In this how to video, you will learn how to use the Nerf Gun Long Shot. First, you will need to know about the magazine. These can hold 8 shots and are spring loaded. Do not load 8 shots, as it will jam. Instead, load 6 shots to prevent this. The shots can be used in other guns, but the Long Shot magazine can only use this shots. The holes in the shots make a whistling sound. If you get shot, you will feel it regardless of distance. The gun has a trigger, a mount, a quick grab design, a hidde...

Kessler's flagship camera crane is the KC-8 Basic, and the KC-Lite 8.0 offers a stripped down, easier to manage version. In this tutorial you'll learn how to put together the KC-Lite crane, and you'll also get a quick demonstration of the crane in action.

It's no secret that the vast majority of Null Byte readers range from beginner to seasoned coding pros and developers. Regardless of whether you're interested primarily in building websites or creating best-selling apps and games, working with a wide variety of programming languages remains one of the best ways to make serious money in an increasingly app-driven world.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

A partnership between augmented reality company Zappar and IoT services provider EVRYTHNG will bring AR experiences to consumers while supplying market data to brands.

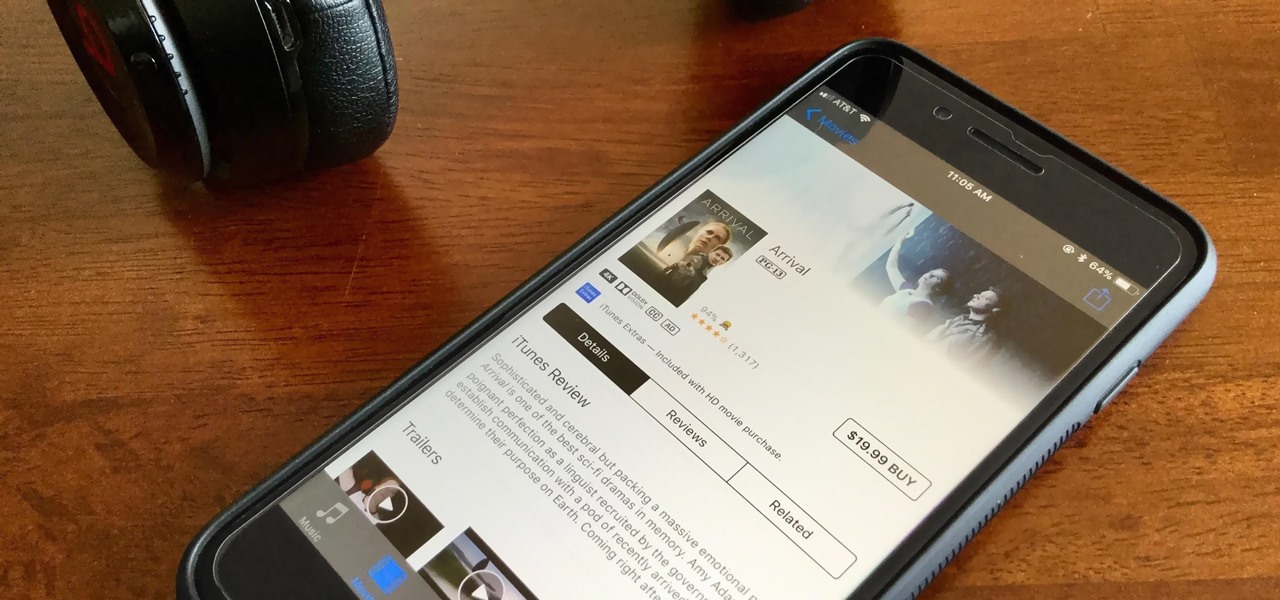
HDR, or high-dynamic range, is currently the best way to view movies and TV shows on your iPhone 8 or 8 Plus. With a wider color gamut and a broad luminance range, there's no beating HDR video for the ultimate viewing experience. Unless, of course, you don't have the storage to hold those giant Dolby Vision or HDR10 files.

While it might be a little past its prime now, the running gag about Nokia phones never breaking was one of the internet's favorite jokes. "If you buy one," they would say, "you'll never need another phone again." I think if those users could see into the future, they'd change their tune, as the Nokia 6 is now available to preorder — and I'm guessing it would give any of Nokia's old bricks a run for their money.

