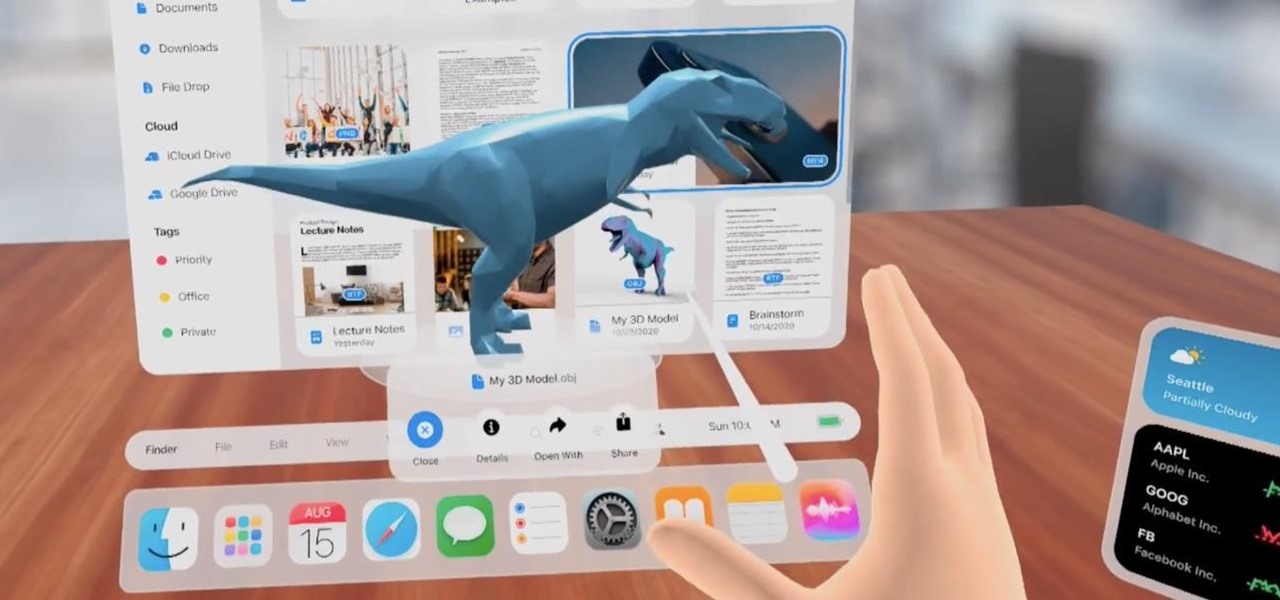
The list of HoloLens applications continues to grow as more companies discover ways to enhance their operations using augmented reality. Air New Zealand is the latest to show interest in the technology, demonstrating their vision for AR in a new concept video.

Augmented reality upstart DAQRI announced today that it has strengthened their in-house talent by recruiting renowned physicist Seamus Blackley and acquiring a team of 15 engineers and scientists from Heat Engine, LLC.

If you've played the game Portal by Valve before, you've most likely popped one portal onto the ceiling and another directly below it on the floor, dropped your Companion Cube in, and then watched it fall forever. Well, now it has been done in real life, in an actual hallway, not in a rendered world.

In addition to trying to give Pokémon a life on the HoloLens, Sky Zhou, a founding member of mixed reality studio Matrix Inception, won Microsoft's Actiongram Fantasy Contest Quest last month for his video concept on slaying dragons. But fantastical creatures aren't the only thing Sky can whip up on the HoloLens.

Here at NextReality, we talk a lot about the many different ways of controlling holograms in the HoloLens and other augmented and mixed reality devices; New and creative ways are coming more and more every day. Most recently is something called the HoloSuit. In the 25-second clip below, you can see a woman moving the arm of a jacket which in turn moves a 3D model of Darth Vader on the screen. It's a simple idea with big potential.

Google has been working on its voice recognition technology ever since the days when you had to call a phone number with a Silicon Valley area code to dictate your query. As you can imagine, things have come a long way in the decade or so that has passed, to the point where we talk to our phones as if they were a person nowadays.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

In this video series, our expert Terry Leafty will teach you about safety equipment including hoods, body protection, sleeves, and welding hats before showing you the different types of welders.

