Looking for a fun way of making a nice little concealed pocket shooter for spit balls, q-tips, the whole shebang? Well check out this awesome video on how to convert a G2 ball point pen into a small pen shooter that you can load smaller ammunition into and fire from to annoy someone, or to use as a back up weapon in office warfare when you run out of nerf ammo!

This video shows how sublimation works. The instructor shows how to mix bubbled water, ice water and dry ice to create dry ice smoke. He is essentially making a hand made fog machine. This task must be done carefully because if the solution is isolated and concealed it will build pressure and possibly explode. Take extreme caution in doing this home experiment. The instructor also shows you how to make music spoons using temperature changes on the metal.

Still wearing those angel wings on your back for Halloween? Then honey, your whole world is about to be turned upside down (in a good way). Take a gander at this Halloween makeup video to see how to paint on an angel wing mask (each eye a wing).

Sometimes it may not be the best idea to apply foundation before going out. It may sweat away, get all over you clothes, or just be uncomfortable on those hot and humid days. This video will show you exactly how to achieve a flawless, concealed look without using any foundations; just moisturizers and powders.

This video discusses Dead Drop Devices and how to use them to transfer messages. The video starts by explaining what Dead Drop Devices are. They are basically common everyday objects that are hollow inside to store a message. The video shows a large lag bolt and a spike that are actually Dead Drops. The head of the dead drop bolt screws off and reveals a hollow cylinder used to store something valuable. The second object is a spike that is supposed to be shoved into the ground so that it will...

This instructional video by ToyotaUSA guides you on how to use the rear cargo area of a 2010 Toyota 4Runner. The 2010 Toyota 4Runner is extremely spacious and the 5 passenger model has a sliding rear cargo deck which can be pulled out as demonstrated by moving the lever and pulling it to one of the two positions (halfway out or fully extended). There is also a concealed storage area between the second row seat and the cargo deck. It also has rear tide outs to secure cargo. The rear hatch has ...

Here is a step by step tutorial video on how to make an origami shuriken. A shuriken is a cool Japanese concealed weapon and is also known as a ninja star. This video is a silent demontration, but there is text to guide through the process of folding your own shuriken.

Blind is a Limbo-like platformer on A10 Games where the player must platform through 2D environment that is largely concealed to them. This video will walk you through all of the game's 21 levels.

Before there was Gray's Anatomy, physicians and medical students used anatomical flap books to explore the inner workings of the human body—a scientific illustrated guide that takes its name from the moveable paper flaps that can be "dissected" to reveal hidden anatomy underneath. Similar to pop-up books, these instructional tools mimic the act of human dissection, allowing doctors and students to study the intricacies of the body normally concealed by flesh.

Leave your geometry teacher speechless when you turn a circle into a square! This very cool magic trick is easier than you would think. With this tutorial, learn how to impress your family and friends, step by step.

The makeup artist Julia presents this tutorial in partnership with VSP vision care in order to demonstrate makeup tips for people wearing glasses or contact lens.

When it comes to your smartphone, you don't have to be a cheater to want a little privacy. I don't even like people playing Temple Run on my mobile because I don't want anyone beating the achievements I've been working on getting myself.

You know that you have the Gmail app on your iPhone. After all, you get Gmail notifications, you see it in the app switcher, it's in the Settings app, and there's an "Open" button in the App Store instead of "Get" or a download icon. But you cannot find the app on your Home Screen. If this situation sounds like something you're dealing with on iOS 14 or iOS 15, there's an easy answer.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

During Huawei's P30 smartphone launch event on Tuesday, the China-based company unveiled a surprise addition to its line-up: smartglasses.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little screwed—both digitally and in real life.

Are you a messy burger eater? Ants and fruit flies invading your home? Hate drinking warm drinks? Find out the quick and easy DIY solutions to these problems with these 10 amazing tips and tricks for the summer.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

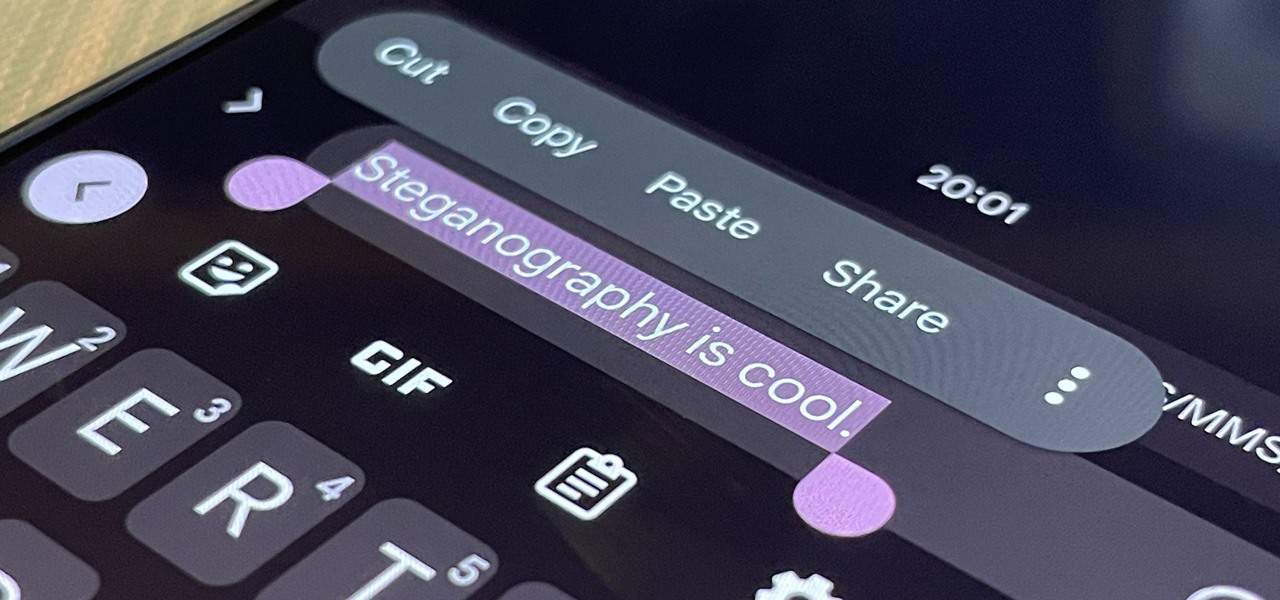
With a simple web-based tool, you can hide secret messages for family, friends, and fellow spies inside of plain text communications, and anyone that intercepts the messages will be none the wiser.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

This tasty treat might stop your heart but it'll seem worth it. There's nothing much better than your favorite candy bar, but trust me there is and favorite candy bar fried. No longer reserved for fairs and carnivals this artery buster can be made right at home.

Fire. It’s everywhere— always has been. From the Ordovician Period where the first fossil record of fire appears to the present day everyday uses of the Holocene. Today, we abundantly create flames (intentionally or unintentionally) in power plants, extractive metallurgy, incendiary bombs, combustion engines, controlled burns, wildfires, fireplaces, campfires, grills, candles, gas stoves and ovens, matches, cigarettes, and the list goes on... Yet with our societies' prodigal use of fire, t...

Synopsis: Tell one guy that a girl that one of the other guys knows just had some sketchy demonic encounter/satanic experience at some Wicca gathering she went to last night while she was trying to get answers from the past. Then say she’s incredibly creeped out right now and is home alone tonight so they are going to seize the opportunity(while she’s still scared) and have him dress up as Satan himself and go to her house late at night and “appear” to her in her bedroom. (Don’t be overly des...

Take the best RPG of all time. Combine with the only instrument with invisible strings. And you have pure elf-worthy magic!

The buttons are mid way up the wall and there is no visible redstone, which adds to the sexiness factor.

Want to keep your money and valuables safe while traveling abroad? Play it safe and outsmart thieves by placing your money, passport, jewelry and other expensive things in unexpected places. Sew a secret inner pocket in your pants, or if that's too much work, try cutting open a tennis ball, using empty film canisters, or simply placing a small amount of money in a spare wallet while your real wallet is more concealed within your luggage or purse.

*****TOON BUILDS***** STARTER GEAR FOR YOUR TOON 150+ OF EACH

Lisa Eldridge is one of the most preeminent makeup artists in the fashion editorial space today, working with nearly every A-list female in Hollywood. Her blog is full of interesting tutorials and articles, and Eldridge recently posted a fascinating interview with Madeleine Marsh, historian and author of Compacts and Cosmetics: Beauty from Victorian Times to the Present Day.

If you've ever had to call a large communications company with a customer service issue, you've most likely experienced the hopelessly not-at-all helpful operator from hell. Thanks to a program on VRT Belgium, you can now experience a small sense of vengeance for tortured customers everywhere.

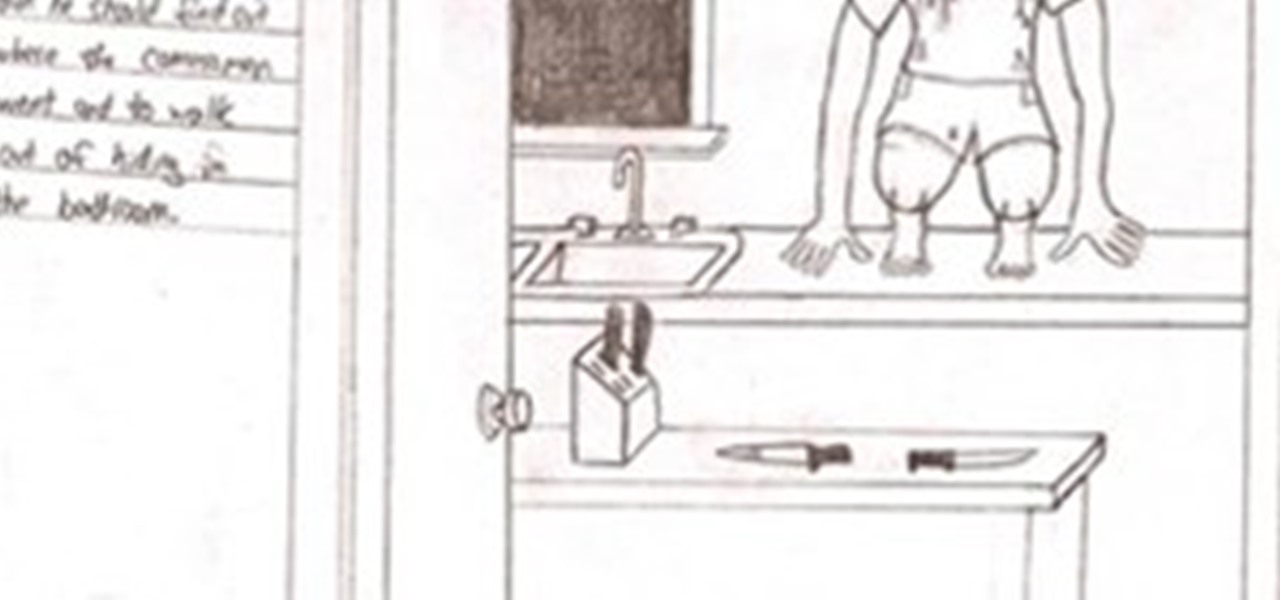
Below, learn to detect the markings of a Satanic cult member. Hard to believe, but yes, this is a bonafide HowTo (truly, it's on the FBI's official list of resources on “Beheadings & Ritual Murders").

When you are in Rome, do as the Romans do... avoid carrying your wallet in the back pocket of your jeans. But no matter what city or country you are in, there are several easy precautions you can take to keep yourself as pickpocket-proof as possible so that your amazing travel memories won't be sullied by the experience of having your camera or passport stolen.

Now we're getting to the kids who actually know what's going on. You're more likely to get enthusiasm and dare I say focus from grade school and middle school kids. Here's the lowdown:

The medical field has known for some time now that negative pressure (re: suction) can drastically speed up wound recovery time. However, the machines that are currently available are quite expensive, and not an option for third world countries. Enter MIT student Danielle Zurovcik. The doctoral student has created a hand-powered suction-healing system that could completely revolutionize first aid in developing nations. Her device goes for only 3 bucks a pop.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Oh, the power of redstone! But, what good is any technology if it can't be harnessed for killing? Here's a redstone build for the mad scientist in each of us.

Oh, teenagers. Maybe you would be better off planning a scavenger hunt for the screaming toddlers. Just kidding! Despite the mood swings, teens will enjoy a scavenger hunt more than younger kids. Some things to keep in mind, though:

Artist Austin Houldsworth of the UK has come up with a device that drastically speeds up the process of fossilisation. Entitled Two Million & 1AD, Houldsworth is capable of creating a fossil in a few months (which otherwise might require thousands of years). Houldsworth is currently experimenting with objects such as a pineapple and phesant, but ultimately hopes to fossilize a human. Houldsworth proposes: