
How To: Control two computers with one keyboard and mouse
Two computers, two displays...one keyboard and mouse. Molly Wood from CNET shows you how a free software app (Synergy) can make beautiful music between PCs, Macs, and even Linux.


Two computers, two displays...one keyboard and mouse. Molly Wood from CNET shows you how a free software app (Synergy) can make beautiful music between PCs, Macs, and even Linux.
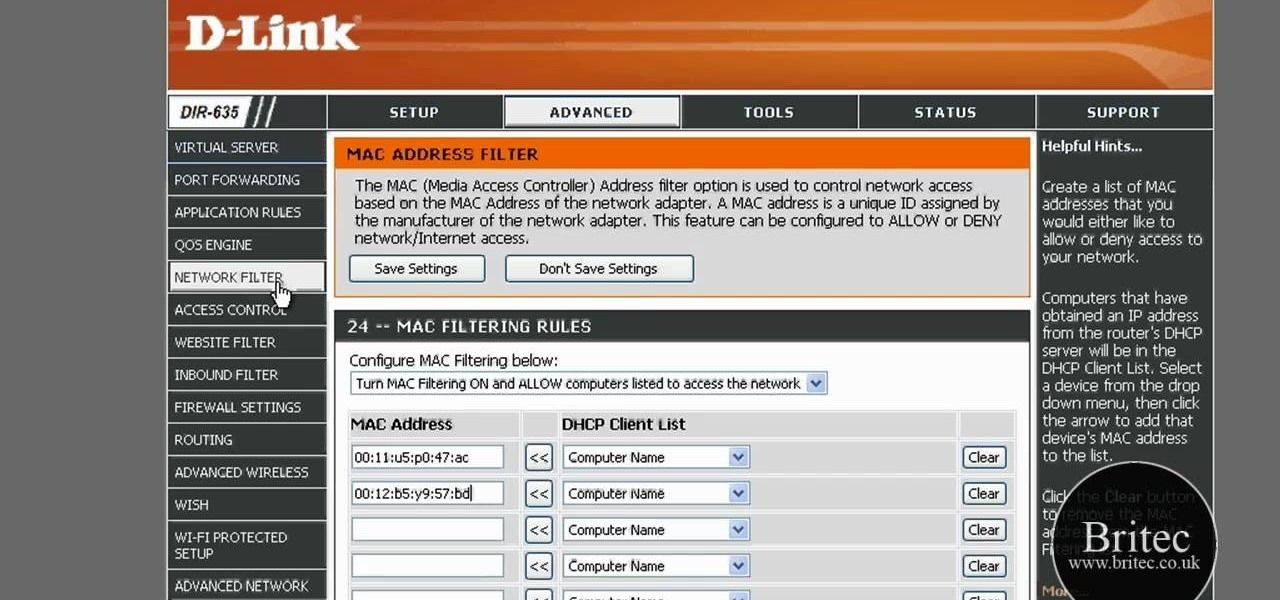
In this tutorial, we learn how to detect all computers connected to your Wi-Fi network. To begin, go to the website, http://msdn.microsoft.com/en-gb/netframework/aa569263.aspx. Once you are on this site, download and install the program. Once it's installed, open the program and then look for the MAC address. Once you find this, go back to the website and enter this into the MAC address line. After you do this, you will be able to see what computers are listed on your network. If you see any ...
In this tutorial, you'll learn how to share a single keyboard and mouse across multiple Windows, Mac or Linux computers with an application called Synergy. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.
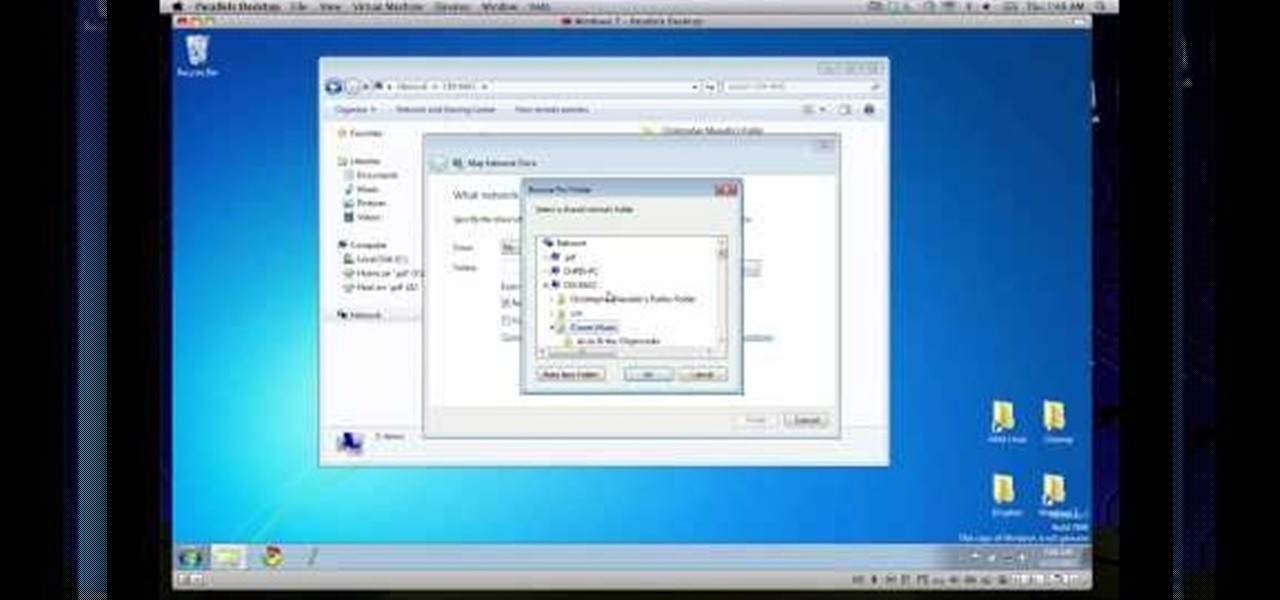
In this clip, you'll learn how to transfer files to and from Microsoft Windows, Apple Mac OS X & Linux desktop or laptop computers. For more information, including a complete demonstration, and detailed, step-by-step instructions, as well as to get started using this trick yourself, take a look.

Some tricks which you can play to your coworkers in the office including: turning Windows on to high contrast mode, creating a fake desktop, and pulling a fake delete prank.

Whether you are sharing an internet connection, working together or just playing group video games, you will need to network your computers. Check out this tutorial and learn just how easy it is to create a home network.

If you've ever connected your iPhone to a computer before, you know iOS prompts you to "Trust" the computer and enter your passcode to confirm. According to Apple, trusted computers can "sync with your iOS device, create backups, and access your device's photos, videos, contacts, and other content." That's a lot of permissions to hand off, especially if the computer's not your main laptop or desktop.

I regularly use iTunes on my home laptop and my work desktop forty-five traffic minutes away. I'm ashamed to admit it, but until recently, I'd been saving my iTunes library on a USB and transferring it back and forth, over and over again, between the two computers.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

The $35 Raspberry Pi is an amazingly useful single-board computer (SBC) with a good balance of price, performance, and connectivity options. But for some projects, it just isn't enough. Whether you need more computing power, a smaller size, or better machine-learning capabilities, there are other options available.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.
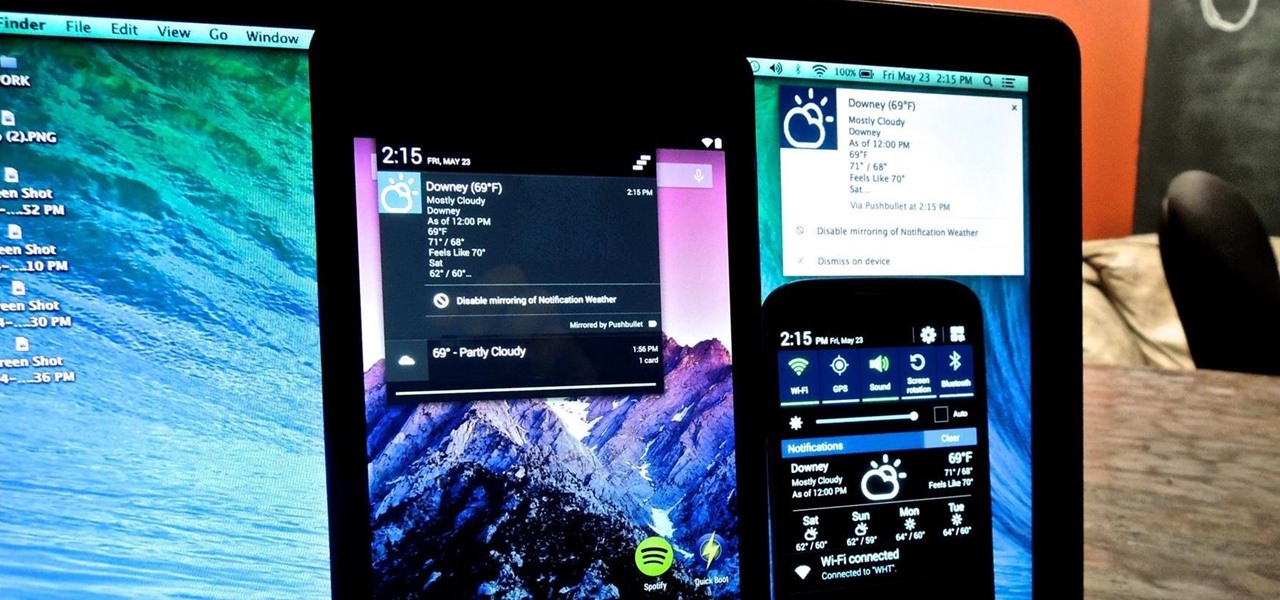
We're not always near our phone, so Pushbullet made it easy to get your phone's notifications straight to your computer, like calls and text messages. But with their latest update, you can also sync alerts with other Android devices using their new cross-device mirroring feature.

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.
If you've got a desktop computer, I can almost guarantee that you've got a widescreen monitor set up in landscape mode. It's how just about everyone uses their monitor these days, including myself. Except that it's not always the best way of working.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.
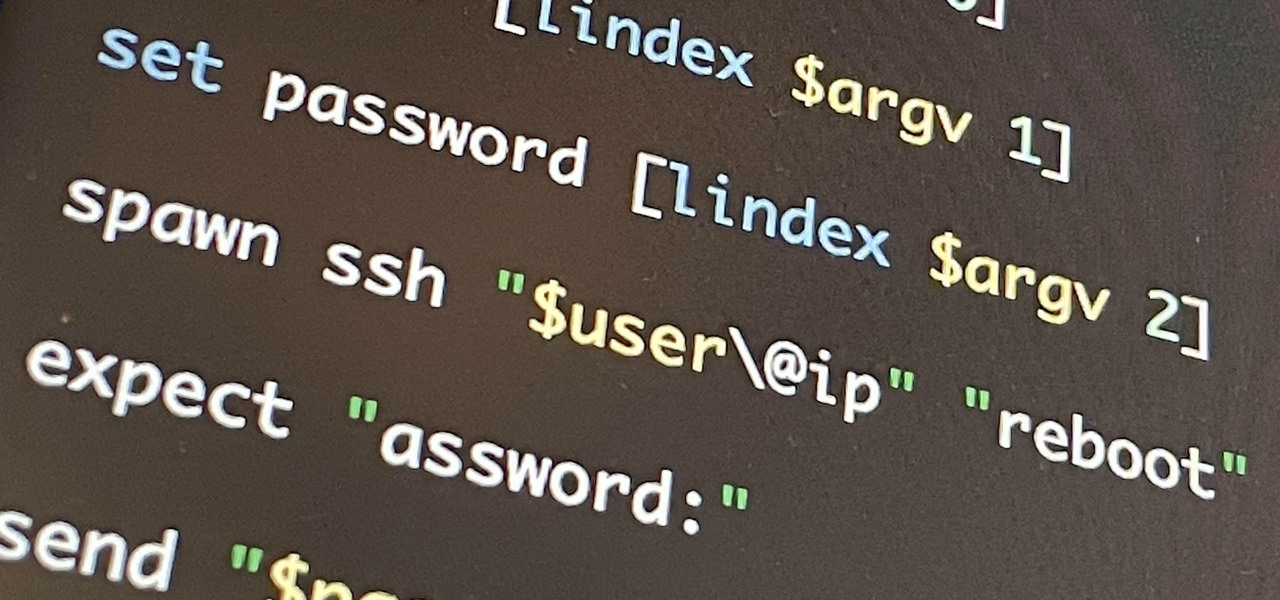
If you're getting into automation, Bash scripting is usually the way to go. However, there are a couple of limitations, and one of them is logging into another device like a Raspberry Pi and running a script automatically. To help in those situations, we're going to automate delivering an SSH payload with an "expect" script.
The USB Rubber Ducky is a well-known hacking device in the cybersecurity industry, but it needs to be preprogrammed before it can be used. That means it's not easy to issue commands