Cybersecurity is an industry that isn't going anywhere. After the mass move to online work, the need for more cybersecurity professionals skyrocketed. That demand isn't going away because more and more industries are keeping online and cloud services going for their workers.

The focus on augmented reality over at Apple is, so far, restricted to the iPhone and the iPad. But if some of the most reliable analysts in the business are to be believed, we'll probably see some kind of AR or VR wearable from the company later this year.

Snapchat popularized personalized stickers for social media and messaging with Bitmoji, followed by walled-garden versions from Apple with Memojis and Samsung with AR Emojis. Even Google has gotten into the game, integrating an emoji generator for Gboard.

Over the last few years, the only thing teased by Magic Leap more than the Magic Leap One itself has been the company's flagship gaming title Dr. Grordbort's Invaders. The game, developed by New Zealand studio Weta Workshop, finally got its debut last week during the L.E.A.P. conference in Los Angeles.

After the first image leaked of the upcoming successor to the Razer Phone, many were taken aback by its design, specifically how familiar it was. Last year's Razer already stood out with its boxy design and large bezels, and many thought the successor would change this. It didn't. But what if the reason for the familiar form factor is a project they teased earlier in the year?

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

Something that always brings a tear to my eye is uninspired Instagram stories. When you have a bunch of like-minded friends, you end up with like-minded stories. While it may seem difficult to stand out, stickers were designed so that you can differentiate yourself from other users — and knowing everything there is to know about Instagram stickers will make you a sticker master.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

No matter what your holiday preference, you're probably aware that Christmas is now just days away. By now, you've already decked your halls with boughs of holly (either physically or virtually), thanks to our last holiday app roundup.

There's no doubt you've heard the old saying, "When life gives you lemons, make lemonade." The phrase was penned in an obituary to a dwarf actor in 1915 by an anarchist named Elbert Hubbard, who lost his life five months later aboard the RMS Lusitania when it was torpedoed by a German submarine.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also lots of thanks to DrapsTV. They have helped me a lot with Python and making awesome programs. The video is here:

There's only three weeks left until the spookiest holiday of the year, which means stores and costume shops everywhere are bringing out their Halloween inventory full force. So now's a good time to start prepping your Halloween costume—because you really don't want to do it last-minute again, do you?

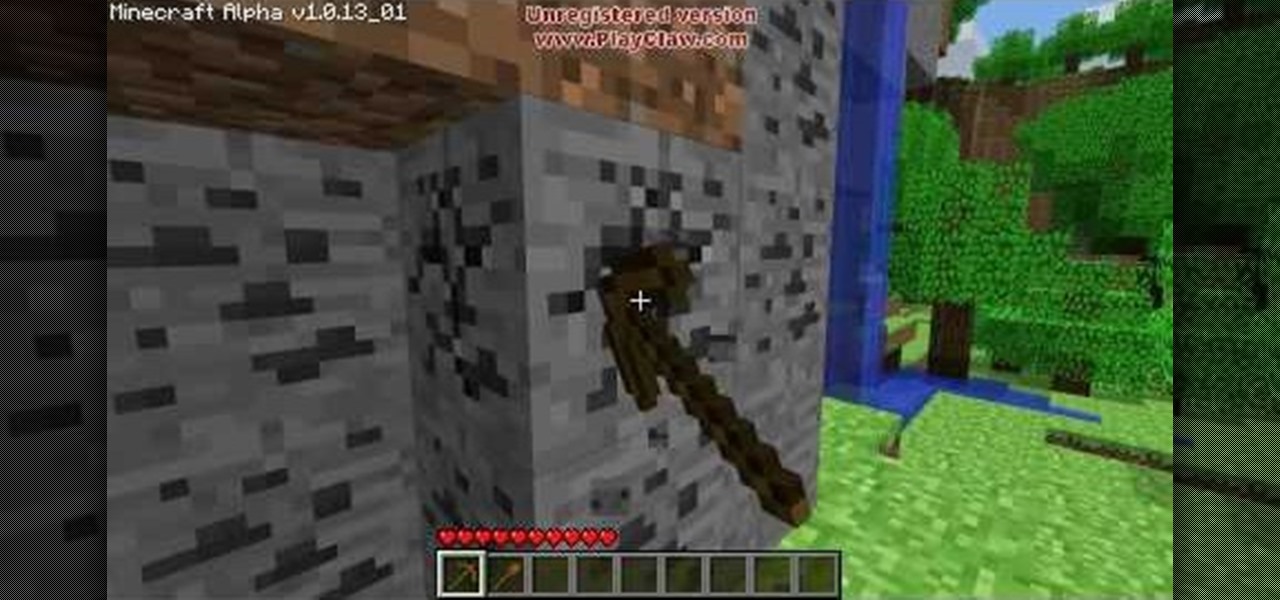
Minecraft is a game that snuck up on the gaming community and set a wild fire bigger than the ones in California! Even though it's not even done and still in Alpha phase, reviewers are already reviewing it, and people are jumping on board. The game itself is based around a basic concept: survive, craft, build, conquer. You play the only man in the world who starts with nothing, during the day, it's safe and you can mine and harvest material, but at night, creatures come out, including Zombies...

Welcome to Google's Python Class – a seven-segment, two-part free virtual class for people with a little bit of programming experience who want to learn Python. The class includes written materials, lecture videos, and lots of code exercises to practice Python coding. The first exercises work on basic Python concepts like strings and lists, building up to the later exercises which are full programs dealing with text files, processes, and http connections. The class is geared for people who ha...

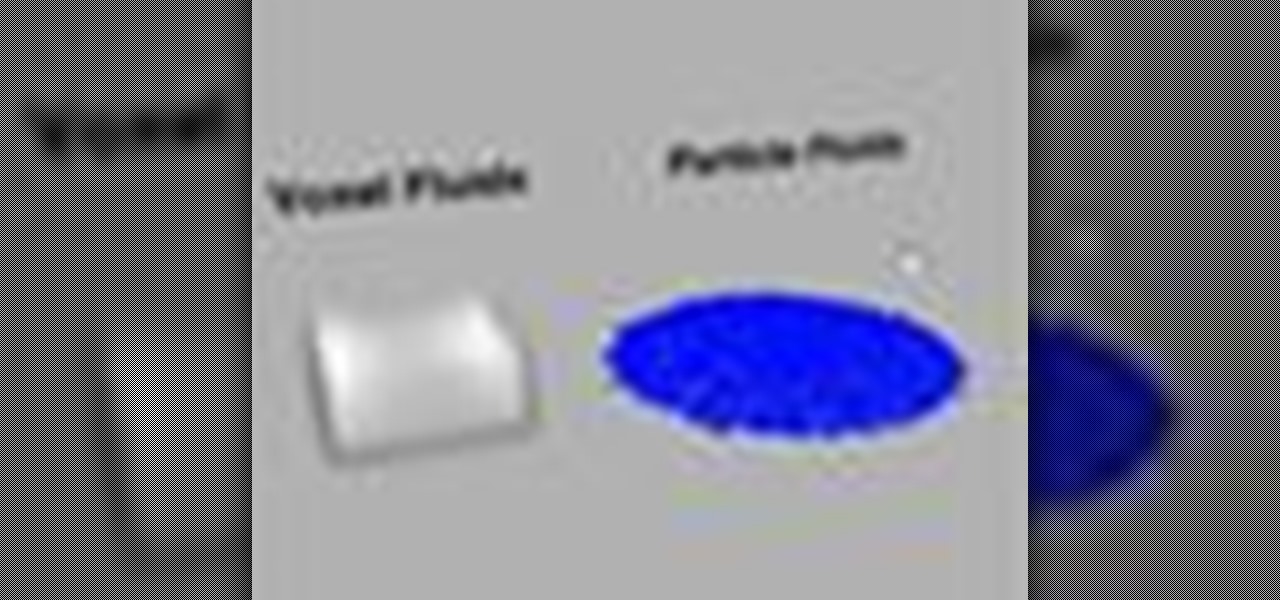
Created by Houdini Product Specialist Stephen Tucker, this crash course series focuses on the concept of fluid dynamics and how they work within Houdini. These videos on Voxel Fluids should help any artist get up in running with the foundation tools available for creating fluid effects in Houdini 9.5. Topics range from how to create a container to how to gain access to fluid attributes for shading, and even passing data from volumes to particles.

