
How To: Execute the perfect backflip by a Cirque du Soleil guy
This is a comprehensive tutorial on how to execute a proper gymnast's backflip. You must get yourself high enough to rotate back before attempting the flip portion of the trick.


This is a comprehensive tutorial on how to execute a proper gymnast's backflip. You must get yourself high enough to rotate back before attempting the flip portion of the trick.

Soldering isn't hard as you might think. This video will cover the basic soldering techniques for electronics and electrical wiring. It presents a comprehensive look at the soldering process, covering everything from choosing a soldering iron and solder to proper soldering technique. Get started soldering with this electronics how-to.

This software tutorial is a comprehensive exploration of the Marquee Selection tool in Photoshop using Photoshop CS2. Learn how to use the marquee selection tool when editing images and photos in Photoshop.

This sequence of instructional videos provides a near comprehensive lesson on how you can change your voice from that of a male to that of a female. This video series is aimed at aiding transgender individuals, but is also useful for people who want to learn to do really great voice exercises and impersonations.
If you're interested in changing the recommended items presented to you each time you open the shop in League of Legends, check out this guide. You will need to have access to your Riot Games and League of Legends directories first.
In this clip, you'll learn how to make recourse to the documents folder from within an iOS application. Whether you're new to the Objective-C operating language and Xcode IDE or are a seasoned developer merely looking to pick up a few new tips and tricks, you're certain to be well served by this tutorial. For more information, including a complete overview and detailed, step-by-step instructions, watch this free video Objective-C programming lesson for iPhone & iPod Touch developers.
This is a very basic introductory video that teaches you how to successfully install Quartz Composer on your MAC OSX 10.5 Leopard. Quartz Composer is a node-based graphical data software that uses visual programming language. Built exclusively for use on the MAC OSX, it's a handy software for graphic designers.

This is the first of 3 steps that will show you how to juggle three balls. Jim the juggler demonstrates how to get them up and going. Step 1 begins with one ball, so be patient, you need to work your way up! (WMP files and smaller videos are available at the root directory)

