Learn a cheap and effective way to make sure you pass any test with this easy way to sneak answers into class without getting caught. Taking a simple band-aid and writing the answers on the fluffy, white underside can conceal your notes without drawing suspicion (as most teachers never think to check a wound!) The guide even shows you how to make it look authentic with just a little bit of ketchup. Just make sure not to get caught (especially if you sit right up front)!

In this video, this woman is describing how to eliminate pimples in a clean, healthy and effective way.

Don't freak out when your hair starts to thin, there is help available! Check out this video for information on how to hide that pesky bald spot.

This works well for short hair. First of all you need to have artificial hair extensions of golden color or any other color of your choice. You also need a glue gun and hair clips to hold these extensions to your real hair. You can choose to fix these extensions on the left side of your head, just below the hair. Lift your hair at the left sides, add some glue using the glue gun and place the extension. Now add clips to fix it on your hair. Carefully conceal it below your real hair. Take care...

Spray the Styrofoam ball with a color that adheres to the scheme of the ribbon and ornaments. There will be white space when you make a Christmas ornament tree, and the color on the ball will help to conceal the space.
Learn how to apply a peacock feathers eyeshadow look. You will need Covergirl True Conceal Concealer, Jesse's Girl Sparkle eyeshadow in Black, Jesse's Girl Eye Dust in Gold, Jesse's Girl Eye Dust in White, Jesse's Girl Eye Dust in Purple, Jesse's Girl Eye Dust in Blue, Avon Big Color Eye Pencil Night Glisten, Max Factor Volume Couture Waterproof Mascara in Rich Black, and Maybelline Define-A-Line eyeliner in Ebony Black. Watch this how to video and you can create a peacock feathers eye look.

In order to perform a three color-changing card trick, you will need the following: a deck of cards.

In order to perform the Four Kings magic card trick, you will need to begin with the set up. Remove the four kings for the deck. Place the four kings on top of the deck. When they pick a card, force your king as their card. Make it look like you are pushing their card into the center of the deck, instead, put it at the bottom of the break: i.e. underneath the 3 other kings. Show them the top four cards and show them that one of the cards is theirs, but peel off 7 cards, showing them their kin...

Everyone loves a magic trick, especially when you wow them with a seemingly normal object. In this trick, take a regular coin and make it disappear and move around magically! Soon, you will be the hit of every party!

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Remember when the whoopee cushion was the epitome of a good office prank? Seriously, when was the last time you've actually seen a whoopee cushion? It's a shame when a classic prank fades into the shadows like a fart in a dungeon. These days, office pranks need to be a little more involved—and way louder—like this amazing air-horn chair prank.

When Google introduced the Call Screen feature with the Pixel 3, I had never been more excited to get a Pixel device. This AI feature provided real protection against rising spam and robocalls, which billions of people deal with each year. After a recent update to the feature, you can reduce robocalls and other spam calls to nearly zero.

Meta Company filed suit today against a former employee and his startup DreamWorld USA, Inc. for the misappropriation of trade secrets and confidential information.

Cake decorating is one of those activities that used to leave my hands sticky and my spirits dampened. No matter what I seemed to do, the final result always ended up looking like a preschool art project.

Here is how you can build a frame for your MEGA SOLAR SCORCHER in under an hour, and for less than $8!! This is effectively a 4 foot magnifying lens that concentrates insane amounts of heat from the sun. What would you do with all this free solar power? My design for this custom "Scorcher Frame" is easy to use, and incredibly cheap to make, as you can see in this step-by-step video.

Tomorrow's the 1st of April which means it's the one day of the year you can put aside the daily grind, and go at it Dwight Schrute and Jim Halpert style. Yes, there are easy apps to do your dirty work, but if you're old school and you like to do it the old fashioned way, here are 10 simple pranks for torturing your co-workers.

There is something so satisfying about dipping your spoon into a perfectly smooth slice of cheesecake. There is something a bit less satisfying about it if the top of the cheesecake is cracked and cratered.

Seeing that you probably can't go ten minutes without lying (according to this study), you're probably interested in becoming a better liar. The best way to do so is to learn what makes a bad liar, and then do the opposite.

