Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

To some, SCRABBLE is just a board game to play during family game night or during a casual get-together. Others think of SCRABBLE as a mere hobby. But with any activity, there will always be fanatics—the ones who would rather sell their soul than stop—the ones with a constant yearning for self-improvement—the merciless.

Still on the fence about Apple's native Notes app? The latest Notes update for iPhone, iPad, and Mac is about to change your mind. With some fantastic new features and plenty of valuable tools from previous software versions, Notes is becoming a clear winner when it comes to saving important information from your personal and professional life.
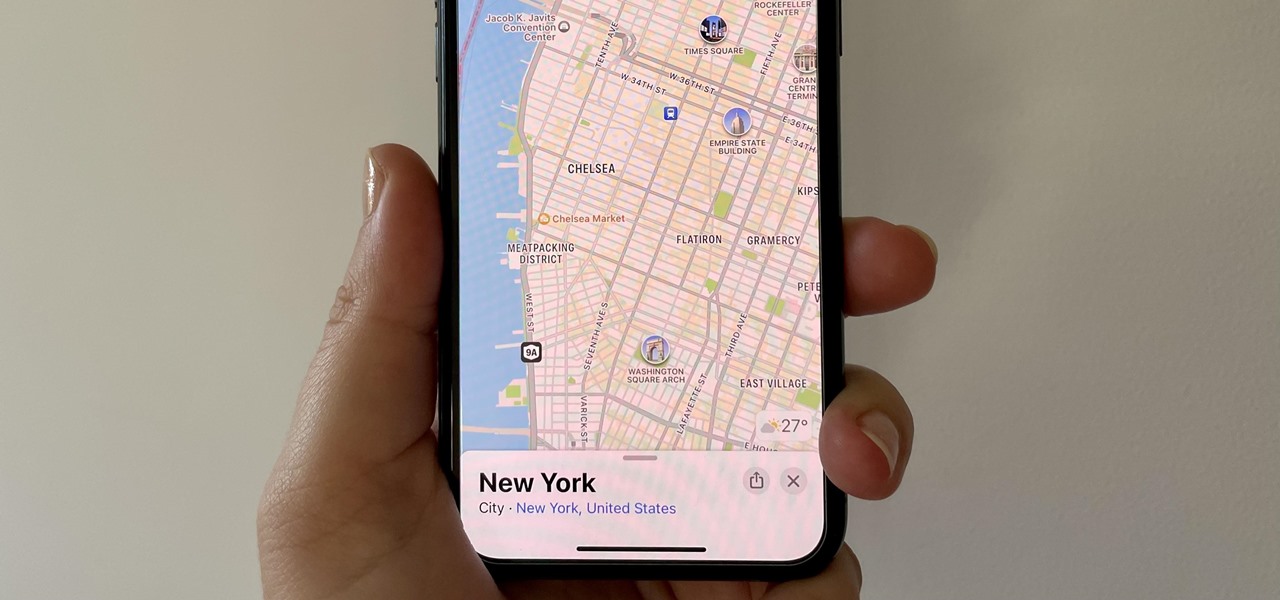
While the Maps app hasn't received as big an update in iOS 16 as Books, Messages, Photos, and Weather did, there are still quite a few exciting new features to enjoy on your iPhone.

There are tons of tools out there that do all kinds of recon, but it can be hard to narrow down what to use. A great way to be more efficient is by taking advantage of scripting. This doesn't have to mean writing everything from scratch — it can simply mean integrating existing tools into a single, comprehensive script. Luckily, it's easy to create your own subdomain enumeration script for better recon.

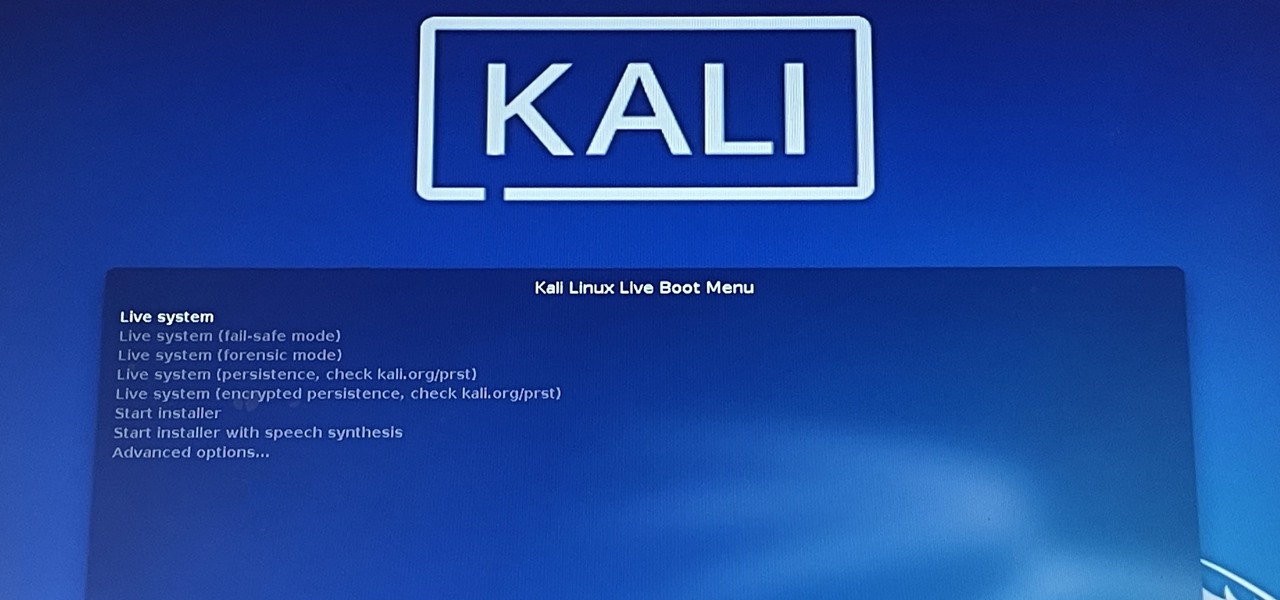
Kali Linux is the go-to Linux distribution for penetration testing and ethical hacking. Still, it's not recommended for day-to-day use, such as responding to emails, playing games, or checking Facebook. That's why it's better to run your Kali Linux system from a bootable USB drive.

As a hacker, the final stage of exploitation is covering their tracks, which involves wiping all activity and logs so that they can avoid being detected. It's especially crucial for persistence if the target will be accessed again in the future by the attacker.

You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers.

