Near Field Communication, or NFC for short, is a feature that allows our smartphones to wirelessly communicate with other devices over a short distance while using almost no power at all. Think of it like a slimmed-down version of Wi-Fi or Bluetooth that can send a small burst of data two inches away without having any measurable impact on your battery life.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

An accelerometer/gyro goes onto an Arduino board and transmits the angular motion of the skateboard via Bluetooth to a virtual reality game I made for Android phones and Google Cardboard.

No doubt you internet-savvy folks have seen the incredibly beautiful rainbow bagel going viral all over the country—and if not, let me educate you on its multicolored brilliance. Crafted by the brilliant bakers at The Bagel Store in Brooklyn, this cheery creation has actually been around for 20 years now. Watch the video below to see how the colorful roll is created.

OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a developer. Aside from developers, the command line tools can offer benefits to normal users as well, like the ability to purge RAM for better performance.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

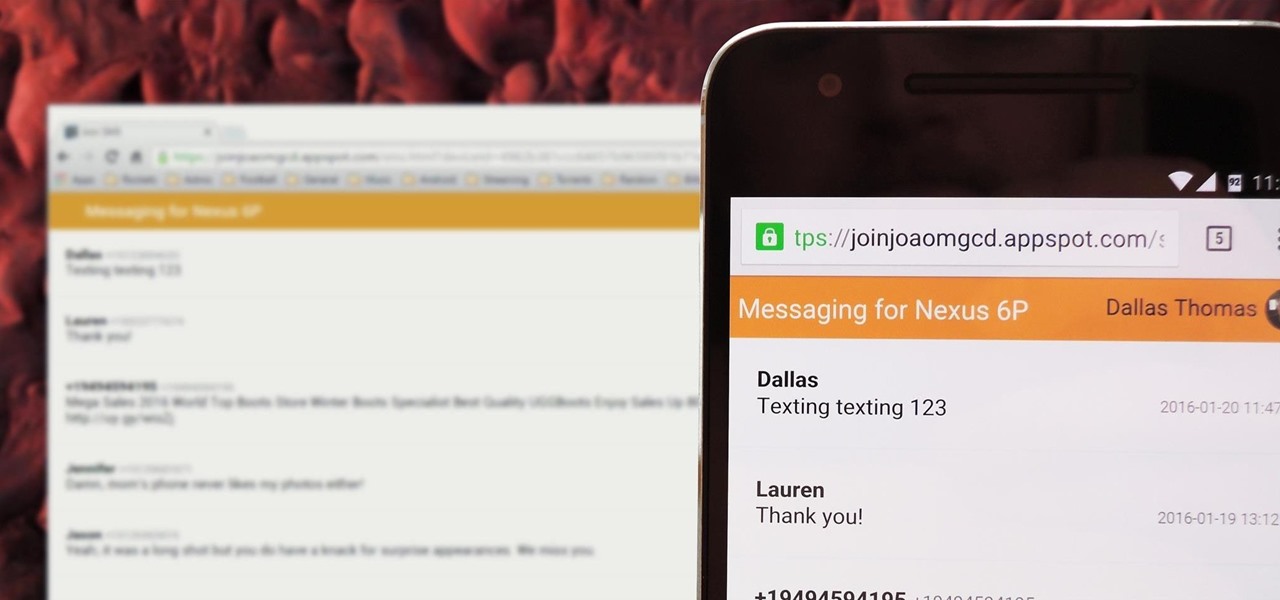
There's no iMessage app on Android, so unlike the folks who own both an iPhone and a Mac, we have to rely on third-party solutions to send and receive SMS messages from our computers. But on the bright side, this means we don't have to buy an exorbitantly expensive desktop or laptop to respond to texts when our phones are out of reach, because Android is all about cross-platform compatibility instead of chaining you to an ecosystem.