to a target computer since you can't interact with it from afar after plugging it in. And if you don't know what the target computer is, you might come up empty. That's where the WiFi Duck comes in handy.
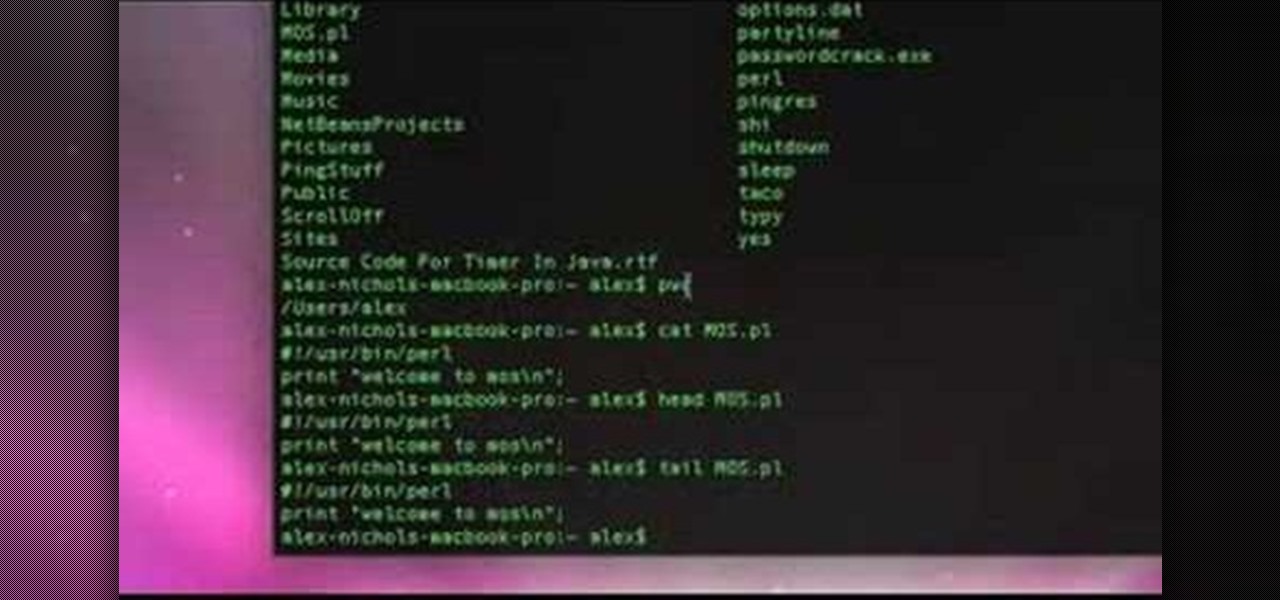
Every Apple computer running Mac OS X comes with a handy application called Terminal… MacBooks, MacBook Pros, Mac Pros, iMacs, etc. They all have Apple Terminal, and it can be found in your Utilities folder in Applications. Which means you can use it.

Need help figuring out how to remotely unauthorize a computer from accessing a file you've downloaded from iTunes? This clip will show you how it's done. It's easy! So easy, in fact, that this handy home-computing how-to from the folks at Tekzilla can present a complete overview of the process in about two minutes' time. For more information, including detailed, step-by-step instructions, take a look.

