When shooting video on your phone, you have two cameras at your disposal, the rear camera and the selfie camera, and you can switch freely between the two. As for microphones, you may have more than one but, unlike with the cameras, it's not easy to switch between them. Filmic Pro solves this problem by isolating the mics so you can choose the best option for the audio track.

Finland-based Rovio, one of the pioneers of mobile gaming, is now ready to break new ground in augmented reality with its Angry Birds franchise.
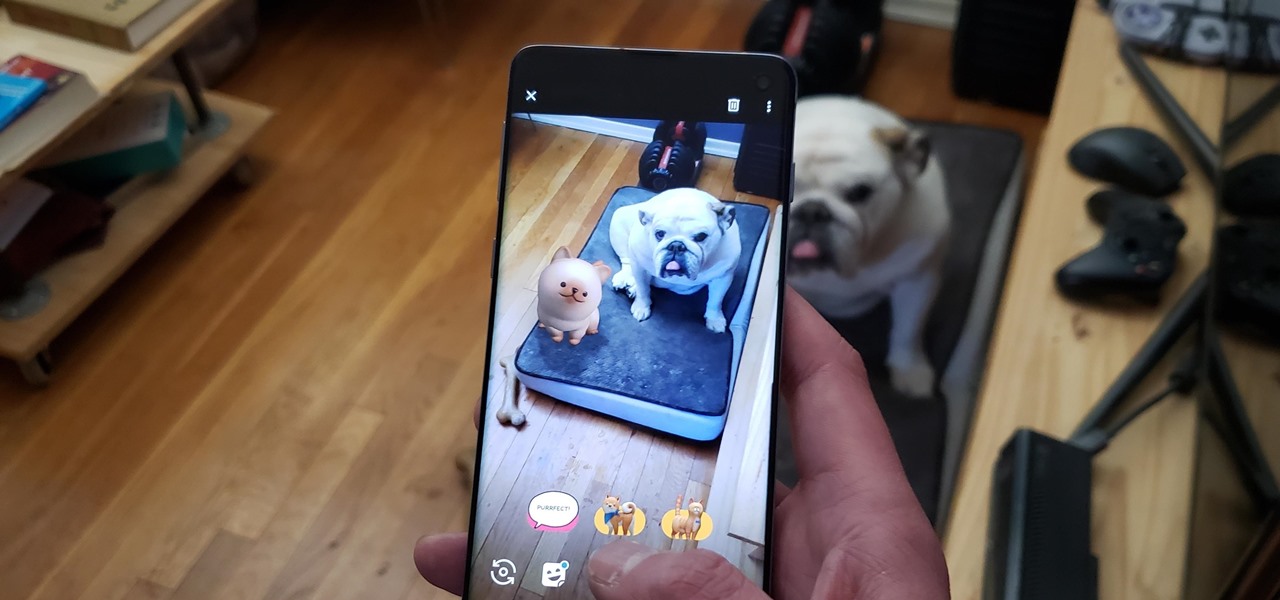
Google's has expanded ARCore support to numerous Android flagships like the Galaxy S10, so if you have a compatible device, you get access to all the cool new apps that can augment the world around you. One of ARCore's most sought-after features, AR Stickers, is normally exclusive to Google's Pixel lineup, but by sideloading the Google Camera app, you can try it on any ARCore device.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

If you salivate at the idea of waking up to the Jarvis-powered smart window from the opening minutes of Marvel's Iron Man, then connected home appliance maker CareOS is here to make your playboy billionaire philanthropist dreams come true.

The emerging narrative as CES begins is that consumer-grade smartglasses require a heavy compromise in functionality in order to arrive at a form factor and price point that appeal to mainstream customers.

Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.

Publicly, things have been pretty quiet over at Meta, the augmented reality headset and software startup based in Silicon Valley. But that doesn't mean that the company doesn't have a few strong opinions about the state of AR in 2018.

