Interested in creating your own dynamic, web-based applications using Microsoft Visual Studio? This guide will introduce you to the fundamental concepts that will help you understand how to create web applications and dynamic websites with the Visual Studio Express tools. Take a look! Create applications with Microsoft Visual Studio.

This hour-long hacking tutorial looks at the Nmap security scanner. In particular, this Nmap tutorial looks at port scanning concepts, TCP three way handshake, stealth scans, idle scans, bounce scans, version detection, OS detection, NSE/LUA scripting and firewall logs. To get started using Nmap, watch this video tutorial. Use the Nmap security tool.

In this After Effects tutorial, Creative Cow leader Aharon Rabinowitz adds to the concepts he covered in his tutorial Straight Vs. Premultiplied and explains how to use the remove color matting effect to fix a bad composite in After Effects. Use the remove color matting effect in After Effects.

An arch is a structure commonly used in bridges and buildings. This video presents examples of the arch as a structural unit and introduces the concepts of compression and tension. Provides support for the structures and mechanism unit of grade 6 to 8 science programs. Understand arches.

This video covers key concepts and methods for optimizing animations. You learn how and when to cache bitmaps, depending on the construction of the FLA file. You also learn how to organize ActionScript code in your document. Optimize animations and FLA files using Flash CS3 Pro.

This video shows you how to slice a button for a website using 9-slice scaling and then using 3-slice scaling. Scaling is done the same way in Fireworks and in Illustrator CS3, so the concepts done here in Fireworks, are the same in Illustrator. Knowing how to use these tools will make creating rich symbols much easier. Use 9-slice and 3-slice scaling in Fireworks.

Check out this instructional cycling video that explains aerodynamic concepts in bicycle fit and wheels to go faster. The bike fitters at Fit Werx talk about all the components of a triathlon bike fit and how it relates to aerodynamics and the individual. This cycling tutorial video covers the following topics to help you pedal faster on a bike:

This video shows you how to use Script Assist to add ActionScript 3.0 to your FLA file. You learn about some of the core ActionScript concepts, such as events, functions, properties, and listeners, while you add code for a button. The button you create plays a movie clip after you finish adding the code and compile the interactive SWF file. Use Script Assist to add interactivity in Flash CS3.

Call Your State's Nurse Aide Registries for School Inquiries

There are endless possibilities for eReaders, and lots of amazing things are already happening. But wow-worthy visual tricks aside, how can technology really change the way we consume books? In the video below design company IDEO presents three separate concepts for virtual consumption: Nelson, Coupland and Alice. IDEO groups their virtual experiences into three separate concepts: Nelson, Coupland and Alice. Core77 breaks down each concept:

These guys always make cool things, and when you give them a stack of PVC pipe, it is no exception. There's a rough how-to here that shows concepts without walking you through the actual projects they made. Very cool stuff.

This project is intended to reuse PVC that makes up the images on billboards and make them into houses for disaster and poverty stricken people. While the images are definitely cg mockups, the concept is awesome. I've personally been working on disaster relief shelters, but my concepts all involve using fresh PVC pipe. These guys have taken it a step further by taking vinyl sign material that is headed for landfills and recycling it into homes.

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, about anything you feel like sharing that is ...

Icelandic artist Olafur Eliasson totally inspires us here at Wonderhowto. His waterfall installations on the Hudson River. His incredible sun exhibit at the Tate in London. His concepts and execution are dazzling. Plus he has Taschen book that weighs a frickin ton. (Yes. The tonnage does translate to respect.)

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

It's remarkable that a gaming device (from Microsoft, no less) designed for geeky gamers has incited broad innovation in medicine and robotics. But that Kinect has captured the imagination of hackers-with-MBAs-in-mind is downright amazing.
Keyword Research Tool. This tool provides you with the ability to directly query the Google keyword databases and truck load of choices of keywords to use in your campaigns. With this keyword tool you are able to create, manage your keyword list and integrate with other tools like competition spy and list builder.

PC Gamer represents all that was awesome about games journalism in the '90s, now sadly diminished. Brilliant, funny, full of integrity, and solid print sales were always present, and with the tragic exception of the latter, still are. Video game magazines were hit harder than nearly any other magazine vertical when the internet began its uncoordinated, but inevitable assault on print media. Magazines are now struggling to find their place in a world filled with more competitors than paying cu...
Oh, yeah. I was a skeptic, too. A few things are worth noting, though. 1) This stuff is cheap. You can get started on a project for very little money. Even advanced fabrication tools are reasonably priced.

I was going to update the first list of 15 Brilliant Google+ Female Photographers to Circle, but then I kept coming across so many amazing women that I decided to create another post highlighting their work. I received many great suggestions from +Kelli Seeger Kim (who takes some beautiful pictures herself), +Suzanne Haggerty, Google+ Photos Community Manager +Brian Rose, and many others.

Henry Goodelman we commend you, sir. You have stunned and baffled us ... more than any of the other 1000+ submitters to the Jackass 3D Prank Contest.

Texas based artist Shawn Smith brings the digital world to reality with his woodcut pixelated sculptures. The combination of a traditional material (wood) with a contemporary concept results in surprisingly fresh work. Plus, the craftsmanship appears to be impeccable. Check out his artist statement below.

