A thesis is the basis of any paper or essay. The thesis statement sets the tone and subject of your paper and starts you off on the right foot. In this tutorial, learn how to write an impressive thesis statement and get an A on your next paper!

Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

Your smartphone stays with you everywhere you go, so it's only a matter of time before you spill coffee all over it or drop it on the ground. For some of you, it has already happened, perhaps even multiple times. That's why we thought it was important to find out which flagship phones are the most life-proof.

Have you ever seen pictures or videos of balloons being let go into the sky and randomly floating away in all directions? It's something you often see in classic posters or movies. Well, guess what? Now you'll be able to do that without having to buy hundreds of balloons, all you'll need is ARKit!

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Do you ever feel as if your mind is running away from you? What if you could map out all of those thoughts into a coherent map that helps you make sense of your reality? Well, now you can.

In a previous tutorial, we were able to place the Mona Lisa on vertical surfaces such as walls, books, and monitors using ARKit 1.5. By combining the power of Scene Kit and Sprite Kit (Apple's 2D graphics engine), we can play a video on a flat surface in ARKit.

In a previous tutorial, we were able to measure vertical surfaces such as walls, books, and monitors using ARKit 1.5. With the advent of vertical plane anchors, we can now also attach objects onto these vertical walls.

In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls!

Have you noticed the many utility ARKit apps on the App Store that allow you to measure the sizes of horizontal planes in the world? Guess what? After this tutorial, you'll be able to do this yourself!

Apple is no stranger to lawsuits. They were in a decade-long battle with Samsung that finally came to an end last month, and they've been duking it out in the courtroom with Qualcomm since last year. The more recent case has seen both companies file suits and counter-suits, but now, Qualcomm is claiming that Apple's new iPhone X infringes on patents from a long-deceased mobile operating system.

It wasn't too long ago that Uber threatened to fire star engineer Anthony Levandowski. Eleven days to be exact. If Levandowski didn't turn over the documentation he allegedly stole from Google's autonomous car division, Uber informed Levandowski that they would take "adverse employment action." Today, The New York Times reported the ride-sharing firm has delivered on that threat. In a memo sent to employees Tuesday morning, Uber announced Lewandowski's official departure from the company "eff...

Microsoft Research has published a technical paper reviewing their work with near-eye displays for virtual and augmented reality to project phase-only holograms.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

Welcome everyone to the second part of the How To Become Anonymous online series. Today I will (briefly) introduce you to what has been defined "The most secure OS" : Tails a Debian based OS. (Official website: https://tails.boum.org/)

Due to recent conflicts, I feel the urge to post this, in hopes that some of you will feel less hatred towards newbies, or a more respectable name, beginners.

Usually when a hacker takes control of a system, they use it for a good purpose (on their end, anyway). But some hackers have made jokes or pranks with their hacks. Here is a list of the top of them...

Gerridae—you've probably seen these weird bugs gliding across the surface of the water when you're out swimming or fishing. These insects are commonly referred to as water striders, or more cleverly, Jesus bugs, for their ability to "walk on water". It's a pretty cool trick, but what could it do for science, right? Turns out, quite a bit. Photo by felixtsao

In our last ARKit tutorial, we learned how to measure the sizes of horizontal planes. It was a helpful entryway into the arena of determining spatial relationships with real world spaces versus virtual objects and experiences.

While "Baby Yoda" from The Mandalorian threatens to overshadow it, Star Wars: The Rise of Skywalker arrives in theaters next week, which means it's time for Disney and Lucasfilm to ramp up its promotional strategy.

While there is a lot to love about Apple's latest suite of iPhone models, the real draw comes down to the cameras. The iPhone 11, 11 Pro, and 11 Pro Max all have killer rear camera systems, but the front camera was also improved. Apple claims Face ID works at more angles than before in these models, which begs the question: can you unlock your iPhone when it's flat on a table?

You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the quickest routes to school or work. So naturally, we all have our favorite mapping apps, but which one is truly the best?

Every now and then, Hollywood has a moment where two (or more) movies arrive at around the same time, most recently with the release of dueling Fyre Festival documentaries.

Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files easy, secure, and painless.

The calendar app is one of the unsung heroes found within your iPhone. It's the ultimate personal assistant that you've come to rely on to keep track of your schedule and ensure you never miss a class or meeting, all while reminding you of upcoming birthdays and deadlines to help maintain good relationships with loved ones and colleagues.

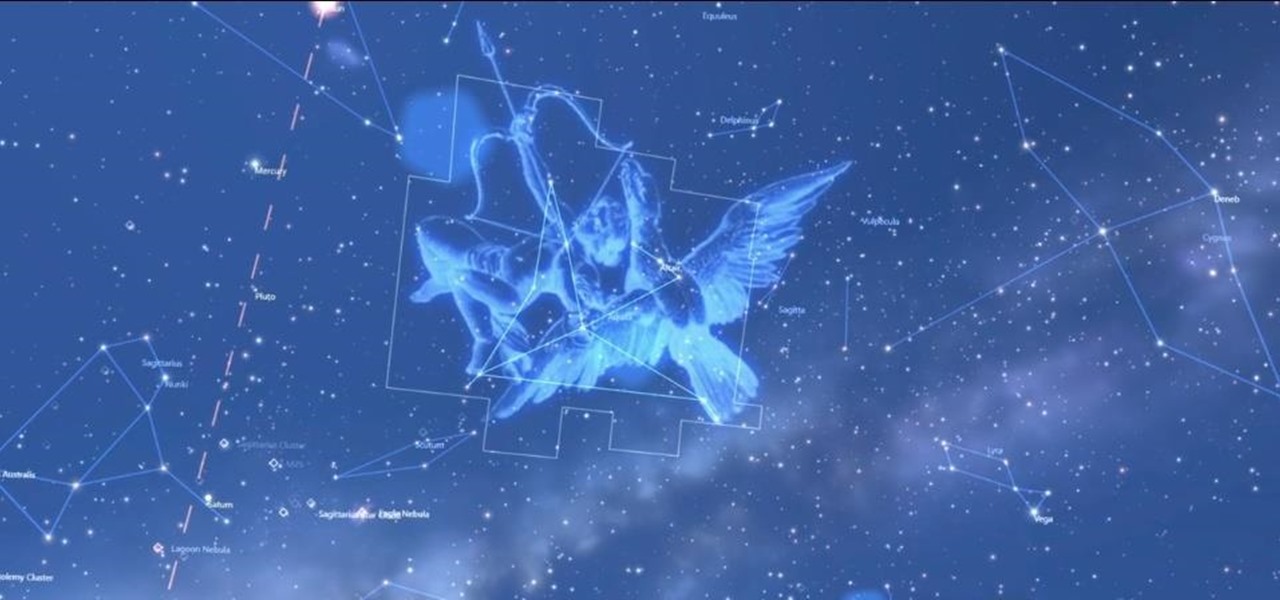
On June 23, National Geographic will begin welcoming visitors to the world's first outdoor planetarium in Quebec, Canada, where an augmented reality experience overlaid on the night sky will replace the projection systems of traditional facilities.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

As interest in augmented and virtual reality continues to grow, so does the need to bring objects from the real world into virtual space. With that, there's also now an increased need for solutions that bypass the time-consuming process of producing handmade 3D models.

The promise of augmented reality when it comes to gaming is the conversion of the player's real-world environment into a virtual playground.

Unity released the Beta 5.6 on December 13 with a bunch of new upgrades in the works, including support for Vulkan, better instancing options, and more improvements to particles—to name just a few that are potentially relevant to the mixed reality community. And today, December 15, Unity has just released the EditorVR that we reported on a few weeks ago as a part of their "Experimental" builds.

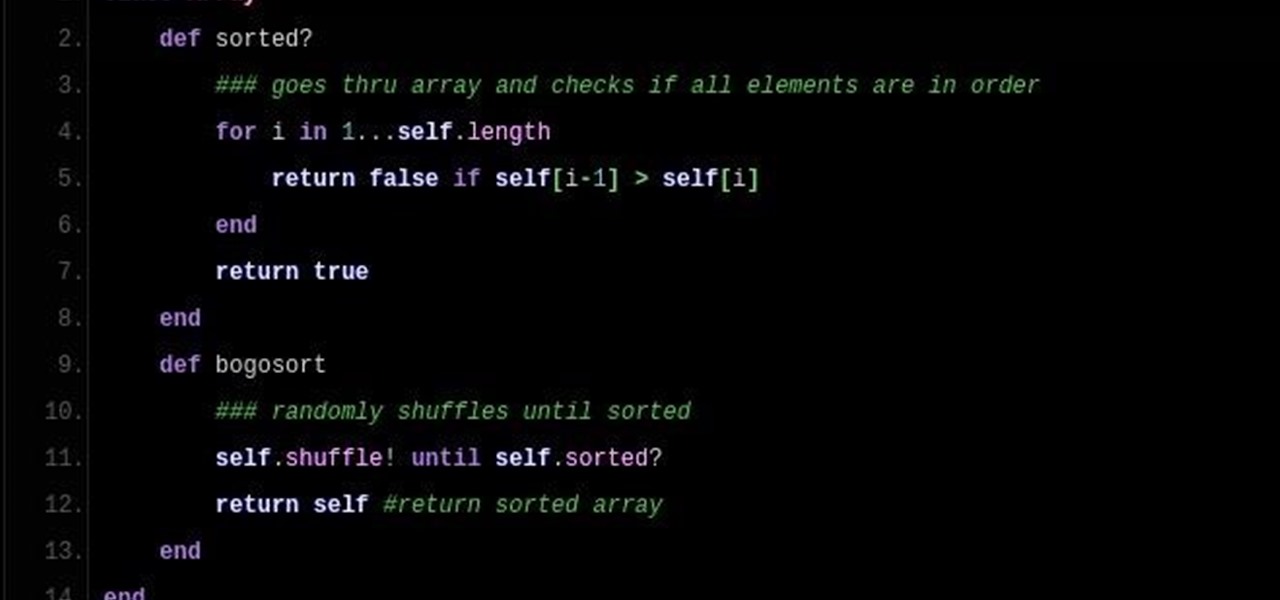
So DTM insisted I write up a little article on Bogo Sort. What Is Bogo Sort?

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

In my last tutorial I very briefly introduced Zanti , but in this tutorial I will start to show its many features. The first step on hacking is recon . You could use Nmap , but the problem with Nmap on Android is that by itself, in order to gain full functionality your phone must be rooted. Thank goodness for a few geniuses in Zanti's dev team whom managed to implant full fuctionality of Nmap in Zanti without rooting your phone. With that being said, boot up your Android phone and lets start ...

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

I've been doing tutorials on Rasberry Pi and I would like to thank everyone that have both read the tutorials and gave me feedback on how well I'm doing. But now I've decided to take a small break and start a mini series that I'm hoping to be at least five tutorials. This doesn't mean I'm gonna stop posting Raspberry Pi tutorials, but since I'm learning so much at the same time I've decided to share some of that knowledge. Hence this tutorial. Please sit back, relax and read on.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...