The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

What's in a name? Quite a lot. Learn how to choose a good one that targets your desired demographic. Whether you're considering the possibility of starting your own Pilates studio or already have one and just need a little help tackling a particular pedagogical problem, you're sure to be well served by this free video lesson from the folks at Balanced Body Pilates. For more information, including a comprehensive overview, watch this video guide.

Need help drumming up new business as a Pilates instructor? This clip presents an overview of the five principle benefits derived from the practice of Pilates. Whether you're considering the possibility of starting your own Pilates studio or already have one and just need a little help tackling a particular pedagogical problem, you're sure to be well served by this free video lesson from the folks at Balanced Body Pilates. For more information, including a comprehensive overview, watch this v...

Did you enjoy Fantastic 4? Was your favorite character Susan Storm? Well, this video is a comprehensive step by step guide to how to draw Susan Storm from Fantastic 4. The video gives very clear and simple instructions. There are very few requirements other than that the viewer should have a pencil and paper. The video gives great advice on how to draw female characters in general. By the end of the video, viewers should have a good idea on how to draw not just Susan Storm, but most female ch...

In this video tutorial the author shows how to use the Cosine Law. He shows how to find an angle of a triangle where he know all the sides of a triangle, using the cosine Law. He uses a lower case letter to designate a side and a capital letter to designate an angel apposite to that side. He gives the formula for the cosine law using a triangle as an example. Now he goes on and demonstrates how to use a scientific calculate. He shows how to use the degree mode in the calculator to solve these...

This video is about solving the Rubik's Cube in 5 easy steps. It gives an overview of the Rubik's Cube which may even be considered as surplus information for some people. It also describes common mistakes; for instance, trying to solve one face at a time. It goes on to give a recommendation that it is better to solve three layers at a time.

Taping fingers is good for minor injuries of the middle joint because taping supports the injured area without preventing motion. Learn how to tape fingers and stay fit in this sports medicine video. Take action: injuring the middle joints of fingers is common, try to support above and below joint but allow flexibility in the joint, check for deformities, while ice and anti-inflammatories can help. Mike Vera, the instructor in this how-to video from Live Strong, is an athletic trainer the Rog...

Everyone has experience foot blisters at one point in their life, whether it be from new shows or something other abrasive material. Prevent and treat blister wounds in a few simple steps. Watch this diet and health how to video to learn how to treat sports injuries.

If you suffer heel bruising you might want to consider using heel pads. Using heel cups and pads for rehab and treatment may aid recovery. Learn how to treat sports injuries in this how-to video on health and rehab.

Did you know that there is a difference between knee support and knee braces? Knee braces are great for stabilization, while knee supports have hinges and much stronger. Learn how to treat sports injuries with knee apparatuses in this diet and health how-to.

Compression pants, or compression shorts, are good for managing hamstring injuries without restricting motion. There are many styles of compression pants, which are also known as compression pants. Learn how to use compression pants and stay fit in this sports medicine how-to video.

Minor lower back injuries can occur during many physical activities. This is why it is important to use lumbar support to prevent and treat back injuries. Learn how to treat lower back injuries and stay fit in this sports medicine how-to video.

Slings and shoulder supports are good devices for minor shoulder strains. Learn how to use shoulder supports and stay fit in this sports medicine how to video. Another good suggestions for injured shoulders offered by our host includes getting lots of rest.

Fractured ribs can be painful injuries treated by a doctor and requiring pain management and adjustments in daily activities. Learn how to treat a fractured rib and stay fit in this sports medicine how to video. Watch and see how to use rib support to prevent further injury.

Runner's nipple is caused by shirt fabric rubbing against the tips of the nipples. Learn how to prevent getting runner's nipple and stay fit in this sports medicine how to video. All you need to prevent runner's nipple is band-aids or petroleum jelly. Watch and see how simple it is to take care of.

This comprehensive pottery sequence from Watchmojo.com will show you the basic steps of making pottery. You will be guided through the basic pottery making processes of wedging, prep, shaping, removing, firing, and glazing.

This comprehensive video series by Bob Davies serves as a basics drawing lessons that are excellent for beginners just starting off in addition to tips for intermediate artists. This series covers all the basics of drawing from choosing paper, drawing medium (graphite,charcoal,etc) and techniques in many of the different medium. These videos will cover pencil, felt pens, charcoal, pen and ink, watercolor pencils and erasing techniques.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

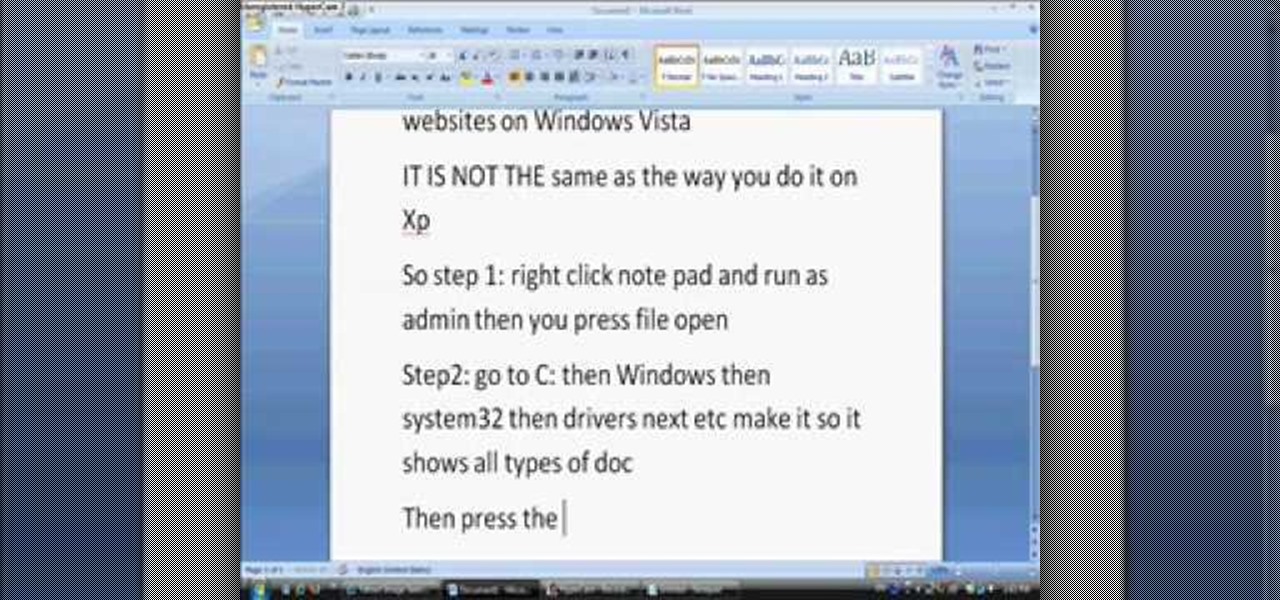
In this tutorial, we learn how to block websites on Windows Vista. First, you will right click on the notepad and then run as admin. From here, you will click "file open". Then, go to the C drive and open up windows. Then, you will go to the system and find the drivers, then click on the host file. From here, go to the second local host and press enter twice. Then, type in "127.0.0.1" and press tab. Then insert all the directories that you want to block. From here, you will be finished blocki...

