Welcome back, my fledgling hackers! If you're like most aspiring hackers, at one time or another you've probably spent too much time playing Call of Duty and not enough time preparing for your final exams.

Yes, there's a whole lot more than 3 chords out there and this lesson of aural training will help teach you the intervals of a minor 6th, minor 7th, and an augmented 4th - thus completing an entire octave in melodic interval ear training. Justin Sandercoe takes the mystery out of music with this clear and comprehensive lesson to make sure you'll be more than a one hit wonder.

While it might pain you to put a price on your art, if you want to support yourself through photography you may have to. Fortunately, it isn't as difficult as you might expect. It's so easy, in fact, that this free video tutorial can present a comprehensive overview of the process in just over three minutes' time. For detailed instructions, as well as to get started sharpening your own knives, watch this helpful how-to.

In this tutorial, learn how to achieve the Exorcist achievement in the Xbox game Metro 2033. This is a very detailed, comprehensive tutorial that shows you exactly where to go and how to act in your game to get this ultimate prize.
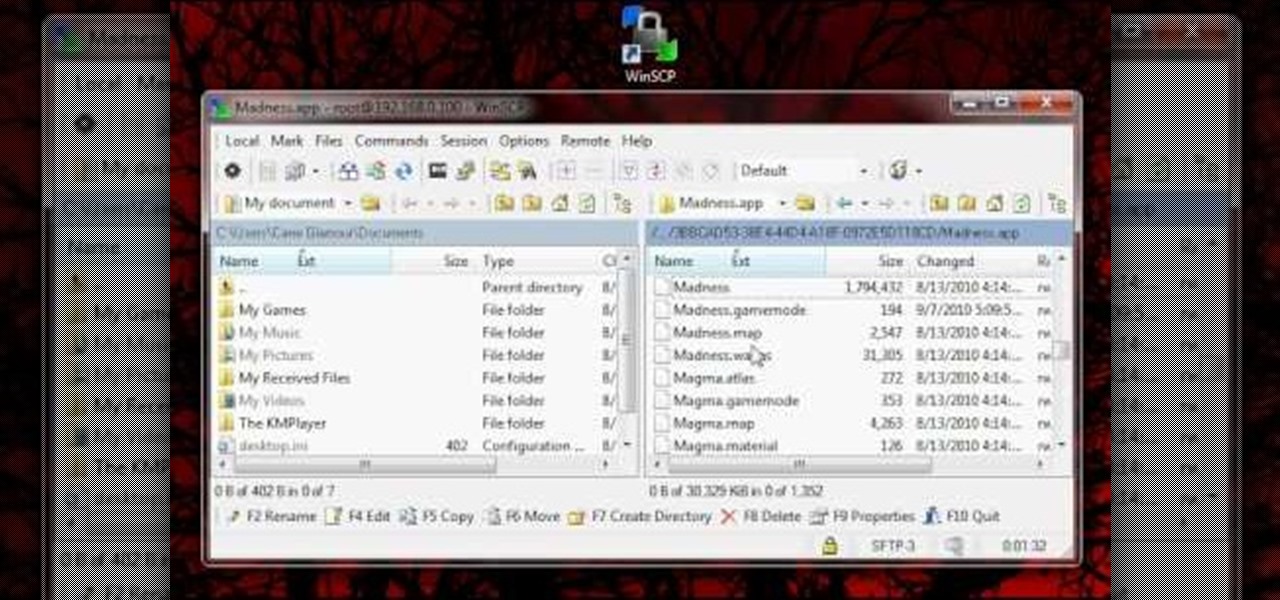
In order for this tutorial to work, you will need a jailbroken iPhone or iPod Touch. Once you have this, download the OpenSSH protocol from Cydia and then download WinSCP onto your PC. Once you've hooked everything up and logged in, navigate through your Applications directory until you find the TowerMadness app. Once you have opened the TowerMadness app, all you need to do now is find the right file and change it around to increase the amount of money you have!

