In the latest software updates for iPhone and iPad, there's an even easier way to view all your saved Wi-Fi networks and credentials and share them with family, friends, and others who need access.
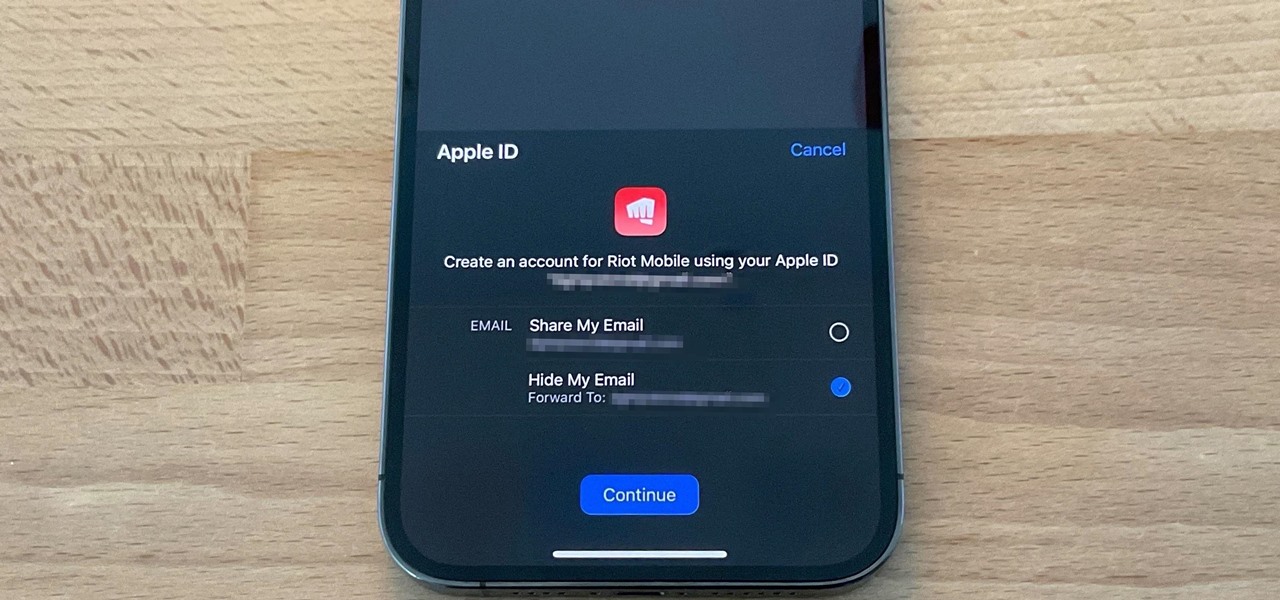
The "Sign in with Apple" service lets you create accounts with third-party apps and websites more easily using your Apple ID. More importantly, it can hide your personal email address using auto-generated disposable email addresses. However, it's easy to lose track of the accounts you use with Sign in with Apple, as well as any throwaway email addresses you used to hide your actual address.