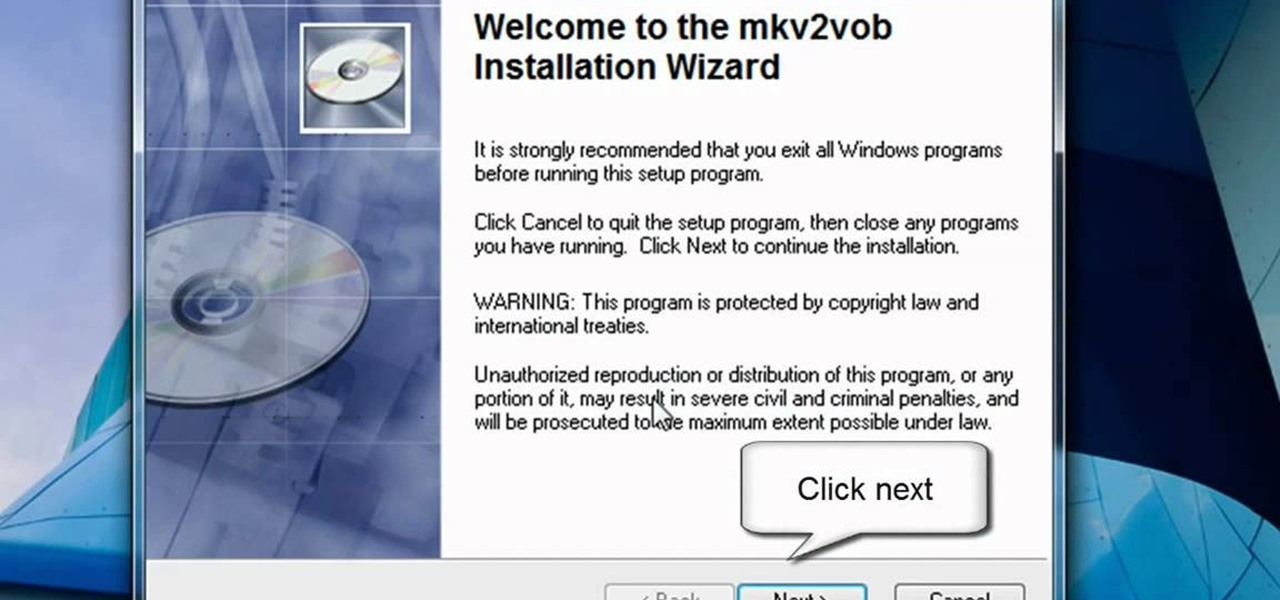
In this video tutorial, viewers learn how to play MKV videos on the PS3 using the MKV2VOB software. Begin by downloading the MKV2VOB programs from the link in the video description. Once downloaded, install it on your computer. Now open the program. Go the Configuration tab and change the setting to the same as the video. Then click on the Add File tab and select Browse under Source File. Find your MKV file and select Open. Then under Destination Directory, select where you want your file to ...

In this video the instructor shows how to hide any kind of file in a .Jpeg image file. To do this take the image in a new folder. Go to start button and then to run. Type cmd in the run and hit enter to open the command prompt. Now browse to the directory that contains the picture and also the file that you want to store using the CD command. Type the command to create our required file as shown in the video. Now a new file will be created that contains your image as well as the file that you...

Brizdo shows you how to download free music from MySpace using the Real player in this walk through video. This video shows how to first select download and install the real player that is most suitable for free use. Next by doing a MySpace search for the artist and visiting the MySpace page of that artist the music track that are on the artist's page can be downloaded by a few clicks. The downloaded tracks can be found in the Real players download directory usually in 'My Documents'.

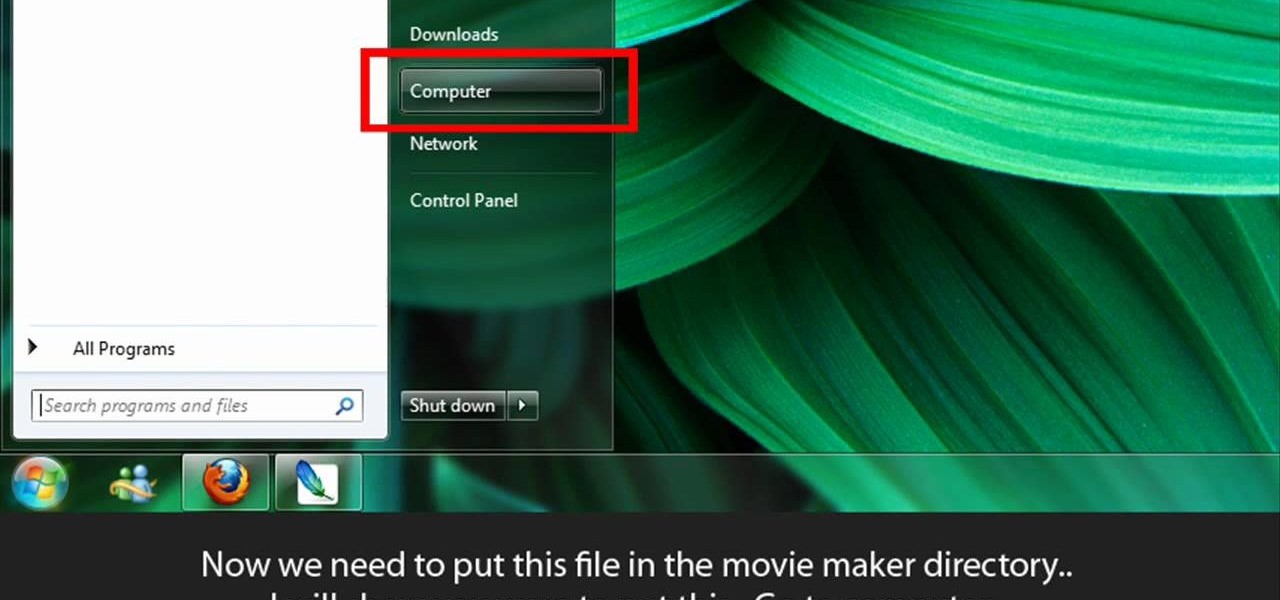
Learn to make HD Video With Windows XP's Movie Maker with this video tutorial. First, go to PapaJohn, there is WMV-HD at the left hand side of the screen. Expand that and click on the Introduction, then 1280*720 link. Download begins, save file on you hard drive. It has to be in the movie maker directory. It is in Program Files - Movie Maker - Shared Link. File must be added in the folder Profiles. Put it there, and if you don`t have such folder, create it. OK, we can start movie maker and ma...

In this tutorial video, we show you how to jailbreak Apple's latest device the iPhone 3G to start the process you need to do the following:

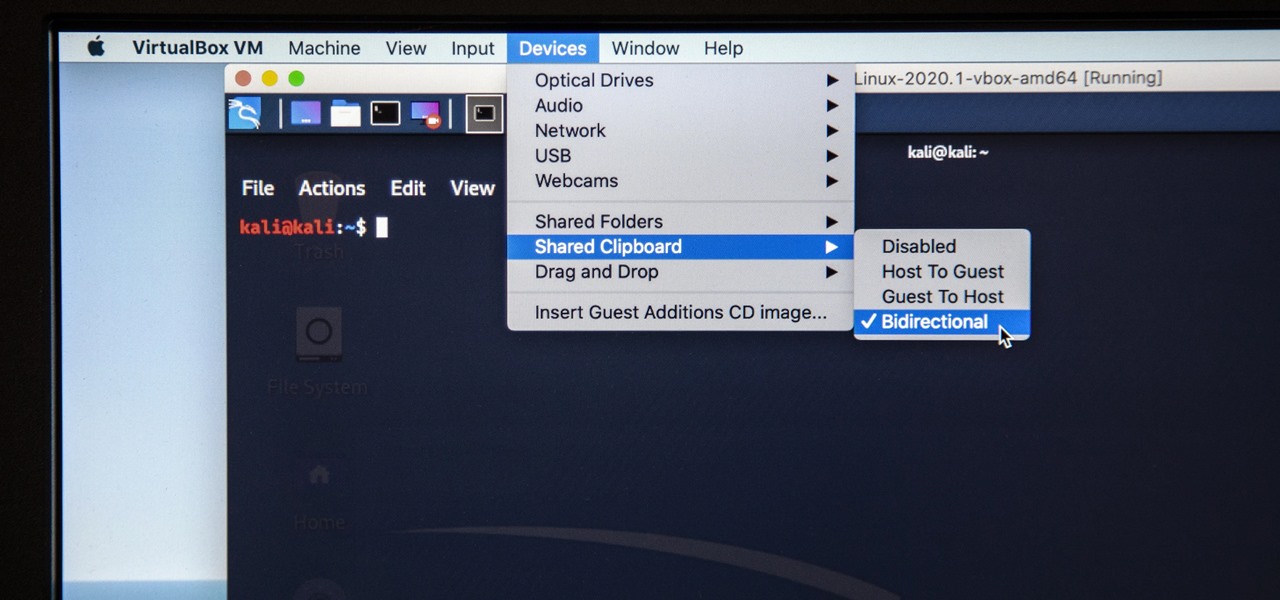
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared clipboard was enabled, but there was one thing that did work for me that may help you out too if you experience the issue.