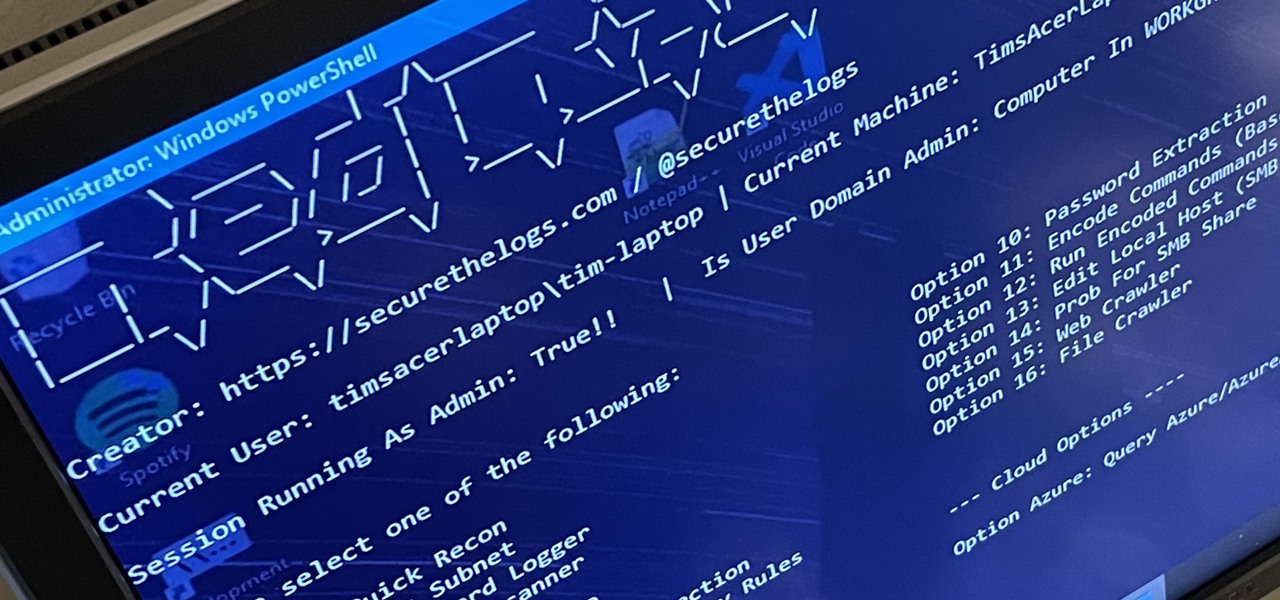
RedRabbit is an ethical hacking toolkit built for pen-testing and reconnaissance. It can be used to identify attack vectors, brute-force protected files, extract saved network passwords, and obfuscate code. RedRabbit, which is made specifically for red teams, is the evil twin of its brother, BlueRabbit, and is the offensive half of the "Rabbit Suite."

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

Are you tired of endless rows and columns of apps on your home screen? Before iOS 14, your only option was to hide apps in folders, uninstall them, or use some sort of elaborate workaround. You could hide a few stock apps easily enough, but that's it. Now, in the latest version of iOS, you can hide apps for real, and even hide entire home screen pages, and still access the apps in one convenient drawer.

Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some significant changes to how it's used.

In the case of Apple Watch v. Fitbit, the winner comes down to the judge at hand. Apple currently offers two smartwatches — the Series 5 and the Series 3 — while Fitbit offers three models — the Fitbit Versa 2, Fitbit Ionic, and Fitbit Versa Lite. Whatever your assumptions about these devices are, throw them out the window, as each has something unique to bring to the table.

If you have a modern iPhone, you have an excellent video recorder at your disposal. Every iPhone since the 6S has the ability to shoot in 4K resolution, and each new iteration has brought new capabilities to the table. But even the best mobile shooter can use a little extra help. That's where these video recording apps come into play, to ensure the footage you capture is as good as can be.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