One major component of Level 4 and Level 5 driverless cars is in very short supply. Venture capitalists and engineers from around the world are racing to fill the LiDAR production, price, and performance void.

Headphone drama has been all the rage in the past year, with Apple killing off the headphone jack and trying to force AirPods upon its users (Apple, stop trying to make tiny, expensive, easy-to-lose earbuds happen. It's not going to work).

The technology driving the automated vehicle revolution relies on the car's ability to see and understand the world around it.

Joyce Kuo of Nijie Technology released a video showing a group fighting it out Dragon Ball Z-style in a restaurant, but instead of Goku, Piccolo or Vegeta, we have two horse-headed young ladies shooting fire and other elements at each other.

Welcome back! Sorry for being so quiet, I've been rather busy with this project lately! Anyways, in the last iteration of how to train your python, we covered lists. Today we'll be introducing iteration and the two loops python has to offer, for and while. Also, we'll be covering a couple general use functions. So, let's get started!

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

A security analyst has discovered a flaw in Chromecast's initial setup process that allows would-be hackers to assume full control over the online streaming device.

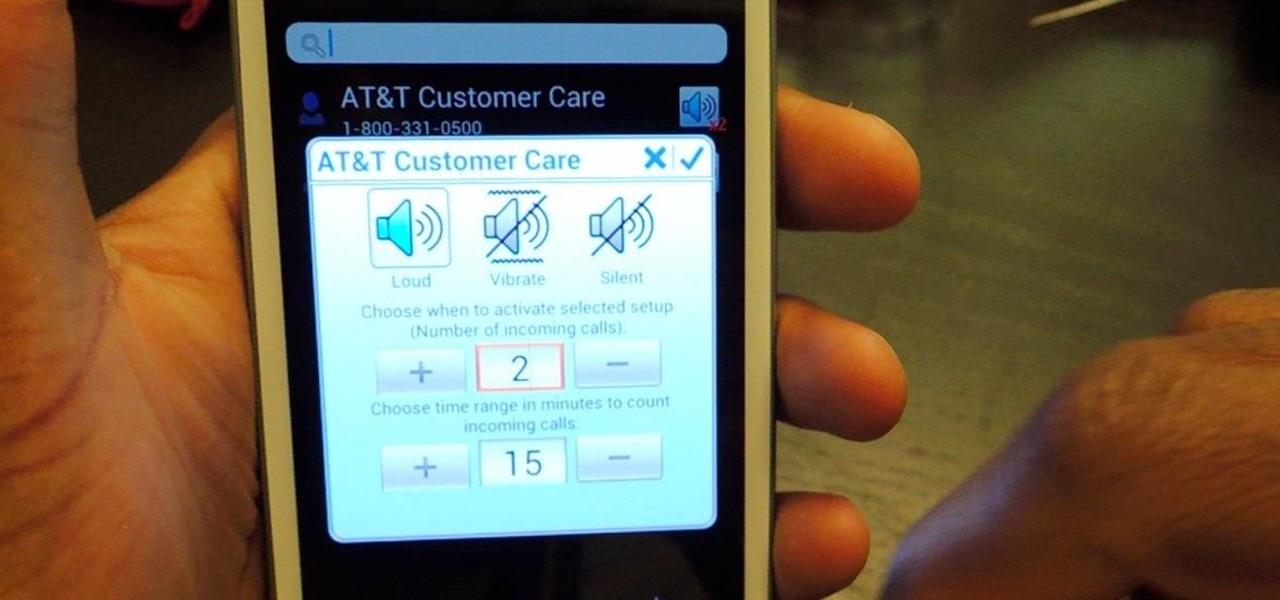
There are two scenarios that absolutely suck when someone calls you. The first is when you accidentally pick up a call you seriously didn't want to take. Debt collectors (thanks college), crazy exes, or that one guy from work. And the other is when you miss a super important call and can't get a hold of them afterwards.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Keyless entry remotes are great, but they don't always work how you want them to. One of the most common complaints is that they just don't reach far enough, and there's nothing more annoying when you can't remember where you parked. After all, what's the point of having "remote" entry if you have to be right next to the car for it to work?

Saher known as “sbGALT” is here to help with your singing vibrato. He gives an example of what vibrato is & how it varies from straight tone when singing. He sings a note with & without vibrato to illustrate the differences.

Have you ever found yourself lost in the Appalachian Mountains, or stranded in the Mojave Desert? Maybe it was because you couldn't read a map… a real map… a real hands-on, folding paper map. Reading a map is an important skill that may be lost in the internet and GPS era, but it' s a skill that everyone should have.

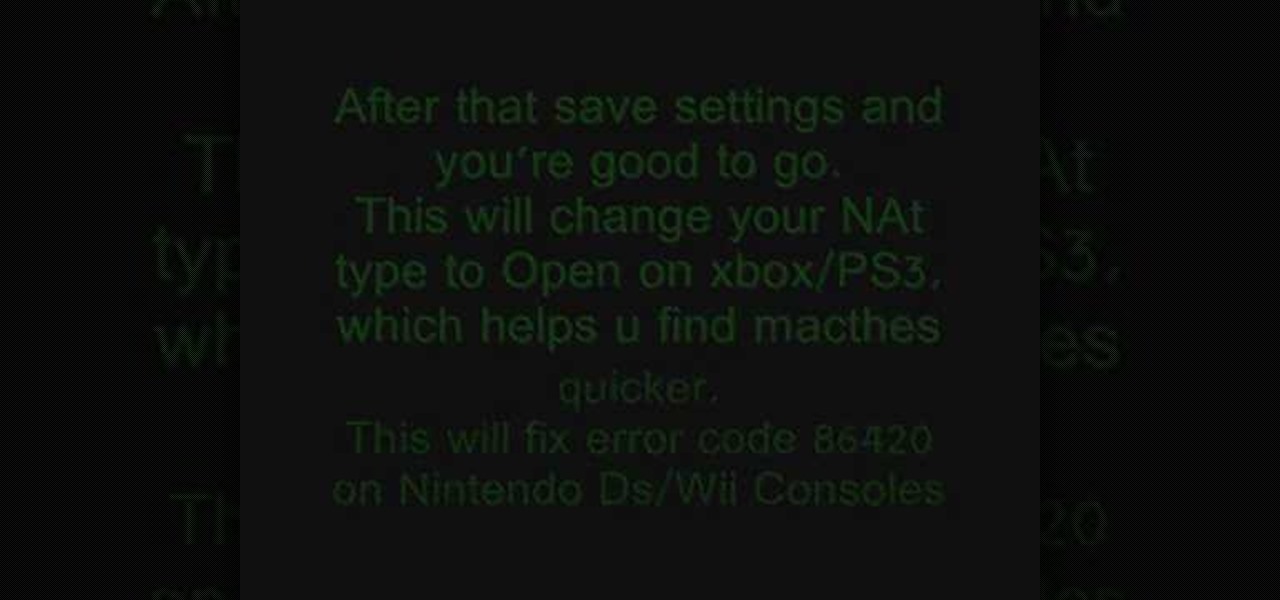
In this tutorial, we learn how to fix error code 86420 and change your NAT type to open. First, go to the website to change the settings for your Linksys router. Next, go to the applications tab that says "applications and gaming". After this, go to port range forwarding, then write in a name next to where it says "application name". Under "start" write the number 1 and under "end" write 6553, then keep "both" marked under protocol. Next, enter in the last 3 digits of your console's IP addres...

In this video from Dr. Carlson, users are shown how to witness the effects of the relationship between temperature and matter firsthand, using light-sticks. For the experiment, users need 3 beakers (or vessels of the sort,) and 3 light-sticks of the same color, shape, and light. To test the range, each beaker must correspond to one of the following states: room temperature, ice-water, or boiling water. Deposit a stick in each of them and observe for two minutes. Thus, one will see how the ato...

In this video tutorial by Dr Suzann Wang you will learn how to prevent gastroesophageal reflux disease (GERD). It is a hyper or low acidity problem in the stomach. The ph factor measures the acidic or alkaline nature of anything and it has a range of 0 to 14; 14 being highly alkaline and 0 being highly acidic. The stomach acidity tends to be 2. 0 which is pretty acidic. The acidity should be 2. 40. If the acidity is lower, it affects the rest of the digestive system. You can rectify this by t...

