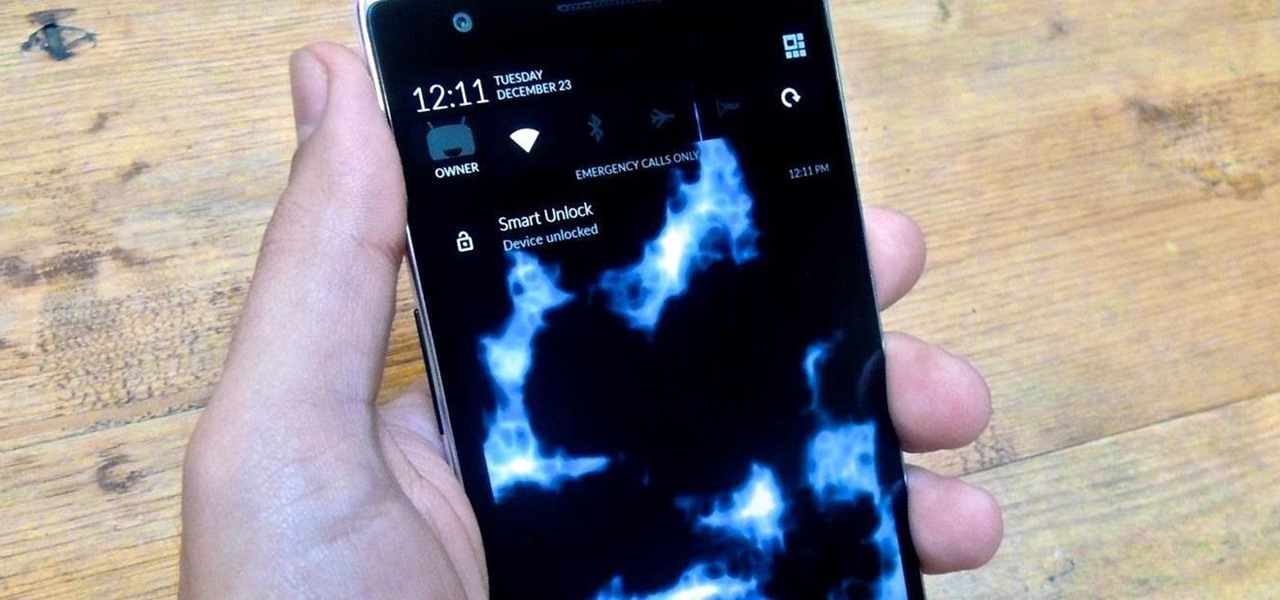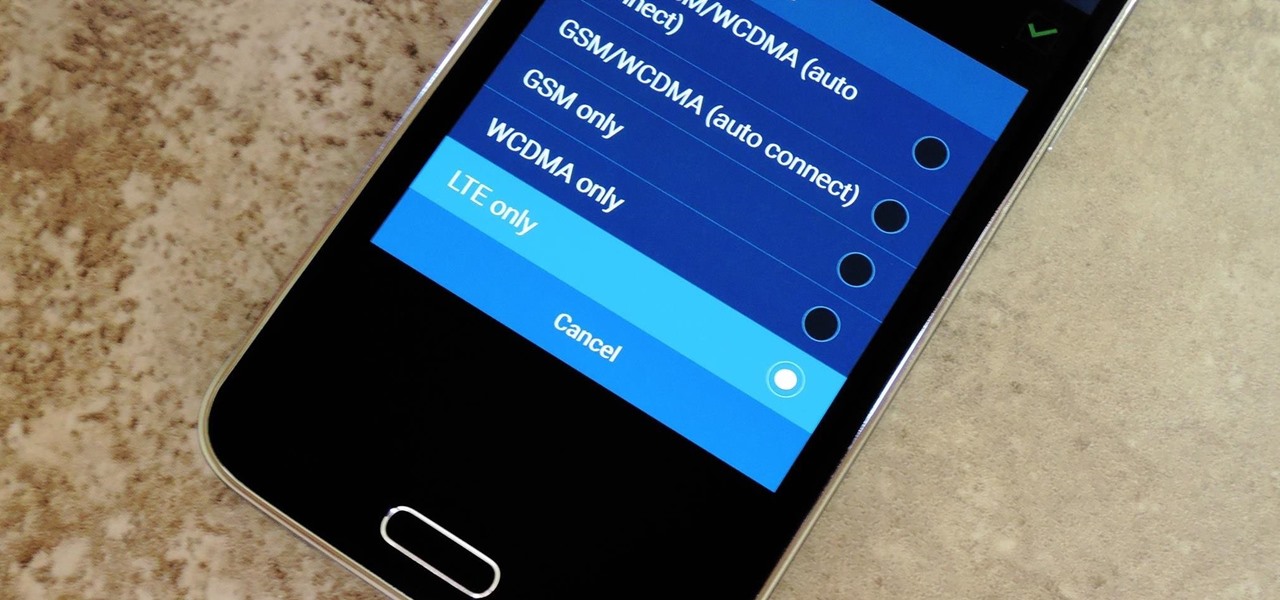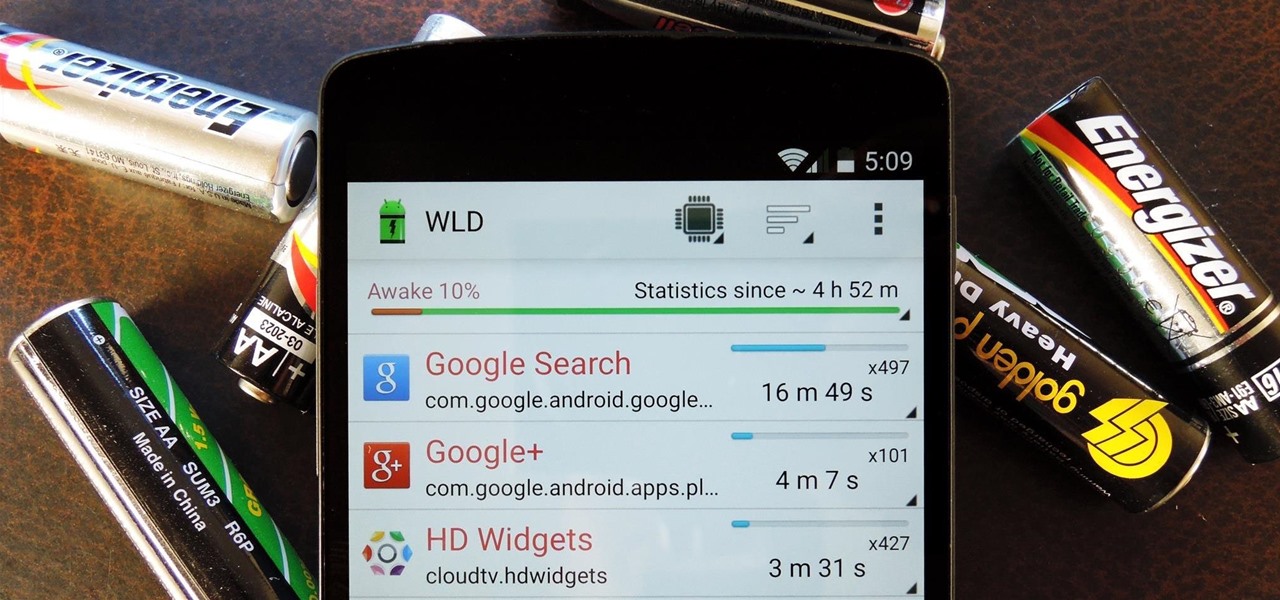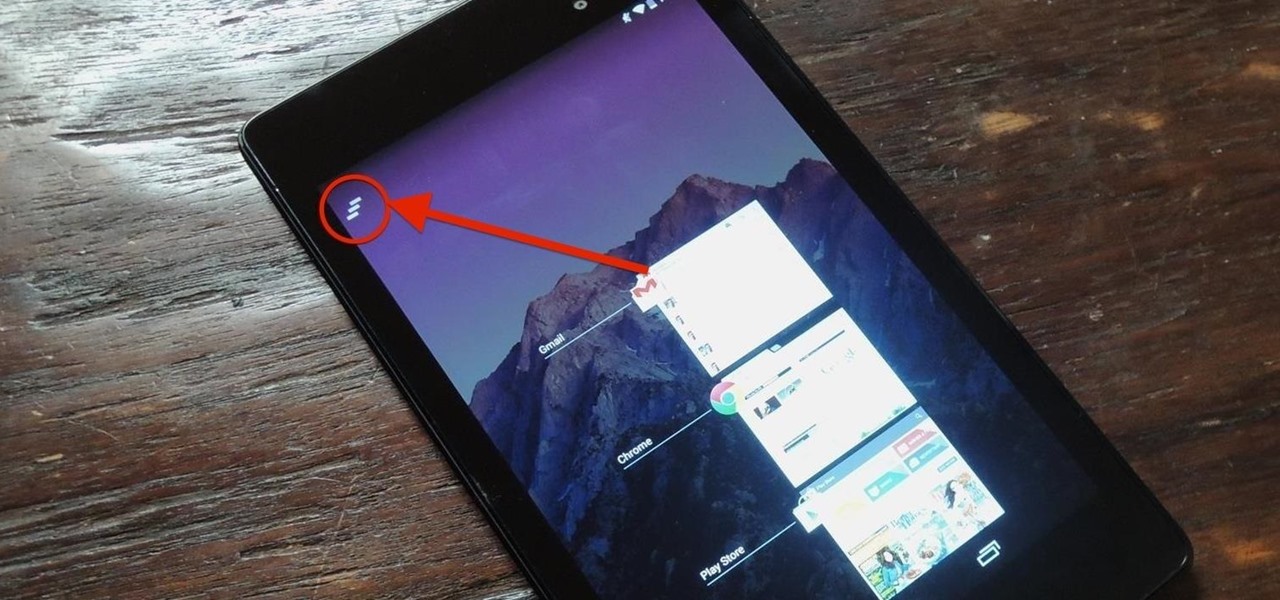
Android Lollipop has an awesome feature called "Battery saver" mode that reduces power consumption through various tweaks in order to squeeze in an extra hour or two of standby time when your battery is running low. It does this by disabling background processes as well as location services and transition animations, so the phone is essentially running at half-throttle.
Looking back at my childhood in the '90s, I can't help but feel like I was deceived. Movies that took place in the "future," like in the year 2015, would showcase awesome technology. You know, self-driving or flying cars, hoverboards, and virtual displays controlled with hand gestures—so where are they?!

