Complete silence or a non-stop Pandora playlist? People are often divided on what type of work environment they prefer. Whether you're a frequent loud music listener or you can't stand any kind of background noise, chances are you're pretty set in your ways.

Okay, it's true: even the highest quality instant coffee is never going to replace really good fresh beans (and properly cleaning your coffee maker) when it comes to creating a great cup of joe. However, instant coffee does have all kinds of uses in the kitchen, as the smart folks over at Reddit observed.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

Butter can be even more delicious than it already is. While that may be a shocking claim, it's most definitely true. Many new cooks and even seasoned chefs don't realize this, but the few minutes it takes to do these things will pay you back exponentially when it comes to that buttery taste.

Just what are probiotics and why are they so good for you? Probiotics are "viable microorganisms" that can confer lots and lots of health benefits if they reach your intestine while they're alive. You may have heard them described as "friendly bacteria."

Journals are a great source of hilarity and embarrassment, detailing everything from your elementary school crushes to those super awkward middle school dances. While rereading your old hand-scrawled entries might make you cringe, that old journaling habit could benefit you as an adult.

The Spanish and Portuguese introduced many things (some desirable, some not, depending on your POV) to Mexico in the sixteenth century: Christianity, language, and lots of flora and fauna.

"Does bottled barbecue sauce even taste that bad?" a friend of mine asked. Well, truthfully, no. But it also doesn't taste that good, especially if you've had truly great barbecue or even your crazy uncle's homemade sauce at a holiday cookout.

Even though I often end the workday exhausted and just want to wrap rotisserie chicken parts in a store-bought tortilla and shove it in my eating hole, I generally try and take a couple of minutes to warm up said tortillas before I begin my meal. But if you're starving, do you really need to take the time? Do warm tortillas really make that much of a difference?

As a species, our cells are designed to use sugar for energy. Is it any wonder that as humans evolved, we grew to love the taste of sugar?

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Many of us experience highly emotional "freakouts", so to speak, more often than we'd like. Weather you experience them personally, or via your loved ones, it can be very difficult to think rationally during an episode, and for some people it can take quite a while to calm down.

2 + 2 = 4. That's about as much math as I can handle without a calculator on a daily basis. I literally hate doing math more than anything in life, mostly because I'm not good at it—and I hate doing things I'm not good at.

If you're an avid PC gamer, then you're probably well familiar with the term overclocking, which is basically just tweaking your computer hardware to run faster than it was originally intended.

You may or may not have heard the term "greebles" or "kit-bashing" before, but if not, they may sound like nonsense. Particularly 'greebles', which sounds more like the name of a small, gremlin-like creature. However, I assure you that they are very important in prop-making, and if you can master them both, you'll be able to make intricate, great-looking props in hardly any time!

Notes: My guides are setup like old Lego instruction booklets; picture intense/text lacking. Just remember you're building from the ground up, each step is a layer to go onto the previous layer.

Fashion Television is responding to viewers request to learn how to bleach jeans. First, you need a spray bottle. Any bottle will do, and you want to fill more than half the bottle with bleach, and the rest of the bottle with bleach. If you use only bleach, you will ruin your clothing. Go outside to bleach jeans because it is dangerous to use it in the home. You must bleach items in a well ventilated areas. All you have to do is just spray the jeans. Wait for it to dry, and if you do not like...

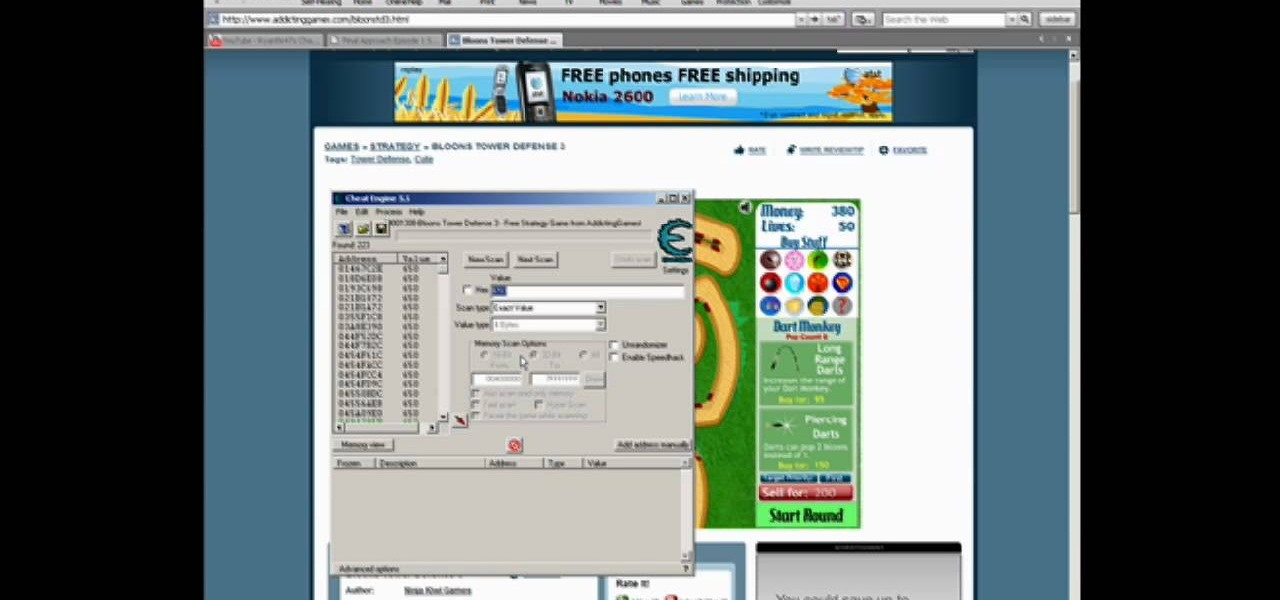
Bloons Tower Defense 3 is a flash game from Ninja Kiwi. Learn how to hack Bloons Tower Defense 3 with tricks and cheats. Watch this video tutorial to learn how to hack Bloons Tower Defense 3 with Cheat Engine (09/28/09).

This arts and crafts video teaches us how to make a mermaid tail in minutes. Our instructor tells us how she got requests for this after people saw her video, in which she swims in a mermaid tale. To make the mermaid tale, find some stretchy pants. Any pants that are light and are able to stretch will work. Do not use jeans. To make the tale, you put one leg in one hole of the pants, and then you put your other leg in the same hole. Next, take the other leg of your pants, wrap it around your ...

Giving a speech in front of a large crowd doesn't need to be the nightmare everyone imagines it to be. We speak to many people every day and yet it is still very common for a person to be nervous when delivering information in front of several people. This fear can be overcome by practicing how to give a speech and being prepared.

Apple released the newest update for iPhone, iOS 14.5.1, today, Monday, May 3. The update (build number 18E212) is the first since iOS 14.5, which Apple made available one week earlier on Monday, April 26.

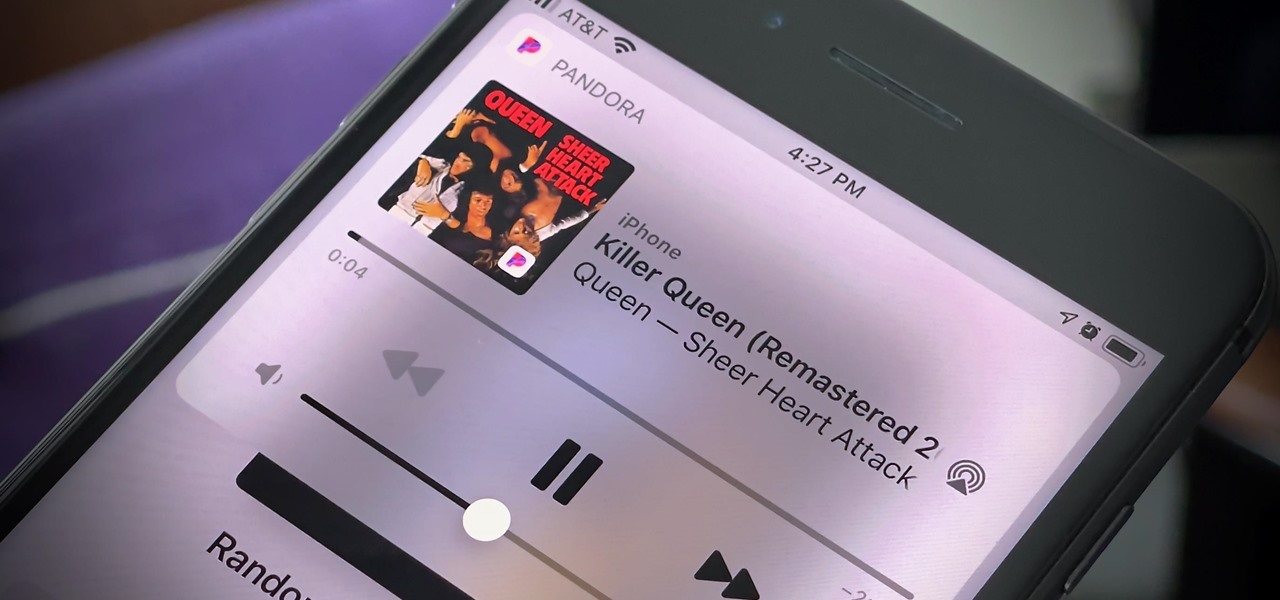
If Pandora is your primary music app on your iPhone, you know it can be frustrating to use with Siri. The digital assistant always wants to use Apple Music instead, so you need to specify that you want to play through Pandora with almost every request. That's now a thing of the past because iOS 14.5 allows you to set Pandora as your Siri's preferred music player.

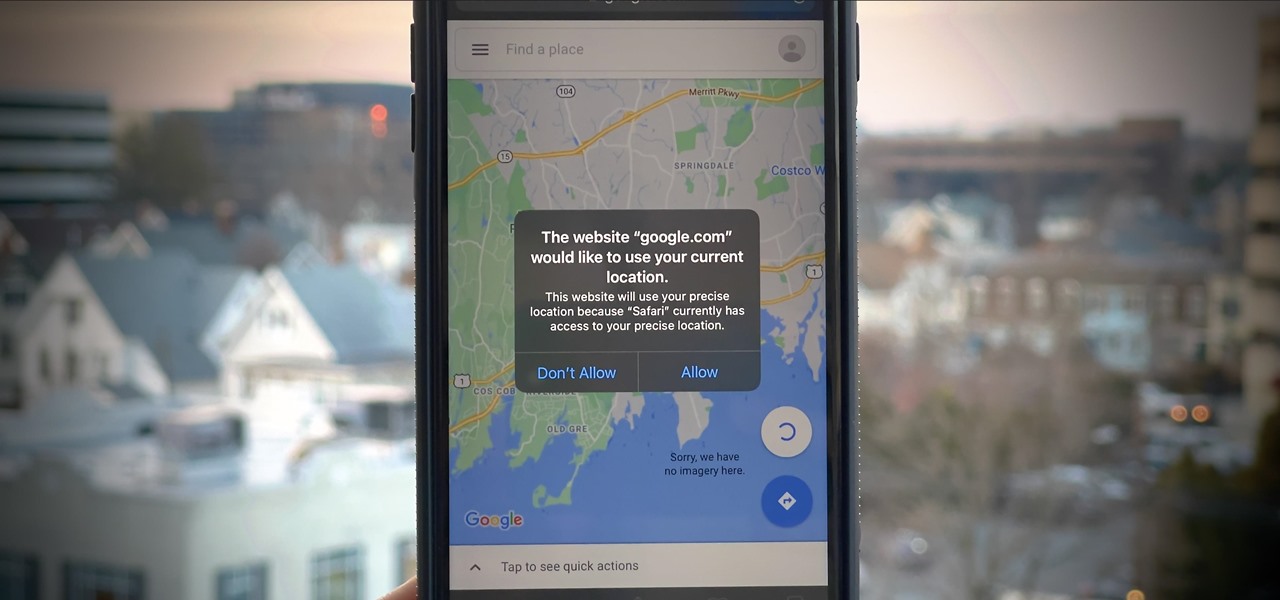
If you surf the web on your iPhone, you no doubt run into this problem all the time: a website wants your location. It can happen when performing a location-based task, such as using a store locator, or whenever a web app just wants to deliver better ads or local recommendations. If you're tired of allowing or denying permission each time, there's an easy way to stop the annoying security pop-ups.