Signaling a new direction forward for the company, Magic Leap shook up its executive suite by re-assigning to top leaders to new advisory roles. Meanwhile, a new startup backed by Hollywood executives, tech venture firms, and notable angel investors plans to bring new life to AR for marketing entertainment properties.

It's no secret that MoviePass is a shell of the service it once was. The primary $9.95/month plan for three movies each month is inconsistent and can change drastically depending on your location. Thankfully, MoviePass isn't the only movie ticket subscription service available. We've compared all the best plans on the market to help you find the one that's right for you.

If you or someone you're shopping for has a newer iPhone model or an Android smartphone like the Galaxy Note 9 or Pixel 3, they come with wireless charging capabilities. Problem is, they don't come with wireless chargers. But there's no better time to snag one than on Black Friday, and we've found the best deals out there for 2018's holiday season.

Let's face it, iPhones are expensive. With the latest iPhone XS Max reaching as high as $1,449, our wallets could all use a little support. That's where Black Friday comes in, supplying us with deals and discounts on iPhones of all kinds. If you're looking for a new iPhone this holiday season without having to break the bank, you've come to the right place.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

The new iPhone XR, XS, and XS Max have everyone buzzing. But, at first glance, the XR and XS look pretty similar in almost every way. So, what's the difference? It comes down to the XR's "Liquid Retina" LCD screen vs. the XS's "Super Retina" OLED display. How do they compare, and why does it matter when considering which new iPhone to preorder?

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Incoming phone calls and FaceTimes, whether you want to answer them or not, will take over your entire iPhone's screen — no matter what you're in the middle of doing on the device at the moment. You could be browsing the web, playing a game, or chatting on social media. It doesn't matter, you'll get interrupted. But you don't have to put up with it anymore.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

By now, you already know that the Magic Leap One ships with an array of apps to immediately get you accustomed to operating in your new spatial computing reality. The first one we're going to focus on is Screens, an app we told you about previously, but only now have managed to try for ourselves.

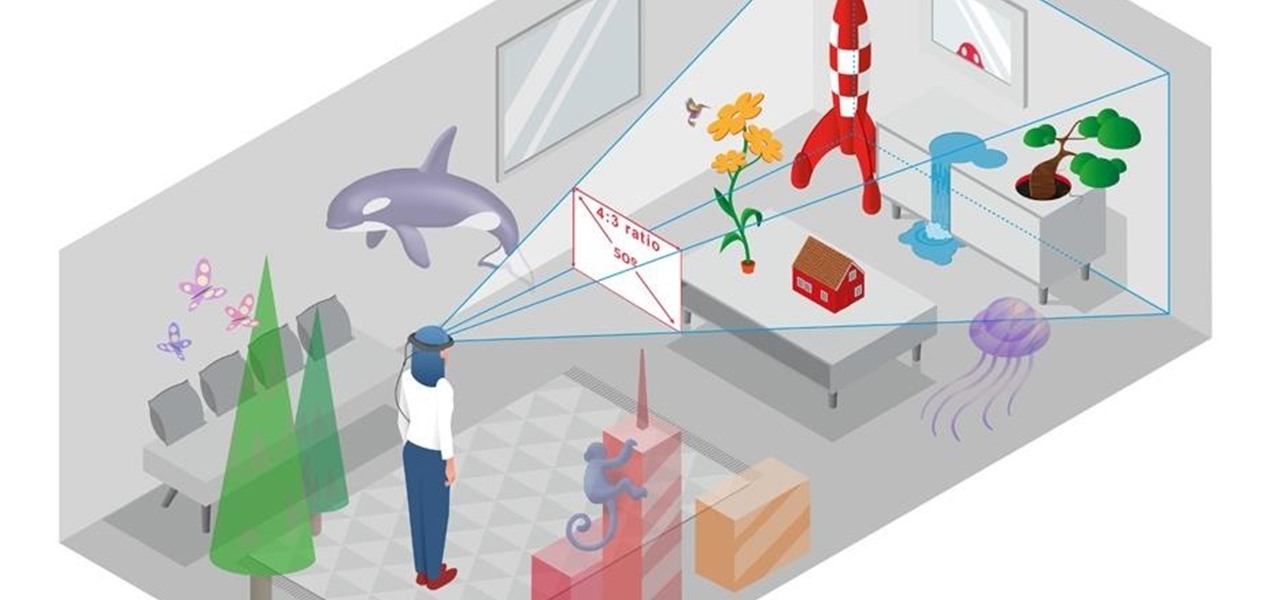
In the lead up to the Magic Leap One launch, Magic Leap has been coy about what the actual field of view (FoV) is for its first commercial product.