On this platform, we talk a lot about the future of augmented reality, and we pay attention to what is being said elsewhere as well.
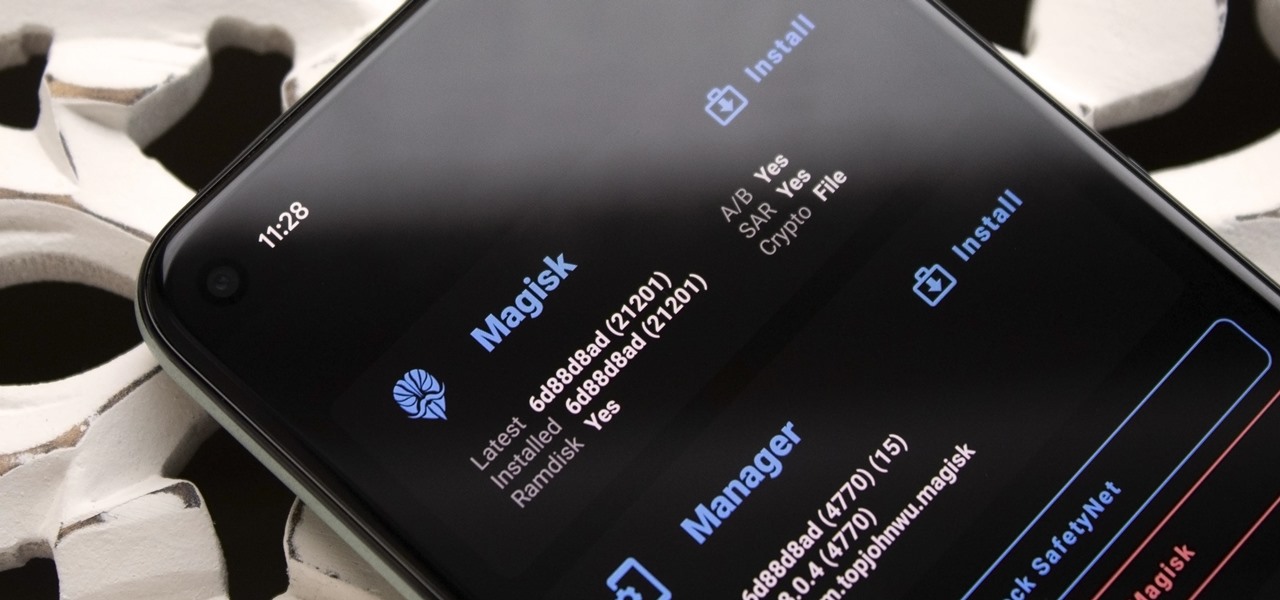
Okay, so you rooted your Android phone .... now what? There are a few ducks you need to get into a row, like backing up your stock boot image, getting SafetyNet sorted, and improving security with biometrics. But there are also awesome root mods waiting for you — just don't get ahead of yourself.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

You're a busy, on-the-go professional, so you deserve an email client that keeps up with you. "Mail" on iPhone wasn't always the best option, but thanks to iOS 13, it feels like a completely different app. That said, there are plenty of alternatives that offer a different experience. Better yet, these apps are free. You won't need to spend a dime to try them out for yourself.

Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.

Over the years, we've seen security breach after security breach, as well as high-profile data scandals where collected personal information was misused by companies. Apple makes customer privacy a priority, so there have been few issues to worry about when it comes to its services on your iPhone. However, there are still plenty of privacy settings to explore and change, especially within Safari.

All fields of study have their own language. For people interested in learning about microbes, the language can sometimes be downright difficult — but it doesn't need to be. From antibiotics to xerophiles, we have you covered in an easy-to-understand glossary.

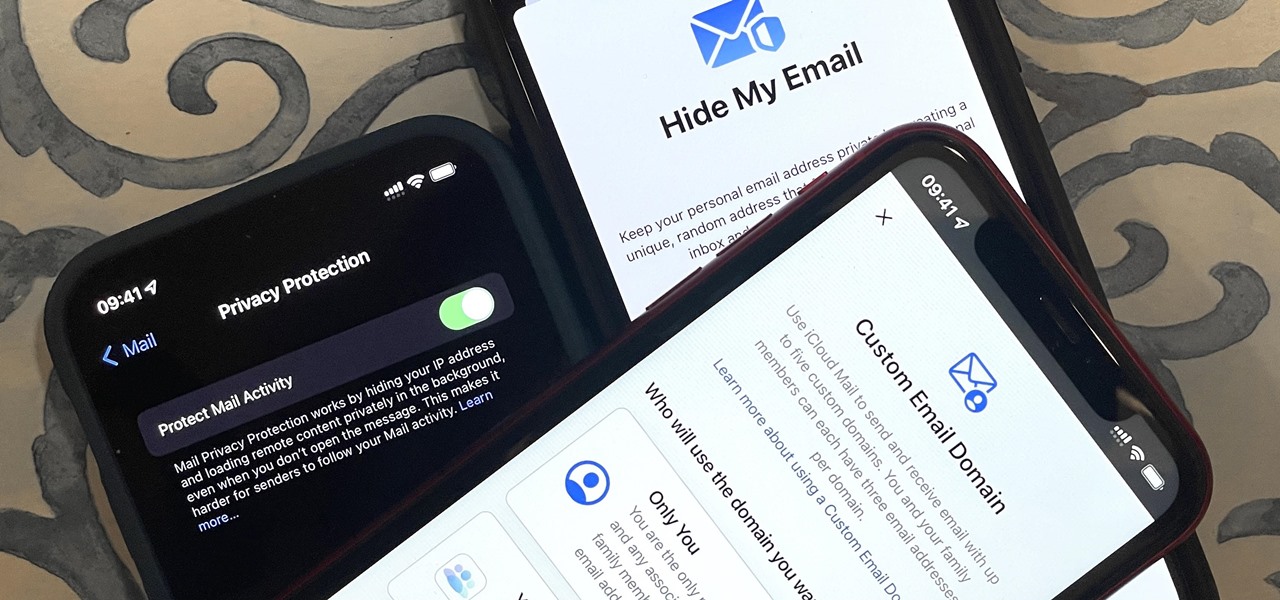
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.

