Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.

Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

What's up guys! It's time to discuss strings in more detail. Review

!!!WARNING!!! !!!Because of misleading informations please wait for the new post about this same argument instead of reading this post!!!

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

Well, this is my first article so if it sucks tell me...lol!! Story Time

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

Welcome back, my hacking friends. We use our smartphones every day, for business, socialization, and leisure. The number of iPhone users is increasing in dozens of millions every year, with a whopping 63.2 million users in 2014 alone. That's a lot of users.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

Get some tinfoil hats and make a time machine because we are about to go back to the 90s and learn about some phreaking.

While our smartphones are many things, one of their primary functions is to make calls. Many of us try to avoid ever having to make calls, but there are situations when it's a must, such as wishing your grandma happy Birthday or calling 911 — and in those times you want stellar call quality.

Whether it's a short road trip or an 18-hour flight, our phones are now essential travel companions. No longer do we need a GPS unit, maps, cameras, camcorders, or even boarding passes. However, not all phones are created equal in this regard. Some are more suited for traveling, no matter the duration.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

This week, Snapchat parent Snap came closer to fulfilling its smartglasses destiny by adding new 3D content capabilities to its third-generation Spectacles. At the same time, the now defunct Meta Company continued its fall from grace, as a judge ruled in favor of the plaintiff in the patent infringement case against the Meta 1 and Meta 2 headsets.

It was a long time coming, but we finally have a meaningful conclusion to the legal case against augmented reality startup Meta Company.

While photography usually gets all the love, our phones have gotten really good at capturing video. Think about it — when was the last time you needed a camcorder for a vacation? With mobile cameras getting better each year, we're now at a point where smartphones can be used for pro-level videography.

The HoloLens has made enough of an impact on the healthcare industry for Microsoft technology partner Medivis to convince investors to pledge $2.3 million in funding for its surgical platform.

With the same starting price as its predecessor and a nice list of improvements, the OnePlus 6T is a great buy for a number of reasons. But for many Android users, the main selling point for the latest OnePlus flagship is how easy it will be to root and mod the device.

Between acquisitions, hirings, patent applications, and insider reports, all signs point to Apple building a smartglasses product that could ship as soon as 2020, but the company has not officially confirmed such plans.

Although the initial reception for the Galaxy S9 has been generally positive, recent reports paint a potentially bleak image — some S9 owners are complaining that their new devices have "dead zones" in their displays, which don't register their touch inputs. Luckily, there are steps you can take to fix this problem.

Apple's Animojis took the world by storm with their ease of use and fluidity. They added new life to your emojis by mapping your face with the technology that lives inside the iPhone X. Now, Samsung is also adding new life to emjojis with the introduction of AR Emojis in the Galaxy S9 and S9+.

Samsung and Apple are the two titans of the mobile phone industry. After Apple deployed the iPhone X in November, Samsung had three months to brood until Mobile World Congress, where they unveiled the Galaxy S9. Now that both phones are out, it's time to put them head-to-head.

Google and Samsung are the biggest players in the Android world. Despite a rocky launch, Google's Pixel 2 XL became one of the premier Android devices of 2017, headlined by fast performance and a pure version of Android. Still, many users prefer Samsung's offerings, and their Galaxy S9+ is poised to be the phone to beat in terms of specs.

With the Galaxy S9 finally making its debut, flagship season is officially underway. But even though Samsung's latest offerings are the newest phones out there, they already face some stiff competition — namely, the LG V30.

Meta Company has filed its response to allegations that the user interface for their augmented reality headsets infringe on six patents owned by a mostly-unknown company.

We may not know what Magic Leap's product looks like. And we haven't received even a "save the date" for its launch. But we know that it will display mixed reality comics from Madefire when whatever it is arrives.

The highly anticipated iPhone X is finally up for preorder, and it's been almost as exciting as we expected. With the dual cameras, bezel-less display, and high-tech facial recognition, there's almost nothing on the iPhone X that won't be liked. But around the same time as the iPhone X's announcement, another phone was revealed, and almost everyone seems to have forgotten about it. We didn't.

Now that the cutting-edge iPhone X is up for preorder, everyone is excited to see how the new device will compare to offerings from Apple's competitors. Namely the Galaxy Note 8, which is a beast of a phone in its own right.

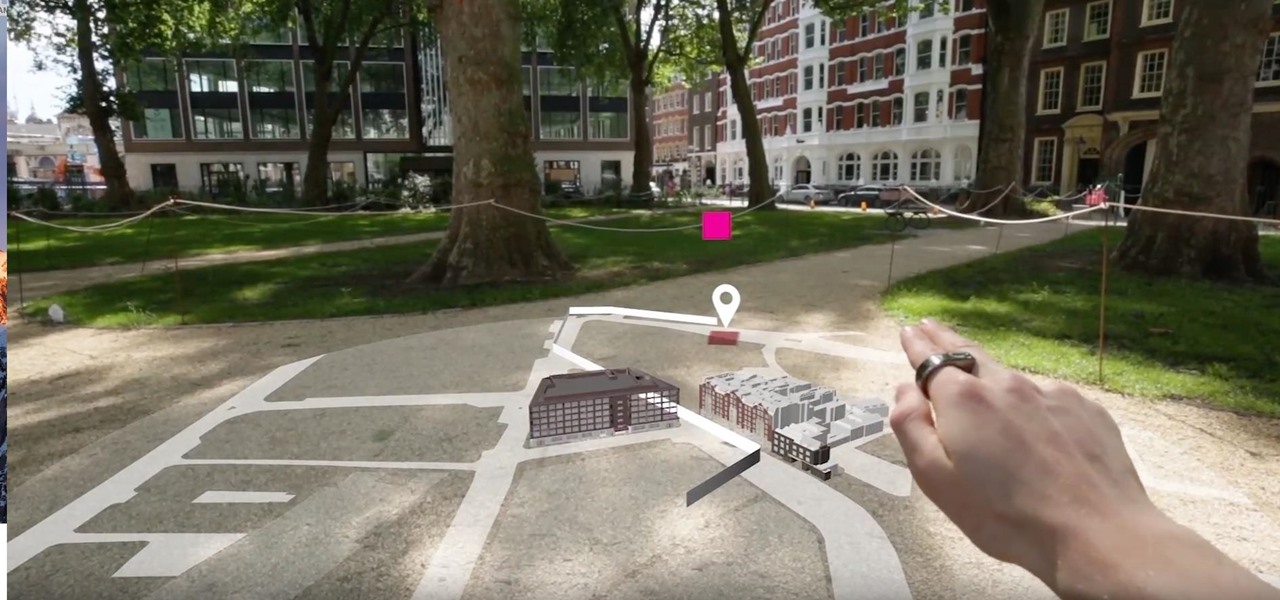
Forget what you know about controlling augmented reality experiences. "Scroll" lets you interact with augmented reality using a much more subtle approach: A ring.

Apple is notoriously private when it comes to perspective products, but the latest leak from their De Anza office in Cupertino suggests that a new augmented reality device could be coming to a store near you.

Antibiotic use in infants has been associated with a host of childhood conditions later in life. Yet when an infection is suspected in a newborn, usually a sample of their blood is drawn to check for the presence of bacteria and 5 to 8 percent of them receive antibiotics while the diagnosis is pending.

The brand new Pixel and Pixel XL, Google's first direct attempts at taking on the iPhone, haven't rolled out exactly how Google would have liked. The devices have already had more than their fair share of issues, starting with the camera, and now extending to the built-in speaker. The camera issues were marked as "solved" by Google, but the lens flare is still very much there, just not as prominent.

Forget headphone jacks and "Courage." Look past the shiny Jet Black finish and beyond the minimized antenna lines. Sure, quad-LED flash and dual cameras are nice—but dual-SIM would've been much better.

When Apple announced its new iPhone 7 and iPhone 7 Plus models in San Francisco, one of the biggest new features was an "IP67" water-resistance rating. Couple that with a few official renderings that show the new iPhone covered in water, and you'd probably arrive at one logical conclusion: The iPhone 7 is waterproof.