Some of the best images I've seen were shared via Snapchat, but once they're expired, they're gone forever, with no way to view them again unless I want to take a screenshot. But that will, of course, alert the sender.

hello hackers,newbies and followers of this great community, after some research here in our community, I noticed that there is not even one tutorial that teach Web Development. We have a lot of tutorials on how to hack web site but many do not know exactly how a web site is composed, then I decided, meeting the community's needs, begin to teach people how to develop web sites.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Video: . Being one of the most popular DIY/maker projects around, Musical Floppy Drives are nothing new. However, myFloppyDriveOrchestra includes a few unique features, which separate it from the crowd.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

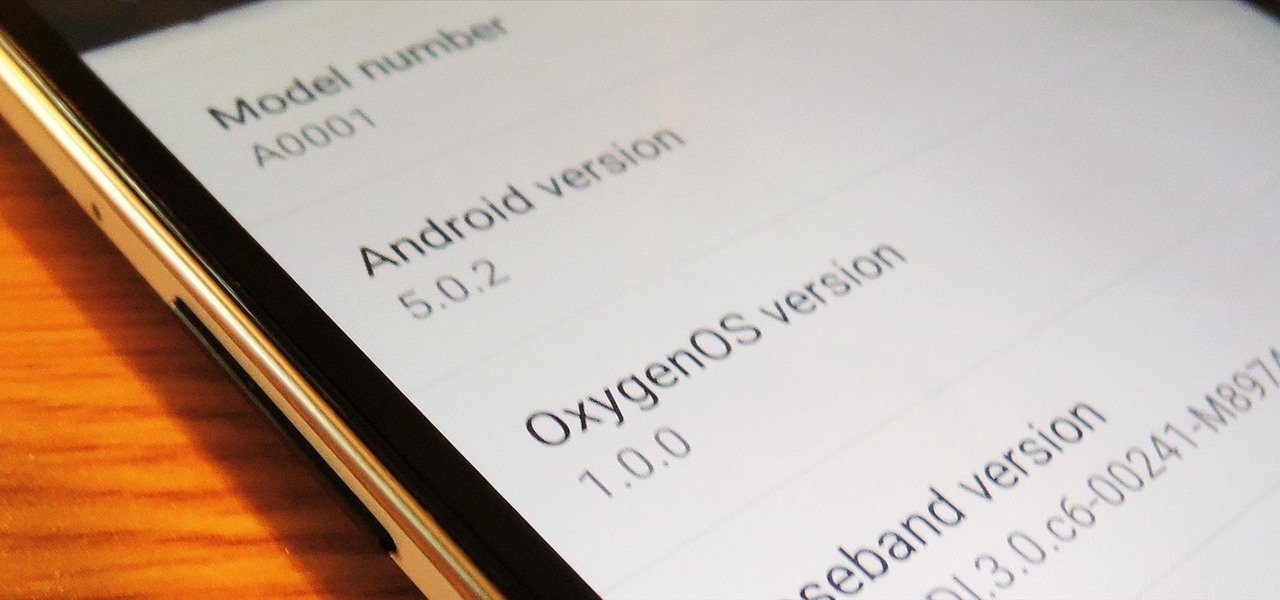
Despite CyanogenMod actively working on their CM 12S Lollipop-based ROM, OnePlus has opted to develop their own ROM, and after a few setbacks, OxygenOS is finally out. The OS is the result of OnePlus wanting to ship their devices without needing an outside company to create a ROM to power it. Like CyanogenMod's ROMs, Oxygen OS offers a vanilla Android Lollipop experience tailored for the OnePlus One.

Android has a system-wide user dictionary file that any third-party keyboard can utilize, if it so chooses. This file contains all of the words that you've added to your keyboard manually, and of the big-name players, Minuum, TouchPal, and the Google Keyboard call on this file to determine their user dictionaries.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

Emojis, smilies, emoticons—whatever you prefer to call them, these fun little guys can bring a text-based conversation to life. If you're worried that someone's sarcasm meter might be broken, just toss in a wink at the end of your message. Or perhaps you can't quite put your sentiment into words, but one of these little graphics suits the moment perfectly.

If you've ever flashed a custom ROM on any of your devices, one of your main motivations for doing so was likely the set of neat tweaks and extra options that come with something like CyanogenMod. Another deciding factor was probably the fact that most custom ROMs offer a much cleaner interface than manufacturer skins.