In its latest feature with an assist from augmented reality in storytelling, the New York Times shows readers the virtual crime scene it constructed to prove that the Syrian military conducted chemical warfare against its citizens.

When it comes to the sub-$250 price range, the new Nokia 5.1 might be the perfect phone. Of all the new models announced at Nokia's event in Moscow, the Nokia 5.1 offers the most with the least compromises. For a third of the cost of a flagship, you get a phone with a premium build, solid specs, and good battery life.

During an event in Moscow earlier this year, Nokia announced a refresh to their Nokia 2, 3, and 5 series phones. While there is no official confirmation of a US release for the updated Nokia 2 and 5, we do know that as of July 2nd, you'll be able to snag a new Nokia 3.1.

As Magic Leap prepares to ship the Magic Leap One later this year, the company is putting its focus on mentoring developers and creators to build a content ecosystem for the spatial computing platform.

If you're looking for your gaming fix and nothing on the App Store is piquing your interest, you should give soft-launched games a try. These are games that haven't been released in the US yet because they're getting tested in smaller markets first. Using a simple workaround, you can install them on your iPhone in any country.

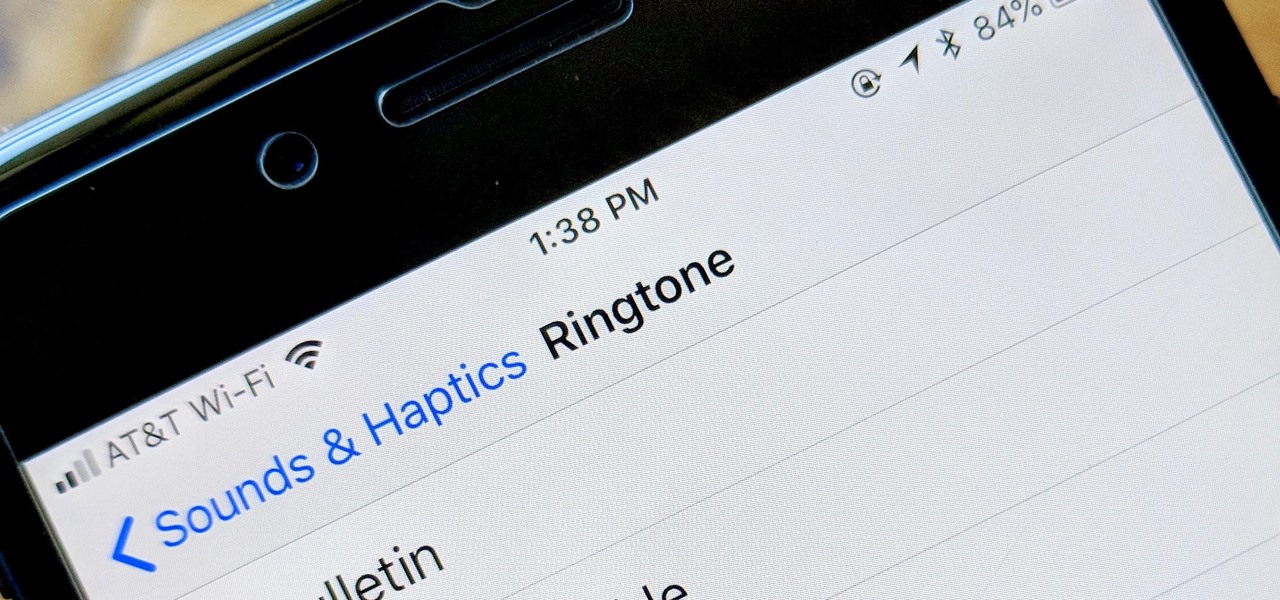
With the exception of "Reflection" on the iPhone X, Apple hasn't updated their catalog of ringtones and alarms since iOS 7 dropped back in 2013. Since then, the company has come a long way with the quality of the iPhone's speakers, but their tones haven't adapted to meet those changes. That's left an opening for others to create their own ringtones mastered for the iPhone.