Android 10's new dark mode is a pleasure to behold for longtime users. Ever since OLED panels became widespread, we've been clamoring for the feature. But now that we have it, there's a new problem: it doesn't turn on automatically based on time of day. Thankfully, a simple app can turn dark mode into a true night mode.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to modding Android.

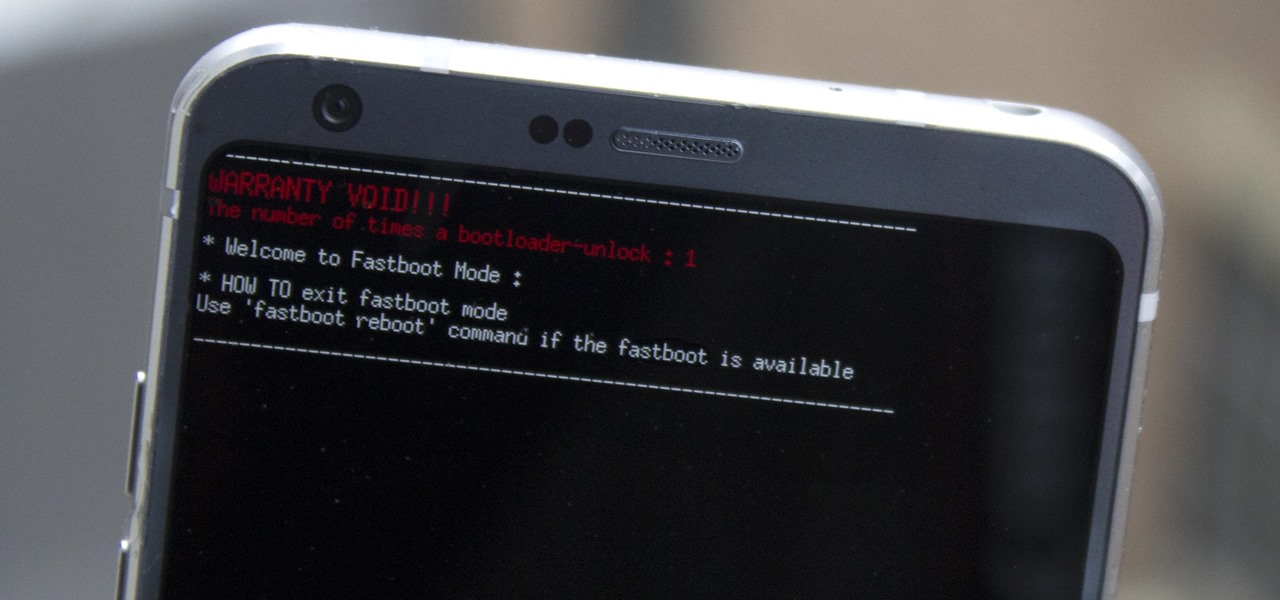
Preorders for the LG G6 have all been fulfilled, and the phone has been up for grabs at local cell phone providers for three weeks now. However, not every LG G6 was created and released equally. The T-Mobile variant of the LG G6 features an unlockable bootloader, while most other North American variants come with a tightly locked down bootloader, which effectively limits the full potential of your brand new fairly expensive phone.

Android's flexible operating system allows for lots of customization, and one of the most common ways to add personal flair to your smartphone is to set your own ringtones and notification sounds.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a developer. Aside from developers, the command line tools can offer benefits to normal users as well, like the ability to purge RAM for better performance.