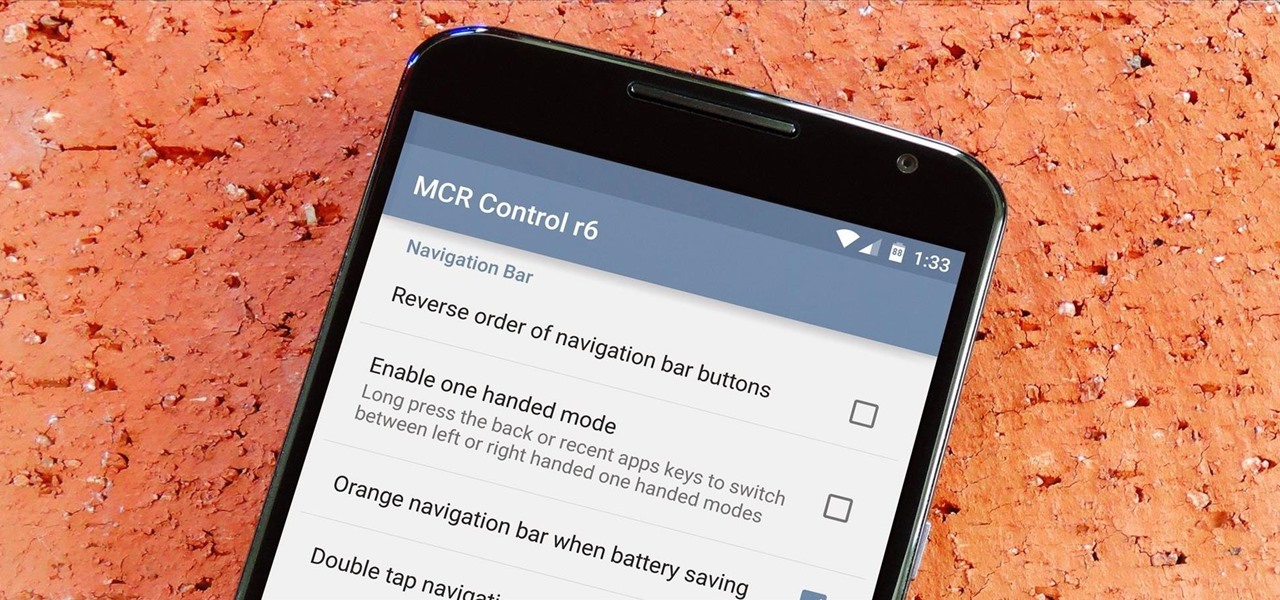
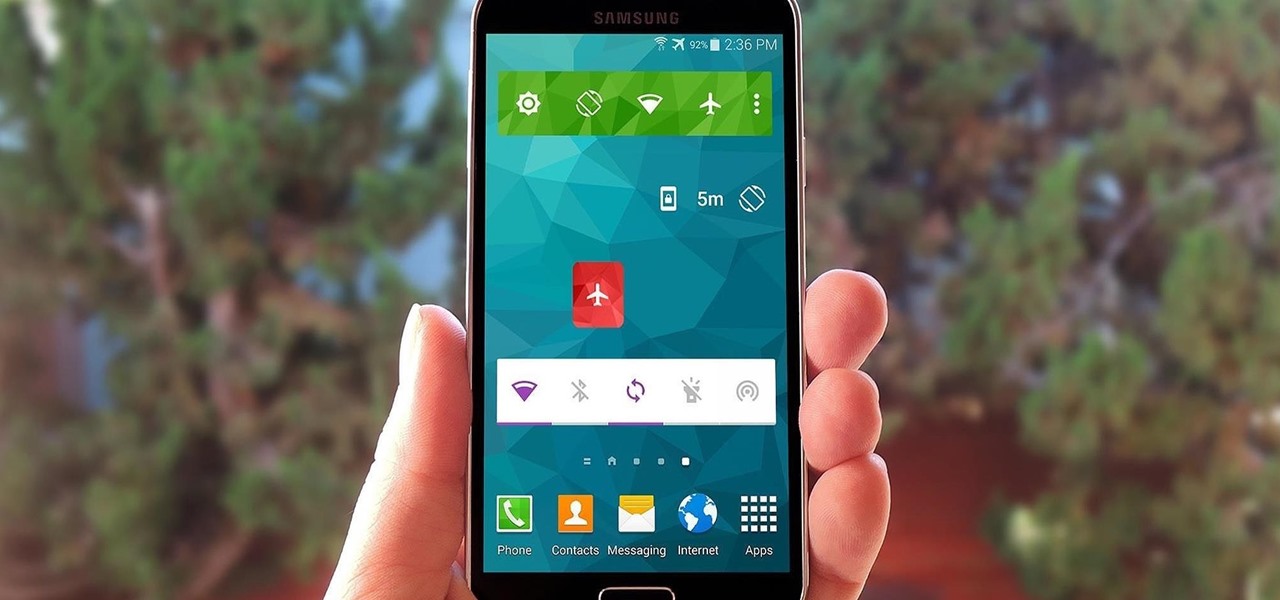
Widget toggles, or "power toggles" as they're often called, have been around for quite a while. They serve their purpose nicely as an easy way to add switches to your home screen or notification area for functions that don't come with the stock software on your device.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

