Codenamed "Nougat" after the sugary stuff that fills your Snickers bar, Android 7.0 is living up to its name with tons of sweet features. There's almost too many changes over Marshmallow to cover in one go, with new functionality ranging from a revamped Doze Mode for battery saving, to split-screen apps, and even an easier update process. All told, the Nougat update has a lot in store for your phone or tablet.

Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little screwed—both digitally and in real life.

Pokémon GO made waves as the first augmented reality game to gain popular adoption. In fact, it was so popular that it only took a few days to uncover some the benefits and serious issues with combining physical and digital worlds.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic
Smartphone cameras are so good nowadays that there's almost no reason to own a point and shoot. Once the megapixel spec race was finally settled (hint: more isn't always better), manufacturers started focusing on the quality of their camera sensors, which has led to a huge jump in color accuracy, dynamic range, and image clarity.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Making sure you have the best gallery app available for your Android device used to be as easy as just installing QuickPic. But late last year, Android's top photo-viewing app was sold to a company who is notorious for permission spamming, so QuickPic quickly lost everyone's approval.

We spend over 30 percent of our lifetimes sleeping—yet it never seems like enough, does it? Distractions ranging from work issues to personal relationships keep our minds racing well after they should be shutting down for the night, and the onset of smartphones has only added to this problem with the instant information and easy entertainment that they offer.

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

Fall is a time of change. The leaves change color, the weather changes from warm to cool, and we change our clocks to fall back an hour. This last change means that many of us will get home from work in pitch-black darkness; for me, the early onset of night makes me less interested in cooking dinner and more interested in getting in my sweats, throwing leftovers in the microwave, and binge-watching The Affair.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Tofu has been a staple food in Asia for over 2,000 years, but due to the health craze of recent years, it's enjoyed a surge of popularity in the Western world. Derived from the milk of soy beans and typically coagulated by calcium or magnesium salts, tofu can be found in consistencies ranging from extra-soft or silken to extra-firm. Based on which firmness you prefer, there are a myriad of ways to prepare your tofu for consumption.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

Mobile payment systems have been around for almost 5 years now, starting with Google Wallet. But when Apple got into the game last year with their new Apple Pay service, things really started to take off. Around this time, Samsung responded by acquiring an up-and-coming mobile payments company that owned the rights to an incredibly innovative technology called Magnetic Secure Transmission (MST).

When most people think of "gaming computers," they're probably thinking of Windows-based PCs. They offer a huge variety of devices with better equipped software and hardware for a cheaper price, and there are more available games than there are for OS X-based systems.

Welcome back, my rookie hackers!

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

Whether I'm in my car or making dinner, I always have music playing. And since I don't like to keep my headphones on me at all times, I end up using my Android's built-in speakers a good portion of the time.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

As someone with a pretty nice TV, I've never found the allure in purchasing a projector. While they're certainly smaller and sleeker than a television, and more portable, they can be pricey and produce a less than stellar image. And who really buys a projector anyways? They're for school, they're for work, they're for theaters, but they're not really for my apartment, right?

Part 1: What is Popcorn Time? Part 2: What is a torrent?

With only a few days until Apple Watch preorders begin, and just a couple of weeks until its official release, the biggest question in Apple Land seems to be: "Are you going to get an Apple Watch?"

With the brand new SMS-based ordering service called Magic, anyone with a mobile phone can order whatever they want—really, anything—by sending causal text messages. Who says magic isn't real?

The oven is arguably our most essential kitchen appliance (right alongside the fridge, freezer, and yes, even the microwave). But even though we've been using them for a few millennia, many of us know so little about our ovens that our cooking or baking can feel like a roll of the dice sometimes.

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

Though many students spend four years of high school learning a foreign language, most of us probably retained very little. Chalk it up to the carelessness of youth, but chances are you've since been in situations or places that left you wishing you paid more attention in class or had continued practicing long after you graduated.

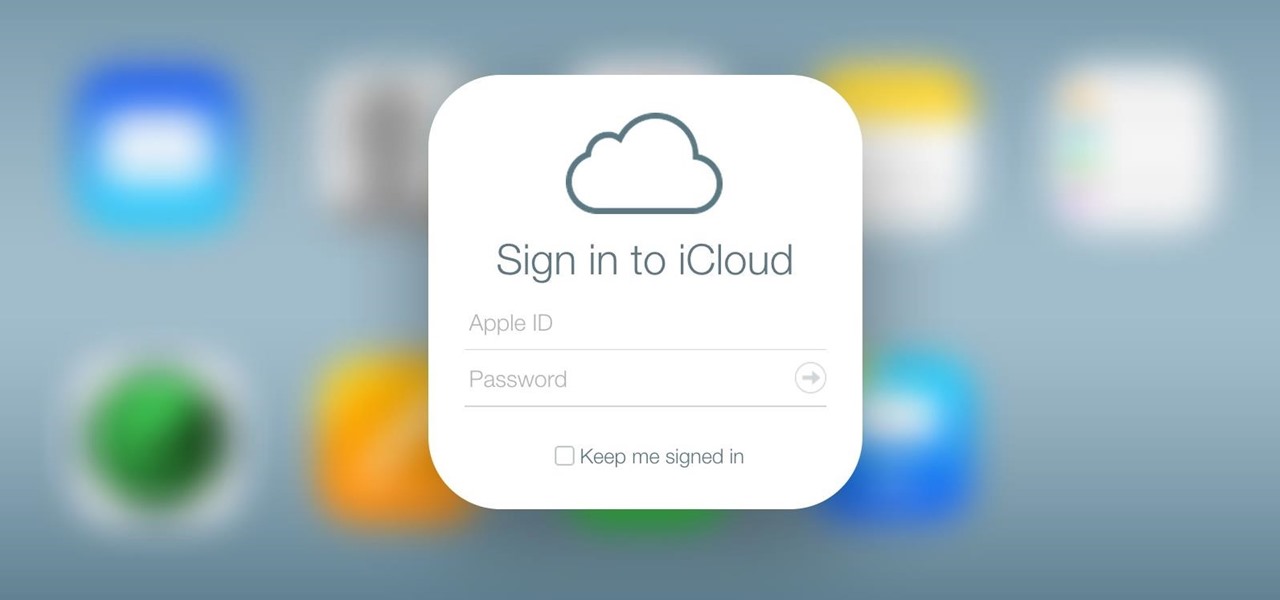
We've already shown you how to free up internal space on your iPhone, and now it's time to tackle another problematic storage issue—your iCloud account.

