Just what are probiotics and why are they so good for you? Probiotics are "viable microorganisms" that can confer lots and lots of health benefits if they reach your intestine while they're alive. You may have heard them described as "friendly bacteria."

Journals are a great source of hilarity and embarrassment, detailing everything from your elementary school crushes to those super awkward middle school dances. While rereading your old hand-scrawled entries might make you cringe, that old journaling habit could benefit you as an adult.

"Does bottled barbecue sauce even taste that bad?" a friend of mine asked. Well, truthfully, no. But it also doesn't taste that good, especially if you've had truly great barbecue or even your crazy uncle's homemade sauce at a holiday cookout.

Even though I often end the workday exhausted and just want to wrap rotisserie chicken parts in a store-bought tortilla and shove it in my eating hole, I generally try and take a couple of minutes to warm up said tortillas before I begin my meal. But if you're starving, do you really need to take the time? Do warm tortillas really make that much of a difference?

As a species, our cells are designed to use sugar for energy. Is it any wonder that as humans evolved, we grew to love the taste of sugar?

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Many of us experience highly emotional "freakouts", so to speak, more often than we'd like. Weather you experience them personally, or via your loved ones, it can be very difficult to think rationally during an episode, and for some people it can take quite a while to calm down.

2 + 2 = 4. That's about as much math as I can handle without a calculator on a daily basis. I literally hate doing math more than anything in life, mostly because I'm not good at it—and I hate doing things I'm not good at.

If you're an avid PC gamer, then you're probably well familiar with the term overclocking, which is basically just tweaking your computer hardware to run faster than it was originally intended.

You may or may not have heard the term "greebles" or "kit-bashing" before, but if not, they may sound like nonsense. Particularly 'greebles', which sounds more like the name of a small, gremlin-like creature. However, I assure you that they are very important in prop-making, and if you can master them both, you'll be able to make intricate, great-looking props in hardly any time!

Notes: My guides are setup like old Lego instruction booklets; picture intense/text lacking. Just remember you're building from the ground up, each step is a layer to go onto the previous layer.

Here's a great traditional feast with a glazed ham, cheesy scalloped potatoes and beans. This ham meal is super easy to prepare. Watch this how to video to learn how to make a glazed ham that the entire family will love.

Chef Elvis "Gator" Hillard will show you how to prepare the water and add the salt, cook the pasta, chop the fennel and garlic, and strain the pasta. Elvis will also show you how to cut the asparagus, sauté the fennel and garlic, add the Romano cheese, incorporate the sauce, and add the cream and the peas.

In this video author introduces a new grain called quinoa which is considered very healthy and has good nutrition values. Quinoa is rich and proteins and fibers and low in fat. It is Excellent food for muscle builders and someone trying to lose weight. Quinoa basically is tasteless but you can add flavor to it. It is very easy to cook quinoa. We need to wash quinoa and mix with double quantity of water. We also need to add a little bit of salt. Author adds freshly cut salsa to mixture of quin...

Don’t wait for your next headache to pull out that bottle of aspirin. Aspirin can be used as a topical home remedy for some medical problems, and as a handy fix to remove stain, keep your flowers fresh and even start a car battery.

Boiling eggs isn’t as simple as boiling water but it almost is. This videos shows you how to use a nifty little egg boiling device that seems to quickly steam the eggs when put in the microwave. This is a handy kitchen counter top tool.

The healing power of scents has been used for centuries. Learn about the world of aromatherapy in this free video series about making aromatherapy oils and bath salts.

In this video series, our expert will teach you how to make your own spa body and facial scrubs. You will get step-by-step instructions for making a homemade sugar scrub and sea salt scrub.

In this online video series, learn how to make zucchini bread from expert homemaker and cook Carolyn Saylors. She will teach you what ingredients you need to make zucchini bread, how to beat eggs and mix the sugar and oil, how to mix vanilla and flour to make zucchini bread, how to add oats and cinnamon to the zucchini bread dough, how to add baking soda and salt to the zucchini bread dough, how to shred zucchini for zucchini bread, how to add walnuts and shredded zucchini to the zucchini bre...

After months of waiting, the iPhone 11 is here. At an event in Cupertino, Apple unveiled the iPhone 11, 11 Pro and 11 Pro max. You probably have a lot of questions after reviewing the specs sheet, including wanting to know more about the IP68 rating that all three phones have. We're here to clarify.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

Update February 25: The new Sony Xperia flagship has been announced, and it has a new name: The Sony Xperia 1. You can read all of the official specs and details at our full article on Sony's new model.