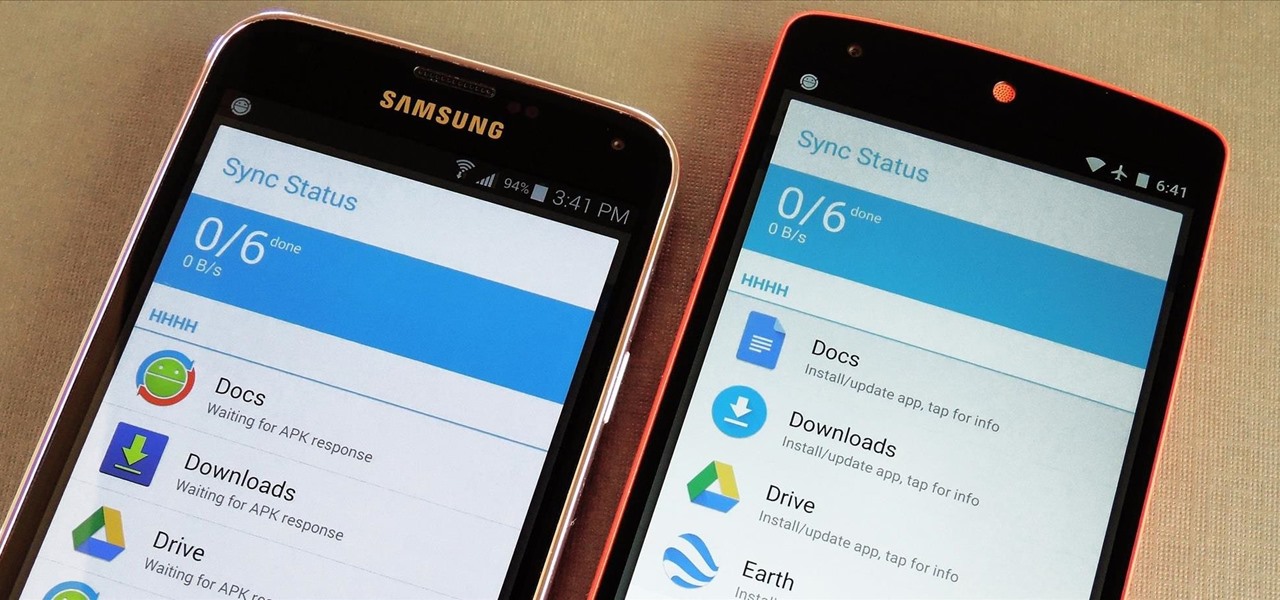
If you own multiple Android devices, you're surely familiar with the struggle of keeping apps and games in sync. While games with proper Google Play Games support will indeed sync progress across your phone and tablet, many developers neglect to include this feature in their wares.

If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and physical barriers to delineate their cultures.

The Nexus 6 uses an Ambient Display notification system that was heavily inspired by the Active Display feature on the Moto X. Essentially, the device shows a black-and-white version of the lock screen whenever you receive a new notification or pick the phone up. This is all made possible by the N6's AMOLED display that doesn't have to waste any battery to power black pixels on the screen.

Stock Android is a great experience, and it's probably one of the biggest reasons that people purchase a Nexus device over other Android phones. Without carrier or manufacturer modifications to the core software, the entire user interface feels a lot more clean and snappy, and this also means that developers encounter fewer compatibility issues when creating flashable ZIPs and custom ROMs.

Google's latest Nexus device is big, bold, and beautiful—and now it's got root. Thanks to some quick work by legendary Android developer Chainfire, the Nexus 6 already had a clear-cut root method before most stores even had it in stock.

So, you're scanning the internet for some cool articles to read during your lunch break and you come across something pretty interesting—"The 50 Most Incredible Things Every Person with a Brain Should Know." That sounds interesting, so you click, and boom, you are hit with the utterly obnoxious Page 1 of 50. Really?

