Even an Apple device can get a virus, and you'll want to conduct a scan regularly to keep everything working well. Fortunately, there's an app for that! After you add McAfee to your iPhone or iPod Touch, you can run the program to check your device for viruses.

This shows a step by step method for using the Wii controller to output MIDI control to Apple Logic Pro and "conduct" MIDI with the Wii stick! This is a way cool Wii hack that makes the bluetooth controller work with Logic. You need to install another program to receive and control the data.

Oobleck, a word coined from the Dr. Seuss book "Bartholomew and the Oobleck," has contemporarily come to define the substance created from mixing cornstarch and water. This mixture is notable for its dilatant properties, and as an inexpensive and non-toxic Newtonian fluid. While seemingly liquid, under pressure, the substance reacts as a solid. Gentle treatment, however, will allow the material to remain in its fluid state. More simply put, this sh*t is crazy.

In this Education video tutorial you will learn how to conduct a viscous remanent magnetization (VRM) experiment. The purpose of this experiment is to measure the VRM decay vs time. You have to take two Orbo rotor magnets and mount them on a base. Mount two samples of the ferromagnetic tore used in the Orbo motor for the stator coils on a rotating disk. The disk can be rotated by a simple brushless motor. When the ferromagnetic core moves in front of the static magnet, an optical sensor detec...

This video details how to survive a knife threat from behind. When threatened from behind with a knife, do not attempt to move the body first, this will result in the attacker maintaining the capability to thrust the knife into the body. When threatened, place arms out and low in a submissive position, this is to be followed by moving the left arm backward in a sweeping motion to push aside the arm which is holding the knife. Once the arm is moved, turn the body and bring the elbow up into an...
Redstone is a pretty versatile substance in Minecraft. You can use it to rig up explosions, set timers and conduct electricity to open doors and make traps. This tutorial is a basic primer on everything redstone you can find in Minecraft.

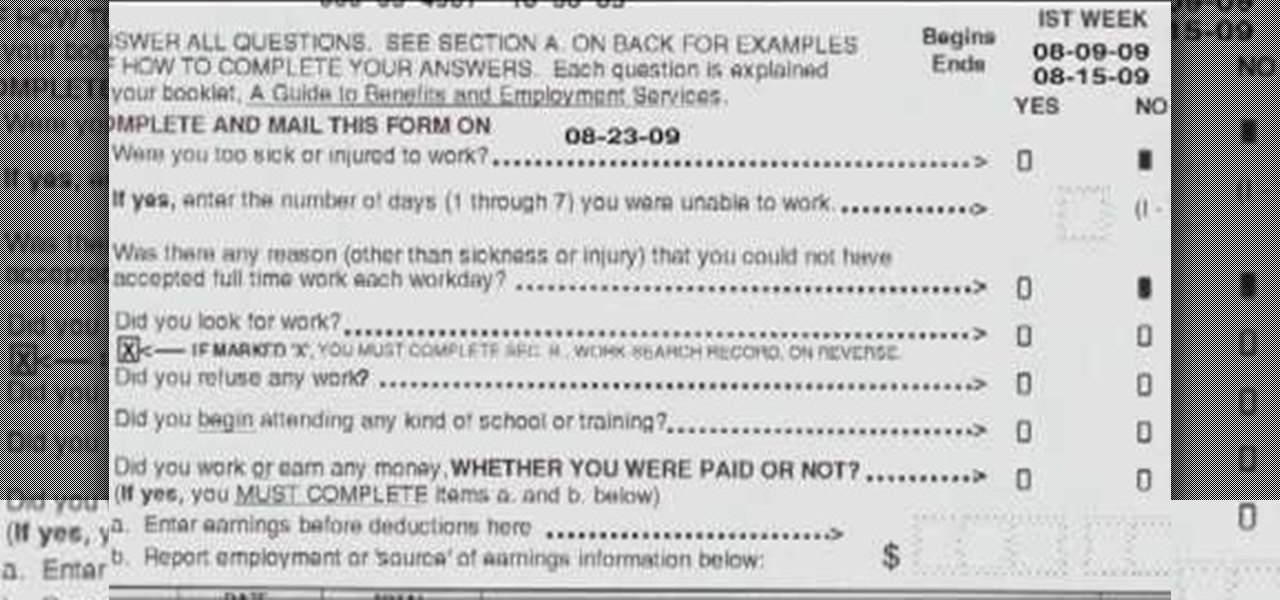
If you're an out-of-work Californian, take advantage of the benefits provided by the Employment Development Department (EDD) of California. If you've already followed the directions for applying for unemployment insurance benefits, then there are a few more steps involved in getting and maintaining your monetary unemployment reward.

The scientific method is one of the great constructs of modern academic thought. If followed rigorously it makes science as accurate as any general procedure can make it. Watch this video to learn the steps of the method and how to use it to conduct your own experiments.

Send text messages, conduct Google searches, play music, get directions and even send emails (complete with emoticons!) using the voice actions function available on your Android phone. This tutorial demonstrates this awesome new voice input functionality for your Google Phone.

The Georgetown Army ROTC program first describes the benefits, and then demonstrates a proper army pushup to standard. Pushups are common in the army, they increase the strength and endurance of your chest, shoulders, and triceps muscle. The push up is also a part of the Army Physical Fitness Test (APFT). In order to be contracted and received scholarship benefits male cadets in the age range of 17 - 21 must perform 43 pushups while female cadets in the same age range must perform 19 pushups.

Unless you're a high-schooler building a nuclear fusion reactor, the hardest part of a science investigatory project often is coming up with a good idea. You want it to be cool yet feasible, novel but still useful.

Trust is one of the most important aspects of a relationship. But there can be times when your instincts may be saying something that may conflict it. If you are dating someone who you think is still interested in his ex, then you need to find out before it's too late.

In this video tutorial, viewers learn how to make a tinder carrier that will keep the tinder dry. To make a tinder carrier, users can simply by a small cheap tin can. Then cut an X-shape in the side of the can to allow you to burn and blow on the winder. Now place the tinder in the can. The tin can can be used to store the tinder for dryness, and conduct fire with the tinder. This video will benefit those viewers who are planning to camp, and would like to learn how to make a tinder carrier t...

Eddy Currents are little circles of electricity created when metals are moved by magnets or even when magnets are moved by metals. To understand this practically take a regular piece of cardboard and drop it in between a horse shoe magnet. It drops normally with out being effected by the magnet. This is because the cardboard does not conduct electricity. Therefore it does not cause any eddy currents. But instead if you use an aluminum piece in the same way, it falls very slowly, because alumi...

How much air is actually inside a packing peanut? There is a simple experiment to conduct to see what is leftover. To begin, pour 200 ml of acetone into a glass container and add approximately 1800 ml of packing peanuts. Stir with a wooden spoon to dissolve. The video's author starts with the 1800 ml and realizes that that isn't enough. He then keeps adding until he has added an entire large bucket to the original 200 ml of acetone. After all are dissolved, all that is left in the glass conta...

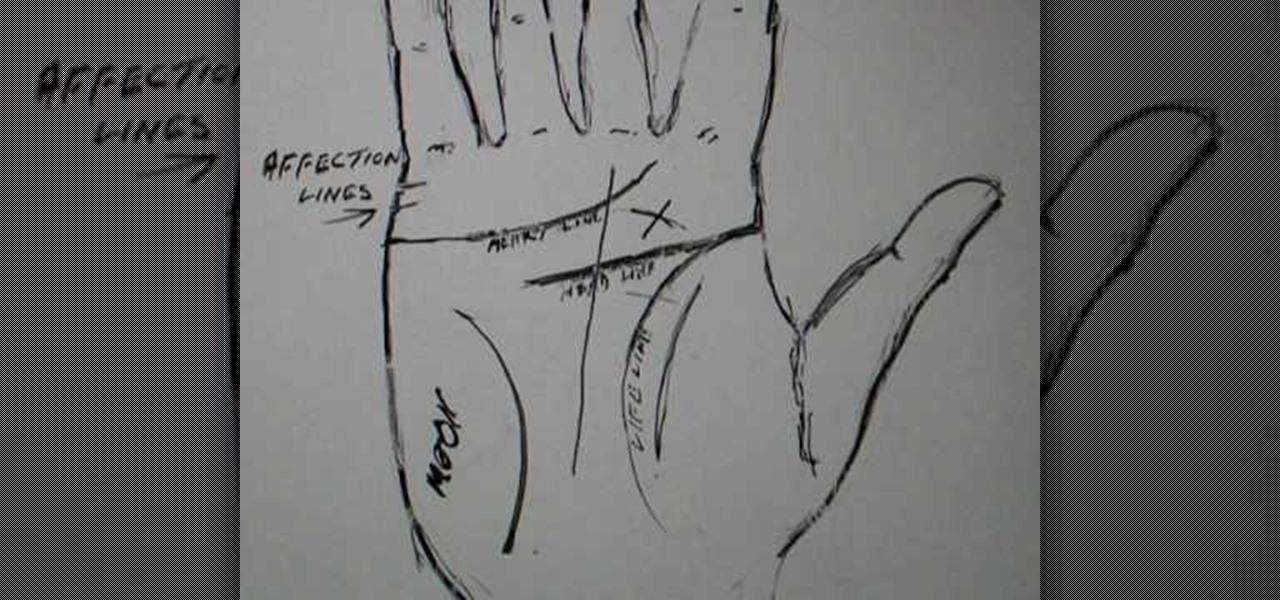
This video provides a diagram and explanation of the some of the more common mysteries in palm reading. Although the video does not provide much instruction for the actual act of palm reading, the diagrams are very helpful in determining which lines on the palm of the hand would be used to conduct a reading. The diagram shows the names and locations of each line that can be read on the palm. The life line, line of affection and line of intuition are explained in detail. The psychic cross is a...

This video describes the process of cutting glass with a regular pair of scissors. Objects required include a pair of scissors, glass to cut, gloves, a tub, and water. First, fill the tub with water to a proper depth to allow for submersion of the glass. Once the tub is filled, submerge the glass and once the glass is submerged, while holding it, begin to slowly cut the glass with careful and slow cuts from the scissors. It is suggested to not conduct the procedure with haste, take the proces...

Hypnosis can be used to manage pain, relieve anxiety, conquer phobias, prepare for childbirth, and cure insomnia, among other things. With a little practice and some simple techniques, you can amuse your friends or help them break a habit through hypnosis. Learn how to hypnotize someone with help from this how-to video.

Your friends want you to marry them! Before you can officiate their big day, you'll need to jump through some legal hoops. Learn how to officiate at a wedding.

Step 1: Score! Watch for the referee signaling a touchdown, field goal, extra point, or successful try by raising their arms straight up over their head. Raising their hands above their head with palms together signals a safety.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

The rectovaginal examination allows testing of the cervix, and perhaps a little higher. It is one of the first way a doctor may detect abnormalities on the ovary. Watch this video medical health tutorial and learn how to conduct a rectovaginal gynecological exam.

A proof of concept for an overhead crane training simulator is in the works. Using Microsoft HoloLens and an industrial-style controller, trainees can pick up holographic loads and transport them throughout a warehouse setting.

Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigatory projects.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Thanks to its intuitive interface that makes sending and receiving money a breeze, Venmo has become the go-to app for millions in the US. In fact, you've probably heard the term "Venmo you" being tossed around between friends. But before you take the plunge and sign up, it's always a good idea to read the fine print and know what you're getting into. Money is involved, after all.

Features like themes and a tab queue make Firefox an extremely versatile mobile browser. Mozilla is constantly adding bonus functionality like this to Firefox, but a long-time staple is perhaps the most powerful feature: Extensions. This system gives you the ability to add features without having to upgrade the entire app.

Whether you're a pro or someone just taking off the training wheels, buying a bicycle can be difficult. There are plenty of choices and different kinds of bikes for different conditions. Knowing which bike to choose could be daunting. Taking the time to select the right bike ensures that your investment yields the rewards you desire.

JrHelgeson teaches viewers how to recover their cell phone after getting it wet. First, once you get your phone out of the water, immediately take your phone apart. Make sure you take out the battery and the SIM card and various components. Also, try to shake out as much water as you can. You need to use distilled water next because it does not conduct electricity and it MUST BE distilled water. Fill distilled water all over your cell phone to rinse off as much of the normal water as you can....

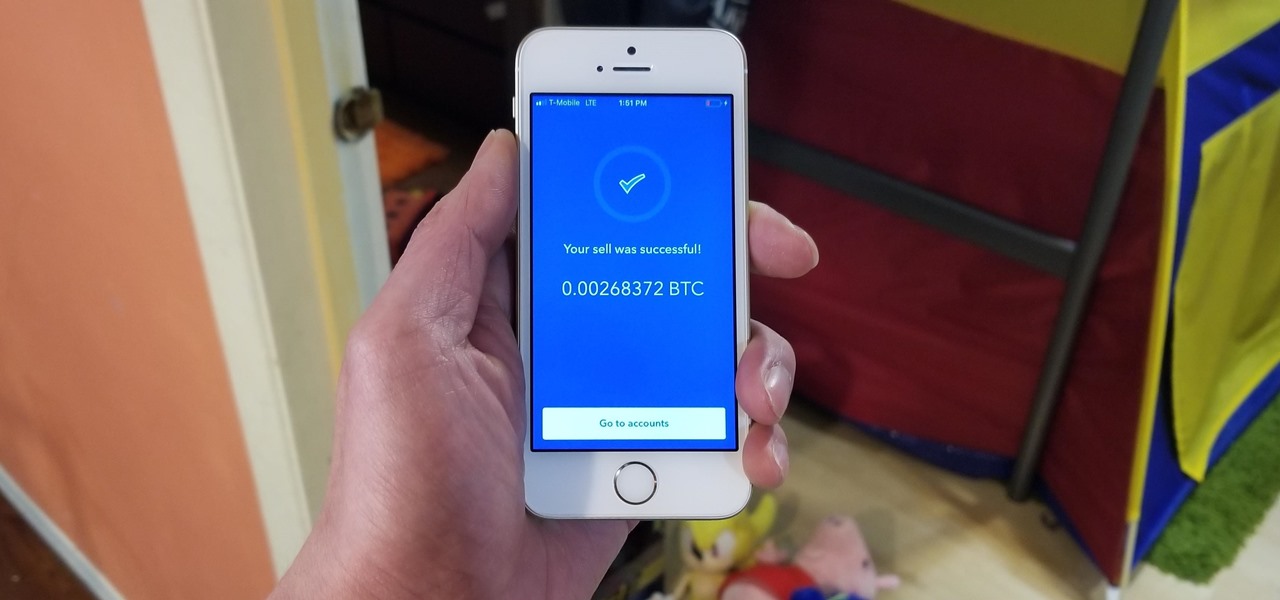
Coinbase has become the most popular mobile wallet app due in large part to its user-friendliness. The app takes the hassle out of buying and selling Bitcoin (BTC), Bitcoin Cash (BCH), Ethereum (ETH), and Litecoin (LTC), letting Android and iPhone users alike trade their favorite cryptocurrency in a few easy steps.

You must ONLY conduct this experiment if you are experienced in using combustibles and understand the risk. Fire is very dangerous and can seriously burn you. Seems harmless at first, but believe me, these are bubbles turned evil. When ignited, the bubbles pop almost instantly, and all the propane is released in a huge fireball.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

Whether it's for your company, your professional image, or just your personal account, making a poll on Instagram is a great way to reach out to followers, friends, family, and other users to measure their thoughts and opinions about any given topic. Instagram for Android and iOS makes it fun and simple to do so, offering the same tools to professional and personal users alike.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.