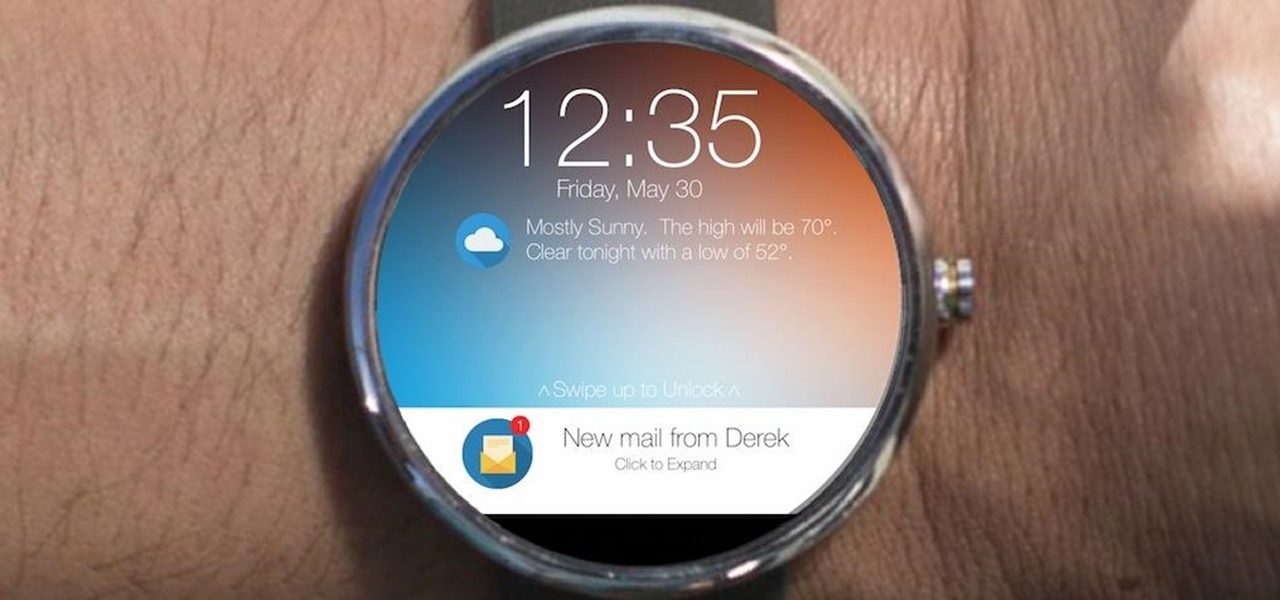
With the release date of its round-faced smartwatch drawing near, Motorola is calling on the public to help design clock faces for its new Android Wear device.

In this article, I'll show you how to make a high-powered, long-range, air-powered rocket gun. This launcher is based on a sprinkler valve, a modified propane tank, and a few other components. Though not hard to make, this device is VERY dangerous! The rocket can seriously harm, if not kill any living thing it's shot at. Here's a video of it in action, quite an accurate shot by my friend Chris... Parts

Note: The article assumes that the reader has a fundamental understanding of at least one other programming language and Perl. This is intended serve as a quick reference for Perl's input/output of data to databases.

Another week has passed on the online battlefield as the CISPA legislation continues to grind away at our freedom. Here at Null Byte, we try to keep our community informed and knowledgeable at the same time—and that means creating content for them to learn from.

Last time, we looked at archaic cryptography, so you should have a basic understanding of some of the concepts and terminology you'll need. Now, we'll discuss one of the most important advances in computer security in the 20th century—public key cryptography.

Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each server will have numerous known security holes, but until then, let's get back to the regular weekly coding sessions and realistic hacking missions on HackThisSite.

Lost the product key for your game? If you have to reinstall the game and don't have that key anymore, you're out of luck, especially if you didn't "buy" the game. But never be in fear of losing product keys again with today's Null Byte, where we'll be practicing a little bit of mind-kung fu.

We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But for now, back to the normal flow of things...

Lock picking is defined by locksmiths as "the art of opening a lock without the key". There's many ways to accomplish this, but I'm specifically interested in using a lock pick set. Since locks vary in shapes and size, it's better to stick with just one kind of lock at first. Most locks are based on fairly similar concepts, so sharing methods across locks is possible.

We're aiming for this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with, we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But, for now, back to the normal flow of things...

The community tore up the first realistic mission last week. You've applied the techniques learned in the basic missions to a real scenario, so I'm pretty content. The realistic missions are where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, f...

Following the first part in this series on advanced cracking techniques, we are going to go over how we can intelligently crack passwords using the old-fashioned bruteforce method. These unique cracking techniques aren't widely used, because most crackers are Script Kiddies who have no idea what the concepts are behind cracking passwords, thus, word won't get around too quickly.

It has been suggested that about 150 million internet users will be affected by today's blackout of Wikipedia in protest of SOPA and PIPA. If you don't know what those are, go here and read up on it, and then take action yourself! After you've contacted your Representatives about these bills, you'll probably still need to get some work done today using Wikipedia's English-language site.

Last week I reviewed Kinotopic, the iPhone app that lets you easily create cinemagraphs. While I loved the result, I found the app hugely flawed. Kinotopic forced you to use a Facebook log-in, and didn't store the finished video on your phone itself. Instead, you had to visit the Kinotopic website to see your cinemagraphs or link to your Kinotopic page using Twitter, Facebook or Tumblr.

Community byters, it's time to get serious. We are finally moving on to the realistic missions in HackThisSite. This is where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials...