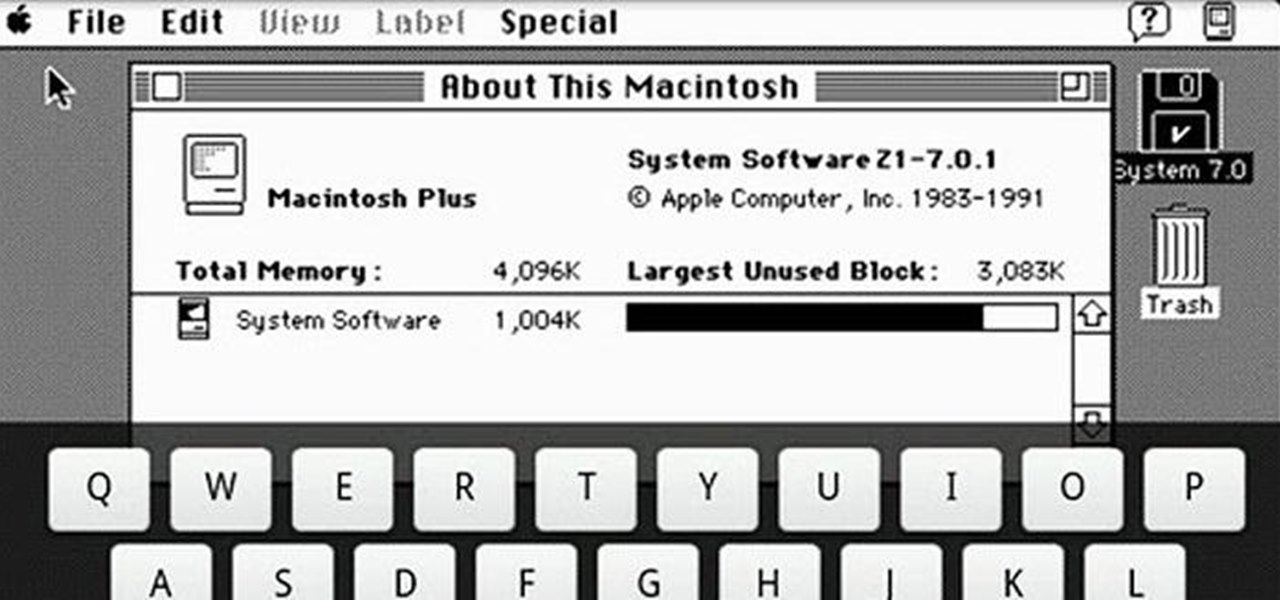
Remember these? Sadly, I don't, but I'm sure someone out there does. Anyone? This monstrosity, called the Macintosh Plus, was introduced in 1986 for the low-low price of $2,599. Wait...what? Almost three grand for that bulky baby?!? With a whopping 1MB of RAM standard?!? Whoa there...

Even though it seems like forever, the phenomenon of "rickrolling" has only been around since 2007. It was started as an inside joke by a 19-year-old who just wanted to troll his buddies, but ended up becoming one of the Internet's most popular memes with over 66 million views (as of this writing).

While the Google Play Store is filled with big name magazines like Time, Forbes, Sports Illustrated and Maxim, it also panders to smaller audiences, like with Coin Prices, Soap Opera Digest, Watch Journal and Quilter's World (which yes, is all about quilting). If you have a select few that you enjoy reading, prices aren't usually a problem; issues range from $1.99 to $4.99 for each one, or from $19.99 to $39.99 for yearly subscriptions. If you're someone that is a magazine connoisseur, prices...

As a multitasker, I've embraced the hustle and bustle that has filled my life. I'm constantly doing several things at a time, while looking for shortcuts to finish all of these things quicker than before. I brush my teeth with my cell phone in hand and drive to work with breakfast in mouth—I spare no time. Well, now there's an application for the Mac users among us that can help take some of the stress out of doing a thousand things at once.

When you're capturing video with a DSLR, not having some type of stabilization system can lead to some pretty awful and shaky scenes. Camera instability is not only painful to watch, but breaks the fourth wall. Once that the invisible barrier between filmmaker and audience is apparent, it may break down that magical relationship between the two.

There is nothing worst then having to wait for something you really want. It doesn't matter how old you are or what the item is, the fact that you have to wait for it makes you want it even more. It's the love-hate relationship I have with Amazon and anything I order, and when that anticipation is for a new smartphone, it's amplified by about a thousand. The LG Nexus 4 has received great reviews and is one of the most sought after phones this holiday season, but it's a hard one to get a hold ...

Eavesdropping from a distance can be tricky because it usually requires some sort of bug or transmitter. It's easy to transmit audio through lasers, but you can also use lasers to build a microphone that picks up audio from a distance. LucidScience built the Laser Spy System for about $20. To make your own, you'll need a cheap laser pointer, an NPN phototransistor, a headphone amp, and a few other small pieces listed below. A light-to-sound circuit is installed in a small plastic box with the...

So, you've finally managed to get addicted to one of those free farming games, like Farm Story or Tiny Village. You play the game nonstop now, and the only thing stopping you is that dreaded on-screen notice to come back in 23 hours to finish farming or building. Come back in 23 hours… WHAT?!? Most of these free games will start charging you at this point. Time becomes a luxury. Well, not anymore, thanks to XDA Developer StupidIdea, who made a time-tricking app called GMD Speed Time (that's t...

