Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

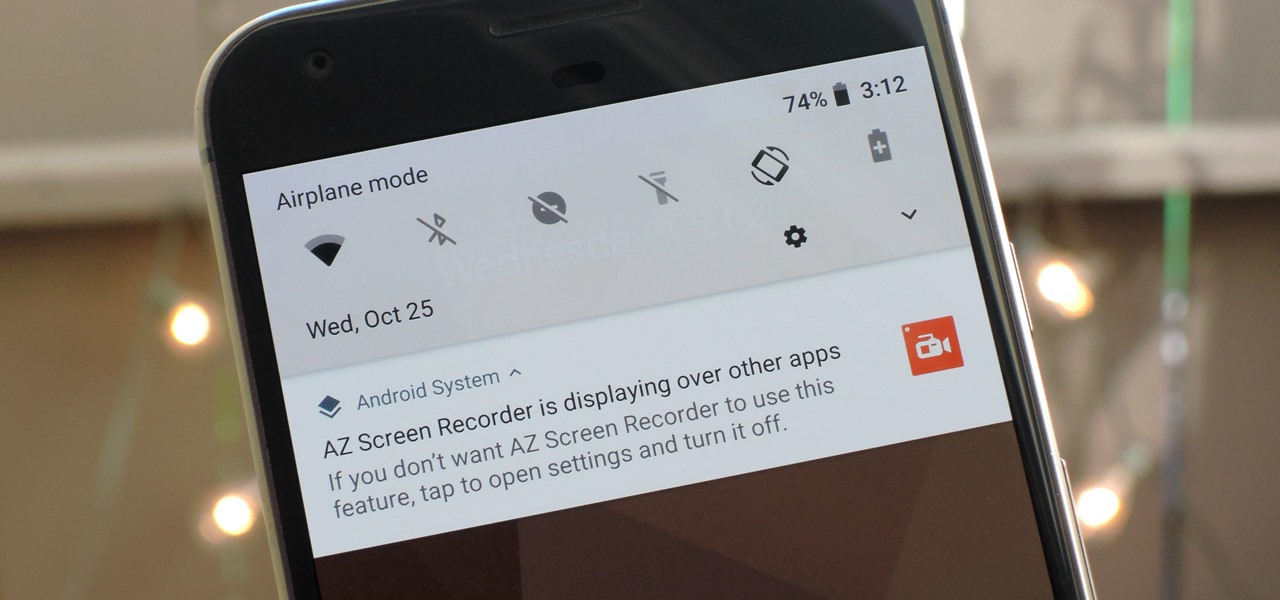
Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

The Moto G7 Power is a phone that screams battery life. From its display resolution to the massive battery, it was designed for those who hate to recharge each night. But unlike other battery-focused smartphones, it comes at a price almost anyone can afford.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

When left unmaintained, lock screen notifications can be an overwhelming, chaotic mess. Alerts coming in at a rapid pace can be hard to see because there are just too many of them, and your iPhone's screen sometimes can't even take it, falling asleep before you can read only a few notifications. If that sounds like you, there's an easy way to take back control of alerts — and your sanity.

The biggest change this year for iPhones comes with the cameras. All three iPhones get a new ultra-wide camera, which allows the device to capture more of what's in front of you. Not so new this year is the 64 GB base storage, which will fill up fast when shooting in 4K at 60 fps. A new feature will also add to your storage concerns, however, a feature that captures more video than it really should.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

While the iPhone XS actually comes with a smaller battery than the iPhone X, Apple claims it, along with the XS Max and XR, offer users longer battery life than last year's first Face ID model. While that may be true, your new iPhone still ships without meeting its full battery-saving potential. There are, however, steps you can take to make sure your X, XS, XS Max, or XR makes it from morning until night.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

Anyone who paid attention to the Lavabit shutdown had a feeling it was connected to Edward Snowden, the high-profile NSA whistleblower. Ever since the government's case against Lavabit went public in late-2013, people have put two and two together.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

According to Nielsen, the average American spends about 34 hours per week watching television. That may sound like a lot, but when you factor in multi-screen viewing, it could be even higher—81 percent of Americans use their smartphones or another device while watching TV. It's the new picture-in-picture.

As with most things on the Internet, browser cookies can be either helpful or harmful, depending on how they're used. On one hand, they make your experience more convenient by storing information about sites you use frequently. On the other, they can help companies track you across the web or cause your computer to be more vulnerable to attacks on public networks.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

OnePlus unveiled its latest device — the OnePlus 7 Pro — Tuesday, May 14. Usually, the company touts a device with impressive specs, build quality, and price, all without sacrificing too much. This time around, however, OnePlus decided to include a Pro device without compromise, while retaining those core values, making the 7 Pro highly competitive against the "low end" phones of their competitors (the iPhone XR and Samsung S10e).

