Along with rebranding Magic Leap 1 for enterprise customers, Magic Leap has gifted its developer community with some new toys with a tease of more to come in 2020.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.
When it comes to shooting games, battle royale titles like PUBG and Fortnite have come to dominate the scene, leaving other sub-genres like top-down and third-person shooters living in the shadows. They're far from irrelevant, though, as evidenced by all the great games released just in 2019 alone.
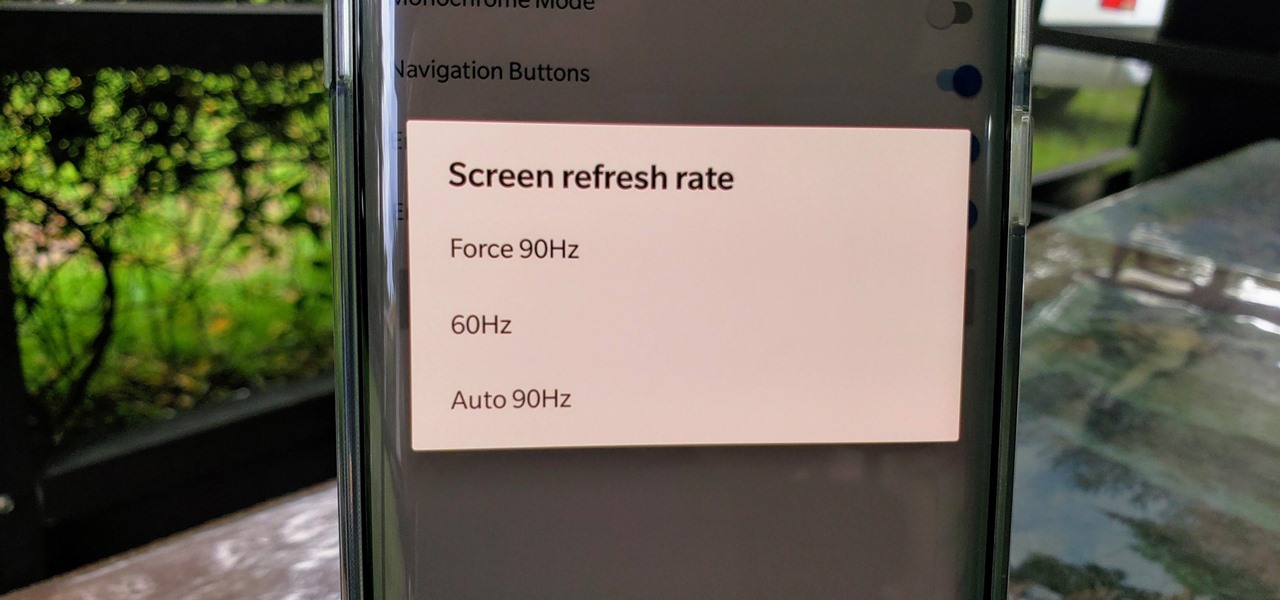
One of the standout features of the OnePlus 7 Pro is the 90 Hz display. A higher refresh rate means smoother gameplay for all your favorite games, which is precisely what you'd want out of your gaming experience. However, not all games play nicely with these higher refresh rates — but luckily, there's a pretty simple fix.

What does mainstream augmented reality look like? I'm not talking about the stuff you see in concept videos and science fiction films. No. What does it really look like?

