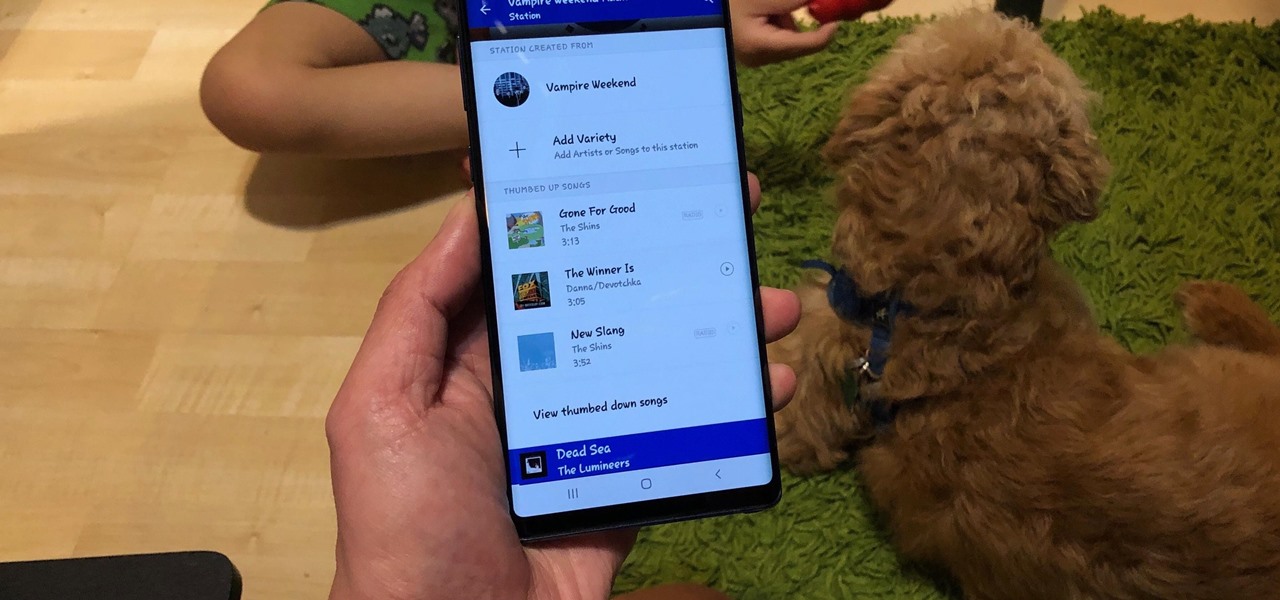
Pandora has a simple rating system that works by hitting either the thumbs-up or thumbs-down icon on a track that's playing on your station. If you choose the former, the song you like along with others similar to it will play with more frequency, while selecting the latter will prevent that song and others like it from playing in your station moving forward.

As the tech world patiently waits for the advent of mainstream consumer smartglasses, Google is content to stick to the business world (for now).

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

The legal drama framing the closure of Meta Company continues even after the company's assets have been sold to a new owner.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

Intel's RealSense family of depth tracking cameras has a new addition with a different set of sensory capabilities.

We are in the midst of a mini-boom for communications tools designed for augmented reality headsets, with the introduction of Avatar Chat and Mimesys for Magic Leap One and Spatial for the HoloLens within the last few months.

Designing and manufacturing waveguides for smartglasses is a complex process, but DigiLens wants us to know that they have a software solution that partially solves that problem.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

Occipital's initial augmented reality module, the Structure Sensor, gave iPhones and iPads the depth-sensing abilities of the HoloLens. Now, the company's latest product promises to do the same for Android devices, as well as augmented reality and virtual reality headsets and other devices.

Election Day is like the Super Bowl for network and cable TV news, so ABC News is breaking out the big guns with a new augmented reality experience to win over eyeballs of viewers.

In the waning days of October, at the Innovation Tokyo 2018 conference, attendees got their hands on some of the new augmented reality experiences that Niantic is working on through its Real World Platform.

Augmented reality productivity software maker Upskill has expanded the reach of its Skylight platform with support for Microsoft HoloLens.

While many of the latest content partnerships announced by Magic Leap appear to lean towards entertainment and gaming, a new partnership with medical technology provider Brainlab has Magic Leap getting down to more serious business.