Ever since the mid-2000s, there's been a lot of bandying back and forth on the Internet over what exactly Steampunk is. Some people think it's one thing, others another thing, and some think that it shouldn't be defined at all.

If you bought the new iPhone 5, you've probably been less than thrilled with the lack of cases and accessories that you can use it with. Docks are no exception—users were disappointed to learn that Apple has no plans to even make one for the newest addition to the Apple family.

The original NES controller has become one of the most recognizable symbols of the Nintendo gaming culture, thanks to its perfectly rectangular shape and simple button design. But despite its popular appeal, people just don't game with them anymore. So, what do they do with them? They savor the memories and turn it into something more useful, like a light switch.

Gear up the performance of your car with a comprehensive tune-up. Check out this video tutorial from the DIY Network to see how to give your car a complete tune-up. You'll need to get spark plugs of course, and the wiring harness. If your vehicle needs a change, help it out with these automotive tips. Change the belts, the air filter, the oil filter, and more. Learn from the masters.

To do basic crunches the lady is lying on her back with her knees bent and feet on floor about a foot apart. Fingers are spread under her neck and head. She raises her chest and shoulders looking up and back down to the floor slowly, 14 times. Now, the left feet crosses over the right knee which is still down on the floor and shoulder to the opposite knee with a small range of motion 14 times. She reverses doing the same thing with opposite leg and opposite shoulder. Now, arms are extended un...

Attention jewelry makers! When making your own unique jewelry designs, one must learn how to secure the end crimp beads with crimping or chain-nose pliers. Crimp beads can be used for finishing off your strung jewelry or as "stoppers". In this tutorial, learn how to hone your jewelry-making skills!

Crochet a cool house-tent for your little homeless friends. This instructional video will walk you through a super simple pet project. Whether you're out to craft dwellings for a dog, cat, pig, or free-range snake, this tutorial demonstrates how to build and combine all the necessary components, including the frames, walls, and personalized decorations. The results are quite cozy.

Learn how to do a standing barbell curl drop set while leaning against a wall. Presented by Real Jock Gay Fitness Health & Life.

Follow these juggling volley drills in order to increase the range and precision of your shot. Try both full and half volley juggling drills.

Amazon Web Services (AWS) is the premier on-demand cloud computing platform. Offering a wide range of APIs to companies, governments, and individuals on a pay-as-you-go basis, this Amazon subsidiary pulled in over $35 billion in revenue in 2019 alone.

It looks as though the novel coronavirus and social distancing guidelines are here to stay for a while. So companies of all sizes and industries are scrambling to adapt to a new reality in which everything from morning meetings to large-scale presentations are done entirely online. It looks like this is going to be the new normal for the foreseeable future.

If the interconnected worlds of blockchain, Bitcoin, and cryptocurrencies scare you a bit, you're not alone. Thanks in part to the extreme and seemingly random fluctuations in the value of Bitcoin over the past three years, more than a few developers and investors are wary of the cryptocurrency revolution and its ties to blockchain development.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

During its presentation at Unite Berlin, Magic Leap gave attendees a crash course in developing experiences for Magic Leap One (ML1), we found out quite a bit more about how the device works and what we can expect to experience with the device.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

Last week, augmented reality startup Proxy42 released Father.IO, a multiplayer game that turns any indoor or outdoor space into a laser tag arena.

Like humans, cats can suffer infections caused by ticks, and too often, the disease is fatal. Learn about tickborne diseases that affect cats and what you can do to protect Fluffy from an untimely demise.

In the US, ticks can spread several pathogens in one bite. A new test offers physicians the ability to identify what infections ticks are carrying and can detect if one of the pathogens could be the spreading Powassan virus.

In the music world, it's safe to say electric instruments are more versatile, but they lack the portability of their acoustic counterparts. However, with the aid of your smartphone plus an audio interface, you can play your electric instrument anywhere — with all the pedal effects you please — and even record your efforts.

Long before Apple and Android became household names, Nokia dominated the mobile industry. The Finnish company was one of the first to develop smartphones, and their classic N95 with 2G "high-speed" internet connectivity was declared the "best smartphone ever" by some in 2007. Outside of the US, before the iPhone became all the rage, owning a Nokia phone was a status symbol akin to wearing a Rolex or Omega watch.

One of the big hurdles when equipping vehicles with sensors for autonomous driving is the cost. For example, the Light Detection and Ranging (LiDAR) sensors that power many versions of self-driving car technology are pricey, currently ranging from around several thousand dollars up to $85,000 per sensor—and vehicles often need multiple sensors to see enough of what is going on around them to drive safely.

As a former repair tech, I've heard the same reasons over and over as to why people opt not to purchase phone insurance. Some cite the cost—why pay extra every month for insurance when you're careful with your phone? Deductibles are expensive, so why not just spend that money on a repair instead of getting a refurbished phone as a replacement?

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

Welcome back! In our last training session, we covered some advanced list topics. We'll be going deeper into the advanced list rabbit hole today with lambda and lambda operators! (And I'm not talking about Gordan Freeman)

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.