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

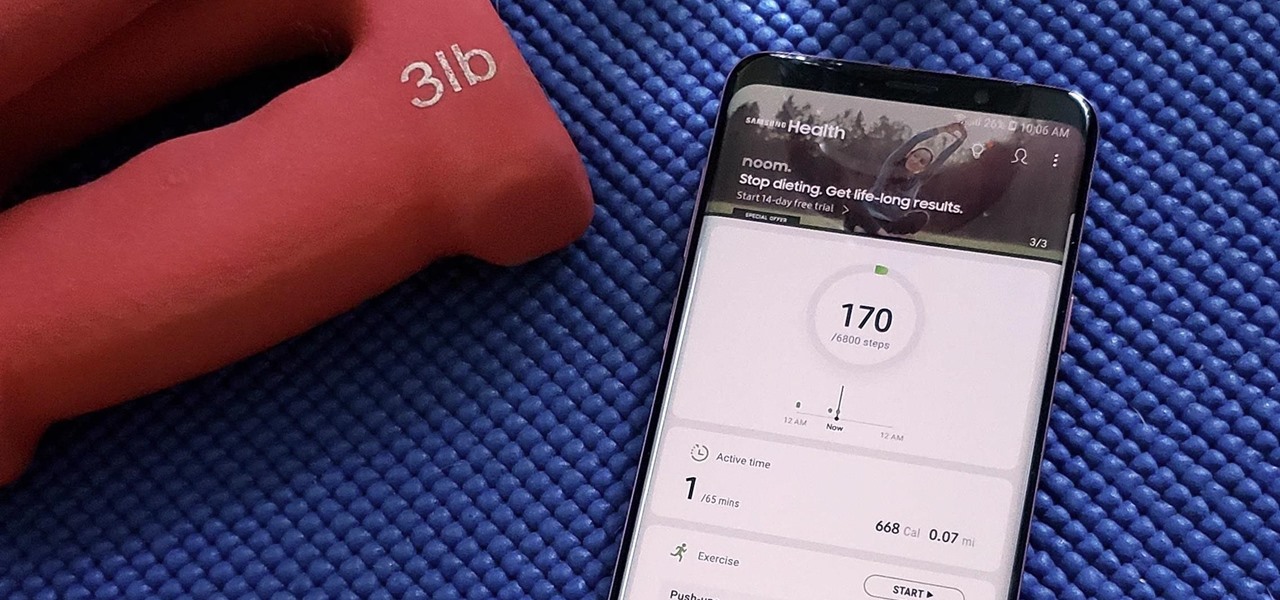
Samsung Health has become one of the most comprehensive wellness apps thanks to features that cover everything from step counting to nutrition logging and symptom diagnosis. But because the app has so much to offer, it can be easy to overlook some smaller, but useful features.

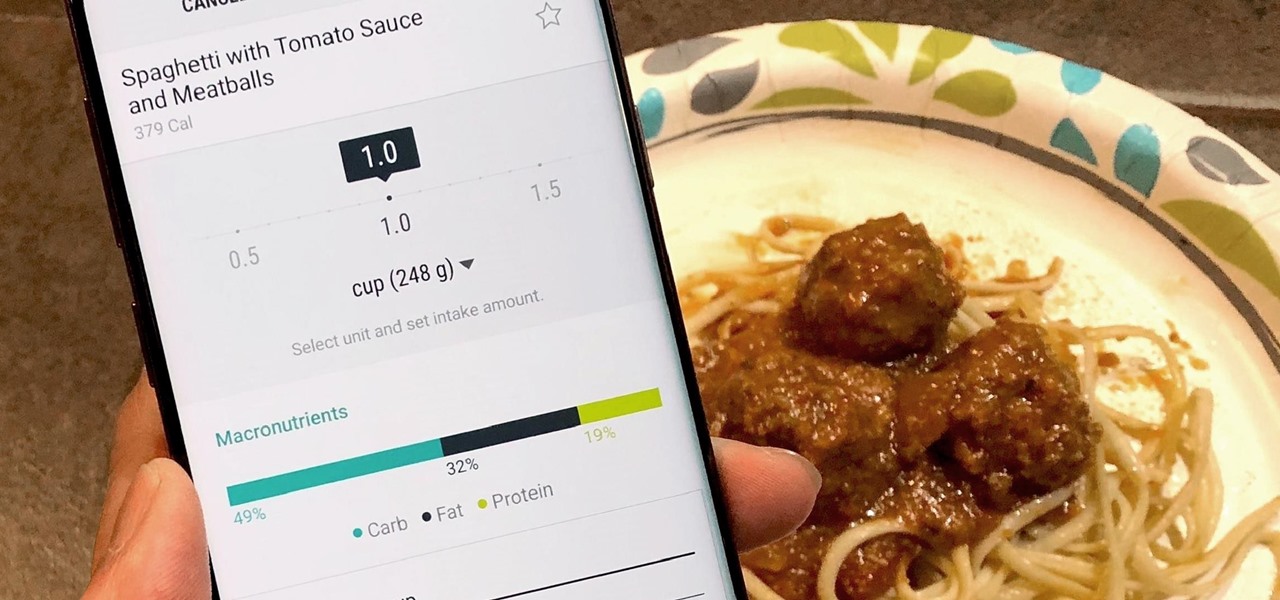
The most essential part of a healthy lifestyle is managing your diet — after all, what would be the point of a daily workout regimen if you were eating junk food? Thankfully, Samsung Health makes it easy to record your calorie and nutrient intake to get a clear picture of your dietary habits and how you can make them better.

If you've ever been on the receiving end of a threatening phone call, you'll immediately know the value in being able to record phone conversations on your iPhone. Beyond that extreme example, however, recording calls is still an extremely useful feature to have for important conversations like business meetings and verbal agreements, and it's totally doable with a third-party app.

Two companies armed with web-based augmented reality tools, Vertebrae and Shopify, are ready to help online retailers boost their sales.

By far, one of the biggest advantages to having a jailbroken iPhone is being able to apply custom themes to Apple's user interface and truly set your device apart from the rest of the crowd. And if you want to change your iPhone's app icons from rounded squares to circles for an entirely unique look, there's nothing stopping you.

It seems like each day new rumors and leaks come out for Huawei's upcoming P series devices. Everything from its name change to its specs has been leaked, sometimes with contradicting rumors. One of the biggest leaks is the inclusion of triple rear cameras, a first for smartphones.

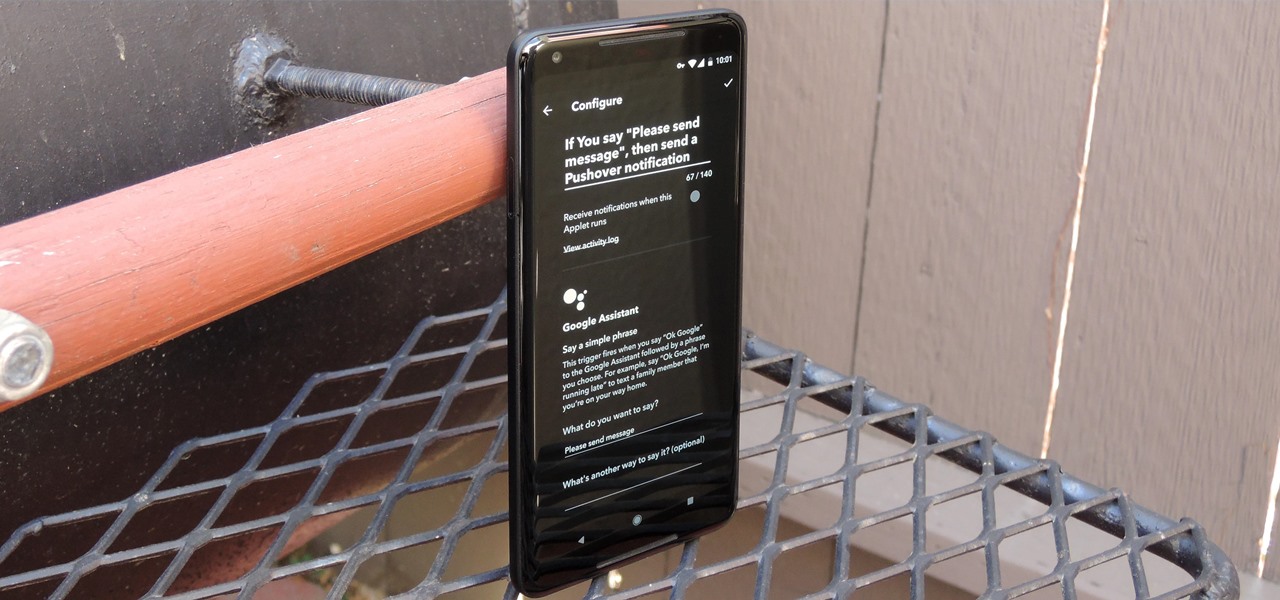
IFTTT is a fantastic tool that lets you trigger actions on your smartphone that normally require more advanced hacking. With the help of its friendly user interface, turning your phone into a more personal device has never been easier. However, the app has some more intricate options under the surface, making advanced implementations of applets difficult for beginners.

IFTTT (short for If This, Then That) is an amazing piece of software that automagically links actions on your phone with online services and real-world objects. For example, an applet could read: "if you come home, then turn on Wi-Fi." IFTTT goes further than just using simple smartphone functions, though — thanks to applets, it's fully configurable with a ton of smartphone apps.

At this point, we've seen Samsung's vision for Android Oreo on both the Galaxy S8 and Galaxy Note 8. Just last month, Samsung opened its Oreo Beta Program for the S8 to the public. A few days ago, we obtained and detailed a leaked beta build of Oreo for the Note 8. While both of these updates have some compelling new features, there are always tweaks we hoped to see that didn't make the cut.

Update 10/23: The hits just keep on coming. We're now seeing reports of a "smearing" effect when scrolling through apps on the Pixel XL 2. We'll expand on that at the bottom of this article, but it's still worth reading the background information on issues with LG's new POLED displays.

The Pixel 2 is a solid upgrade when compared to the 2016 model, but we've reached a point where the latest generation of a smartphone is never leaps and bounds better than the last. It's hard to justify dropping nearly a grand on a phone when it doesn't improve your situation much — especially when a few software tweaks will give you most of the upgrade for free.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Blowing dust and fungal spores are creating a public health problem that could be just a slice of what's to come with climate change.

The large, dome-shaped LiDARs that have become a fixture on driverless car prototypes are expensive and notably ugly. And yet, these unsightly devices should remain planted on driverless cars, even when they become available in commercial fleet services across the country in a couple of years.

When you have an infection, a doctor prescribes antibiotics to make the bacteria that causes it disappear. Sounds like a good idea, but the disappearance of microorganisms that have inhabited humans for millennia could be driving rising numbers of serious illness and debilitating conditions.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

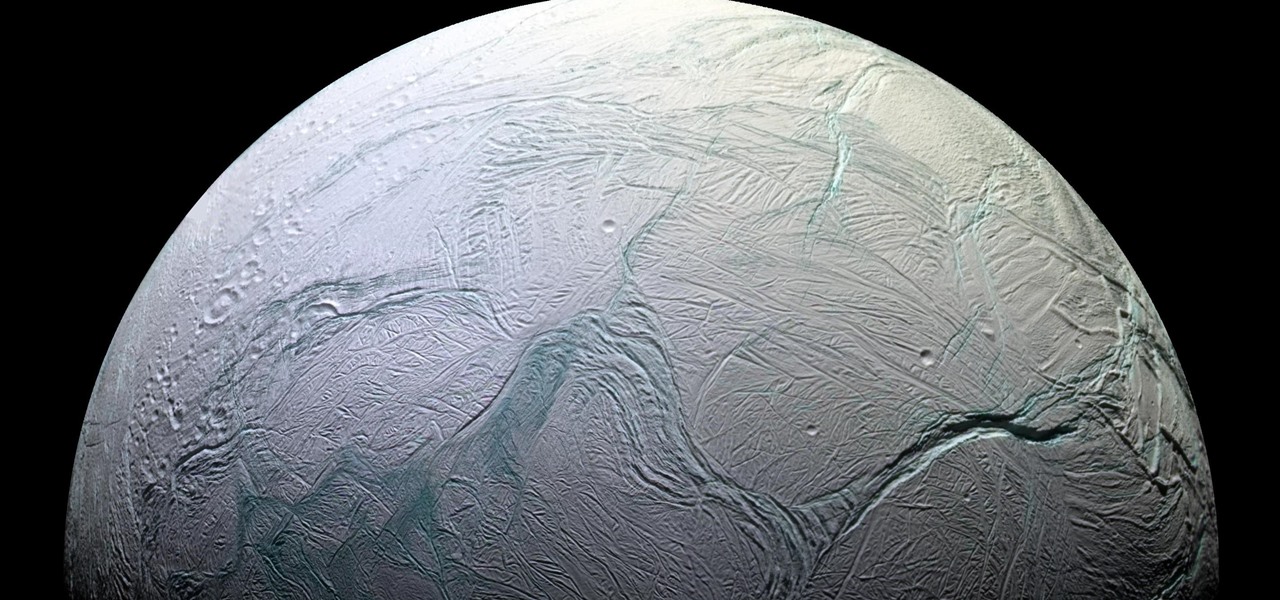
Earlier this year, NASA reported on findings that might point to water, and microbial life, on moons orbiting Jupiter and Saturn. Named Europa and Enceladus, those moons contain large oceans under their icy surfaces, which many speculate could hold microbial life.