They're finally here. Apple announced three new iPhone models at their "Gather Round" event in Cupertino, and they're all absolutely gorgeous phones. With bezel-less screens and polished titanium edges, the iPhone XS, XS Max, and XR are truly marvels of engineering — but perhaps the most impressive design feat Apple pulled off is the fact that two of these models are rated IP68 under the IEC standard 60529.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

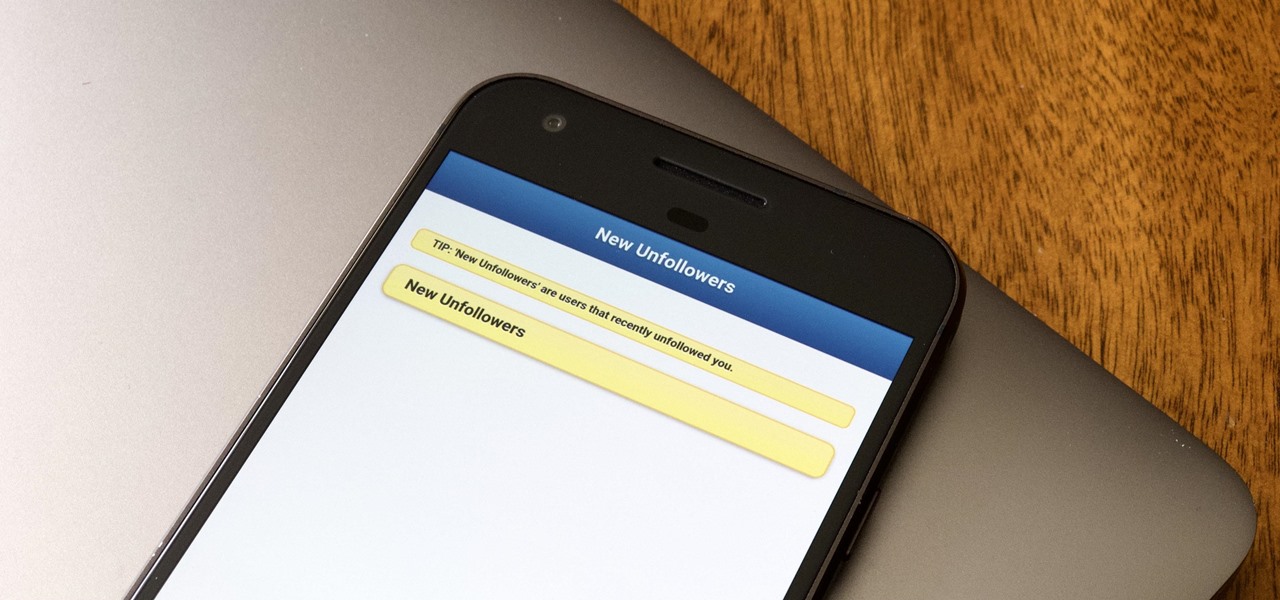
Followers are everything. After all, you need someone to listen to your tweets about last night's episode of your favorite TV show. But what about when people unfollow your account? Not only have you lost part of your follower base, you have no idea who left. Luckily, there are tools out there to help you learn just that, even if Twitter itself won't give up the info.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

Not to be outdone by Apple and it's new line of flagship phones, Google has followed suit and finally announced the followup to their highly regarded Pixel line of handsets — the aptly named Pixel 2. Thankfully, the tech giant has also joined in on the trend towards more durable devices, and has engineered both the Pixel 2 and Pixel 2 XL to have a rating of IP67 under the IEC standard 60529.

Bacteria, viruses and other germs sometimes set off the immune system to overreact, producing a severe condition called sepsis. Sepsis is so dangerous that it is the leading cause of death of children across the world, killing a million kids every year, mostly in developing countries. Probiotic bacteria might be able to prevent sepsis and infections, but no large research studies have been done to find out whether that actually works. Until now.

Unfortunately, the very places we go to receive health care put us at risk for becoming infected with superbugs, bacteria exposed to so many antibiotics that they have become immune to their effects. Clostridium difficile (C. diff) is one such bacteria. It causes inflammation of the colon and rampant diarrhea that can have life-threatening consequences. Part of its virulence lies in the tough spores formed by the bacteria. They are responsible for starting infections in the colon and for spre...

An older man dies of Zika. A younger man who cares for him catches Zika — but doctors cannot pinpoint how the disease was transmitted. While proximity to the patient is sufficient explanation for the rest of us, for microbe hunters, it is a medical mystery. Why? Zika is not known to transmit from person-to-person casually.

Look no further than Flint, Michigan, to discover the serious consequences of contaminated drinking water. Around the world, water polluted by pathogens and toxins sickens people or cuts them off from safe drinking water. Looking for a solution, researchers created tiny, swimming robots that pack a powerful punch against waterborne pathogens.

Viral infections have been the focus of attention in the development of autoimmune diseases—diseases where the body's immune system reacts to the body's own cells—because they trigger the immune system into action.

If you want to appreciate the value of microbes, look no further than a chunk of cheese. Because cheese roughly traces back to the Neolithic Era, we might say the earliest cheesemakers were the first humans to manipulate microbes—without even knowing it. Now, thanks to microbiologists and the long tradition of cheesemaking, we know a lot more about the microbes that make our favorite types of cheese possible.

Cholera may be rare in the US, but cases of the disease have increased worldwide since 2005, particularly in Africa, southeast Asia, and Haiti. An estimated 3 to 5 million people are infected, and more than 100,000 die from the disease globally each year, mostly from dehydration.

The story of Helicobacter pylori is a real testament to the tenacity of medical researchers to prove their hypothesis. It took decades before the scientific world would accept that the bacteria H. pylori caused ulcers.

If you're grossed out by anything creepy, crawly, and with more than 4 legs... then stop being so close-minded and eat some bugs already, dammit.

Maybe you've had a long day... or maybe you just want to treat yo' self. So you head to your local watering hole for some tasty, tasty liquor. Your current fave on the cocktail list is a drink of something strong with bitters; you don't know what bitters are, but damn if that booze isn't delicious.