Have a file or a number of files too sensitive to be stored on your desktop hard drive? Thwart would-be snoopers with an encrypted USB flash drive. This free video tutorial from the folks at CNET TV will show you everything you'll need to know to create your own password-protected thumb drive directories.

In this video tutorial from Get Connected TV, hosts AJ Vickery and Mike Agerbo will show you how to safely move your iPod files to your home pc, for back up purposes, just in case something were to happen to your iTunes account or your iPod is damaged, or music directory accidentally deleted. The program they introduce in this video is called iPod-Rip, and they lead you through the steps necessary to back up your iPod files safely and easily, without damaging or deleting your files.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!

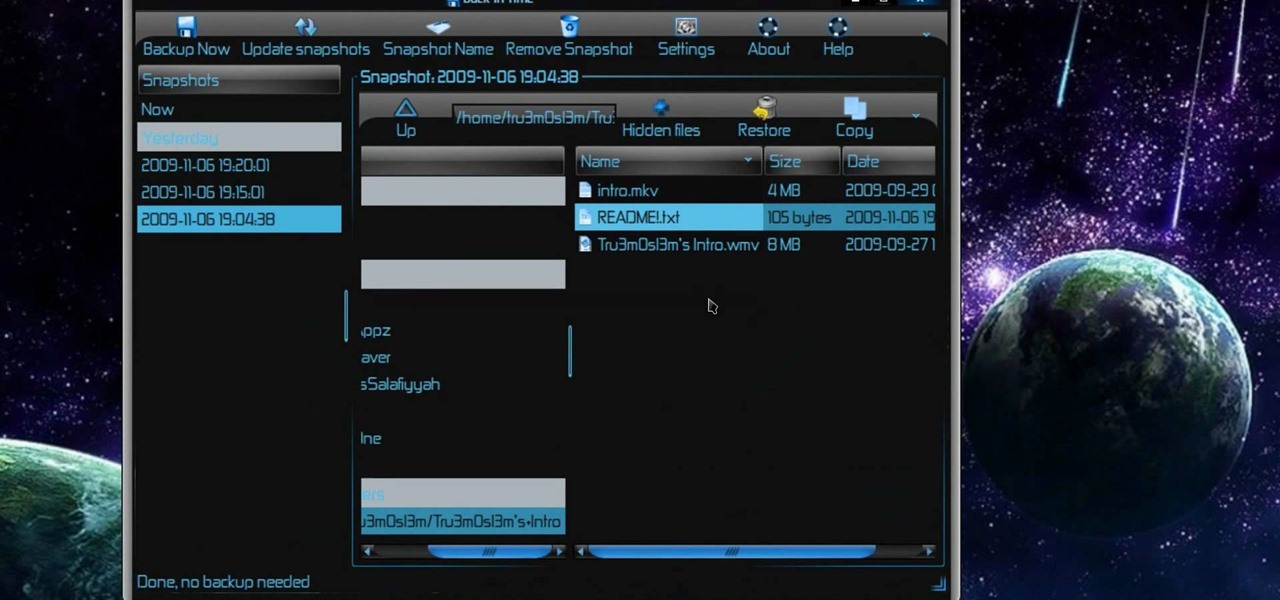
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to back up and restore data easily on Ubuntu Linux.

If you like shortcuts, then this shortcut for Windows XP should peak your interest. In this video, you'll learn the exact steps to adding a command prompt shortcut option to the Windows Explorer right-click menu. This allows you to access hidden functionality by adding a right-click option to select "Command Prompt Here" from the menu in Windows Explorer on a directory.

