Ever drive a friend's car? Maybe a rental? Then you've probably found yourself in a very frustrating situation when you realize you need some gas. Heck, it probably even happens to you in your own car sometimes.

What's the meaning of life? That's the age-old question; but can it ever really be answered? I mean, isn't life just a big game anyway? Perhaps, a game of inches?

This is an awesome little science trick that has to be seen to be believed. Simply by emptying a bottle of "supercooled" water into a glass, you can watch it turn into ice right as your pour! It's no magic trick or chemical craziness—it's normal water and you can try it yourself right in your own home.

Thanks to everyone who submitted ideas in last month's Mad Science contest. The question called for your best idea for using Sugru, a temporarily malleable silicone modeling clay that self cures for a soft-touch permanent bond. It's a marvelous product for at-home quick fixes and for even making some cool DIY bumpers and grips for your electronics. William scoured through all of the comments and chose the two winners he felt best deserved a pack of Sugru.

SiFu Allan Lee explains coverage and uses a Pak Sau drill to illustrate the concept

The rock drum beat is an intricate drum pattern that incorporates the hi-hat, snare and bass drum. Learn some tips for playing various patterns of the rock drum beat from an experienced drumming instructor in this free music lesson video series.

Installing clutch shoes is very simple. What you need are the clutch shoes, clutch shoe installation/removal tool which costs about $5 or a flat tip screwdriver. First, line up the clutch shoe. Plastic shoes wear out faster. Aluminum last longer. With the screwdriver method you bend the spring out. Take the bent out spring and push it down. Push it straight down. This is not the authors favorite method. Using the clutch shoe installation tool, simply push the spring out and push straight down...

In this how to video, you will be introduced to the concept of a movable NU in Greek as well as have the Greek accent marks summarized. The movable NU is used at the end of Greek texts in the present active indicative third person plural form. The movable NU is comparable to the English article "a" or "an". This lesson in perfect for those who wish to study this ancient language of Greece. Watch this language tutorial and you will be speaking biblical Greek in no time.

While many of you were off surfing and lounging on some sandy beach or trying to figure out how to balance work with sky-high summer temperatures, I've been talking to all the companies that make augmented reality what it is today.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Michael Jackson, the King of Pop, has changed the way audiophiles listen and create music. He's a very influential part of everyone, whether they know it or not. Pay tribute to the King of Pop by drawing a skillful sketch of him and his signature dance. DragoArt has this video tutorial on how to draw a Michael Jackson sketch. Get more detailed instructions on the step-by-step cartoon drawing here.

The swing groove drum beat is an intricate drum pattern that combines the hi-hat, snare and kick drum. Learn to play several variations of the swing groove drum pattern by displacing eighth notes with expert tips in this free drumming video series.

The swing drum beat pattern is an intricate jazz rhythm that incorporates the snare, hi-hat and kick drum. Learn to play several variations of the swing drum beat with expert tips in this free drumming video series.

In this video series, learn how to sequence Reggaeton beats on a Korg Triton keyboard. Our synth expert, Ryan Larson, will explain the basic sequencing process step by step, including how to use samples, setup and create loops, choose and add effects to tracks, record instruments like a thumping bass drum, crisp hi hat cymbals, tight snare hits, and other percussion, add bass lines, keyboard melodies and horns, how to mix tracks, and even how to play the sequencer for a live performance.

Our holiday expert Matt Cail will show you how to make your very own elf costume, starting with the undergarments and tights, then on to the shoes, gloves and familiar elf hat. He also includes tips for elf makeup, ideas for the kind of presents elves like to give, and even tells you how elves are supposed to behave.

In this series, Matt Cail will show you how to select a dress and hat, how to improve your costume with leggings and props, and how to apply makeup to the eyes, nose, chin, and neck to create your spooky witch.

Flower arrangements bring color, life and mood to everyday life or a special occasion and the best part is you can make these bouquets yourself. The flower god will show you some of the ideas and an example using sunflowers for balanced table centerpieces. You will want to choose a main flower and several supporting pieces of foliage and flowers to increase depth and interest to your spread. The meaning concept is balance and accent. This video shows a minimalist, three vase approach for a ch...

You start the Swedish back massage first by putting lotion in your hands to warm it. You first use long fleeting strokes and work your way into shorter spinal column strokes (remembering of course to keep even pressure). You then move to the petrissage stroke running your hands smoothly interchanging the openness of your fingers alternately all across the back. You then go back to work on the trapezes remembering to push outward from the spinal column. The video also brings up the concept of ...

In this photoshop tutorial you will see how to create a crumbled stain cloth look from scratch. This is a very simple and easy concept. Watch and learn how to make your own satin material effects in Photoshop.

This how-to video demonstrates how to weave the ends when you are crocheting. The basic concept of weaving ends is that you weave in the ends into the crochet project to make it look neater. All you need to practice this technique is a metal needle. Watch and learn.

Slides, slurs and legatos are all very similar concepts with slight differences and different notations . In this music theory how to video, learn the difference between slides, slurs and legatos.

Learn what common time or 4/4 time is and how you can use it with this how to video. This music theory tutorial will help you understand the concept of time signatures and counting rhythm.

In this lesson we will learn about one of the most important concepts in algebra SQUARE ROOTS. The square root of a number m is another number n that satisfies the following formula: m = n x n. You can also say that m is the square of n. The opposite of squaring a number is finding its square root. You can use the radical symbol to indicate that the square root of m is n:

Mark Wenzel pioneered the concept of mime performances at theme parks, becoming the resident mime at Sea World of San Diego, where he entertained more than a million visitors a year for eight years. Now he trains mimes for all of Sea World's aquatic parks. He shows you some practice exercises in this video series.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

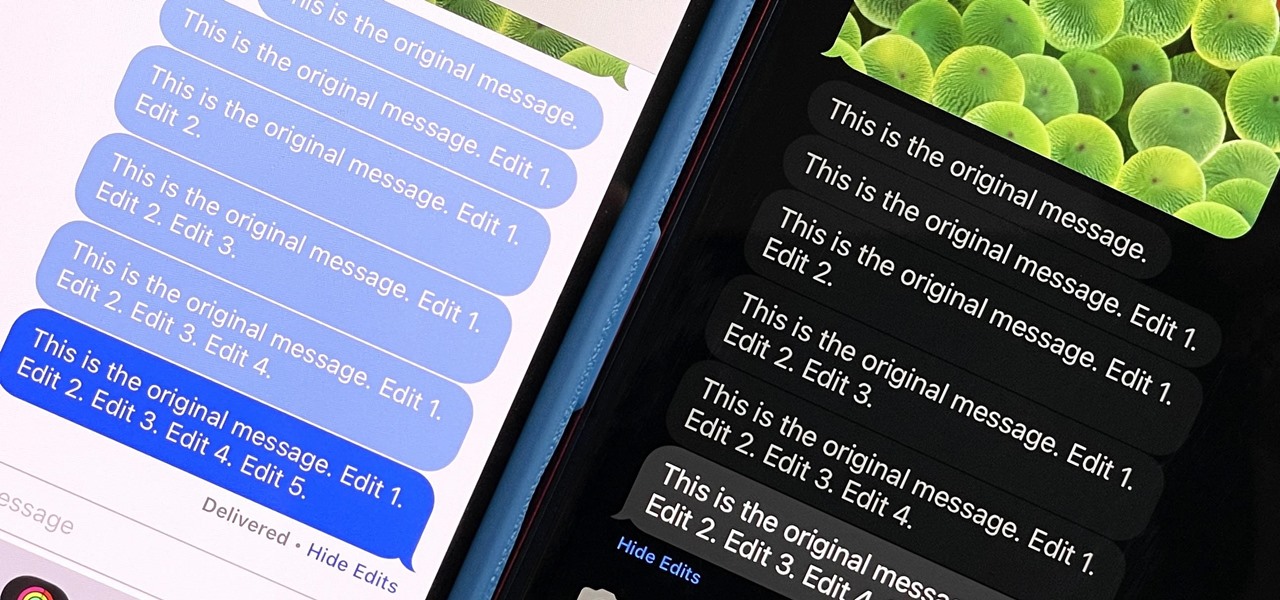
Apple's controversial iMessage-editing feature in iOS 16, iPadOS 16, and macOS 13 Ventura is now less likely to be abused by malicious users.

