Welcome to the 10th Community Byte session for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Null Byte is looking for forum moderators! Welcome to the ninth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the eighth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the seventh Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the sixth Community Byte for coding in Python and beating the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the fifth Community Byte for coding in Python and beating the challenges given to us from HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmers to aspiring hackers—even people that are nearly computer illiterate.

West LA Seido Karate-do embeds its personal protection program into its on-going classes. Private instruction in this aspect of Seido can also be arranged with Kyoshi on an individual basis.

Ever wanted to display text in Minecraft? It's actually not overly difficult. In this tutorial, I will endeavor to guide you through the process between storing and displaying text from memory. To do this, we will examine two different methods of displaying and storing text in memory.

Yesterday, Mojang announced their next video game project 0x10c, and the response has been tremendous. Discussions have covered everything from the math mystery over the game's name, to creating projects that interpret the assembly instruction code the in-game computers use (more on that later), to the debate over why a monthly fee would be required to play online in the "multiverse". To answer that last one, Mojang wants to run everyone's virtual computers in their cloud, even if the user is...

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.
Does this video prove that otherworldly intelligent life has visited Earth? No. It does not prove anything other than there are designs ‘etched’ onto the surface of a field. Does the video immediately above prove that otherworldly intelligent life hasn’t visited Earth? Yeah, you saw it coming; no, it proves nothing more than humans are able to ‘etch’ designs in a field of grain.

This is the third part of my electromagnetic pulse series (see Part One and Part Two). By now, I've covered the hardware and general concept of electromagnetic pulse generators, but how exactly do they disable electronics? How can an invisible field of energy have such a catastrophic effect on computers, cell phones, and most any other electronics? I'll be answering all these questions in part three of Making Electromagnetic Weapons.

You're never going to see a project from me that involves straight pipe. You would have when I was a kid, but after too many years in the construction industry, I need to see a good finish. If the project doesn't look slick, I don't want to say I did it.

Two new and radically different ARGs (Alternate Reality Games) have burst into the news in the last week, and illustrate the very best of an innovative phenomenon: the commercial tie-in ARG, and the public service ARG.

It was brought up a while back in a Community Call to Arms that *math* is handy for encryption (and let's face it, everything) so let us go over things you just have to know. "In its simplest meaning in mathematics and logic, an operation is an action or procedure which produces a new value from one or more input values."[source]

Imagine you're in Paris and you need to get to Versailles. Looking around for directions, you come to a cold realization—you do not speak a lick of French! How are you going to get to Versailles and what happens if there is a detour? It will be a difficult struggle, and you'd probably get lost and eventually fail. This is why it's important to know some of the country's language before taking that trip in the first place.

Culinary collective Studiofeast is known for thinking outside the box, especially when it comes to food. They've hosted inventive and spectacular events like the L Train Lunch, where a high-end meal was served to guests on a moving train, and the Datalicious Last Supper, where results from a survey of people's desired "last meals" informed the menu.

Who could resist a retro SCRABBLE board game for two bucks? Suereal definitely couldn't, especially with the challenge of totally revamping a board game into something genuine and creative. Craftster's Craft Challenge #51 last June was meant to bring life back to an old board game with the following expectations:

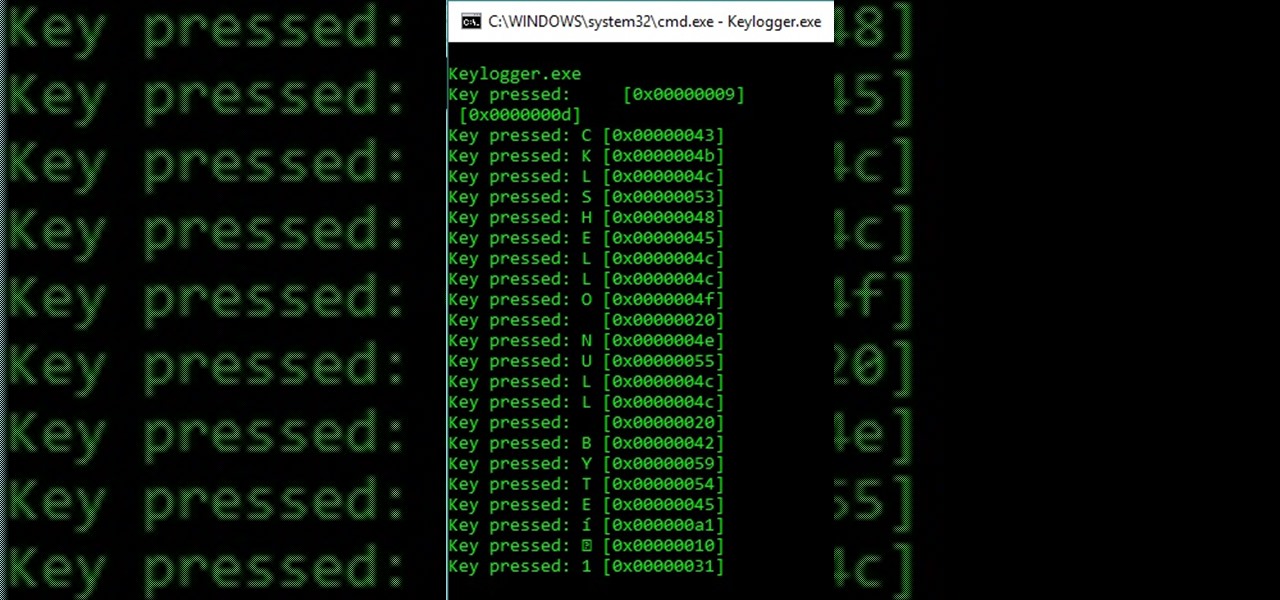
Yo yo yo, what's goin' on my devilish fiends? Have you come here to learn how to make a keylogger for malicious intent? You sly fox! But in all seriousness, this article will cover quite a simple method for creating the most basic of Windows keyloggers. You're in for a surprise! Let's dive right in!

Henry Goodelman we commend you, sir. You have stunned and baffled us ... more than any of the other 1000+ submitters to the Jackass 3D Prank Contest.

Rajan Sadalia shares his concepts of industrial design with us in these series of videos. Do industrial design - Part 1 of 11.