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.
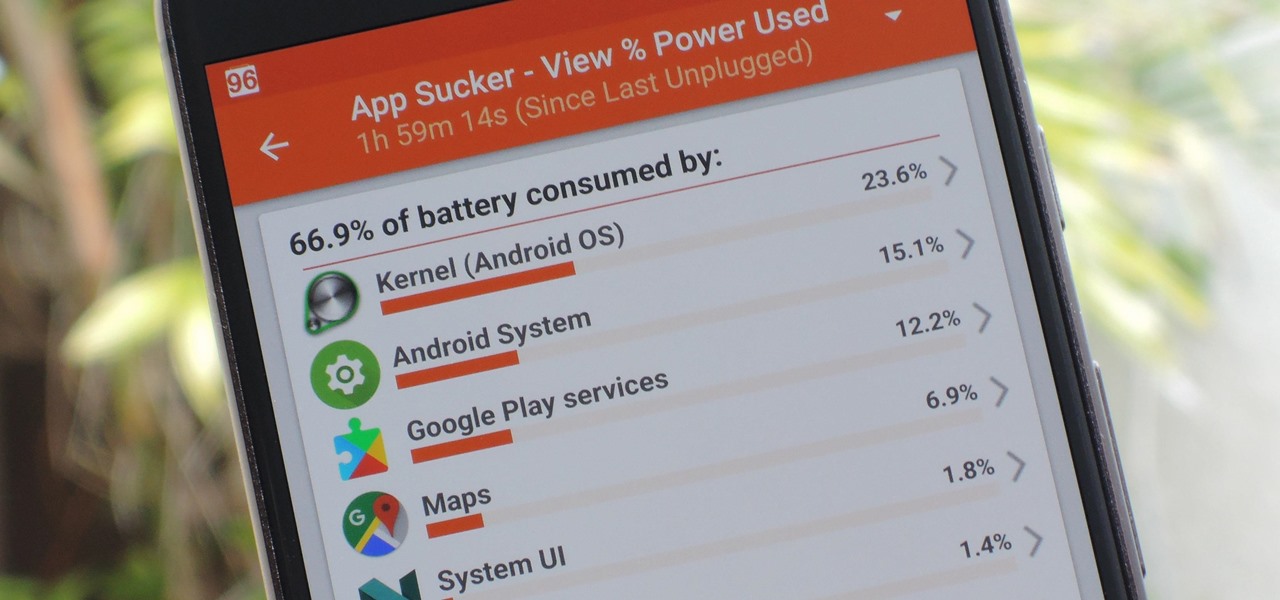
Figuring out exactly which apps on your phone are eating through resources and battery life can be a difficult task. Though some information can be found in Android's battery menu, the charts and graphs provided here pale in comparison to what's offered by the GSam app. If you configure this app properly, it provides deep insight into battery, CPU, and data usage.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.
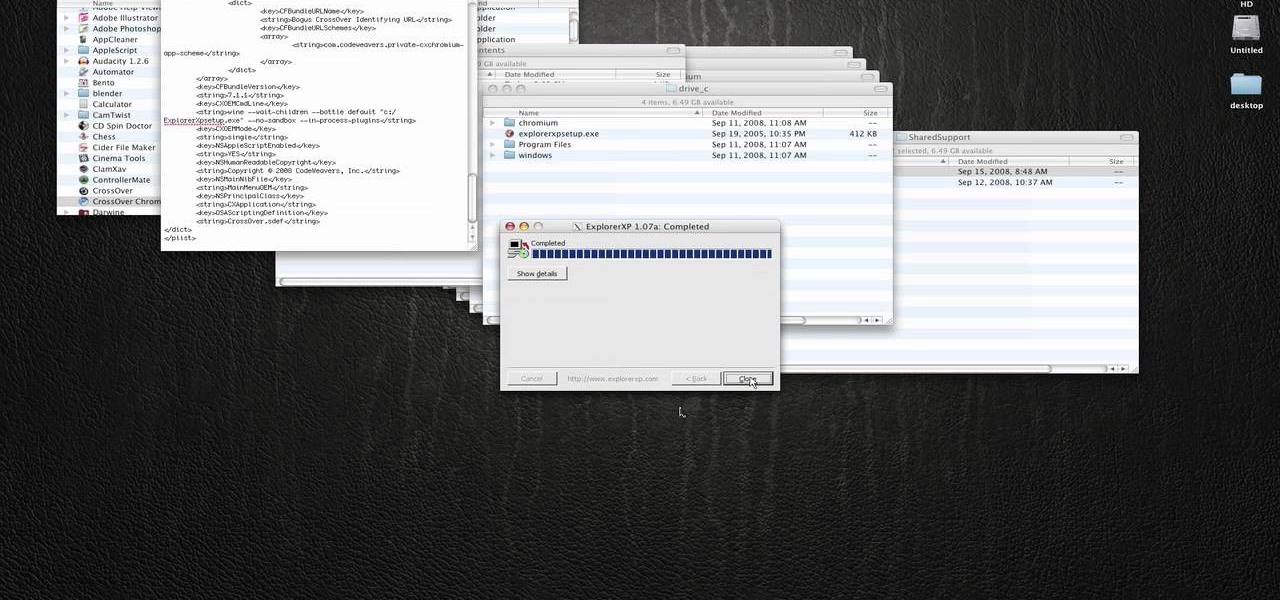
In this how to video, you will learn how to run Windows programs for free on a Mac using Crossover Chromium. You will need to download Crossover and install it by downloading it and dragging it into the applications folder. You will also need Explorer XP. Go to the applications folder and show the package content of Crossover. Go to shared support as you will need a file here later. Open Chromium, go to support, Chromium, and Drive, and then drop Explorer XP into the folder. Open the info fil...

This video shows the method to SSH into iPod Touch 1G or 2G. You need an iPod touch 1G/2G with Firmware 2.2.1 or previous (Windows), a Windows based computer and a jailbroken iPod Touch which has Wi-Fi connectivity. Open Cydia, go to search and type OpenSSH and install it. Go to settings, Wi-Fi and click on the blue arrow next to the network. Copy down your IP address from the resultant window. Open WinSCP.net and go to Downloads, installation package. Install the package and open WinSCP from...

Attention aspiring screenwriters! In this tutorial, learn how to sell that script. You may have written the next Hollywood blockbuster – but unless you can finance the film yourself, you’ll need to sell the screenplay to a producer who can make it come to life.

Valentine's Day is near, and Judy Topaz has the perfect project for you… a knitted heart. If you want to add a little bit of sweetness to your scarf, sweater or other knitting project, then this knitted heart will surely do the trick. Just make sure to choose a good yarn for good color contrast. Watch all four parts of this comprehensive Valentine's Day knitted heart!
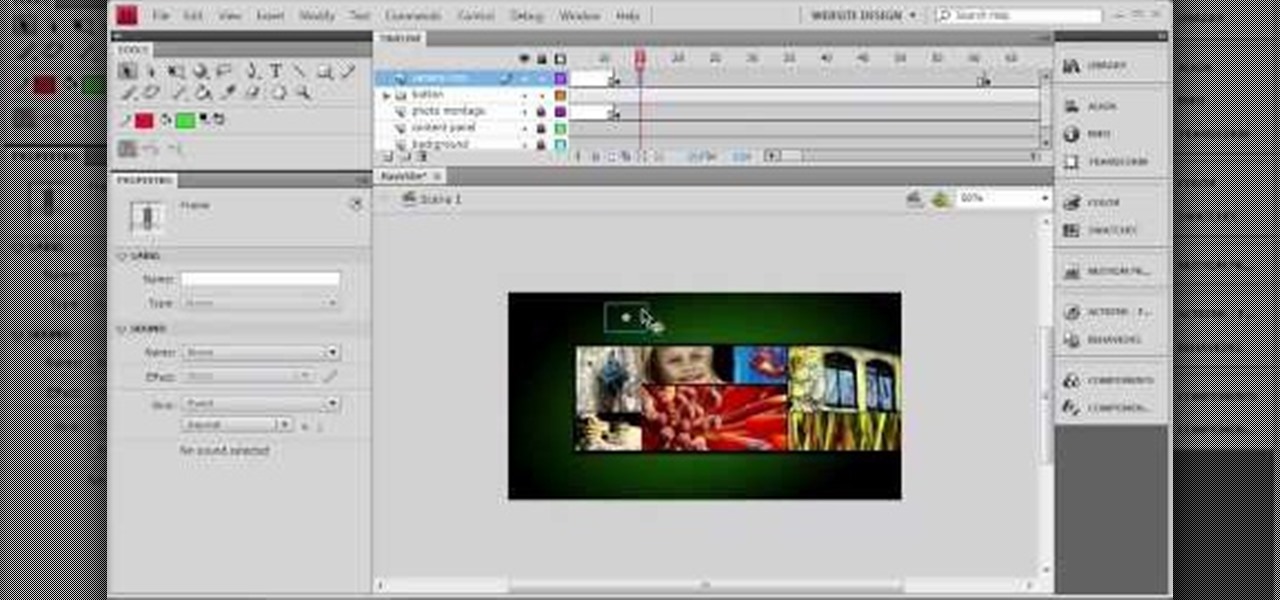
Creating a website using Flash CS4 is one of the most challenging and rewarding ways that you can utilize the internet. This video is chapter 5 of a comprehensive series of videos on designing your own website from scratch using Flash CS4. This chapter covers creating and using motion tweens to improve the animations on your site.

Other World Computing provides a guide for advanced users demonstrating the upgrade or replacement of a hard drive in a Mac Mini Server computer. This comprehensive video takes you through all steps from tool selection to re-assembling the Mac Mini Server and it is recommended that the video is watched right through before attempting the procedure. In particular, it demonstrates the difficulty of opening up a Mac Mini using a small putty knife. Once the case is off, the three wireless antenna...

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentially when you're rooted.

With the release of the Samsung Galaxy S5 right around the corner, the first full system dump has been released by Sammobile. As the inevitable ports of functioning apps slowly begin to leak, today we've got a non-app aspect of the system and the one that tends to leak first—ringtones.

This clip over a rehab technique called 90/90 using the Pilates Cadillac exercise device. Whether you're toying with the idea of opening up your own rehabilitative Pilates studio or merely need some help tackling a certain pedagogical or administrative problem, you're certain to be well served by this free video tutorial from the folks at Balanced Body Pilates. For more (and more comprehensive) information, take a look.

This clip outlines a number of simple Reformer-based Pilates exercises to improve a person's gait. Whether you're toying with the idea of opening up your own rehabilitative Pilates studio or merely need some help tackling a certain pedagogical or administrative problem, you're certain to be well served by this free video tutorial from the folks at Balanced Body Pilates. For more (and more comprehensive) information, take a look.

This clip demonstrates some rehabilitation exercises that you can use for clients who have suffered from an amputation. Whether you're toying with the idea of opening up your own rehabilitative Pilates studio or merely need some help tackling a certain pedagogical or administrative problem, you're certain to be well served by this free video tutorial from the folks at Balanced Body Pilates. For more (and more comprehensive) information, take a look.

Check out this how-to video to perform three beat weave poi. This poi lesson is for beginners who already know how to spin the two beat weave. The three beat weave poi move is an essential component of your poi twirling move-base. It'll be used a lot, so you should learn how to do it well. Here is a very comprehensive tutorial on how to do so.

Demonstrated by expert artists, it is a comprehensive guide to all the basic skills and materials needed to paint a wide range of popular subjects, and packed with practical hints and tips.
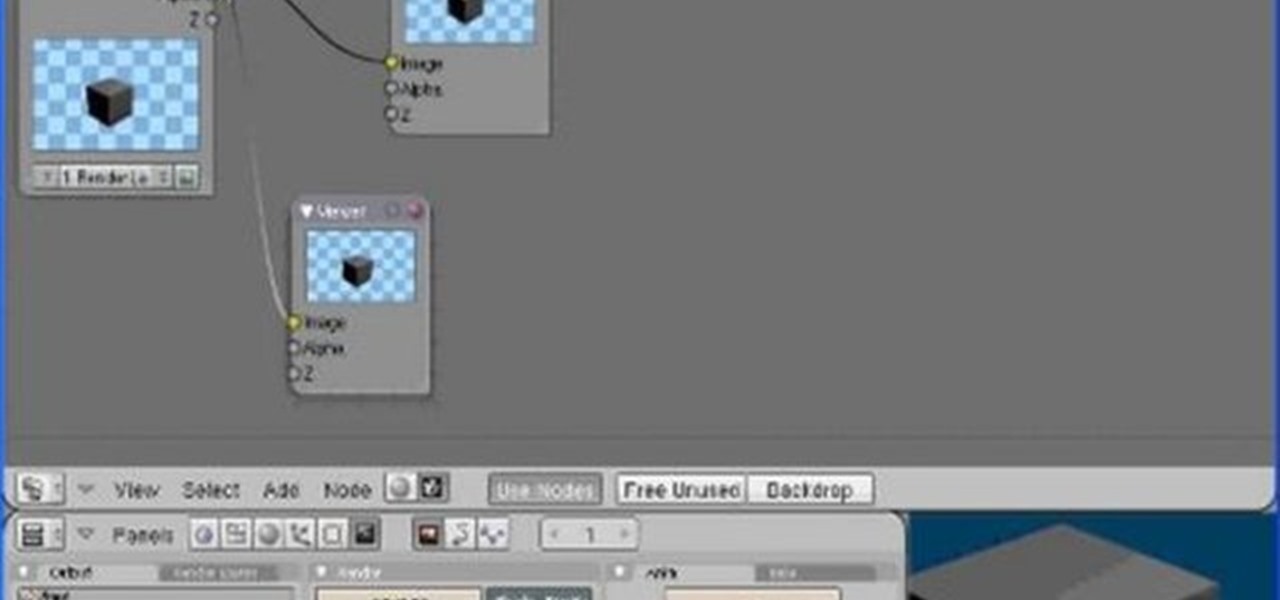
Conceptually, what is node-based compositing and what do nodes do? This clip uses the factory analogy to convey the concept. Blender can process video, images, sequences, and families of images in a directory. Then you'll fire up Blender and talk about threading nodes and how images are duplicated and routed through the compositing network ("noodle"), how threads are created between sockets. Creating threads, cut threads. The clip also points out common threading errors and misrouting threads...

Because of the way Android is laid out, you automatically lose a portion of the top and bottom of your screen thanks to the status and navigation bars. The thing is, you don't always need the navigation buttons. By hiding them, you can enjoy more of your Galaxy S10's big, beautiful display.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.
This is for those using Kali Linux 2.0 that need to edit the CRDA values to get the increase in Txpower

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION
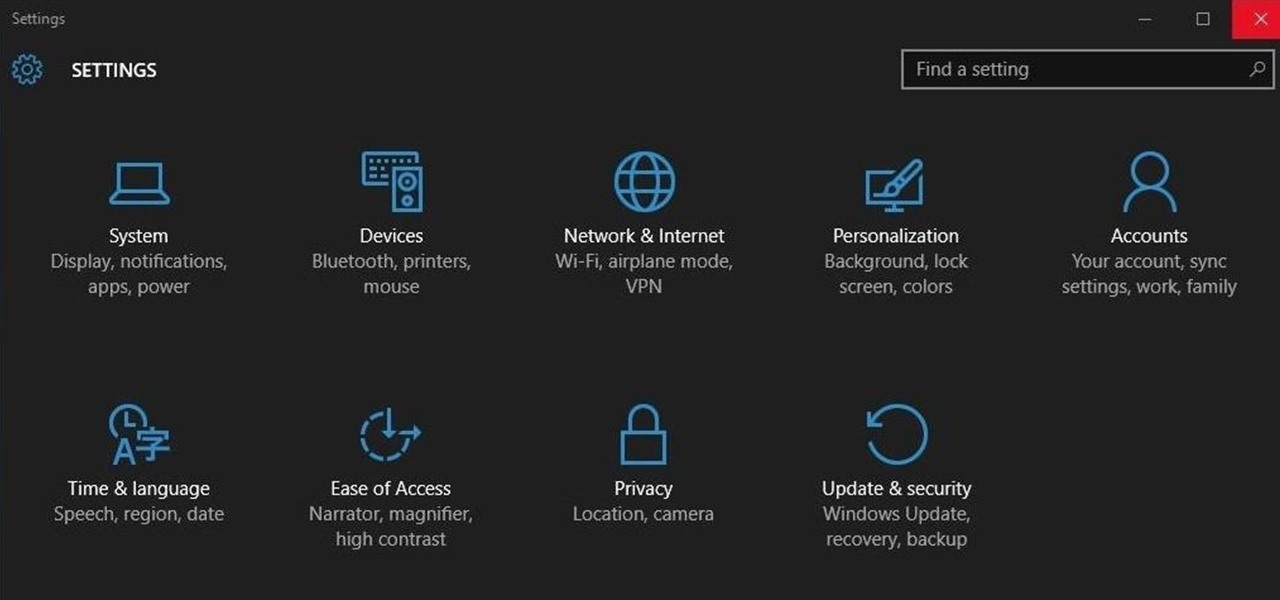
Ah, the fabled dark mode. In the past, many users were delighted to find the existence of something called Royale Noir, a dark theme option that was available for Windows XP. Yet for reasons unknown, Microsoft had kept knowledge of Royale Noir a secret until some bright minds discovered its existence, and the rest is history.