In today's world of ordering food from your PC or hailing a cab with an app, it almost seems archaic when we have to actually use our vocal cords to contact a local business. It sure would be nice if we didn't have to use our smartphones as, well, you know...phones.

iCloud Drive is Apple's new solution to file management syncing across iOS and Mac OS X. If you've upgraded to iOS 8 and you have an iCloud account, you can use iCloud Drive to store files for certain apps. While you won't really be able to benefit with file syncing between iOS and Mac apps until you get Yosemite, you can still access your iCloud Drive documents online.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

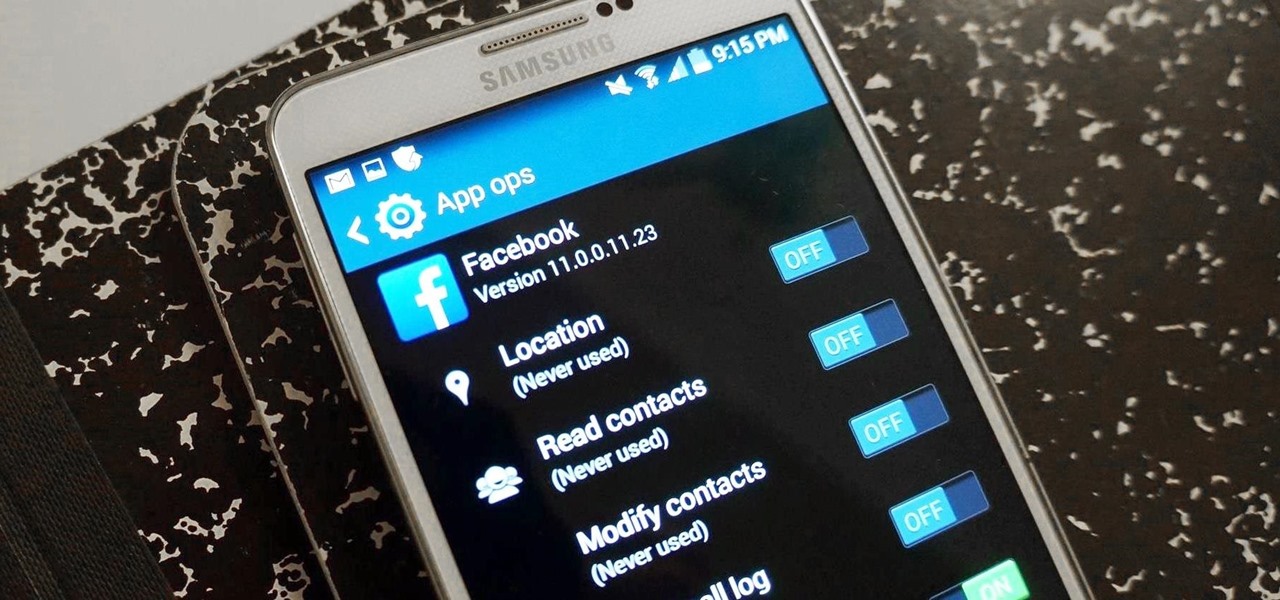
It's a modern day nightmare to accidentally reveal too much information on Facebook. I've inadvertently told the world my location more times than I can laugh off, and my friends haven't fared too well either. Just take a look at the requested app permissions next time you're about to click install and you'll quickly realize how much that app can reveal about you.

What do Hulu Plus, Pandora, and YouTube all have in common? Ads—and lots of them. Sometimes, an advertisement or two isn't a big deal, but when you're bombarded with them daily on your iPhone, they can get old really quick, and might even lead you to delete the apps entirely.

The use of smart phones is not limited only as a mode of communication now-a-days. There are many things that can be done with the help of a smart phone.

One of the most frustrating things about full touchscreen phones, especially for those coming from one with a physical keyboard, is typing and editing text. Whether it's a quick text message, or Swyping out a full e-mail, it sucks realizing you've messed up a few words and have to go back and fix them.

When you were younger, you probably had your parents bugging you not to have your cassette player headphones up too loud. For all you younger readers out there, it was probably a CD player. The even younger readers likely had an iPod or other MP3 player. Either way, your parents didn't want you to mess up your hearing, blasting that Limp Bizkit in your ears (wow, I'm showing my age here).

Overall, I love the Nexus 7 tablet, but one thing that I truly dislike about it is having to press the Power/Lock key to lock my screen.

Why unlock your Samsung Galaxy S3 to use with a different SIM card? One possible reason is that you love your phone, but not your cellular provider because of the poor service or an unreliable connection. If you purchased a Samsung GS3 with AT&T, T-Mobile, etc. on a contract, it might be locked for a specific amount of time called the contract period.

On the new Moto X smartphone, the only thing you have to do to activate the virtual assistant is say "Okay, Google Now." That's it. You don't have to press a button or tap on the display at all. It's always ready for your voice commands via its "Active Listening" feature, making it a truly hands-free experience.