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.

Hard as it is to imagine, there are people out there who loathe garlic and onions. Some might have allergies or medical conditions like IBS, or are supertasters (i.e. people who carry a certain gene that makes them extremely sensitive to how certain foods taste). Others might just be picky eaters.

Facebook will let you do pretty much anything via a text message, but unless you still have a flip phone, it's more of a novelty than actually useful.

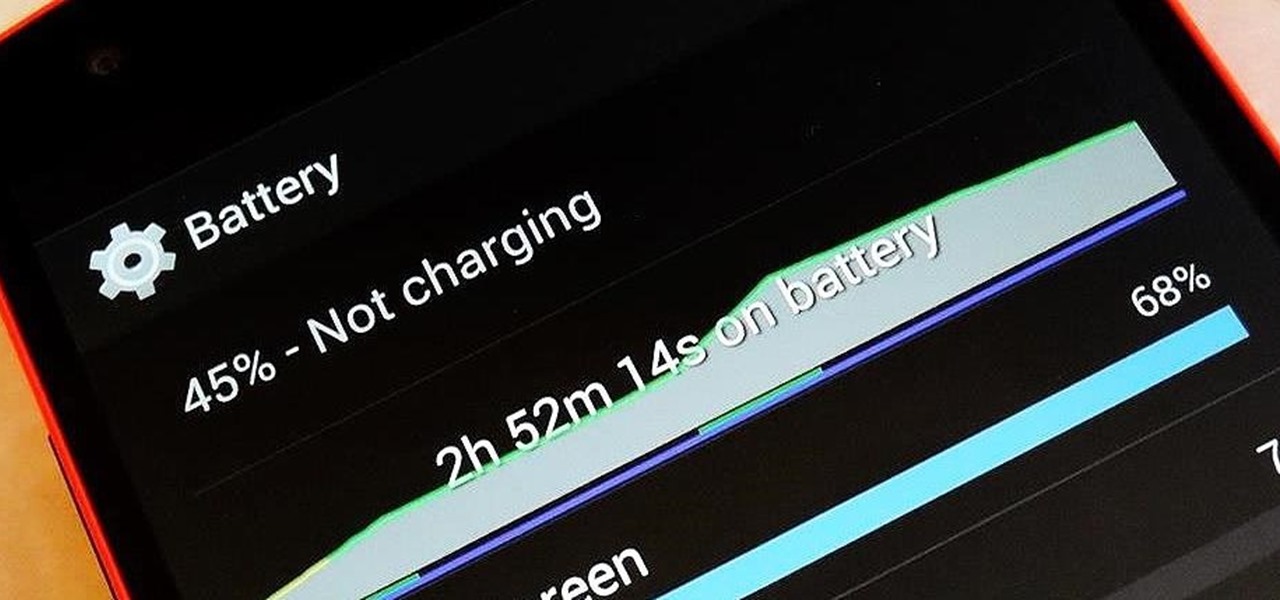
There are so many things to love about the Nexus 5, from timely updates to newer versions of Android to a terrific blend of price and specs. But while mobile phone tech keeps churning along, battery technology isn't quite up to snuff yet, and I find myself wishing that my phone's battery lasted longer on a single charge.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Lenovo brought out the big guns for CES 2014, with the Vibe Z showcased as the Chinese company's' first foray into the LTE smartphone space. Slated for a February release, the ultra-thin and extremely light smartphone will certainly be in the running for top smartphones of this very new year. Photo via CNET

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

The holidays are quickly approaching, which means everyone will be scrambling over the next couple of weeks to find the cheapest options for flights to wherever home is. There are so many sites to buy them from that it can be hard to know where to start, so we've compiled some tips and tricks for making the process as painless as possible, whether you're flying home for Thanksgiving, Christmas, or whenever.

From amateurs to professionals, DSLR cameras are the standard weapon of choice for most photographers. If you own one, then you probably know how expensive of a hobby photography can be. A good starter camera can run between $400 and $500. Then there are accessories like tripods, lenses, filters, and memory cards that can slowly empty out your wallet.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.