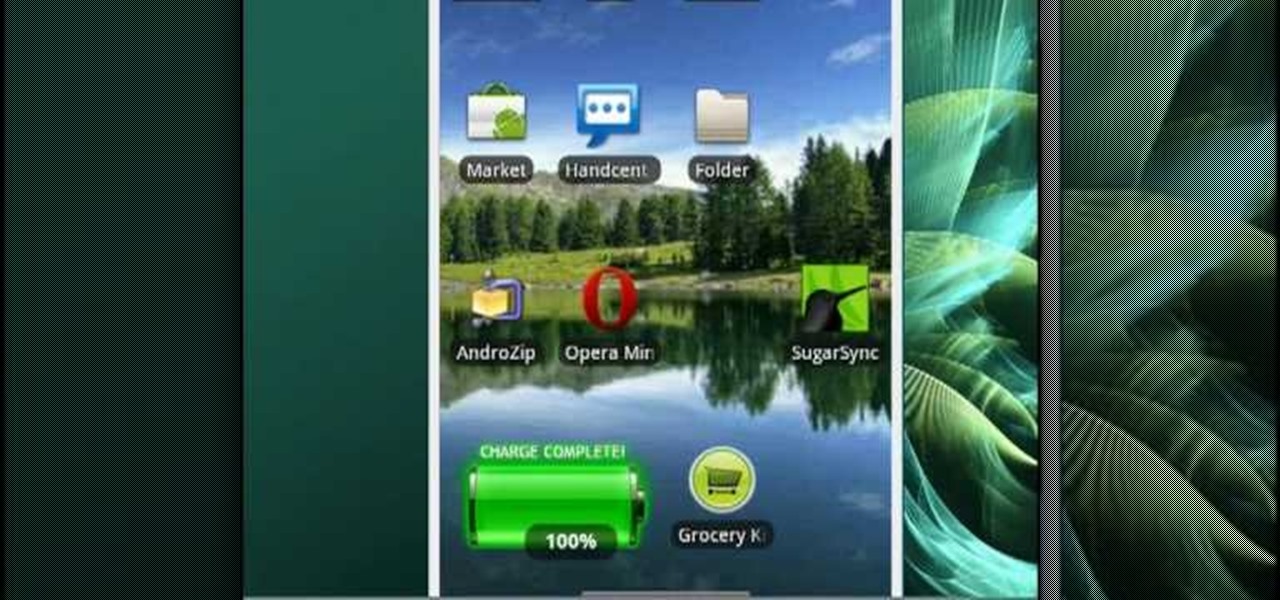
Is your Android phone's home screen a mess? One of the salient advantages of a Google Android smartphone over, say, an Apple iPhone, is the inherent extendibility of the open-source Android mobile OS. There are a seemingly infinite number of settings to tweak and advanced features to discover and use. This free video tutorial will show you how to create and use file directories on your Android device.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

In this clip, you'll learn how to create dynamic playlists for directories of MP3s with PHP. Whether you're new to the PHP: Hypertext Preprocessor scripting language or are a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free video programming lesson. For more information, including detailed, step-by-step instructions, take a look

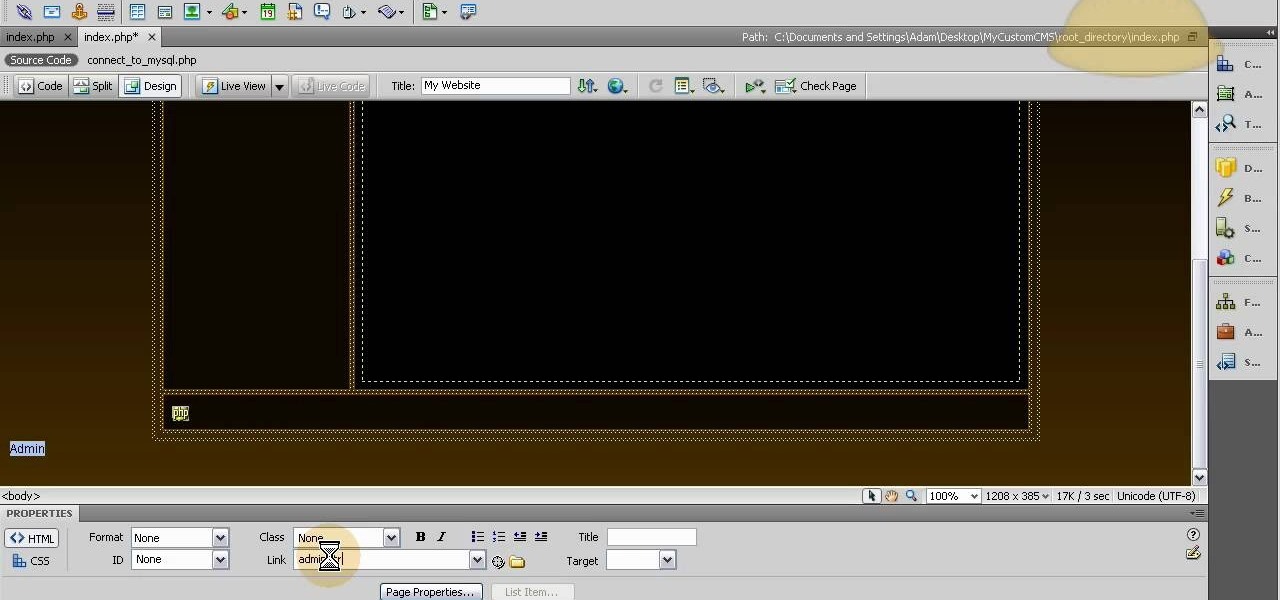
Designate a back end or administrator sector of the website, a place you can use to manage the content on the rest of the site. This tutorial shows you how to use Dreamweaver to set up this area of your website and cordon it off from the rest of your website.

Trying to find your friend's Yahoo! mail address so you can send them a letter or tell them about a cool new website you found? Yahoo! directory makes it easy to find someone you're looking for. All you need is is their name.

Interested in using the Active Directory Administrative Center on a machine running Windows Server 2008 R2? This clip will show you how it's done. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just over three minutes. For more information, including complete, step-by-step instructions, watch this sys admin's guide.

Interested in installing Active Directory Domain Services (ADDS) on a machine running Windows Server 2008 R2? This clip will show you how it's done. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just over five minutes. For more information, including complete, step-by-step instructions, take a look.

Dr. Preis has received Top Doctors recognition in the last 10 years of Castle Connelly's Directory. This video is perfect for parents and gives advice on recognizing if lack of eye contact may be a sign of Autism.

Oded Preis MD FAAP Associate Clinical Professor of Pediatrics SUNY Downstate Brooklyn Dr. Preis has received Top Doctors recognition in the last 10 years of Castle Connelly's Directory. In this DrMDK video, he discusses what bonding is and how to bond in birthing centers.

This tutorial teaches how to create new folders and files and how to move them to new directories using cPanel.

The free download manager wget lets you download all the files on a page or directory with a single command. It also allows you to resume downloads after getting disconnected letting you start where you left off instead of starting the download at 0% again. Check out this tutorial and see how to install and use wget.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Hello friends. This is actually my first how to.

Welcome back, my newbie hackers! Recently, I "upgraded" to Kali as my hacking platform, despite my preference for BackTrack. I did this reluctantly, primarily because new readers here could no longer download BackTrack from their site. I want to point out here that we all must keep in mind that with any software—or for that matter, any product—that is newer is not necessarily better.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

Looking for comprehensible instructions on how to assemble your IKEA Billy bookcase? You're in luck! This free video tutorial presents comprehensive, step-by-step guide on how to put together a Billy shelving unit. For detailed instructions and to get started setting up your own Swedish bookcase, watch this helpful how-to.

Knives gone dull? This chef's guide offers instructions on how to sharpen your kitchen utensils using a knife steel. It's easy! So easy, in fact, that this free video tutorial can present a comprehensive overview of the process in just under three minutes' time. For detailed instructions, as well as to get started sharpening your own knives, watch this helpful how-to.