Apple has an excellent reputation for its privacy and security policies. That said, it isn't a perfect reputation. Take Siri, for example. The helpful iOS assistant isn't just communicating with you — Apple saves and listens to a history of your Siri interactions. If you don't want Apple storing your Siri history forever, there's something you can do about it.

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

Google's been on a mission to improve the privacy and security of Android lately, and Samsung's always been at the forefront in these areas. As a result, One UI 3.0, which is based on Android 11, is the most secure OS version to ever hit Galaxy phones thanks to few key changes and new features.

Almost 20% of the US population (about 60 million Americans) live in rural areas where mobile reception is weak or nonexistent. In times of crisis, these Americans can't rely on the internet to communicate with loved ones or receive new information. This is why being able to interact offline is so important.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

In the pursuit of large displays with thinner bezels, Samsung has sacrificed some components. While the loss of the headphone jack gets all the attention, there are other victims — namely, the notification LED.

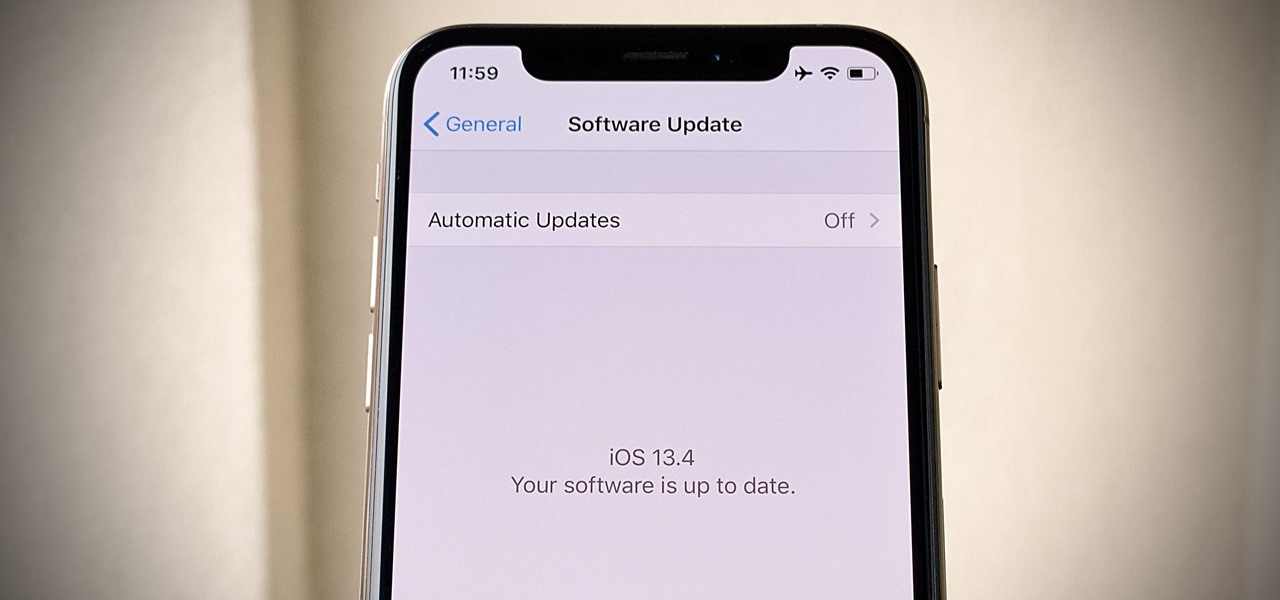
Apple released the fifth public beta for iOS 13.4 on March 10. The update comes three hours after the release of developer beta 5, and exactly one week after iOS 13.4 public beta 4.

Look, we like a new beta update as much as the next tester. There's nothing better than downloading and installing a fresh iOS seed, hunting down any and all new changes and features from the last. That said, we're a bit surprised Apple decided to release iOS 13.4 developer beta 5 on March 10 since dev beta 4 was such a minor update.