This week, we're beginning to see the wide ranging impacts of some of the early iterations of augmented reality hardware and software.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Since making waves at Mobile World Congress 2018, Android Go devices have slowly trickled their way onto US shores. Only one device was officially announced for the US at MWC, but several OEMs have extended availability to the US in the months since, and it looks like we just received another.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

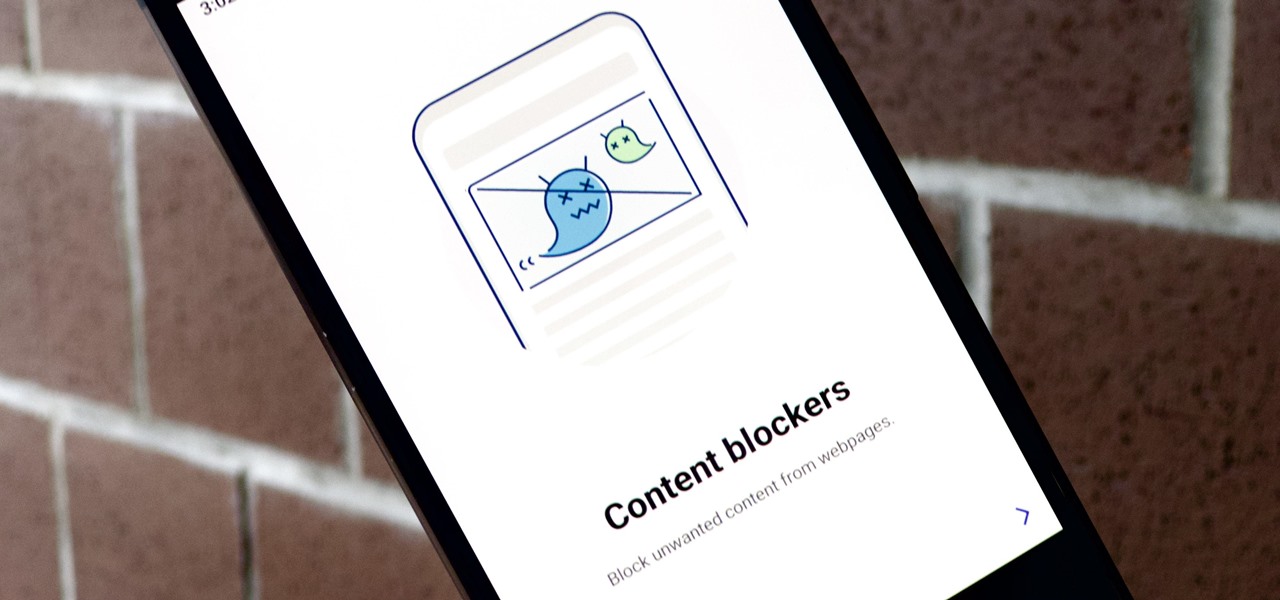
Samsung Internet offers excellent features that enhance the mobile web browsing experience, often through its extensions. A QR code scanner, ad blockers, tracker blockers, and more work directly in the browser, so you can do exactly what you want to do on the web.

Getting an insider view of the goings-on at Magic Leap is hard to come by, but occasionally, the company lets one of its leaders offer a peek at what's happening at the famously secretive augmented reality startup. One of those opportunities came up a few days ago when Magic Leap's chief futurist and science fiction novelist, Neal Stephenson, sat for an extended interview at the MIT Media Lab.