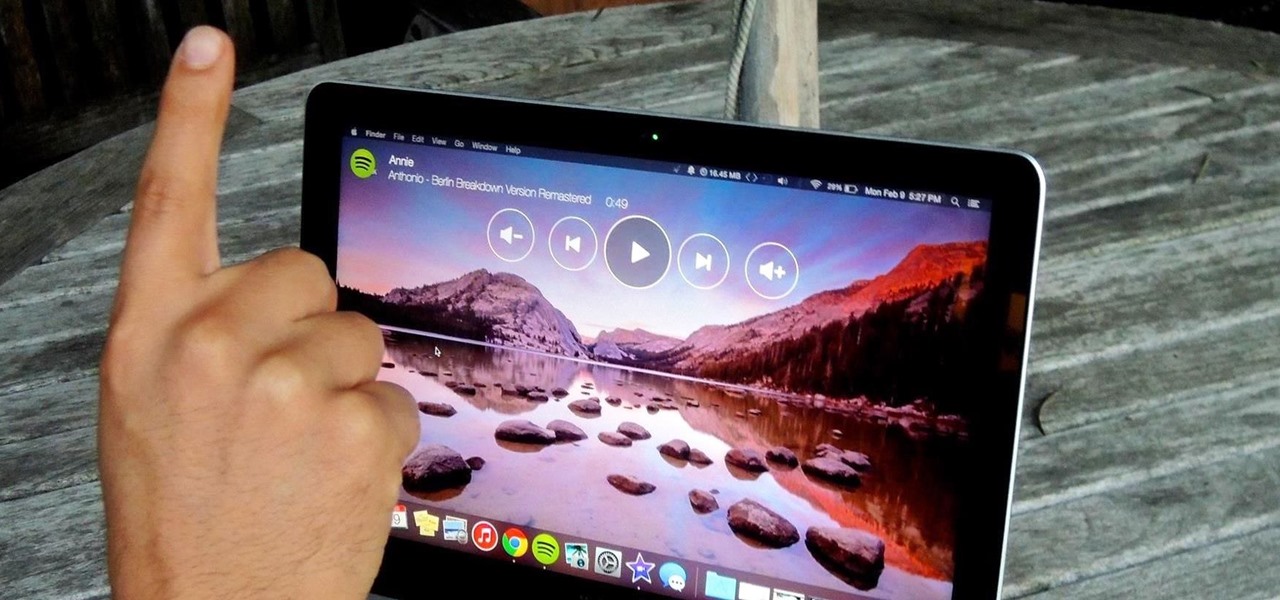
Using shortcuts to control the playback of your music on your computer makes life just a little bit easier. Instead of needing to open up an app, we've shown you how to use keyboard shortcuts, a Notification Center widget, and even Siri to control music on your Mac. Now we're going to show you how to use your iPad, iPhone, or iPod touch as a remote control.
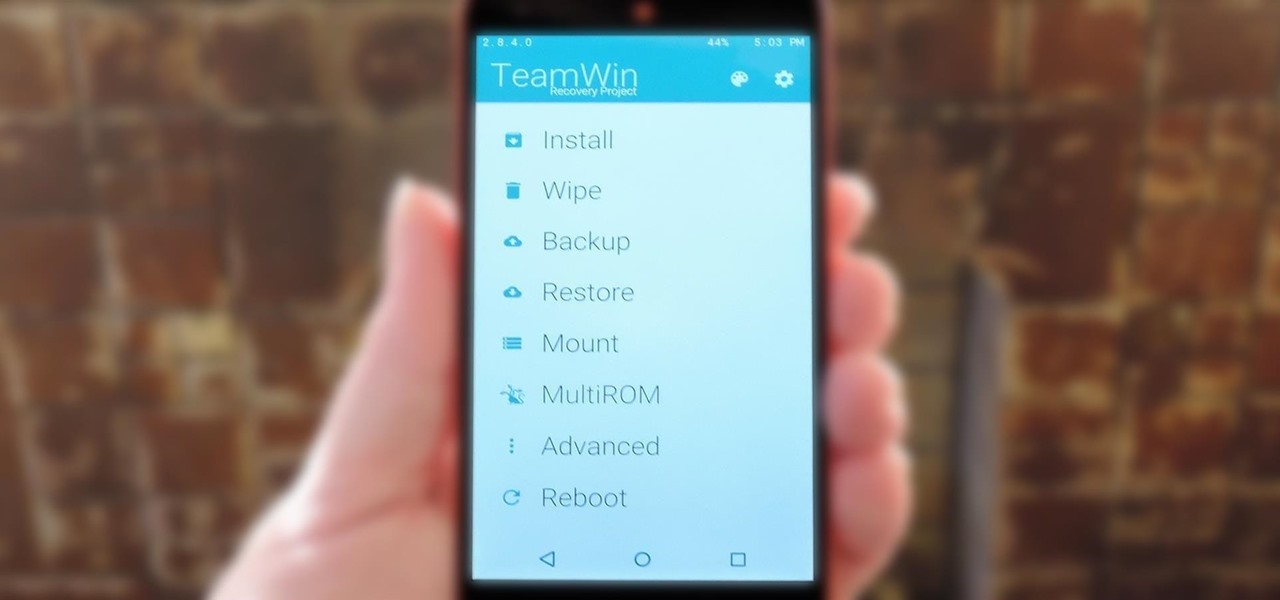
TWRP is hands-down the best custom recovery out there. Its interface, on the other hand, is... well, let's just call it utilitarian. The guys over at Team Win made sure that their product was robust, functional, and easy-to-use, but they didn't put a tremendous amount of effort into polishing the looks.