One developer has taken the formal name of the Magic Leap One: Creator Edition quite literally with an app that enables users to create a custom universe in their own living room.

Four months after unveiling the latest productivity apps for the HoloLens, Microsoft now has a series of compelling real-world use case videos showing how the augmented reality device and its apps are helping oil giant Chevron.

Not content to let NFL's official pizza sponsor corner the market for feeding football fans, 7-Eleven has taken a page out of Pizza Hut's playbook with a promotional augmented reality game.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.

Continuing to take the steps necessary to reign supreme among the top game engines of the world, with a steady stream of major updates, enhancements, and new features, the team at Unity are keeping the user base in a regular state of surprise. At this rate, it's almost like Christmas every few days.

After receiving many requests for the feature, Signal introduced read receipts last year to its mobile apps. However, some users don't like the idea other people knowing when they've read messages. Luckily, Signal lets you disable this feature and reclaim a little privacy.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

French manufacturer Renault Trucks is looking to the HoloLens to improve quality control processes with its engine assembly operations.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

This week, Samsung officially kicked off the Oreo Beta Program for the Galaxy S8 and S8+ in North America and several other markets. The full list of changes is quite substantial, so we'll be running through them in a series of posts detailing what's new. First up, the Galaxy phones inherit notification channels from Android 8.0.

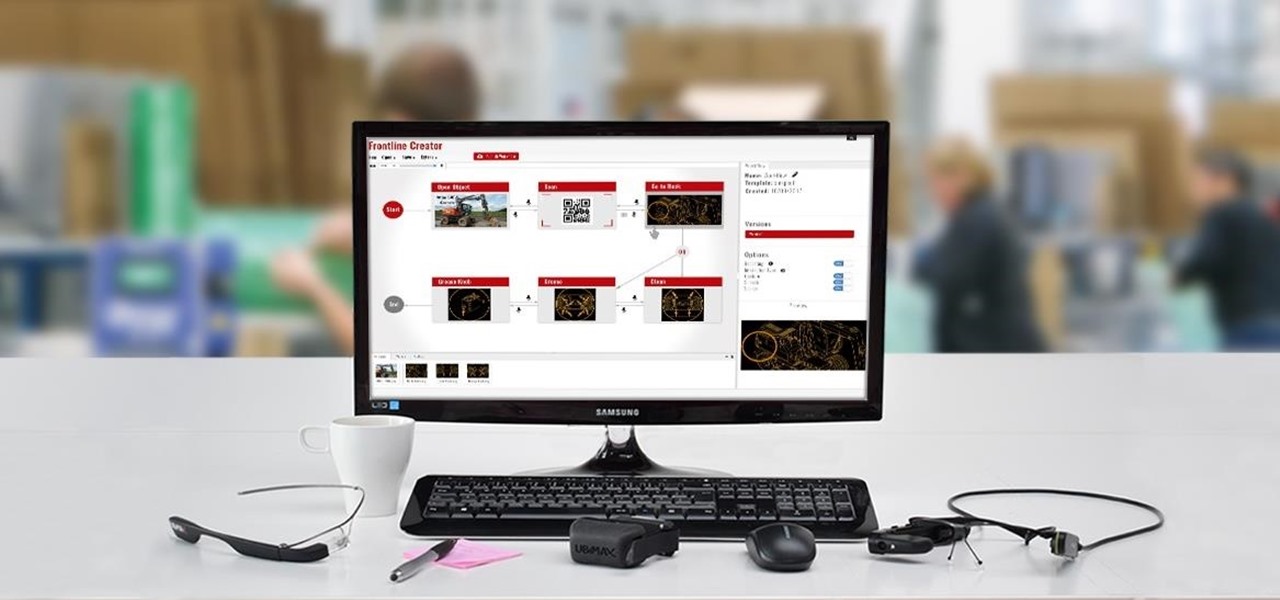
Augmented reality software provider Ubimax unveiled their graphical authoring and publishing tool for their Frontline enterprise platform to attendees at Augmented World Expo Europe today.

When it comes to streaming your favorite movies and TV shows, there aren't many media players that are better than Kodi. With its fast performance and easy-to-use interface, it is definitely one of the best options. But what really sets it apart is its ability to add functionality.

For as long as 14,000 years, the First Nations people of the Heitsuk Nation have made their home along the Central Coast of the Canadian province of British Columbia. Among the territory's inlets, islands, rivers, and valleys lie a clay deposit on the north side of Kisameet Bay, near King Island. For as long as most can remember, the tribe has used the clay as medicine. Now science says microbes that live in that clay may have important antibacterial properties.

3D modeling can be a long drawn out process. If you are a developer or programmer without 3D modeling experience, this process can be daunting, to say the least. This often leaves developers hunting sites like TurboSquid or the Unity Asset Store for free temporary models at the very least, or often times buying final models that don't quite fit their needs.

Recently released accident reports by the state of California's Department of Motor Vehicles show humans did a lot of dumb things to cause accidents with General Motors' (GM) Cruise Automation driverless vehicles in San Francisco this year.

Flu vaccines can help prevent us from getting or suffering the most severe effects of the flu. But, each vaccine only protects us from three different strains of the flu. If we don't have a vaccine against all types of flu, it leaves us open for an epidemic with a flu virus we didn't expect.

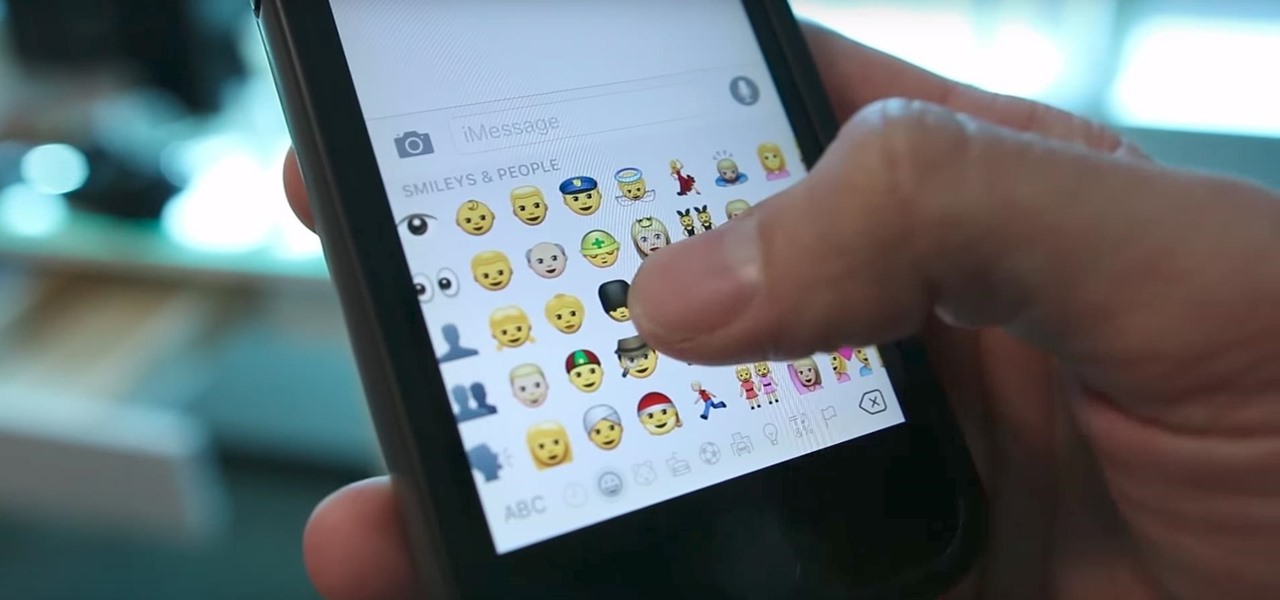
As we all know, and certainly have marked on our calendars, it's World Emoji Day! Considering that over five billion emojis are sent daily on Facebook Messenger alone, emojis deserve to be celebrated, and Apple's doing just that. On this monumentous day, the tech giant is gifting us all with images of its newest emojis. From dinosaurs to headscarf-clad women, the releases are sure to please emoji fanatics throughout the world.

The Chinese government's tight restrictions on gathering data by foreign firms for 3D mapping, the lifeblood of machine-taught driverless systems, could at least slow down access to the market by Waymo, Tesla, General Motors (GM), Ford, and other players hoping to make inroads there.