You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

As a hacker, the final stage of exploitation is covering their tracks, which involves wiping all activity and logs so that they can avoid being detected. It's especially crucial for persistence if the target will be accessed again in the future by the attacker.

Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

This video is a short tutorial to assist in setting the combination for a Giant Surelock. In the event that a combination is compromised, it is important to change a lock to prevent from unwanted break-ins or theft. Watch this instructional video and learn how to reset the combination on an Giant Surelock.

This video is a short tutorial to assist in setting the combination for an OnGuard Lock. In the event that a combination is compromised, it is important to change a lock to prevent from unwanted break-ins or theft. Watch this instructional video and learn how to reset the combination on an OnGuard lock.

WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.

An effective warm up is essential for climbing: you will climb better and are less likely to sustain an injury. With no warm up, performance is compromised, fatigue comes quickly, and injuries are more likely. All together: Not Good!

Six months ago, 1.3 million registered users of Gawker Media had their passwords compromised when the site was hacked by Gnosis. The passwords were encrypted, but 188,279 of them were decoded and made publicly available for all to see. Just three weeks ago, Sony Pictures was hacked by LulzSec, with 1 million passwords taken and 40,000 made publicly available. Comparing the two data sets, Troy Hunt found 88 accounts on both sites that used the same email address, and of those accounts, 67% use...
Unless you avoid the news entirely, you've almost certainly heard about the hacking sprees that have been taking place over the past several weeks. Tens of thousands of usernames, passwords and email addresses have been released online for anyone to download. Thankfully, it seems that one kind soul has put all that compromised info to good use.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

Watch out Macs. Flashback is back. Variations of the trojan have reportedly infected 600,000 Mac computers around the globe, with about 57 percent in the U.S. and another 20 percent in Canada.

Let's begin your journey into cPanel. Today, we'll start with something easy. The tutorial below will teach you how to change your password. It is good practice to change your cPanel password every few months or as soon as you think your password's been compromised.

These are the KGB Agent Guidelines as taken from 542542.com/guidelines. kgb Guidelines

Since its inception in 2007, the Pwn2Own computer hacking contest has been challenging the vulnerability of mobile phones and web-related software. In 2010, the fruit of two full days of hacking came down to the exploitation of the following web browsers: Safari 4 on Mac OS X, Internet Explorer 8 on Windows 7, and Firefox 3.6 on Windows 7. The winners walked away with the successfully hacked computer, plus a cash prize, but they left one Godly browser intact: Google Chrome. Even the savviest ...

This past Sunday, a group called Gnosis launched a massive hacker attack on Gawker media, one of the web's most popular blog networks (Lifehacker, Gizmodo, Jezebel, io9, Jalopnik, Kotaku, Deadspin and Fleshbot). 1.3 million registered users' passwords were compromised, and 188,279 of them were decoded and made public. The biggest takeaway? Many Gawker denizens use downright dumb passwords. (Guess they didn't see their own Lifehacker's story on avoiding such a thing.)

Last time, we looked at archaic cryptography, so you should have a basic understanding of some of the concepts and terminology you'll need. Now, we'll discuss one of the most important advances in computer security in the 20th century—public key cryptography.

This Null Byte is a doozey.

As hard as you try to protect your valuable information with strong passwords and anti-doxing measures, there's nothing you can really do when someone else gives up your goods. And that is the case with the recent Global Payments breach.

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

Does the above card seem a bit unfair to you? I see that Bacheeze has already poisoned your minds with his anti-blue propaganda. These are the words of one who has had his 7 mana-Force of Nature Unsummoned one too many times. He seems to think that those of us who play blue are all a bunch of malcontents who deal with our misery by spreading it around. This is entirely true.

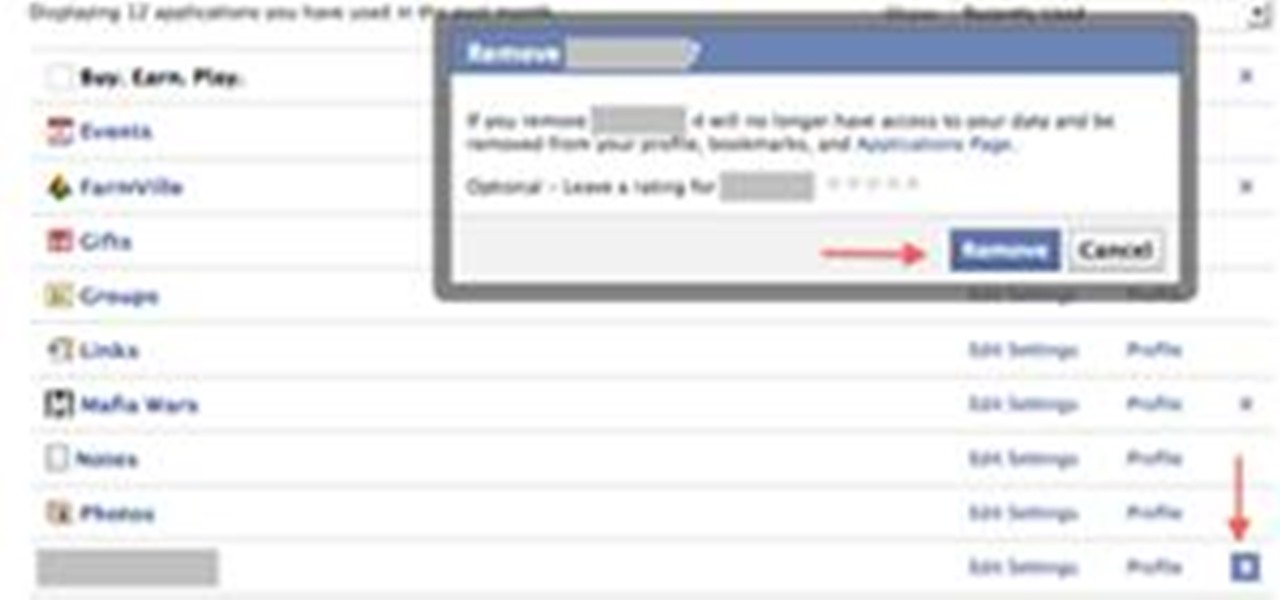
Please share this info with all your facebook friends. It's not just Farmville players that are affected by scams and spam! This post will help you keep your facebook account clean and safe. We start by showing you a scam and discussing what is real, then we show you how to remove pages you don't want, and finally how to remove apps you're not using. Please scroll down to which ever part you need!

You're sitting in front of your grandmother's Windows XP machine that has the worst infection you've ever seen. Safe mode? No dice. Restore points? They're compromised. Even worse, all of the files are hidden and none of the executables will run! This leaves her computer in a bricked state. Without some serious CPR, it will be lost to you. Sure, you could just reinstall the system, but then you might lose all of that valuable data.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-disc call 'Kon-Boot', which allows you to bypass any Windows 32 or 64 bit OS, as well as Linux passwords. There is both a paid and freeware version available.

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?