Getting caught using your iPhone at school or work (when you're using it for personal reasons) can be a little bit embarrassing. Even worse, it can be detrimental to how you're perceived by your teacher or boss. But sometimes you just have to beat that next level of Candy Crush, view a risqué photo on Snapchat, or send an important WhatsApp message.
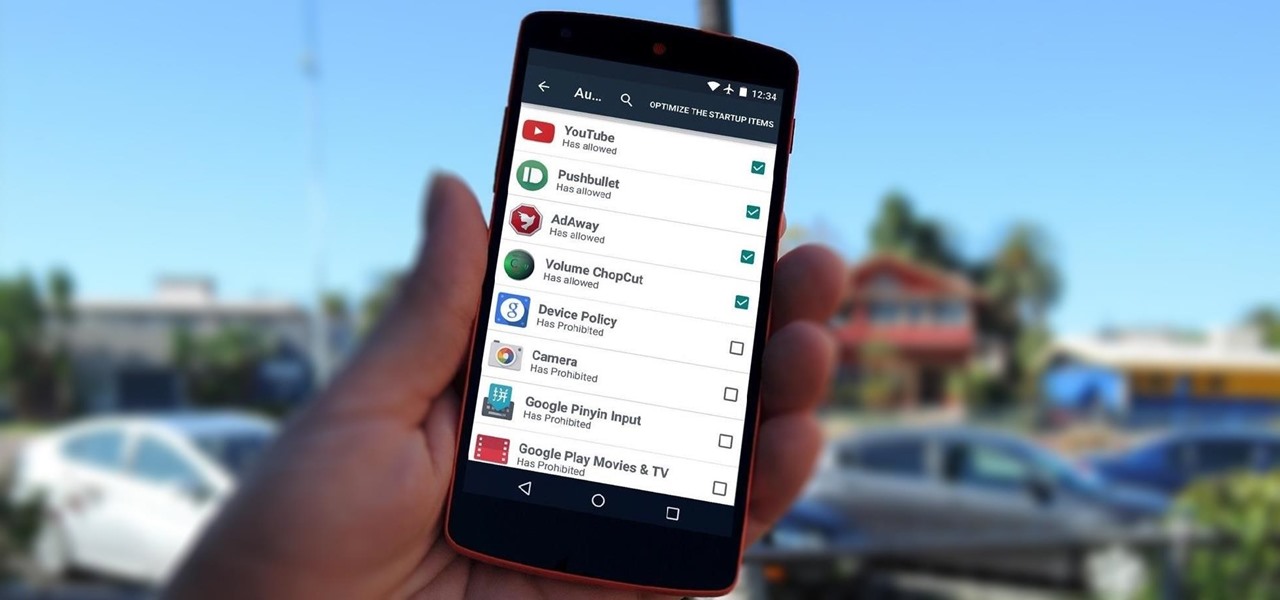
By default, any app that requests a certain permission can run automatically as soon as you start your device. Since Android doesn't offer a granular permission control system like iOS, this gets lumped in with all of the other permissions that you have to accept when you're installing an app from the Google Play Store, and you effectively have no choice in the matter.