The best go-to method for reducing your risk of infection is to wash your hands. Next time you reach for the soap, here is some news you can use.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

By connecting the dots between theory and real-life effect, two new studies offer more proof that neonicotinoid insecticides are causing extensive damage to honeybee colonies.

Bed bugs are parasites not yet known to spread disease — but they cause plenty of irritation. As scientists and landlords search for new ways to deal with the pests, a new study examines how we can deter bed bugs without so many chemicals.

There is a reason the Amanita phalloides mushroom is called the "Death Cap." It can kill you. Mushrooms are a type of fungi, an organism that produces thread-like mycelia that often produce spores. Spores allow the fungi to reproduce. Molds, lichens, and yeast are all fungi, but the most visible fungi are mushrooms. Some fungi are delicious, but others can cause disease or, and still others, like Penicillium, can cure it.

Apple's been hard at work adding new features and finishing touches to iOS 11, and there's evidence of it everywhere. But there's one place where these changes are more noticeable than perhaps anywhere else — Safari.

Samsung's recent TouchWiz rebranding didn't really change much — the skin is still as bloated as ever, and the UI still uses tacky accent colors. But while you can't fully remove TouchWiz without rooting, there are ways to make it look a lot better.

The future of forests looks dreary in the face of a warming climate, but scientists are exploring the relationship between soil microbes and the ability of trees to move to higher altitudes, a key component of their survival.

If you have encountered bed bugs lately, you are not alone. While the pesticides used to fight these pests are losing effectiveness, a fungus shows promise in knocking the bugs out of beds everywhere.

When it comes to global warming, most of us think of carbon dioxide emissions. While carbon dioxide is the most important greenhouse gas, carbon dioxide emissions have stayed constant for the last three years. On the other hand, methane, the second most important gas, has been steadily rising since 2007.

When we talk about driverless technology, the go-to companies are usually Waymo, Uber, or Tesla. However, traditional automakers like Ford and GM are also staking claims to the driverless and advanced driver assistance spaces.

For some, drinking raw milk is a way to get back to nature, improve family nutrition, and hedge against asthma and allergies. However, according to public health authorities, drinking raw or unpasteurized milk is a big mistake—even fatal. So what's the story?

With new diet and health claims coming at you everyday, it's sometimes hard to know what to believe. Well, here's a bright spot: A pair of studies confirm that whole grains are healthy for you, and for the diversity of microbes living in your gut.

If you've got big plans to lose weight and get healthier in 2017, know up front that it will be an ongoing challenge. It's not easy to break bad habits, and it's even harder to form new and better ones.

In the first part of my containers series, we learned how to install Docker on our local machine, pull down "hello-world" and Ubuntu containers, SSH into containers, and install software when in a container. Now, we're going to work on building, customizing, and storing our refined hacking Ubuntu container. Before we dive right in, though, let's make sure we still have a functional Docker installation.

Google's former Self-Driving Car project, now graduated from Alphabet's X division as Waymo, has found a collaborator and potential new partner in Honda. This is an interesting turn of events given traditional automakers' reluctance to work with driverless-car startups over the years.

Hear me out. No, really. Before you sharpen your pitchforks and give me anecdotal evidence of your Chinese restaurant syndrome, I think you need to know a few things about monosodium glutamate. First of all, it's a naturally-occurring chemical compound that can be found in anything from tomatoes to cheese, and is used in all kinds of foods from KFC to breakfast sandwiches. So spare me the comments on MSG and Chinese food—you probably eat MSG on a daily basis without even knowing it. (And also...