As if answering Apple's major iPhone event on Tuesday, Chinese mobile giant Xiaomi held its own product launch event the following day.

Like its predecessors WandaVision and Falcon and the Winter Soldier, Marvel's latest series for Disney Plus, Loki, has its own augmented reality experience.

After introducing a pair of new Spark AR capabilities last week, Facebook had one more trick up its sleeve to unveil at its virtual F8 Refresh developer conference.

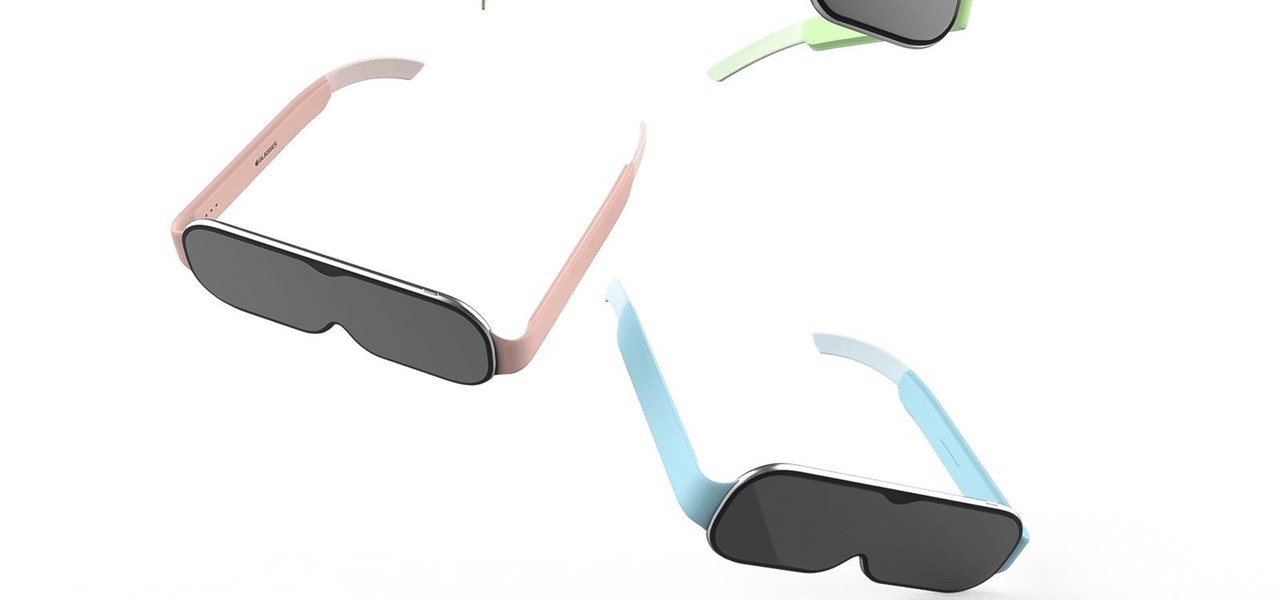
The progress Tooz has been making in the smartglasses space has been mostly kept under wraps, but the company is slowly giving us a deeper look at what it has in store for smartglasses wearers.

The COVID-19 pandemic has increased the demand for virtual and remote collaboration, and Microsoft has a solution that may serve as the catalyst for more such apps for augmented and virtual reality in the near future.