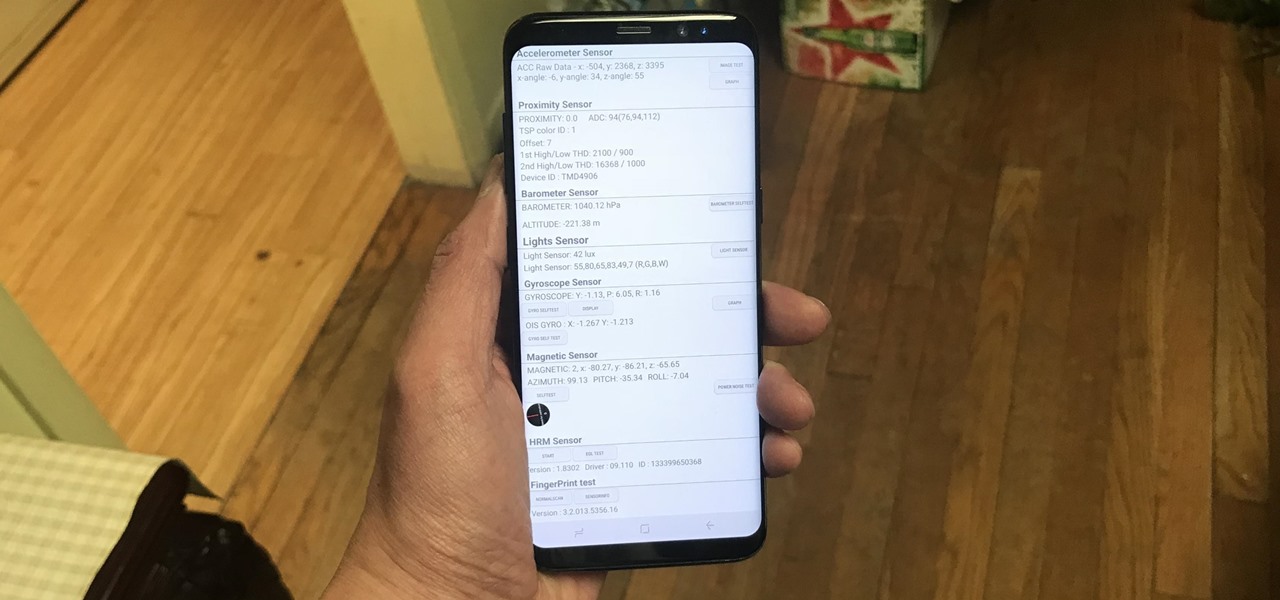
Besides obvious features like a touchscreen and biometric sensors, the modern smartphone comes with an array of state-of-the-art hardware in the form of various sensors that help your device sense the environment around it. And if you have a Samsung handset, chances are, you have a handy feature built in that enables you to check if these sensors are functioning 100 percent.

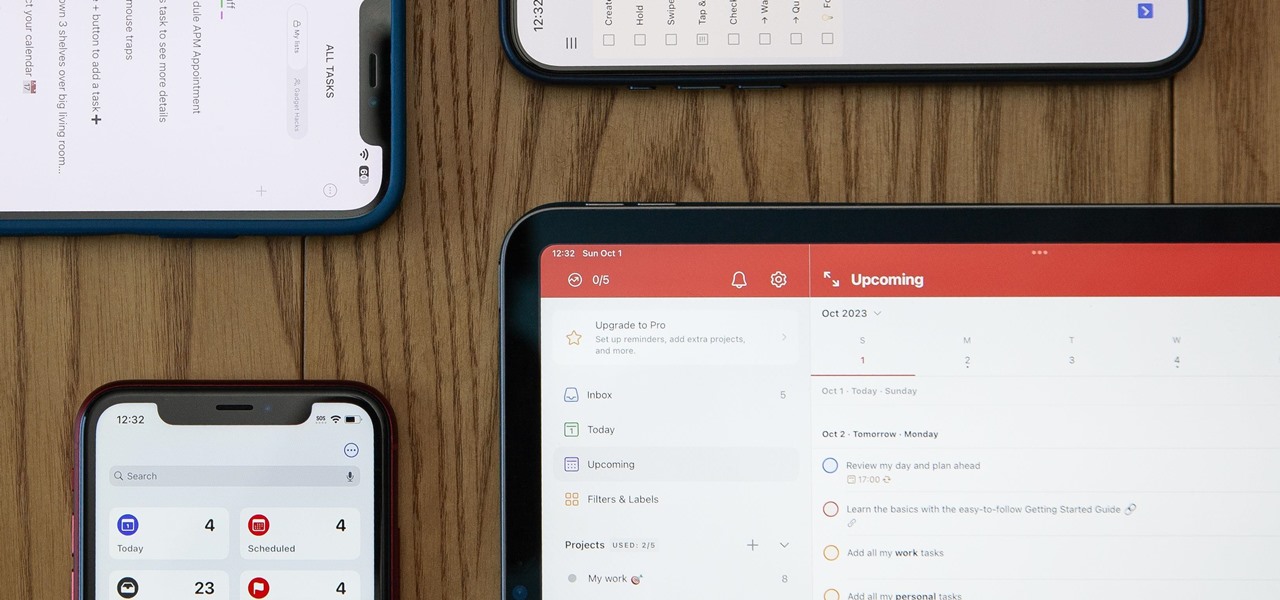
When you want a helpful task manager on your iPhone or iPad, any of the nine apps in this guide should be at the top of your list. But we'll review each app's features to help you determine which one might be best for your workflow.