This video from Your Teacher is one of a range of math solutions. (which is the measurement from the center to the edge when drawn in a straight line) and also the area of the circle, is the amount of total space within its perimeter. The circumference of this circle is 20 pi. The circumference is 2 pi r. So 20 pi is 2 pi r. Which factors down to show that 10 is the radius (10=r). The area is pi r squared. As we know the radius is 10, we can work out the area - 100 pi.

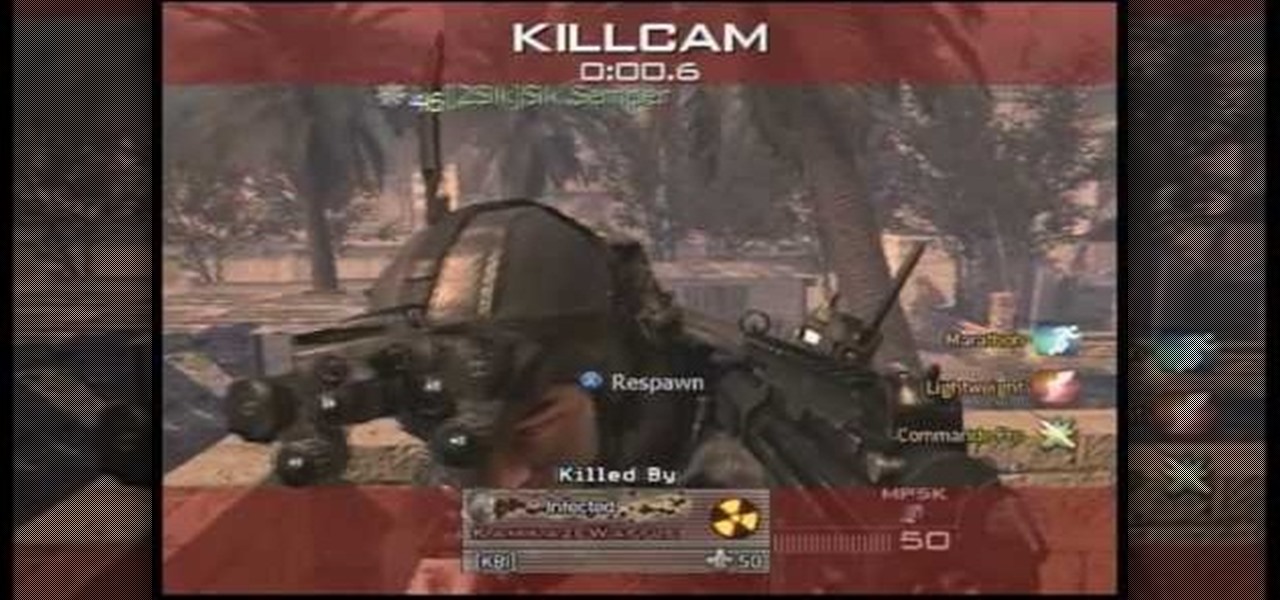
This video shows you how knives can be much more than a short range weapon in the online mood of the game, Call Of Duty: Modern Warfare 2. KamikazeWaffle and other players show you 50 ways of killing you enemy using the knife. Some of those tricks involve throwing the knife across a map and still hits its target. They also demonstrate how any objects around you can be used to change the direction of the thrown knife to the desired destination. Kill cam is recorded for each of the 50 tricks so...

Keith M. Bower explains the meaning of mean and standard deviation. This educational video gives insight in the basics of statistics. The relations between population mean and sample mean and between population standard deviation and sample standard deviation are explained. The mean gives an idea on the central tendency. Standard deviation gives an idea about how spread out the data are. Keith also explains how these two parameters, the joint sufficient statistics, define a normal distributio...

Often artist use, their voice and they are always searching for new and effective methods to improve their singing.

A short informative video showing how to make paper mache. A great arts and crafts project for some simple fun or your child's school science project. Easy to make with just flour, water, salt, and some old newspaper. Apply the mixture to a wire frame or a box like in the video to make a paper mache cave. It's very easy to make and you can create a range of things from masks, volcanoes, and most obviously caves!

Another innovative use of augmented reality - we've seen transparent walls, t-shirts that play Rock, Paper, Scissors, an iPhone operated video game drone; and now, a tattoo that comes to life. Just tattoo a simple "barcode", point a webcam at it, and a flying animated dragon will appear, hovering.