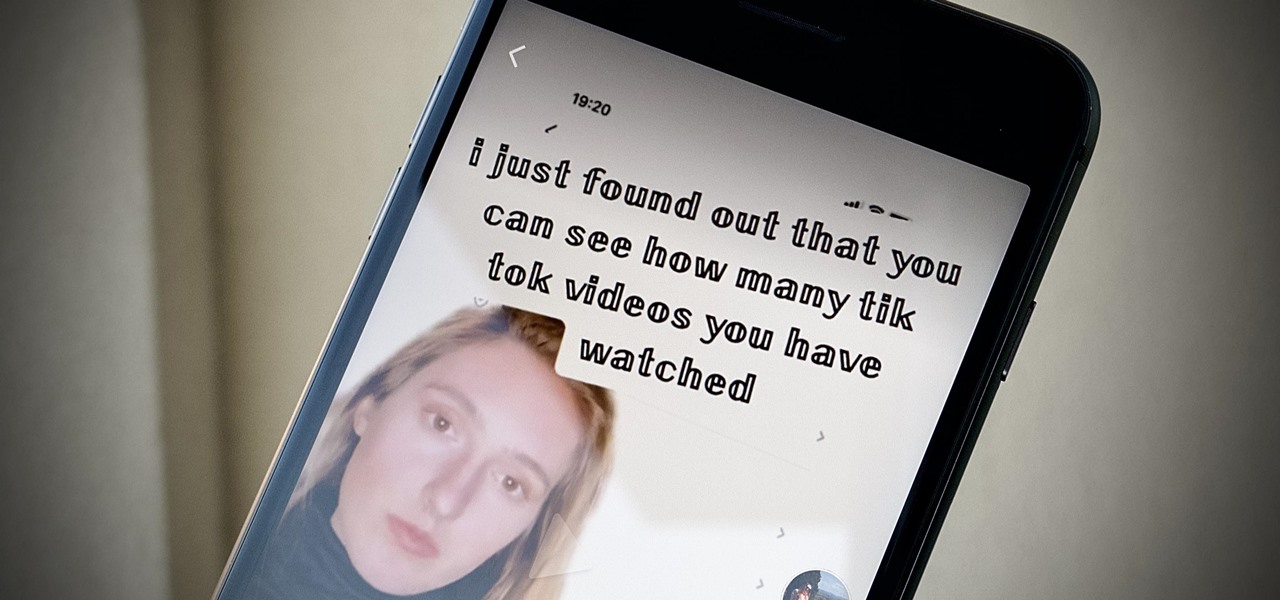
If you're as addicted to TikTok as much as I am, you probably heard about the app's alleged, hidden views counter, which can show you how many TikToks you've watched on your account. Most people who look at their counters are horrified to see that they've watched hundreds of millions of TikToks so far. Can that be right?

With today's release of iOS 13.4 developer beta 4, it seems Apple is closer than ever to releasing the official build for its upcoming iOS update. If you've been following the beta closely, you know that means new Memoji stickers, CarKey API support, and Mail toolbar updates, in addition to general bug fixes. Public testers can now take that extra step, as Apple just released 13.4 public beta 4 today.

March is looking to be an eventful month for Apple. Even with coronavirus throwing the tech industry into uncertainty, we still expect Apple to release the iPhone SE 2, the long-awaited follow up to the iPhone SE. Is it possible we'll also see iOS 13.4 fully released this month? We wouldn't be surprised if we do, seeing as Apple just released its fourth developer beta.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?

When it comes to iOS beta updates, developers get their updates first, and once they do, public testers play the waiting game. Sometimes Apple releases the public version three hours later. Other times it waits 24 hours. It's a roll of the dice almost every time. As for iOS 13.4 public beta 2, it's the latter case, coming exactly one after developer beta 2.

Last week, Apple released the first iOS 13.4 beta with fun and useful new features, such as new Memoji, an upgrade Mail toolbar, and the ability to control your NFC-compatible car via CarKey. To add to that, Apple just released iOS 13.4 developer beta 2, but does the update have any more new changes to be excited about?