Ethical hacking is a useful skill that can make you stand out in the field of cybersecurity. Whether you're just entering the field or are already established and are looking to stay current, learning the fundamentals of the white hat is an essential skill for your professional development.

Rumors of Apple developing smartglasses have persisted as prophecy since 2016, but the arrival of what many herald as the savior of augmented reality have eluded even Nostradamus himself.

If you have information technology or computer science aspirations — even white hat hacking — then Python is a programming language you absolutely have to be familiar with. According to a recent survey of industry experts, Python is the fastest-growing language in the developer field. It's also one of the most sought-after skill sets among employers and is responsible for some of the best hacking tools.

If you're interested in joining the increasingly popular and lucrative world of ethical or "white hat" hacking, you're far from alone. More and more coding and programming pros are turning to this field thanks to the high pay, countless opportunities, and exciting work environment.

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

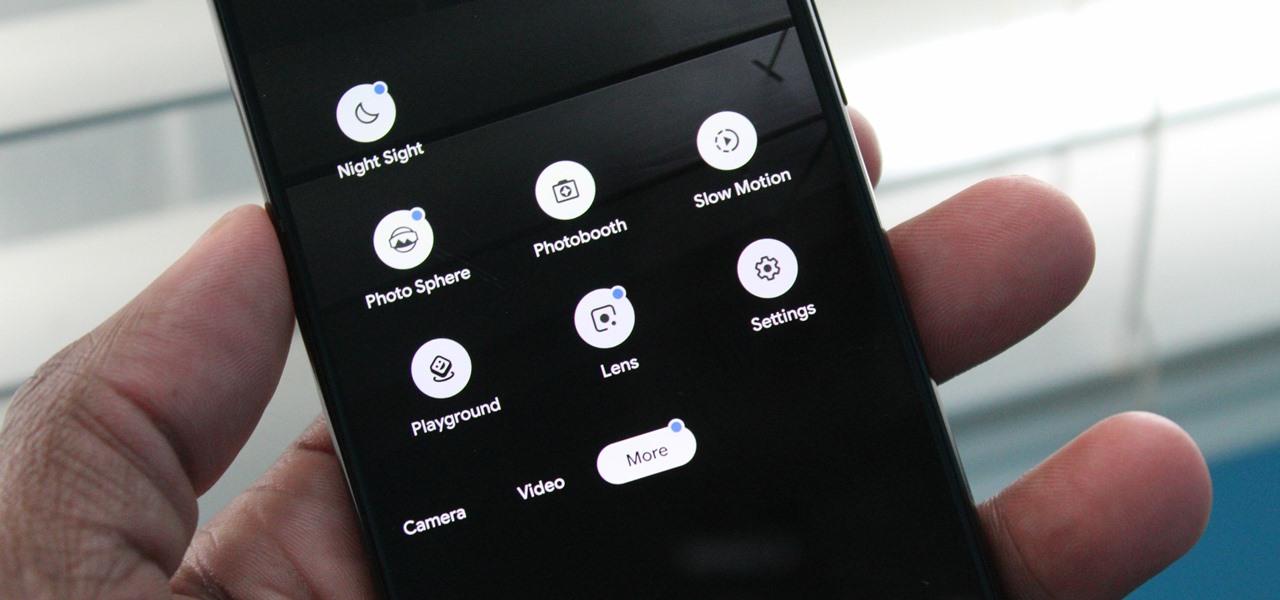
Nowadays, our phones are capable of just more than 30 fps video. Phones like the Galaxy S10 can shoot 4K at 60 fps, even on the front camera. Slow motion functionality has recently started to appear on more and more devices — but as you may have noticed, the quality of the feature differs from phone to phone.

What does mainstream augmented reality look like? I'm not talking about the stuff you see in concept videos and science fiction films. No. What does it really look like?