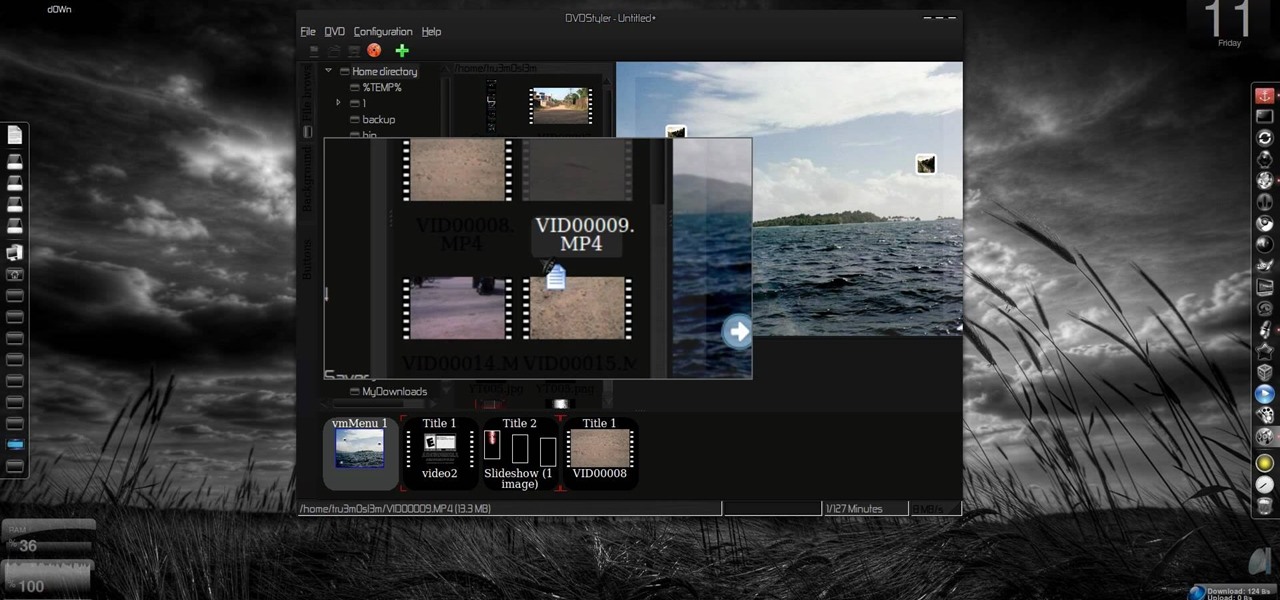
This video shows you how to convert videos to DVD using a cross-platform free, open-source authoring application called DVDStyler. It has a wide range of features, and this video shows you how to use it in the Windows OS. This program will also work for Ubuntu Linux. Update your videos today and make them look spectacular!

This how to video is a singing lesson to introduce resonance, which produces beautiful tone quality. You will learn how to do the silly spinning siren exercise which will help you improve your range and vocal technique. With the exercise in this video you can become a better singer.

This 4 part video series is a gift from me to all the other singers out there who have shown me such great love and support. It contains a full vocal warmup that will improve tone, expand range, and increase control. This is pretty much the kind of warmup that I might do with a private client, but it's for you guys - free of charge.

Ethical hacking is a useful skill that can make you stand out in the field of cybersecurity. Whether you're just entering the field or are already established and are looking to stay current, learning the fundamentals of the white hat is an essential skill for your professional development.

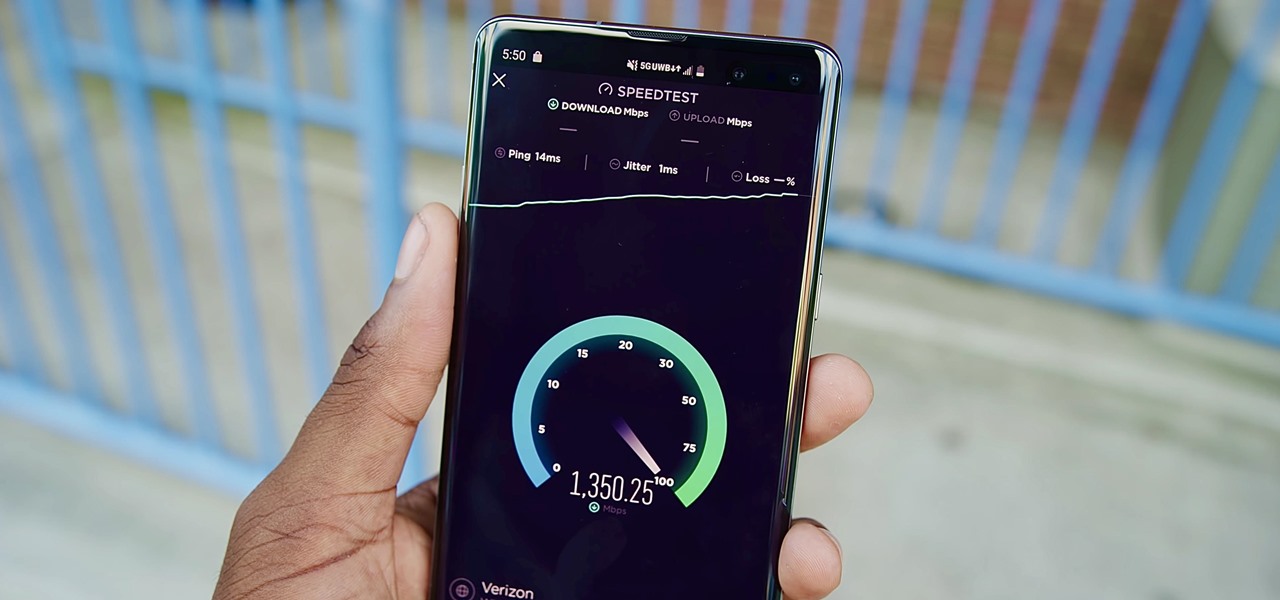
Not all 5G is equal. Even if you dropped the cash on a true 5G phone and you see it's connected to 5G in the status bar, that doesn't mean you're surfing the web, streaming Spotify, and binging Netflix faster than your friends with LTE phones.

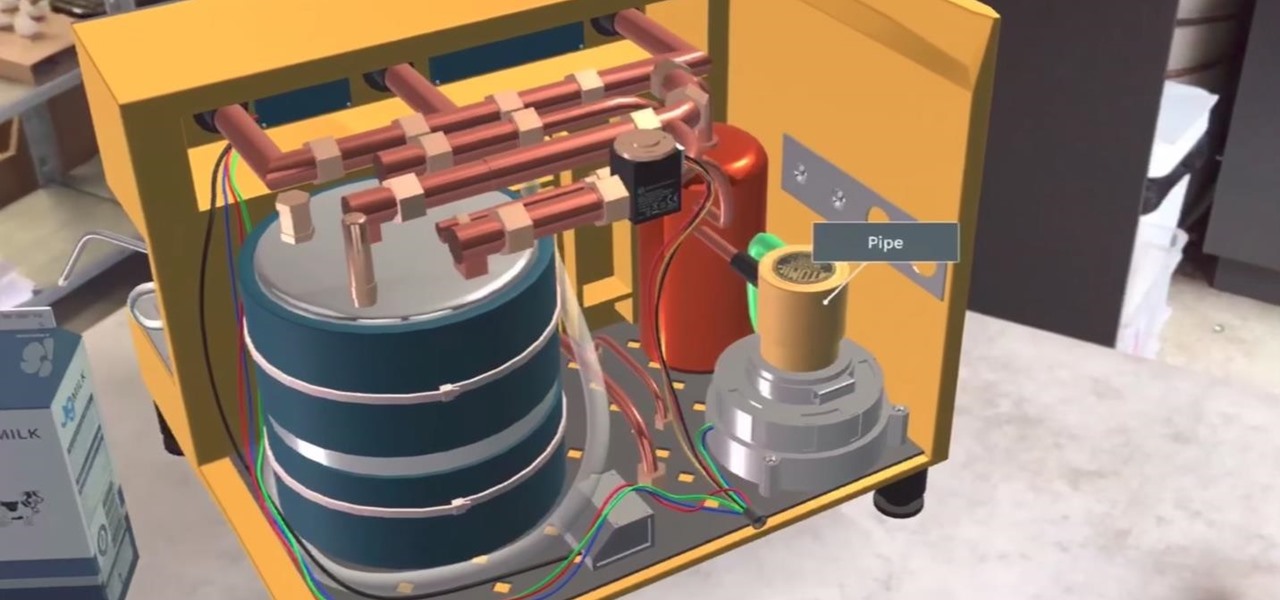
JigSpace, a company that uses 3D renderings to give instructions, showed off a fun new way to learn how things work using Apple's ARKit. The video released shows the anatomy of a range of things, including an espresso machine, an Archer Hb Plus chair, and the manual transmission of a car. Not to mention, they also used ARKit to show a 3D how-to of removing an iPhone's SIM card.