Apple's iOS 16.3 update for iPhone had impressive new features, but iOS 16.4 might impress you even more.

Rumors about the 2022 iPhone series stirred well before the iPhone 13 models were even released. While Apple remains quiet on the next big iPhone, as it always does, we're seeing more and more leaks and reveals for the iPhone 14 series as we lead up to a likely fall release.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

Trying to figure out which music streaming service to subscribe to can be a difficult task when the playing field is so crowded. Each has its benefits, as well as downsides, so finding the right one for your needs and wants can take a lot of overwhelming research. But we've done all the research for you to help you find the best music subscription your money can buy.
The House of Representatives has approved an amendment to the draconian National Defense Authorization Act (NDAA) that will limit the Department of Defense from using data collected by unmanned spy drones against Americans.

Ordinary invasive fingerprinting techniques, such as dusting, are prone to damaging evidence. Micro-X-ray fluorescence images fingerprints without touching them. By stimulating atoms to emit signature wavelengths of light, MXRF also provides chemical information -- such as traces of soil or saliva left in the fingerprints -- in addition to the print pattern itself. Avoid invasive fingerprinting techniques.

Citing no evidence, and on the heels of yet another baseless “activist” report claiming a massacre has taken place in Homs, nameless US officials claimed to the Wall Street Journal that the Syrian government is taking chemical weapons out of storage for possible use “against anti-regime rebels or civilians, possibly in an ethnic cleansing campaign.” » False Flag Alert: US Claims Syria “Moving Nerve Gas Out of Storage” Alex Jones' Infowars: There's a war on for your mind!.

Learn how to prick out seedlings with Monty Don's comprehensive video advice. Sow your seeds in a general, all purpose peet compost. Now you want to prick out the seedlings! Follow along with these expert instructions on how to sow your young seedlings. Prick out seedlings.

Adobe Photoshop CS4 is the industry-standard software for perfecting digital images and is ideal for professional photographers, serious amateur photographers, and graphic designers. In this Adobe Photoshop video tutorial, you'll learn how to use medical analysis tools in Photoshop CS4. For comprehensive instructions on using CS4's new medical analysis tools, take a look. Use medical analysis tools in Photoshop CS4 Extended.

Part of the charm of hardwood floors is their imperfections. Slight variations in grain and color, as well as the minor spots and specs in the wood help provide an aged-to-perfection look for your floors. However, you may encounter a cracked plank or damage to a section of your floor that doesn't look quite so attractive.

Learn how to care for canna plants with Carol Klein's comprehensive video guide covering planting, overwintering, and dealing with viruses such as canna yellow mottle, and bean yellow mosaic.

Adobe Photoshop CS4 is the industry-standard software for perfecting digital images and is ideal for professional photographers, serious amateur photographers, and graphic designers. In this Photoshop CS4 tutorial, you'll learn how to use CS4's new, streamlined layer management features. For (reasonably) comprehensive instructions on working with layers within Adobe Photoshop CS4, watch this how-to. Work with layers in Photoshop CS4.

Adobe Photoshop CS4 is the industry-standard software for perfecting digital images and is ideal for professional photographers, serious amateur photographers, and graphic designers. In this Photoshop CS4 tutorial, you'll learn how to use image cropping with Adobe Photoshop. For more information, including comprehensive instructions on how to use Photoshop to crop an image, watch this digital image editing how-to. Crop an image with Adobe Photoshop CS4.

Adobe Photoshop CS4 is the industry-standard software for perfecting digital images and is ideal for professional photographers, serious amateur photographers, and graphic designers. In this Adobe Photoshop tutorial, you'll learn how to use Photoshop CS4 to resize images. For more information, including comprehensive instructions on image resizing, watch this video tutorial. Resize an image in Photoshop CS4.