You may not realize it but when you buy music or movies from iTunes, you have to authorize it to be used on a computer and you can only authorize five computers. It's pretty easy to buy and replace computers and if you don't de-authorize the old ones, one day you will download a song and it will tell you that you have reached your five computer limit. At that point, what do you do if you don't have any of those computers anymore? Now Apple has put a fix in iTunes itself. Go to the iTunes stor...
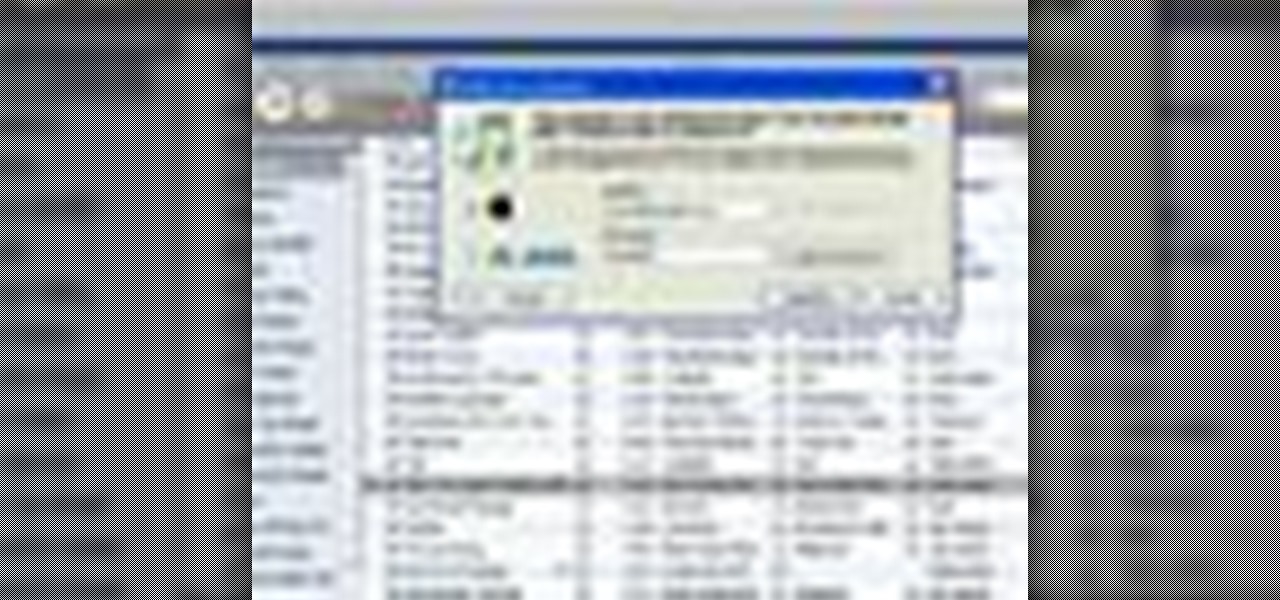
Authorization allows you to copy your music store purchases to other computers and burn them to CD and protects the artists. Each computer you use to play your purchase must be authorized using your music store account. You can authorize up to 5 computers; yours is automatically authorized.

Interested in sharing web bookmarks across your various computers and browsers? This clip from the folks at TekZilla will teach you how to do just that. For complete instructions, and to get started sharing your own Internet bookmarks across different PCs and browsers, watch this home-computing how-to.

With music sharing and iTunes, you can share you music with any other computers running iTunes in the same home. For example, you can play music from your desktop computer on your laptop.
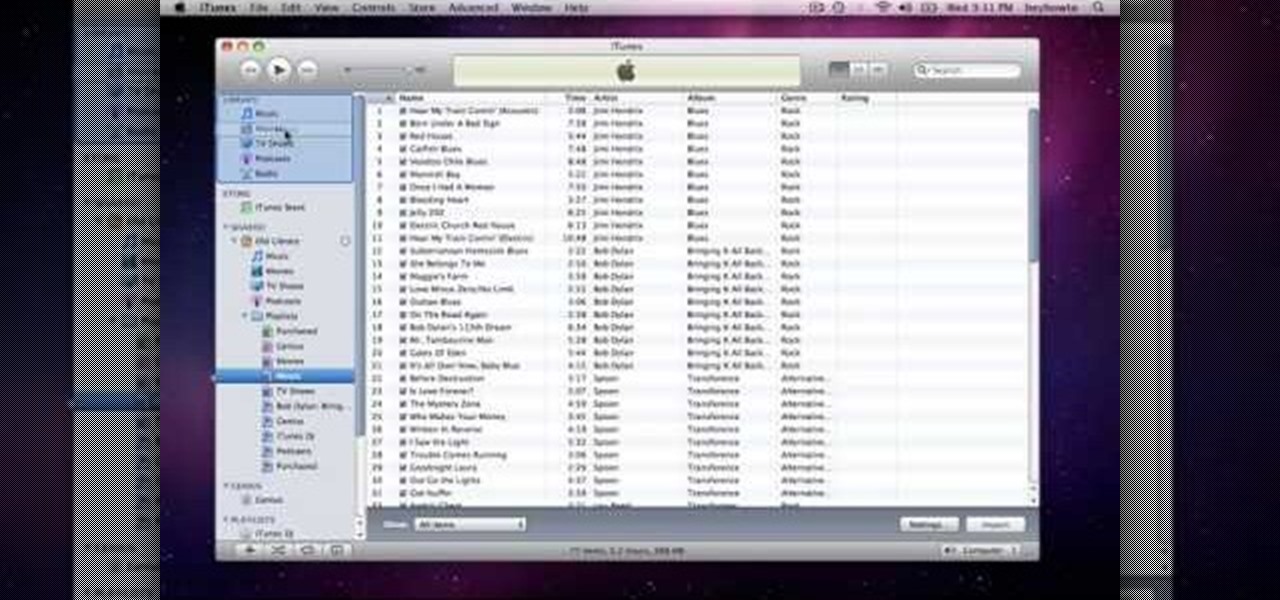
How to use Home Sharing in iTunes 9 to transfer music files to another computer. First make sure both computers have iTunes version 9 installed. To check this go to the iTunes 9 menu next to file in upper left and select the about item. On windows machines this will be in the help menu. In the computer with the music files we need to make sure the iTunes library is nicely organized. Again go to iTunes menu, this time open the preferences menu, and advanced icon. Check mark both sections "Keep...
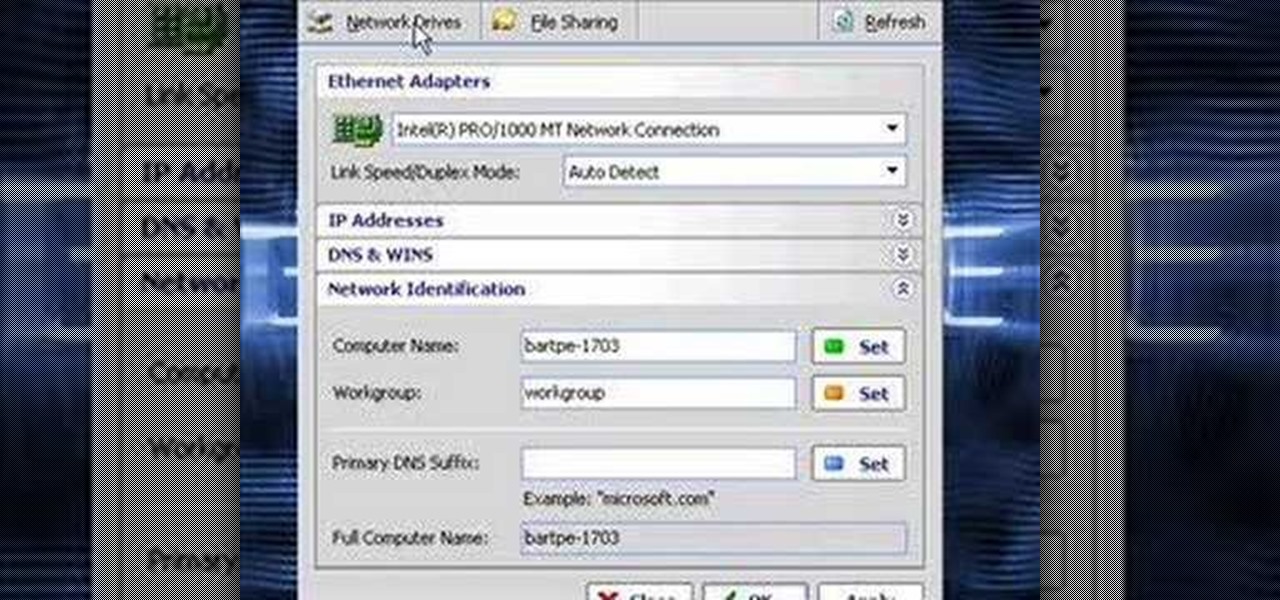
In this video the instructor shows how to clone computers across the Local Area Network using BartPE and Selfimage. To do this first we will have an original computer. Now create the image of the hard drive of the computer and share it on the network drive. Now, using that image from the shared folder you can start the clones of other computers by overriding their hard drive using this image of the main hard drive. Using this technique you can clone multiple computers which are the exact dupl...

In this video tutorial, we learn how to share content from an iTunes library with multiple computers with the Home Sharing feature. It's easy. So easy, in fact, that this home-computing how-to from the folks at CNET can present a complete overview of the process in just over two minutes. For more information, including a complete demonstration detailed, step-by-step instructions, take a look.
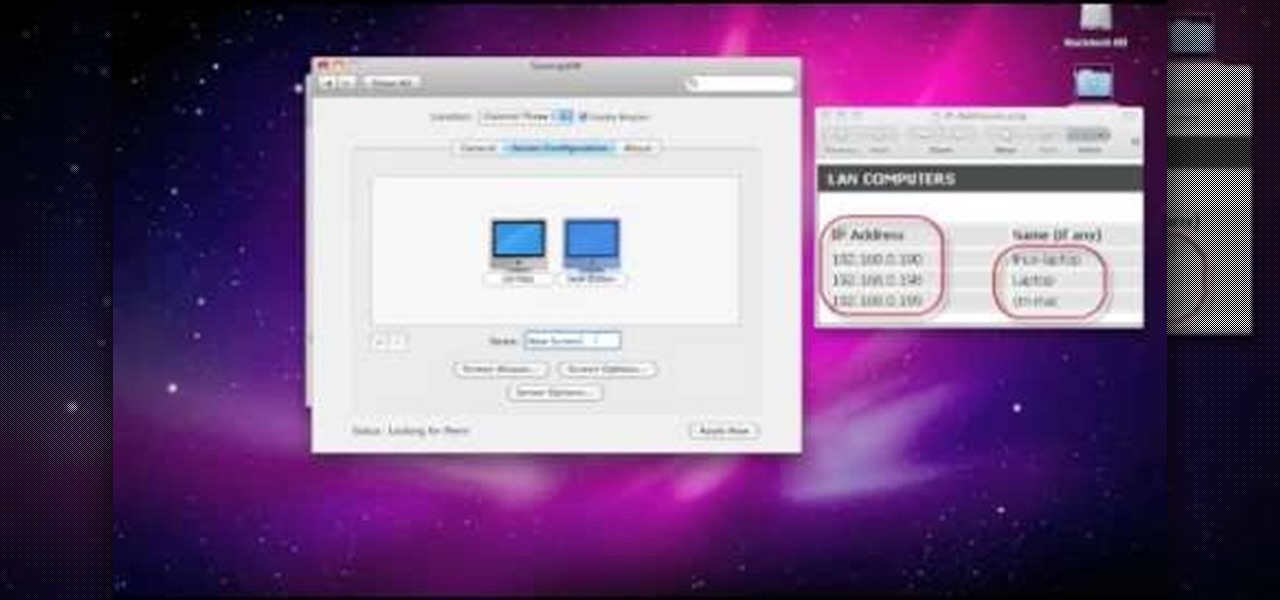
In this clip, you'll learn how to set up and use Synergy to control multiple Windows, Mac or Linux computers from a single keyboard and mouse. For more information, including a complete demonstration, and detailed, step-by-step instructions, as well as to get started using this trick yourself, take a look.

Dropbox is a program (free at the basic level) which will allow you to access important files from multiple files. Just drop your chosen files into the Dropbox folder, and you'll be able to use and access these files from synced computers. You can even add music to iTunes remotely!
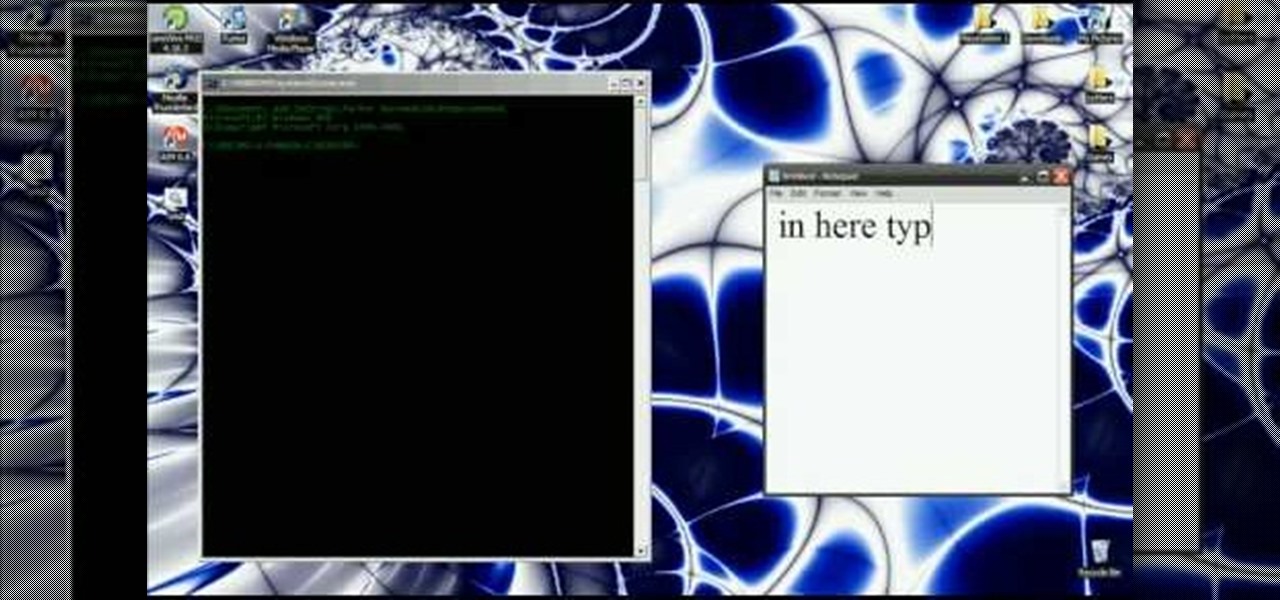
In this video you will learn how to get past website blocks on your school network. Some school computers have command prompts blocked. If this is the case then you will want to open a notepad. In the notepad type command, then save as something school related, making sure the file name ends with .bat. Do not save it on the desktop, but rather in a folder deeper on the unit. Once you've saved it, make sure no one is looking, then open the file. It will bring up a blank black window. In the bl...
With .Mac Sync, you can ensure your contacts, bookmarks and other information is synchronized between all of your Apple devices. For more, and to learn how to synchronize your own Apple devices using .Mac Sync, watch this video tutorial from Apple.
This video will show you how to defrag your computer's hard drive to increase its speed. To defrag your hard drive, do the following: Go to 'Start', 'All Programs', 'Accessories', 'System Tools', 'Disk Defragmenter'. Select the hard drive that you wish to defragment, and select 'Defragment'. Depending on the size of your hard drive, this process could take between one and two hours to complete. After the process is complete, your computer will be uncluttered and will hopefully run a little fa...
In this video, we learn how to transfer your iTunes library between two computers. Now, open up your computer drive and go to the backup menu and find your music. Clear all the music you have in there currently, then add your current music library to your backup file. After you copy this to a backup CD, install iTunes on the other computer you will be using. After you do this, close iTunes and then insert the backup CD into the computer. Once this loads, you will be able to transfer the music...
iCloud is a very convenient service that allows you to share windows between two computers. To learn how to use iCloud, watch this video. With iCloud on your PC you can share information simply and efficiently between multiple workstations, or friends.

There are 133,000 PCs become disused DAILY! That's an absurd amount of electronic waste - let's learn how to stop it!

This easy tutorial shows you how to change your computers appearance. You can change your computers windows, buttons, color scheme and font size.

In this installment of her Work Smart series, Gina Trapani returns to explain how to use three diverse applications to better synchronize the contents of your home, office, and whatever other computers you might have. They are Googledocs, Dropbox, and Evernote, and each one can help your files become easier to access from wherever you might be computing.
Statesman

In this video we learn how find out IP addresses of websites and shut down the computers with those IP addresses. To do this click "start", then "run" then type command prompt. In the command prompt type "tracert website" (example tracrt Google.com) then hit enter. Various IP addresses should be returned. Then in the command prompt type "shutdown-i" and hit enter, this opens the remote shutdown dialogue. In this dialogue you can add the IP addresses and adjust the various other options then c...

Since today (11/11/11) is the last 6 digit binary date this century, I thought we should look at some kinetic binary calculators.