Enter the game and select Stage 1. Click on the rock above you to make a snake come out. Click on the cactus and drop it on the snake to make a hat. Stage 2: Click and drag the trash to the right and click on the lamp. Click on the taxi that will appear to pass Stage 2. Stage 3: Click and drag the brick to the glass above to break it, open the door, and turn on the lamp. Grab the antenna and put it in the black hole on the edge of the building. Stage 4: Click on the boat and then click on you...

Folding paper into shapes is fun. Folding paper into a toy that you an actually use is even better! Making a paper boat is not only a great rainy day activity but works just as well on a beautiful summer's day.

This video shows you how to turn a 5" crochet headband into a beanie hat. #1 Gather your supplies-embroidery floss, 5 1/2" crochet headband, needle and scissors.

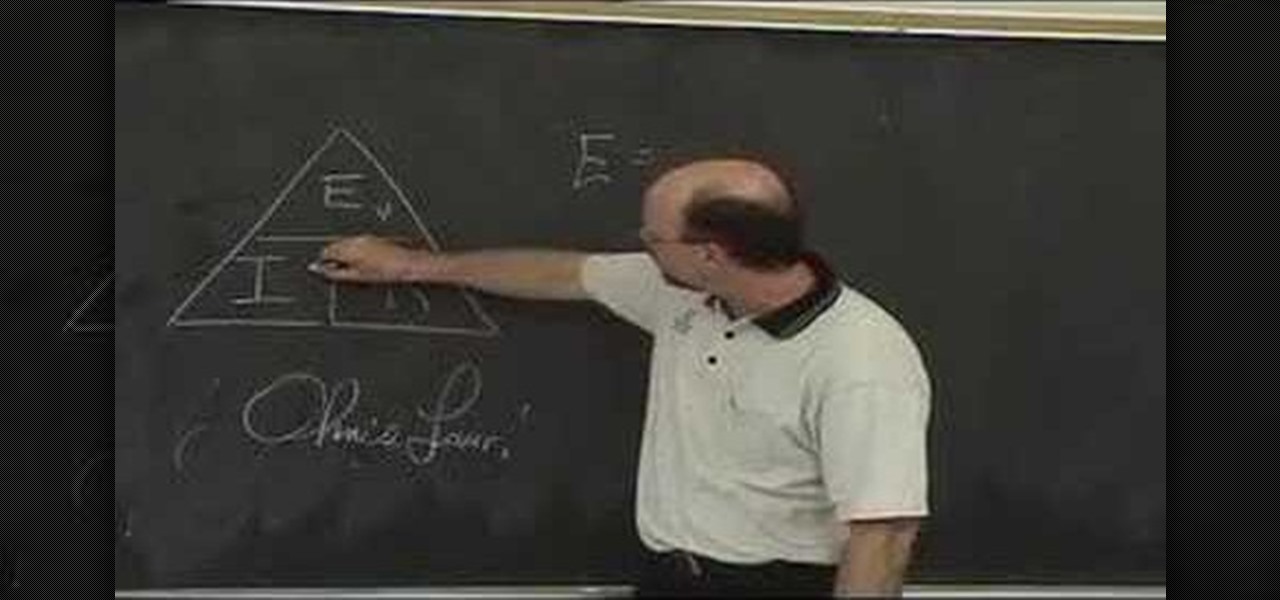
Watch this educational how to video to review Ohm's Law. This math and physics concept is derived from electric motive forces, intensity of current flow and resistance values of conductor. Watch and learn more about Ohm's Law.

Ever a hacker can have their own business that goes beyond cashing in on profitable bug bounties. With the right skill set and certifications, an ethical hacker could build a cybersecurity firm, become a penetration testing for hire, or even just consult on preventive measures to defend against black hats. But learning how to start and grow a business is rarely easy.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

Unless you've been totally off the grid, there's a good chance you're aware that the Disney Plus streaming video service launched this week. And, if you're on this site, you're likely salivating over the new Star Wars series, The Mandalorian.

For Snapchat users wondering if that selfie is ready to send to their crush, independent Lens Studio creator Andrew Mendez created a handy tool called the Smile Rater.