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

Virgin Wireless, perhaps best known for Sir Richard Branson and all of his antics, is an affordable cellular option here in the US. Virgin customers can enjoy — if that's the right word for it — Sprint's cellular service, at a discounted rate, however, there are usually some compromises for that. Now, there will be yet another compromise for Virgin customers who don't like iPhones — Virgin will now only carry Apple's phone on their network.
I've recently been on holiday in Europe, staying in a hotel that was part of a big chain that included many in the local area. A quick review of the wi-fi within range of my room showed that there was another in the chain that was in range of my Yagi Turbotenna, which naturally got me thinking. If I wanted an anonymous internet connection, this could be quite handy.

We've all been there: you're staring at a fantastic-looking salad or sandwich full of your favorite ingredients. You take a bite, and you taste only one thing—raw onion. A glass of water, a toothbrush, and an hour later, and your breath still tastes like only one thing—raw onion.

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

The next generation gaming systems are so close to release I can almost taste the plastic. The new PlayStation 4 is set to be released in just a couple days on Friday, November 15th, but if you're like me, there's only one thing preventing you from upgrading in a second.

Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevolent dictator's computer and temporarily disabled his nuclear launch capability, we have to think about covering our tracks so that he and his minions can't track our good works back to us.

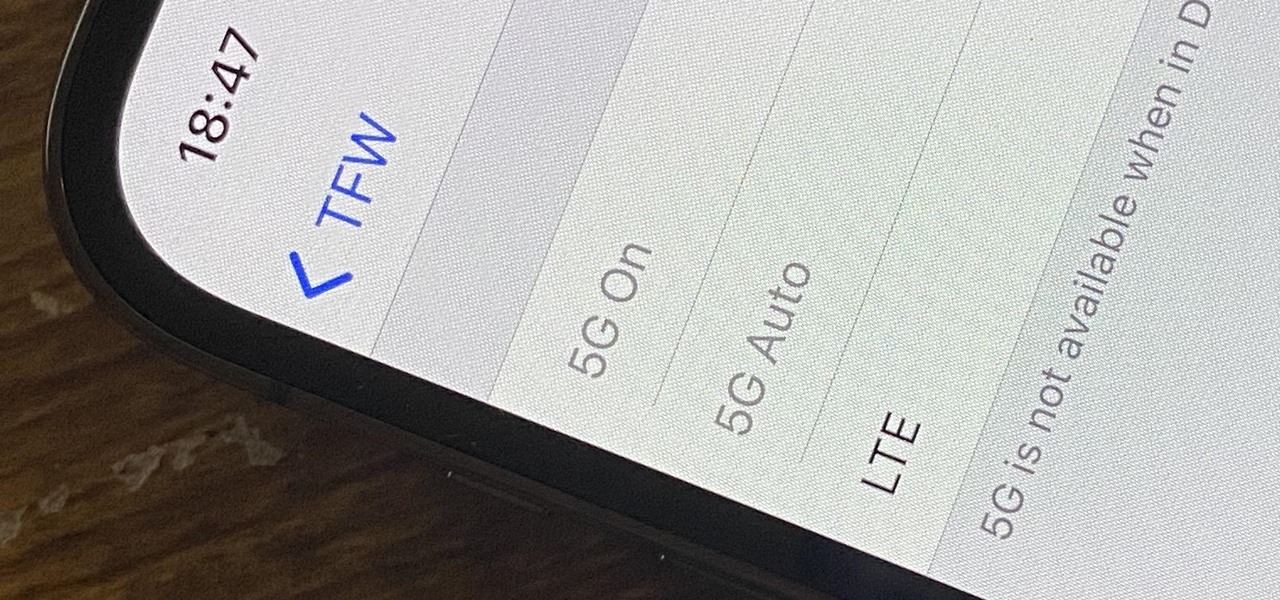
One thing you can expect from Apple is that big features work right out of the box. The company designs its products to be easy to use for any experience level, so you might expect the same to be true for 5G, one of the biggest selling points for the iPhone 12, 12 mini, 12 Pro, and 12 Pro Max. Yet, you might have trouble getting 5G to work on your brand new iPhone. Here's how to avoid that.

Apple has their regular iPhone 11, then two higher-end "Pro" models. Samsung went the other way — they have the Galaxy S20 and S20+, then there's the S20 Ultra. But one thing these smartphone lines do have in common is the base model flagship. How do they compare?

With the rapid demise of the 3.5 mm headphone jack, Bluetooth is fast becoming our best option for universal audio. The problem is, with over a decade of it being a standard component, many of us still own a reliable pair of wired headphones that we don't want to gather dust. Well with one tool, you can have your cake and eat it, too.

To quote MKBHD, cheap phones are getting good. Each year we are seeing manufacturers start to offer more for much less. This not only translates to cheaper flagship phones, but better budget phones. The latest example of this is the Alcatel 3V, which is redefining what you can get at $150.

Ads can detract from your mobile browsing experience, especially if they appear out of nowhere as popups or large annoying banners that take up almost all of your screen. If those weren't bad enough, some ads appear as extremely loud videos that can even disrupt others around you. In fact, ads have gotten so obnoxious that even Google itself was forced to act.

Huawei's push into the US market has by no means stopped, even despite the recent US government pushback. Huawei has already released their top-notch flagship device from 2017, the Mate 10 Pro, and a couple great budget and midrange devices. Their latest release offers an upgrade to a past release.

One of Android 8.0's central themes was battery improvements. Google implemented background restrictions and a few other under-the-hood changes, but the biggest battery-saving measure was almost user-hostile: A static notification that tells you when any of your apps are running in the background.

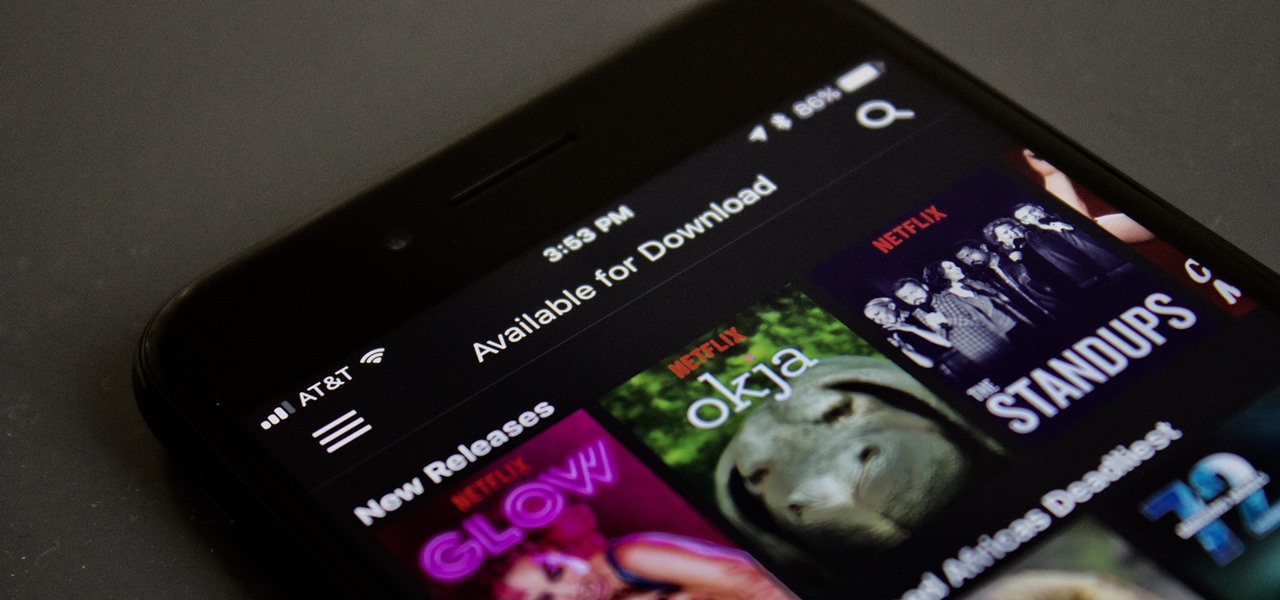
Netflix added the ability to download TV shows and movies on Android and iOS for offline binging back in Nov. 2016, and the process is the same as it is today. So if you anticipate having some downtime to catch up on Narcos or give Bright a try when you'll be away from a secure Wi-Fi connection, download videos onto your phone and save your data for more important things.

Reigns recently went on sale on the Google Play Store (sorry, iPhone users), and that inspired me to give it a go. I've wanted to try this one out for a while now, but the steep price tag kept me away. ($2.99 is a lot for me, okay?)