A deck of cards may be a magician's best way to demonstrate his or her's sleight of hand, but for the prankster, it's the perfect way to deliver a shocking 300 volts of electricity! And that's exactly what I'm going to show you how to do today. Stuart Edge used it in his "Electric Shock Kissing Prank" to show the ladies how a man can really put the sparks in a kiss.

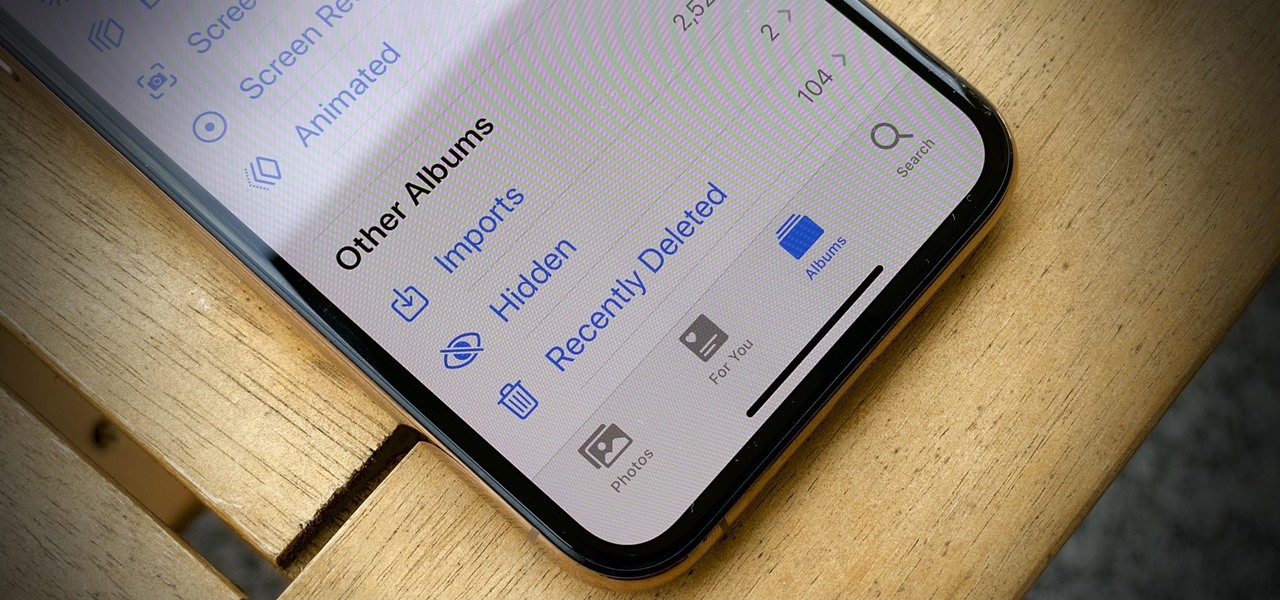
The "Hidden" album on your iPhone has always had one problem — it was never truly hidden. Since iOS 10, when the feature was introduced in the Photos app, any image or video that you conceal in the private folder could be seen by anyone with access to your unlocked device. Finally, that has changed.

In Guardians of the Galaxy Vol. 2, Mantis resides in the shadow of an Ego who considers himself the actual heart of the universe. But when it comes Halloween costumes? Mantis will be the center of attention every time. The internet sure has noticed Mantis, and it's abuzz with debate over who she is. Is she just another iteration of the submissive Asian woman stereotype? Or is her character an empowering representation of empathy and the autism spectrum?

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

You know Moana's a rock-solid pick for Halloween this year. The question is, how far will you go to become Moana? Are you going to just slap on a cream skirt and a red bandeau? Or do you want to go all out and end up with the finished product like YouTuber Gladzy Kei did?

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

The best part about April Fool's Day is that everyone is fair game. Even big tech companies like Google and Twitter get in on the action every year. It encourages even the most uptight, unfunny party-poopers among us to have a little fun driving each other crazy with pranks — even at work.

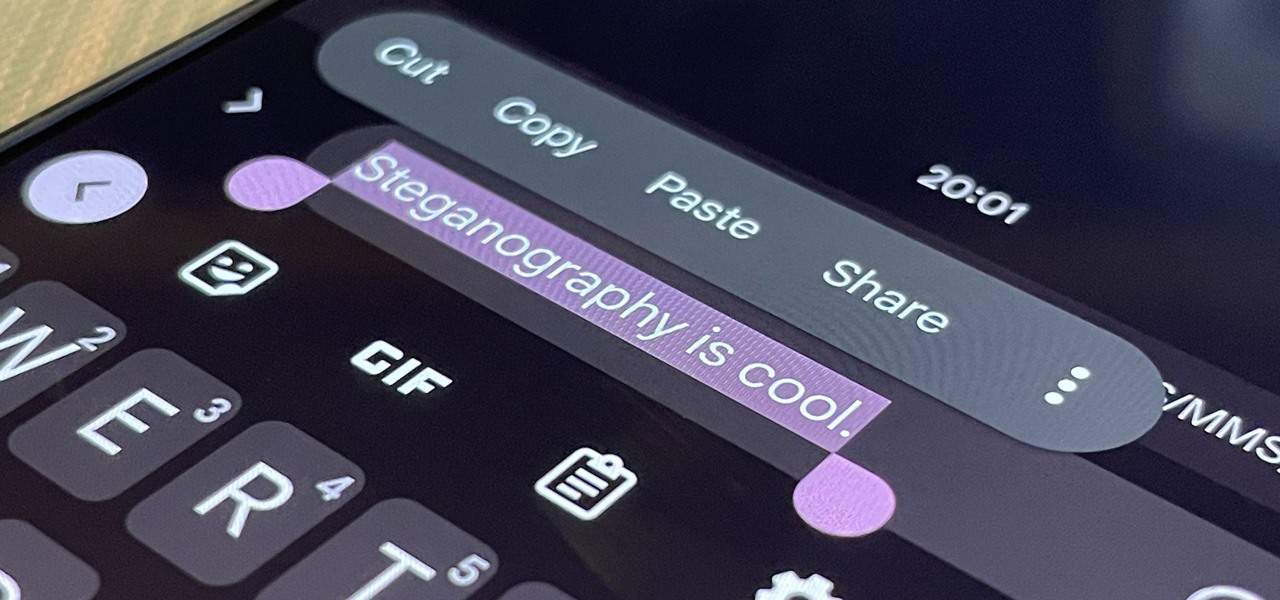
You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Wonder Woman has always been a Halloween and cosplay staple. It's a costume that's both dependable and stylish — just like the Amazon who wears it. This year's reprise with Gal Gadot offers a fresh take on the old standby, with more muted colors, a tougher demeanor, and a decided lack of stars or stripes. Tahnee Harrison from CineFix's DIY Costume Squad has come up with a compromise between the old and new costumes. It's got the cut, styling, and details of Gal Gadot's 2017 costume, but the b...

Kylo Ren, conflicted villain of the new Star Wars trilogy, will surely be a major presence again this Halloween, with The Last Jedi fast approaching. His costume, all black and layered, complete with dark-side helmet and crossguard lightsaber, seems quite perfect for Oct. 31 — as well as your next DIY project.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

With a simple web-based tool, you can hide secret messages for family, friends, and fellow spies inside of plain text communications, and anyone that intercepts the messages will be none the wiser.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

Update: The new Galaxy phones are now official! Check out all the details on the Galaxy S10 and S10+ or the Galaxy S10e.

These days, most images we post online or share with others come from our smartphones. Whenever personal data is in them, such as debit card numbers, addresses, phone numbers, passwords, and other sensitive information, it's easy to jump into your iPhone's markup tools to black out the text before sharing. But a digital marker may not hide everything.

If there's an iOS app you want to hide from your iPhone's home screen, there are a few built-in ways to do so in iOS 14, but there is a clever workaround you can use in older iOS versions. Plus, it also works in iOS 14 as a way to disguise app icons instead of just hiding them, so no app is what it seems.