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.

We use ADB and Fastboot for so many things in our softModder tutorials, and to get them, you normally have to download the entire Android SDK and install them. But not anymore.
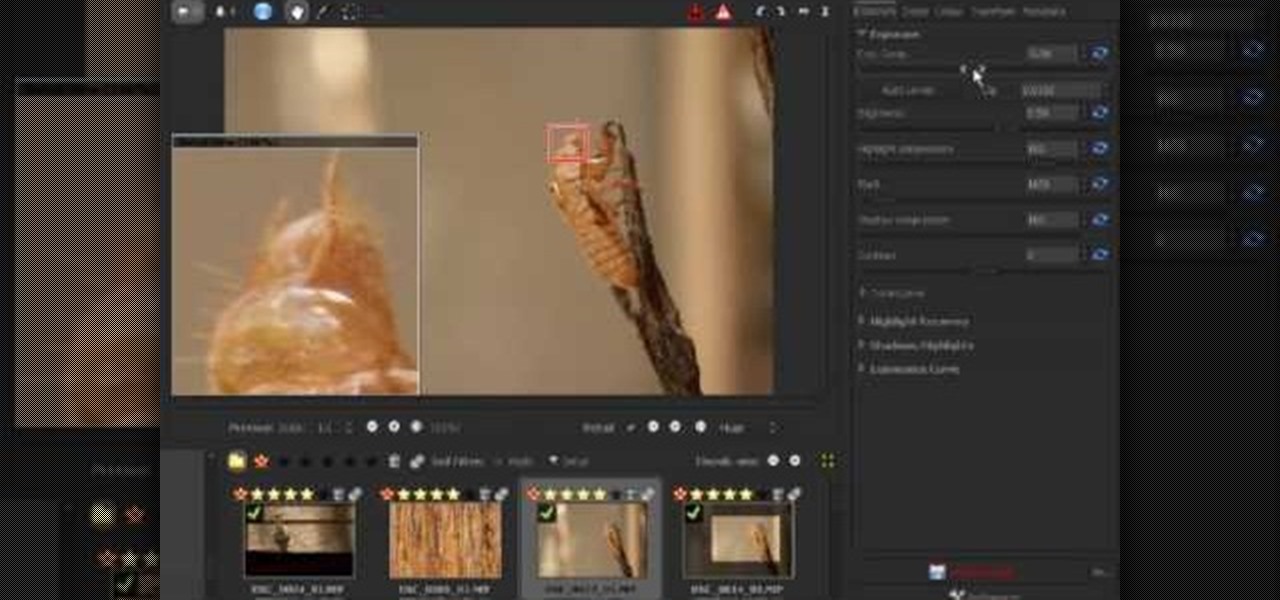
In this video, we learn how to use Raw Therapee with Gimp. First, you need to go online to Raw Therapee, then download and install Raw Therapee. Once you have this, open it up and familiarize yourself with the layout of the software and where the different tools are at. Next, change your preferences and pick your settings throughout the different folders. Next, find GIMP through the program folders as your installation directory. Now, it will export your images to GIMP automatically. This way...
First click the explore button, this will open a fold in which you will click homegroup and the second computer in the network. By clicking on that you will see what is in the homegroup. For example clicking on the video icon shows you all the videos available. If you right click on the video you can choose to watch it, open it, send it to different places, drag it onto your computer or copy and paste it into another directory.

There're plenty of great ways to get traffic, especially this off-site optimization technique using classified ads to point website traffic back into your site itself.