In this cardmaking tutorial, I make a 7x7inch square card using the Pink Peonies from a decoupage collection kit. I also use embossed card and some gorgeous corners to create a really pretty card. Step 1: Items Used

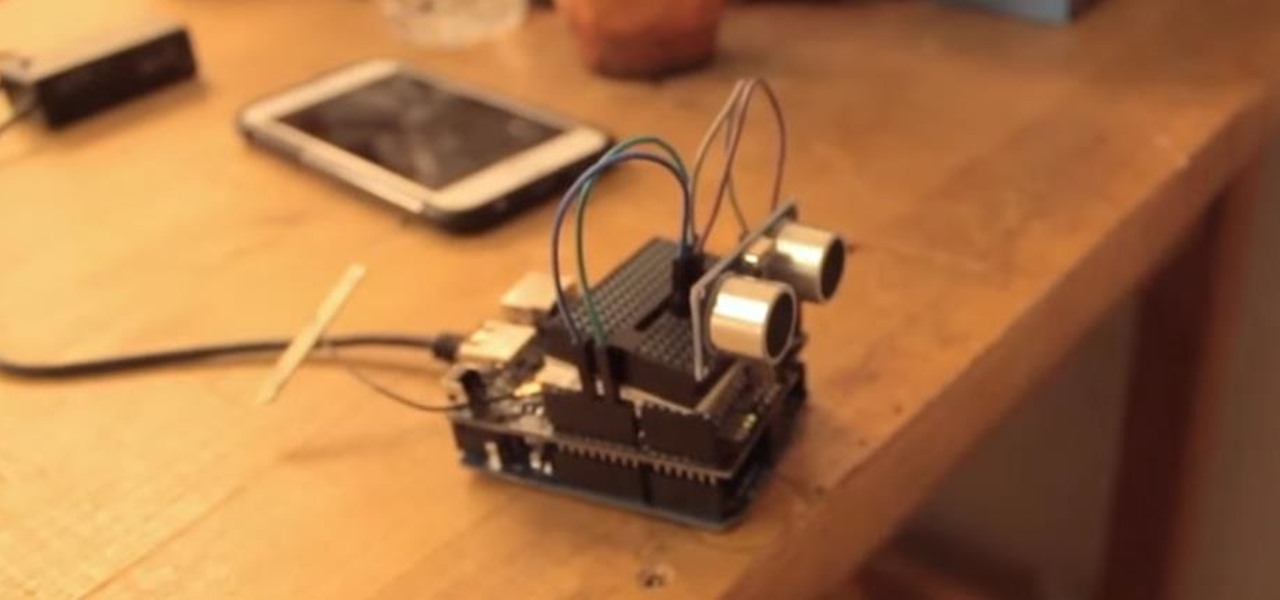
This tutorial shows you how to create an intruder alarm that sends you text message alerts when motion is detected. This may sound complicated but I am pretty confident any beginner with electronics should be able to do this just fine. The range sensor senses motion and tells your Arduino board to send the text (SMS). So you can leave the intruder detector at home, connected to your network, and still receive the SMS alerts, no matter where you are, as long as you have cell phone service.

This card demonstrations shows how I have used the Creative Expressions Die from the Sue Wilson Gemini range, this one is called Corvus. This is Part2 of a mini series. .

This card tutorial is to make a gorgeous daisy collage style card, ideal for any cardmaker with lots of embellishments. I use a wide range of different flowers and include satin ribbon to embellish the card base. This is a easy when you know how card and with stunning finished results. Step 1: Items Used