Sex makes the world go 'round, and when it does, so does gonorrhea. Finally some good news on the growing menace of drug-resistant gonorrhea — a large, long-term study shows a vaccine may work in reducing the incidence of an increasingly dangerous infection.

It's the end of an era. Facebook's WhatsApp just announced that older Android devices equipped with the Gingerbread operating system will no longer be able to use the messaging app as of February 1, 2020.
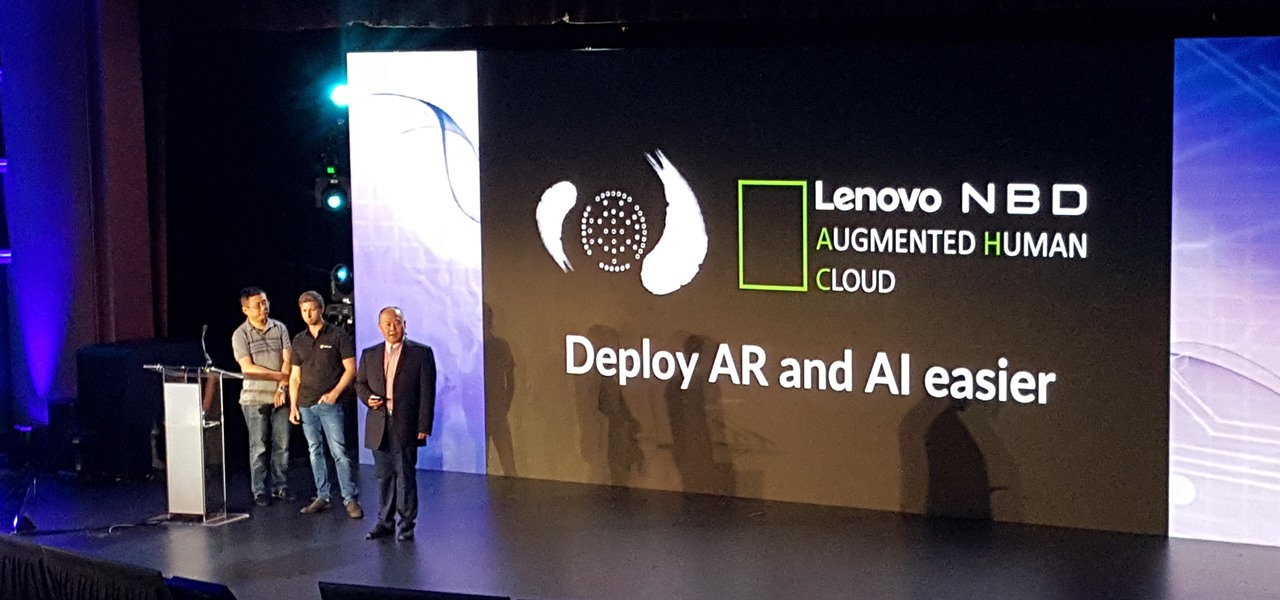
Lenovo has partnered with Wikitude to develop a cloud-based platform for delivering industrial-focused augmented reality content, the companies announced at the Augmented World Expo today in Santa Clara, California.

Sherif Marakby has returned to Ford as the VP of AVs & Electrification after a brief stint with Uber. Marakby's VP title will be effective June 12.

The Nokia 6 has been out since January, releasing in China before having a slow trickle of releases throughout the year. Despite announcing a global release, the United States never received a street date for the smartphone, and for all this time, Nokia has left us out to dry. Now, it seems, their phone could be on its way as the 6 has received its FCC certification.

The race for the future of the automative world has never been tighter, with reports earlier this week that Tesla is now almost as valuable as Ford. The neck-in-neck companies are focused on the same next big step for automobiles: the driverless car.

Experts from the World Health Organization just expressed concern for the rising number of measles outbreaks across Europe. Despite a perfectly capable existing vaccine, "immunization coverage has dropped below the necessary threshold of 95%," causing the measles to spread throughout the European region.

In case we haven't beaten the '90s revival to death enough, now Nokia is coming back to the US market. The three Android midrange devices that made their debut at Mobile World Congress last month are set for a global release, meaning they will also make their way stateside.

Seagrass may help your favorite beach stay a little less toxic. A new study, led by Joleah Lamb, a postdoctoral researcher in the Harvell Lab at Cornell University, found that coastal seagrasses reduce levels of pathogens dangerous to humans and marine organisms in near-shore waters.

You might feel the bite, you might not, but an infected mosquito has injected you with a parasite named Plasmodium falciparum, a single-cell protozoa that quickly takes up residence in your body.

Using mathematical modeling, researchers suggest weather and warming created the "perfect storm" that drove the Zika outbreak in 2016.

As we slowly approach its January 3 start date, CES 2017 seems to be shaping up to be an exciting year for smart glasses as well as augmented and mixed reality.

As first reported by Korean media outlet Yonhap News Agency, Samsung has issued a global recall for all of its Galaxy Note7 models (except China, it seems). This unprecedented move will surely do serious damage to the Note brand, and even Samsung itself.

We can't be in two places at once, but with virtual touch interfaces we can theoretically use a machine to act as our second body in a remote location. Over at MIT, Daniel Leithinger and Sean Follmer, with the advisement of Hiroshi Ishii, created an interface that makes this possible.
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.

Jem and the Holograms was one of the hottest cartoon series on TV back in the mid-'80s (though only for a brief time), and was recently given the big screen treatment with the feature film of the same name. While the film bombed at the box office (with good reason), your Halloween costume doesn't have to.

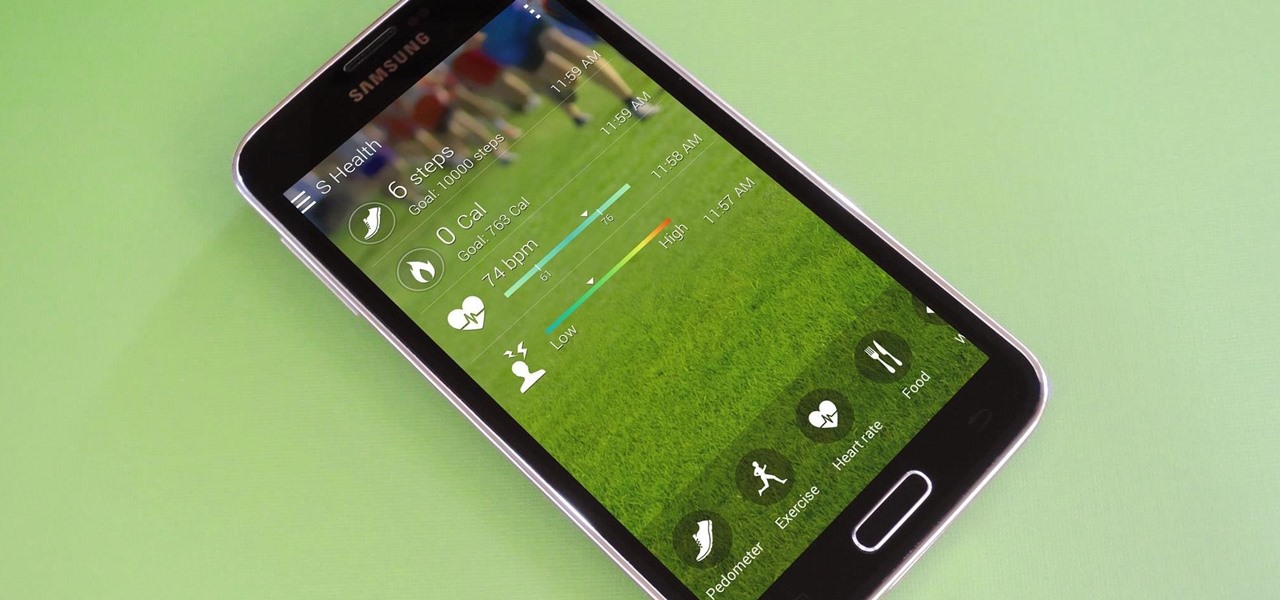
S Health is one of the biggest selling points for newer Samsung Galaxy devices. It offers a centralized place to view and manage data collected by all of the various sensors like the heart rate monitor.

I may not be a well-traveled man, but one thing I've learned from my few excursions across the world is that currency exchange rates are a serious pain to keep up with. With global markets seemingly in a continuous flux, I started looking for anything to make staying on top of them easier, and thats when I found Price Helper.

The new HTC One M8 is barely two months old, and we've already got a leak on its predecessor. Dubbed as the M8 Prime, or more likely the One Max (Two?), the larger, faster device should debut sometime in the fall (September is most likely), not too far away from the M8 Mini that's set to release later this month with degraded specs.

Learn how to choose the rabbit that's best for children. There’s probably not a kid out there who wouldn’t love a pet bunny, but rabbits and children can be a tough combination. To make the match a happy one, follow these steps.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Step 1: Score! Watch for the referee signaling a touchdown, field goal, extra point, or successful try by raising their arms straight up over their head. Raising their hands above their head with palms together signals a safety.