UPDATE: The P20 and its variants are officially available now. However, there's no official North American variant. You can purchase the international version of the P20 Pro or P20 Lite on Amazon, but be aware that it may not work perfectly on US carriers.

The Galaxy S9 and S9+ have a new camera feature that Samsung is calling "Dual Aperture." On the surface, that may sound like your typical techno-jargon, but it actually has some significant implications for the future of smartphone photography.

With only one profitable quarter in the last two years, LG's mobile division is undergoing a shakeup. With a fresh set of executives, LG has delayed the expected launch of the upcoming G7 and instead decided to start the year with yet another variant of the V30.

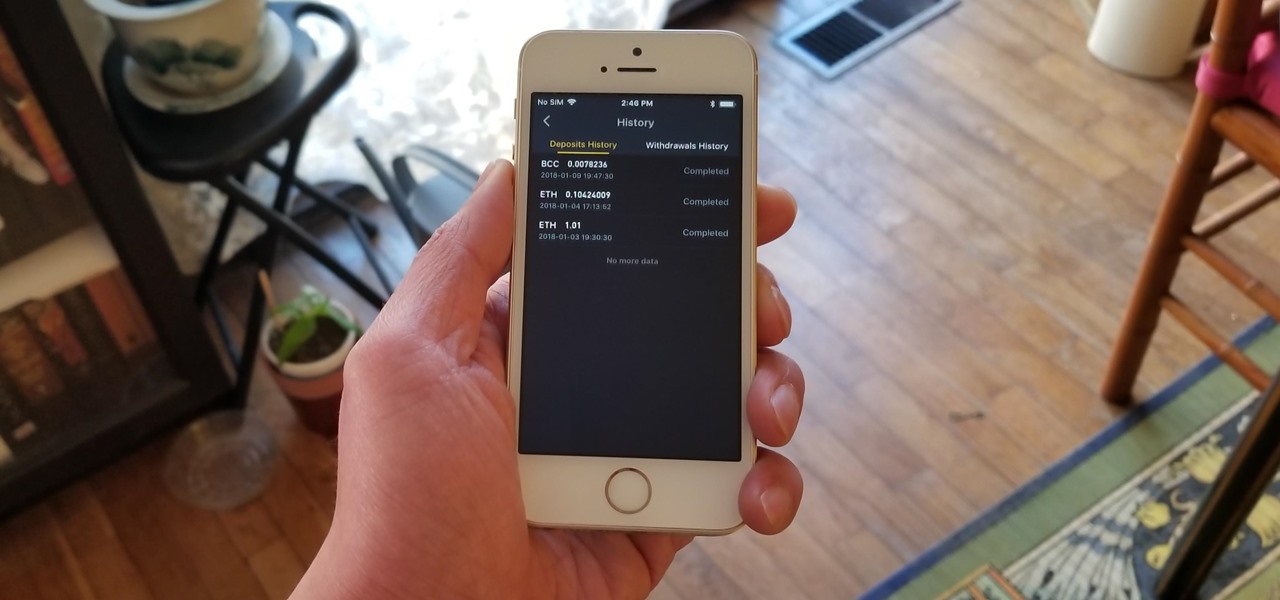
As cryptocurrencies gain mainstream acceptance, it's not far-fetched to think that we'll one day be able to buy alt coins like Ripple (XRP) and Stellar (XLM) using debit cards and bank accounts. Until then, we'll have to rely on using bitcoins and ethereum to buy digital coins. Thankfully, depositing and withdrawing cryptocurrencies with Binance is relatively hassle-free.

Today could mark the beginning of a new age in wireless charging. The FCC has certified the WattUp transmitter, a revolutionary technology that could shape the future of smartphone charging. This new tech addresses many of Qi charging's limitations, and if things go right, may lead to a truly wireless future.

Besides its extensive collections of add-ons for Android, Firefox's mobile browser apps have many built-in features that you won't see in other mobile browsers. One feature in particular, available for both Android and iOS versions, makes it easy to switch back and forth between search engines for any query.