If you read the reviews on Google's Pixel C, you'll notice one big complaint about the tablet/laptop—most reviewers feel that Android simply isn't ready to be used as a desktop OS. The developers at Jide felt the same way, so they set out to make a custom version of Android with proper multitasking support and a UI optimized for the mouse and keyboard.
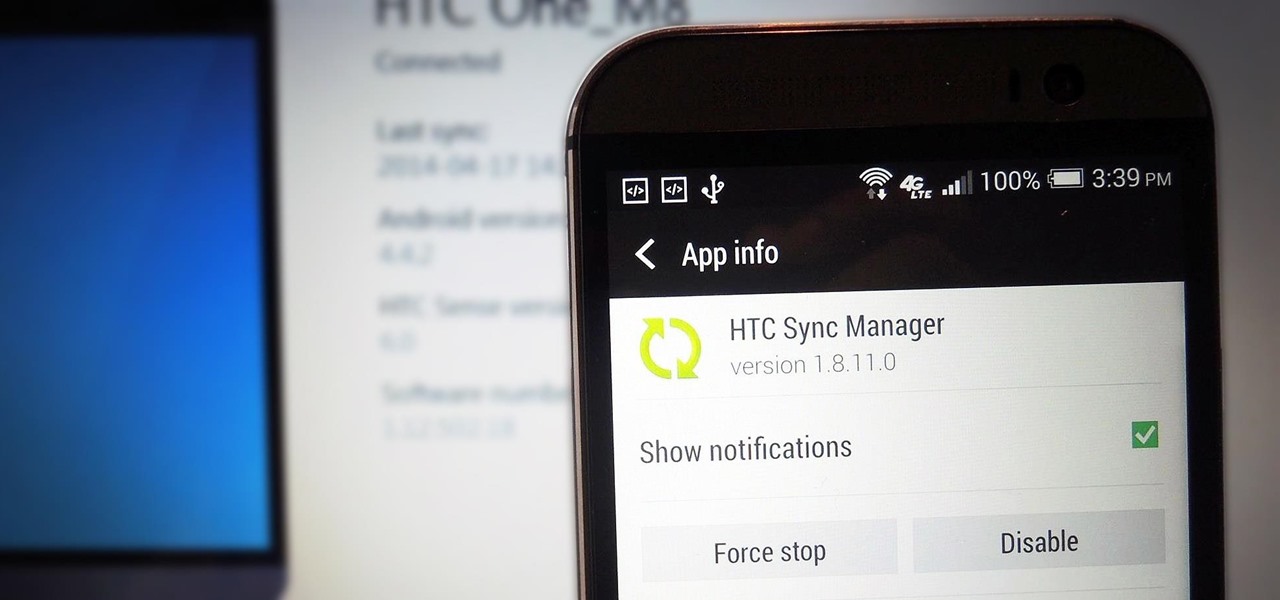
If you've just upgraded to an HTC One M8, chances are you've got some media files you want transferred over from your computer or previous phone. Even after you've done that, there will be times when you want to transfer content back to your computer for safe keeping.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.
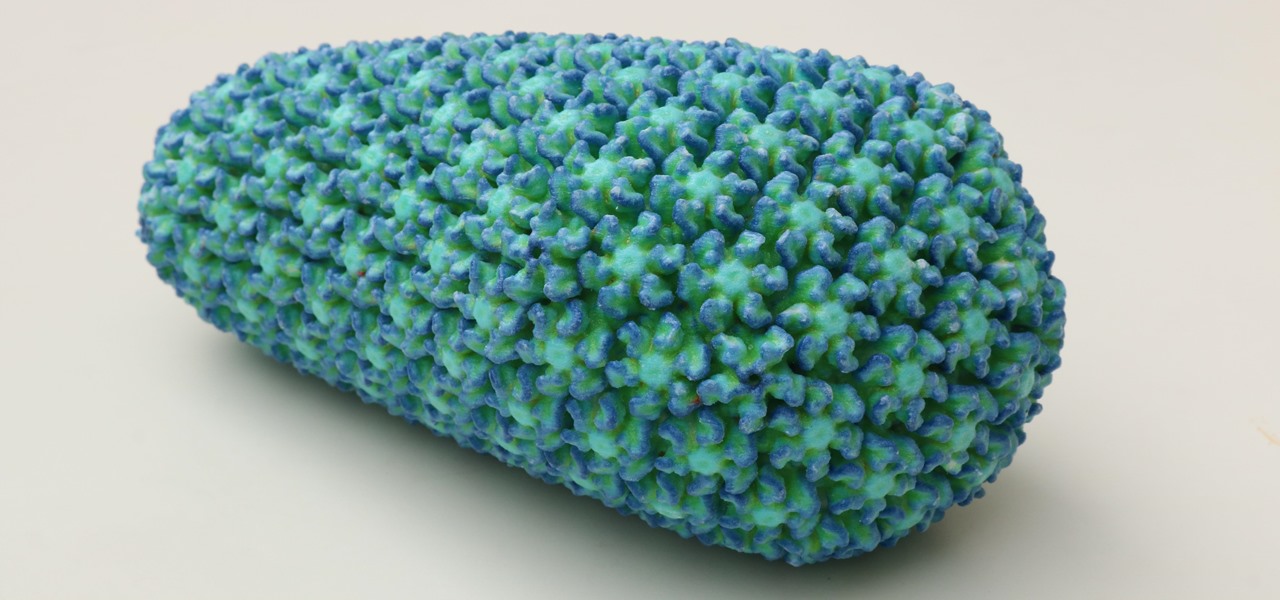
While some researchers look for drugs to treat HIV, other scientists delve deep into the virus itself for answers on how it causes infections.

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

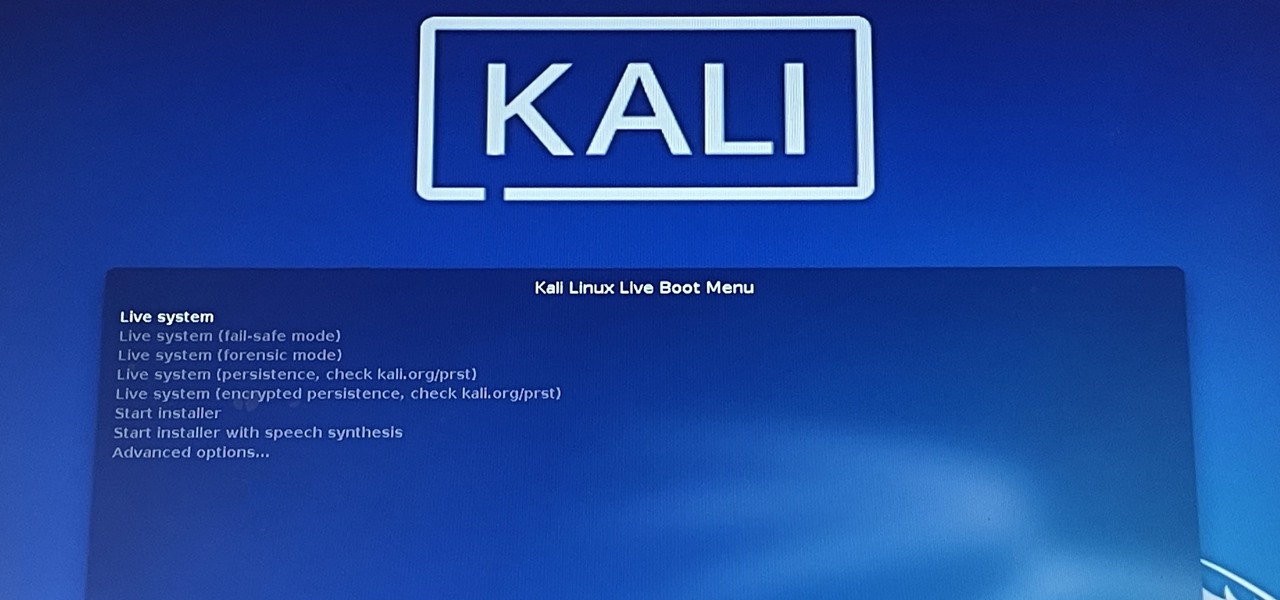
Kali Linux is the go-to Linux distribution for penetration testing and ethical hacking. Still, it's not recommended for day-to-day use, such as responding to emails, playing games, or checking Facebook. That's why it's better to run your Kali Linux system from a bootable USB drive.

With a rather brief and obscure introduction, Brad teaches us how to hook up our computers and our laptops with a television. He starts us off by saying how this can help alleviate boredom when working out on a stationary bike. With a close up of the outlets in the back of the television, Brad shows us step-by-step how to do this process. The last few minutes he tries to humor us a bit by showing how it all works in the end.

This video demonstrates how to check your computer for hackers. The video explains a little bit about hacking and shows how to see the IP addresses of the computers connected to yours.

In this video, a doctor gives you great information on how to relieve shoulder, neck, and back pain from prolonged computer use. It's great advice for those of us who work at computers more than a few hours a day. The best way to improve tension is to fix your posture first, and make sure the screen is not too close to your eyes. Stop shoulder, neck and back tension from computer use.

Many folks seem to treat their computers as a sort of mysterious alien technology that only the shamans of the IT Department can comprehend. You might have gotten it into your head that you're just not good at computers and will never understand them. On the contrary, getting a basic grasp on all the amazing stuff inside your computer doesn't require you to be a technological genius. Most people will never have a need or desire to open up their computer and poke around. But it's your machine....

Password strength and encryption are important things when it comes to computers. A password is the entire security of your computer, and OS passwords are not hard to break. Most users believe that if you have a password on your computer via the OS, that you are safe. This is not true at all, sadly.

Earlier this month, game developer David Braben and his Rasberry Pi nonprofit foundation revealed a $25 USB PC. The computer can connect to an HDMI monitor on one end, and a USB peripheral on the other (such as a keyboard or a USB hub). You can use the USB hub to connect multiple items, such as a keyboard, mouse, printer, USB ethernet/wireless, creating a fully functional computer.

Blacksmith Sage Werbock —also known as the Great Nippulini, "pierced weight lifting extraordinaire"—welded together this Star Wars Imperial Walker sculpture with a bunch of old computer parts and scrap metal. Currently listed on Etsy for $450, the AT-AT is artfully assembled as follows:

Computer viruses are terrifying. They are undetectable, dangerous, and operate constantly right under your nose. For the average computer user, there are only a few repair options. You could buy expensive antivirus software that causes more problems than it fixes, you can wipe your hard drive clean and lose all of your important data, or if all else fails—just switch to Linux.

Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read online articles about elliptic curve cryptography applications to C++? Well, then this article is for you!

Your BIOS, or Basic Input Output System, is the firmware on your motherboard responsible for initializing your computer's hardware when it is first powered on. It probes for video adapters, RAM, the whole works. The BIOS provides a small library of basic input/output functions used to operate and control the peripherals such as the keyboard, text display functions and so forth, and these software library functions are callable by external software such as the OS and system software within sai...

This is Null Byte's fourth part in a series about fully securing our computers (Part 1, Part 2, Part 3). In our last Null Byte, we went over how to encrypt an entire operating system to protect our data, however, this doesn't fully protect us. In the case of legal extortion, the government can actually make you give up your cryptographic key to your computer so that they can look through it.

There is a near-infinite amount of ways a computer can be broken into. But that does not mean that there isn't a reason to secure our computers as best as we possibly can. It's like the principles of a secure house. Which are the most secure houses? The ones with locks and advanced alarms, obviously, but not for the reasons people normally think.

When you buy computer parts, it can be a tough decision where you want to put all of your hard earned dollars into. Not only that, but when you buy a top of the line component, 3 months later (at most), your hardware will likely be outdated. This puts consumers like us in a bit of a pickle when it comes to purchasing, especially on a tight budget.

This is Part II in the Lockdown: The InfoSecurity Guide To Securing Your Computer series. Before beginning, check out Part I. This article will cover using alternate software to increase your security and will provide you with some information about websites and programs that test a computer's security. It will also guide you to software you can install or follow so you know what programs need to be updated on the computer. Lastly, I will talk about some features that should be disabled when ...

I love my laptop. It goes wherever I go. Unfortunately, that means that it also gets pretty grubby after a while. The screen gets dusty. The frame gets smudgy. The spaces between the keys fill up with crumbs of questionable origins. And my desktop? That thing is a dust bunny magnet.

This is a two-part series to locking down the computer to provide maximum protection. Even though this guide will sound intrusive, we are talking about reality here. Extreme measures must be taken to protect our computers, especially when we have confidential documentation or do internet banking, which many people do. We all have to use electronic devices at some stage, whether it be for business or personal use.

The logic board was a common malfunction in the old PowerBooks, but hopefully the unibody MacBook Pros are a little more resistant to failure, but if you have to get a new one, do it yourself. See how to remove the logic board on a MacBook Pro 17" Unibody laptop.

One of the first things you'll have to do when repairing and opening up your MacBook Pro 17" Unibody is taking off the bottom case. This is where you'll access all of your guts. See how to remove the bottom case on a MacBook Pro 17" Unibody laptop.

The new Unibody MacBook Pro's are a little different in design than the older MacBooks, so it may be a little confusing on how to see the innards of the laptop. Watch this to see how to remove the hard drive and battery of the MacBook Pro 17" Unibody.

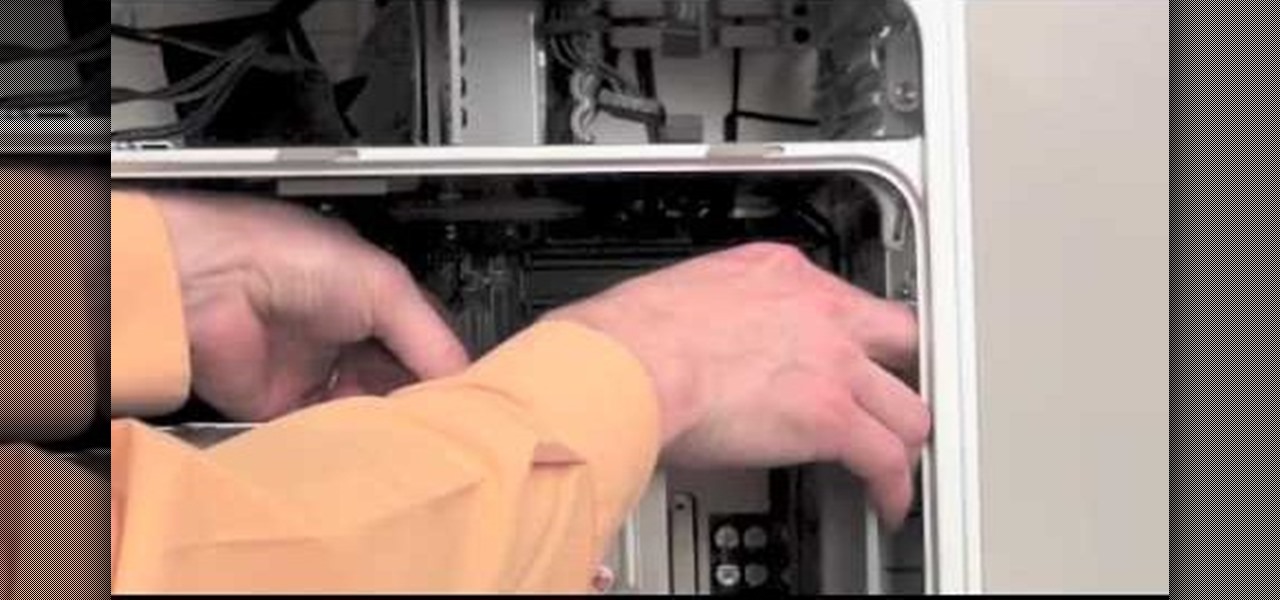
Is your motherboard toast? If your logic board has burned out, it's a sad thing, but you're going to have to replace it. See how to remove the logic board from the Power Mac desktop computer.

Your power supply on the bottom of your Mac may need to be replaced. If you're not sure how to remove it, no problem. See how to remove the power supply from the Power Mac desktop computer.

Can't turn on your computer? The power button might be broke. If so, you're going to have to replace it, and you can do it yourself. See how to remove the power button from the Power Mac desktop computer.

For some reason or another, you might have to remove the processor from your Power Mac. If you don't know how, see how to remove the processor from the Power Mac desktop computer right here.

Is your computer overheating? It may be because of a faulty fan. See how to remove the fan in the Power Mac desktop computer.

To remove your airport card from your Power Mac, you're going to have to know what you're doing… see how to remove the airport card from the Power Mac desktop computer.

Maybe you only have 1G of RAM in your Power Mac. Maybe you ace some bum memory. Maybe it's just time to upgrade. Either way, this RAM upgrade video can help. See how to remove the RAM memory from a Power Mac desktop computer.

Your graphics card may be a little outdated in your Power Mac, so upgrade it to a one that can handle all of your gaming needs. See how to remove the graphics video card from your Power Mac desktop computer.

Your sound from your Power Mac may be nil, or maybe it just sounds really bad. The speaker may need to be replaced. See how to remove the speaker from the Power Mac desktop computer.

If your discs are getting jammed in your optical drive, or if your CDs and DVDs simply aren't playing in your Power Mac, it might be time to replace that old SuperDrive. See how to remove the SuperDrive optical drive from the Power Mac desktop computer.

Want to upgrade your hard drive in your Power Mac? It's a pretty simple task, once you can get inside your computer. See how to remove your hard drive from you Power Mac desktop computer.

Need to fix your Power Mac? Disassembling the Power Mac could be tricky, but not now. See how to remove the side case and fan from the G5 Power Mac desktop computer.

PowerBook Medic is the ultimate resource for Mac computers and electronics repair. They have helpful tutorials on most Apple products including the MacBook, MacBook Pro, PowerBook, iBook, iPhone, iPod, and more, covering topics from disassemblies, to RAM upgrades, to replacement hard drives.