While conducting an OSINT investigation, it's important to be able to pull in information based on any clue you uncover. In particular, license plate information can turn up everywhere, from photos to live data to on your own street. You could use that data to find the VIN, see if a Tinder date has hit anyone, find out who's blocking your driveway, and so on. Skiptracer can help get the ball rolling.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

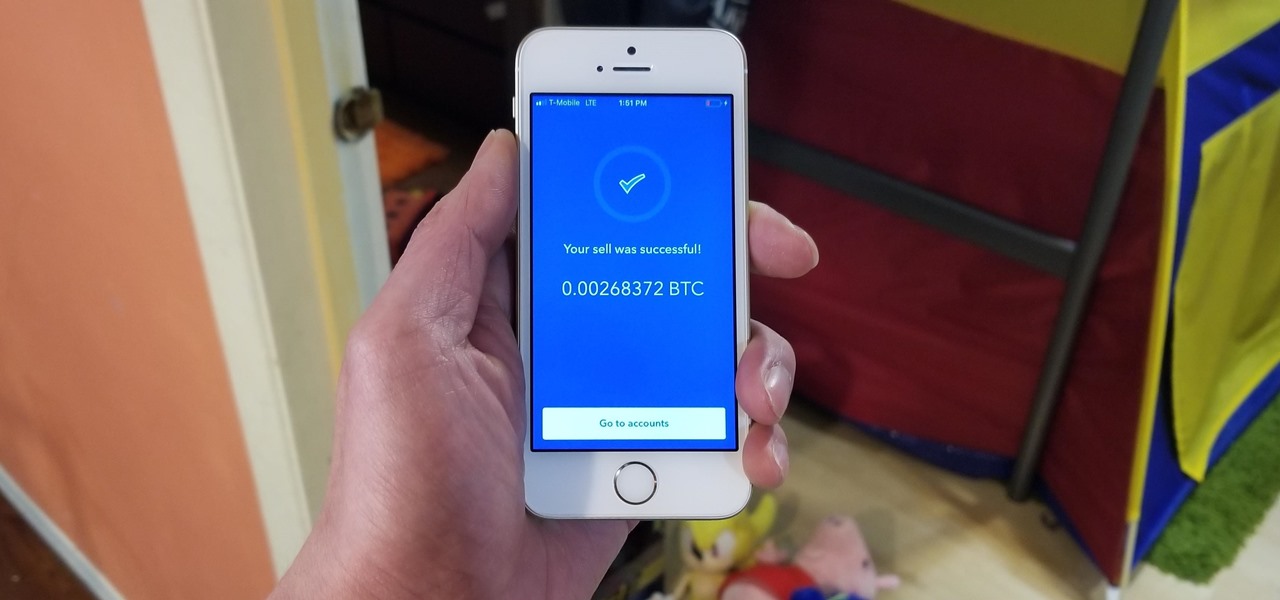
Coinbase has become the most popular mobile wallet app due in large part to its user-friendliness. The app takes the hassle out of buying and selling Bitcoin (BTC), Bitcoin Cash (BCH), Ethereum (ETH), and Litecoin (LTC), letting Android and iPhone users alike trade their favorite cryptocurrency in a few easy steps.

Citrus greening disease — caused by a bacteria spread by psyllid insects — is threatening to wipe out Florida's citrus crop. Researchers have identified a small protein found in a second bacteria living in the insects that helps bacteria causing citrus greening disease survive and spread. They believe the discovery could result in a spray that could potentially help save the trees from the bacterial invasion.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

The gag reflex: it can interfere while in the dentist's chair, upon seeing another person throw up, or even just getting a whiff of a disgusting, stomach-twisting scent. Every time this reflex kicks in, it stops us immediately, inducing a choking, gagging, coughing fit.

Sitting in a cubicle and never seeing sunlight during the workday is unpleasant to even think about—and sitting in a flourescent-light cube can have terrible effects on both our work performance and overall attitude. Yet there are ways to counteract the effects of cubicle sitting, even if you can't sit in a sunny office or work from home.

Complete silence or a non-stop Pandora playlist? People are often divided on what type of work environment they prefer. Whether you're a frequent loud music listener or you can't stand any kind of background noise, chances are you're pretty set in your ways.

There are many, many home remedies out there for relieving itchy mosquito bites. Everything from mud to banana peels and basil leaves to Alka-Seltzer tablets can help curb the itch. But before you even have to resort to any of those methods, you should be thinking about prevention. Wearing white clothing can help to keep mosquitoes aways from your skin, and there are many plants that will help mask your mosquito-attracting smell. But there's even more ways to keep those bloodsucking bugs away.

If you're anything like me, your day doesn't start until you've sloughed away your grogginess with a scalding hot shower. That perfectly-heated water can clear stuffed sinuses, relax the muscles, and make pretty much anyone feel squeaky clean. However, a cold shower can do even more for you if you can stand the low temperatures.

For some, there's nothing more thrilling than carrying an armful of bags while wandering the mall; for others, there's nothing more annoying. No matter what category of shopper you fit into, the truth is that you aren't always in control of what you buy.

Thanks to the steady increase in quality of smartphone cameras, it's easier than ever to take amazing photos or video without thinking twice. If you've been to a concert in the last five years, you undoubtedly know what I mean. But it turns out that using your camera as a new set of eyes might actually be ruining your ability to remember events on your own, rather than helping you to hold on to the good times.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.