OnePlus One's CyanogenMod firmware comes packed with personalization options that standard Android devices could only achieve with root-level access. By simply entering the Settings app, OPO owners can make changes to their lock screen, status bar, and notification drawer, as well as apply themes and gestures to make their device a little more customized.

When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.

In places like underground bars or national parks, your phone's Internet service is sure to slow down to a very sluggish pace, making it difficult to surf the web. Or worst case, data will be non-existent, leaving you with only low-level network support for calls and SMS text messages.

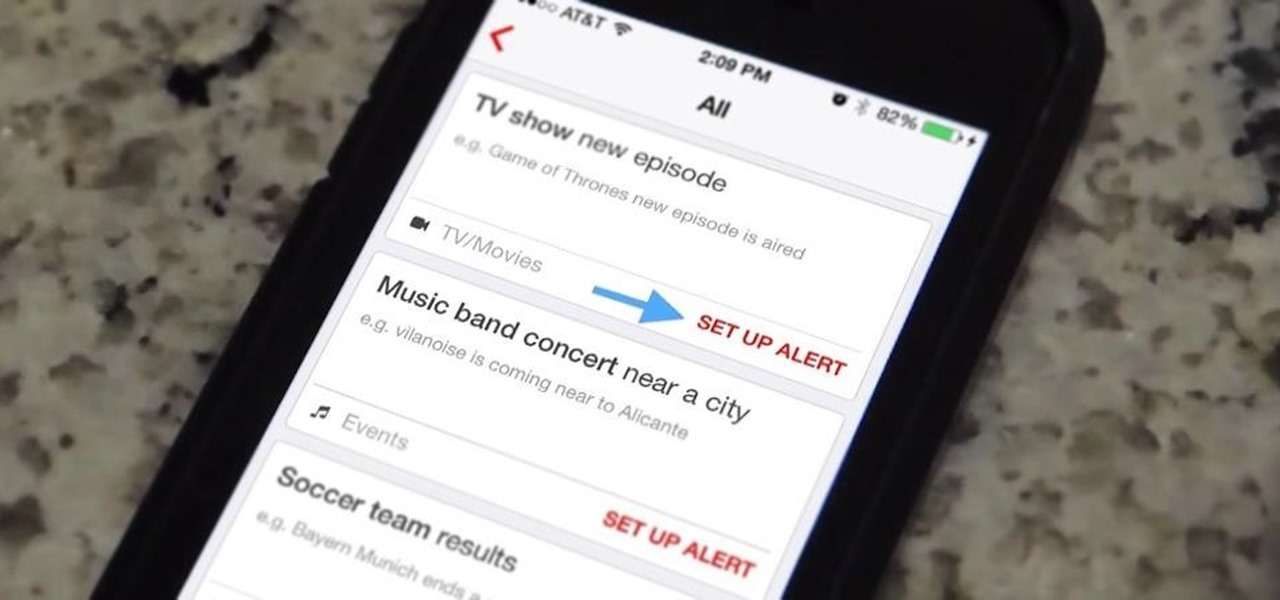
While it's not too hard to remember to watch your favorite TV show every week, it's almost impossible to remember to watch all of your favorite shows. Add on to that sports games, live music events, and new film releases and you'll find yourself in a disorganized mess with a lot of missing out.

Google's Android L developer preview has given Android a more refined look, with developers excited to update their apps with the new Material Design UI. While some apps are slowly getting updated, QKSMS (QK for quick) is a 3rd-party text messaging app that was built with Material Design in mind.

It's becoming more and more apparent that Siri continually drops the ball when it comes to lock screen security. In the past, Siri was exploited in iOS 7.0.2 to send messages without needing a passcode. Then in iOS 7.1.1, Siri was use to bypass the lock screen again to access contacts, make calls, and send emails and texts.

The updates keep coming for iOS 8, and we've got our hands on the developer release of iOS 8.1, currently in beta, which was released shortly after the iOS 8.0.2 update (and 8.0.1 failure) for iPad, iPhone, and iPod touch.

Now that you've updated your iPad, iPhone, or iPod touch to iOS 8, there's a lot of cool new things to explore. If you felt a little overwhelmed from all of the detailed information available in our Coolest Hidden Features of iOS 8 post, then I've got a simple breakdown of all of the new features available with quick links to their walkthroughs and pictures, if available. Watch the short video roundup, or skip below for the list.

While the majority of photos taken on phones are used for personal reasons, mediums like Instagram and Flickr offer a means to show them off to the world. But those pictures of your brunch or beach day can actually go beyond that to make you some money.

Even with the highest-tiered data plan available, there are times that your phone or your carrier might downgrade your connection to 3G or even lower. This usually occurs when you've made a phone call, or you've switched cell towers while traveling.

Android uses a set of permissions that apps can request to perform certain actions, and you're notified of these permissions each time you install an app. The problem here is the fact that you aren't given any built-in way to deny apps these permissions (although Danny just showed a workaround for this).

Unlike the Galaxy S4 and other Samsung devices, the Nexus 7 doesn't have a Clear All option in the recent apps menu. It's a highly requested feature, as it cuts down the time required to go one-by-one swiping each individual app (you can't swipe away multiple ones at the same time).

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.

When I'm showing off my HTC One, the first thing I do is unlock my device and say, "OK Google". It may earn me a weird look or two, but in the end people are amazed by the voice recognition and automation of the Google Now Launcher.

Update: April 24, 2014 Looks the the one day availability was a precursor to a wider launch, as now anyone can buy a pair of the Glass Explorer Edition without needing an invite. Check out Google's Glass Shop for some easy ordering, still with the $1500 price tag.

If you've never played Cards Against Humanity, it's time to get initiated. Originally funded through Kickstarter, the free to download card game is basically an obscene version of Apples to Apples.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

No matter how much of a gamer you are, typing with your PS4 controller is a bitch. Let's just be real. Having to move left, then right, then down, for every single letter can make writing a message very time consuming; so much so that I usually avoid messaging altogether.

Change is something everyone needs every now and then. President Obama used it as his campaign slogan and adult movie stars use it to hide their real identifies. Change is in itself versatile. You never want to have the same thing day in and day out, and that's why us Android users appreciate the massive amount of customization available.

Anyone who is familiar with Linux knows that to use your OS to the max, you will need to use the terminal every now and then. Whether it is to install a package or update the system or even delete a file.

With iOS 7, Apple is finally fighting back against spam, offering the option to block certain phone numbers from sending you text messages or iMessages (plus, phone calls and FaceTime too).

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

While the majority of America was watching the Super Bowl yesterday, the crew over at the evad3rs was finishing its work on their untethered iOS 6.1 jailbreak called evasi0n. Well, the wait is finally over!

It only takes a minute for something well intentioned to turn into something sinister. Facebook created 'memorial pages' as way for friends and family to share their thoughts and feelings for those that are no longer with us.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

Most of the time, asking to borrow someone's car will elicit a really long string of excuses. But unlike letting your buddy use your car, which usually gets you nothing more than an empty tank, GM has found a way to make car sharing beneficial for everyone involved. If you're one of the 6 million people who have a GM vehicle that's connected to OnStar, you're in luck: according to an OnStar employee, you can make up to $1,000 a month just by letting other people rent out your car when you're ...

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

Archie Leach. It just doesn't have the same ring as Cary Grant, does it? Marriage, divorce, or just dislike of the name your parents gave you – all are reasons to follow these steps toward a new name.

This series of videos shows you how to create string art. This is a good project for kids or adults as it can go from very simple designs to very complex ones.

The ability to stay connected online regardless of your environment is incredibly valuable. Being able to access the internet during a blackout, check your messages while camping, or get in contact with emergency services while you're out in the middle of nowhere can be the difference between a brief inconvenience and prolonged suffering. The DuoTurbo 4G LTE Mobile Hotspot with Complimentary 9 GB Data can give you that easy, constant connectivity, and right now it's on sale for $152.99 — 10% ...

Learning to code is difficult, particularly if you're doing it alone. While coding may be among the most valued job skills in many markets, the education is sometimes inaccessible.