Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

The oven is arguably our most essential kitchen appliance (right alongside the fridge, freezer, and yes, even the microwave). But even though we've been using them for a few millennia, many of us know so little about our ovens that our cooking or baking can feel like a roll of the dice sometimes.

Making a good pie crust can seem intimidating to the uninitiated, but once you master this skill, a whole world opens up to you. Not only can you make all manner of fruit, custard, and cream-filled pies once you know all the tricks, you can branch out into the world of quiches, savory pies, and flaky, crispy turnovers, too. We've already told you how to get perfect, firm fruit pie fillings, so now, let's learn about crust.

The recent announcement that Facebook will begin inserting advertisements into its VR experience on its Oculus Quest headset has set the VR and augmented reality industry into a frenzy.

UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the Next Reality daily AR email newsletter.

I've covered augmented reality apps for about three years now and the most useful mobile app I've encountered over that time is Google Lens.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files easy, secure, and painless.

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

Amazon really wants to make itself at home in your home. Like, everywhere in your home, from your doorstep to your kitchen, your kids' rooms, and everywhere in between.

Whether it's a short road trip or an 18-hour flight, our phones are now essential travel companions. No longer do we need a GPS unit, maps, cameras, camcorders, or even boarding passes. However, not all phones are created equal in this regard. Some are more suited for traveling, no matter the duration.

While the iPhone came before the first Android smartphone, every new iOS version seems to include a wealth of features already existing on Android, and iOS 17 is no exception.

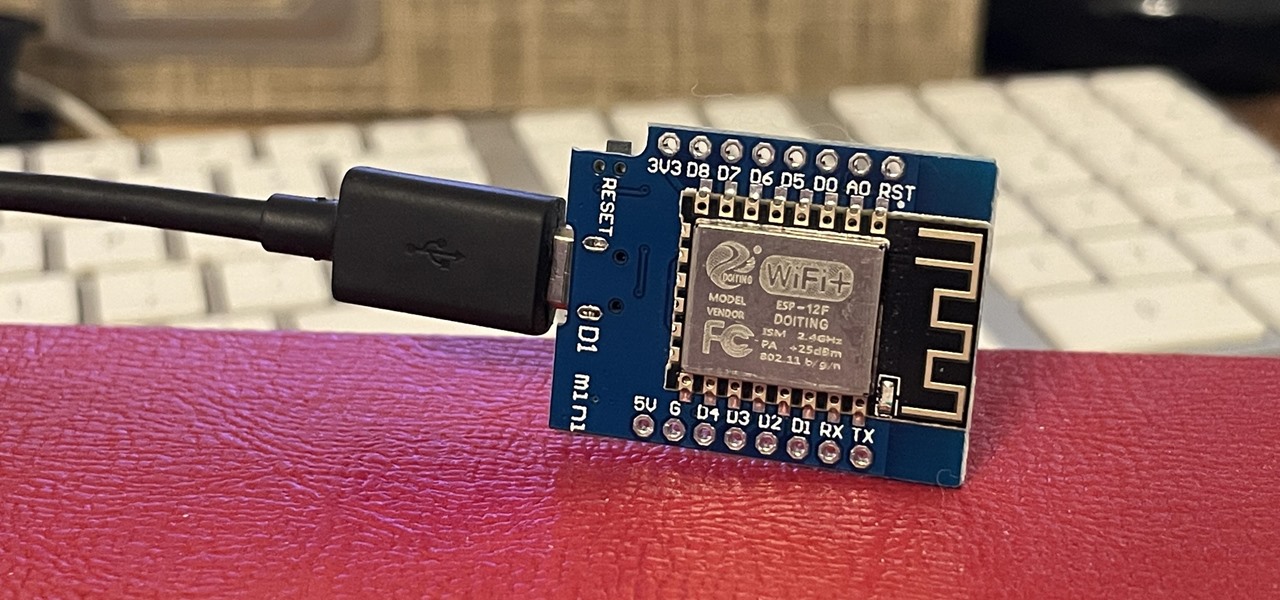
If you've wanted to get into Wi-Fi hacking, you might have noticed that it can be pretty challenging to find a safe and legal target to hack. But you can easily create your own test network using a single ESP8266-based microcontroller like the D1 Mini.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

Remember concerts? Those were fun. While gathering in large groups to listen to live music might not be allowed at the moment, the live music part still is. Thanks to the internet, more and more musicians are taking the stage each day to perform for those of us stuck in social isolation due to the new coronavirus. The best part? Many of these concerts are 100% free.

|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcased as a beta back in March 2019, so we've been digging around in it for several months. There's one dramatic visual change, plus there are a lot of goodies in general.

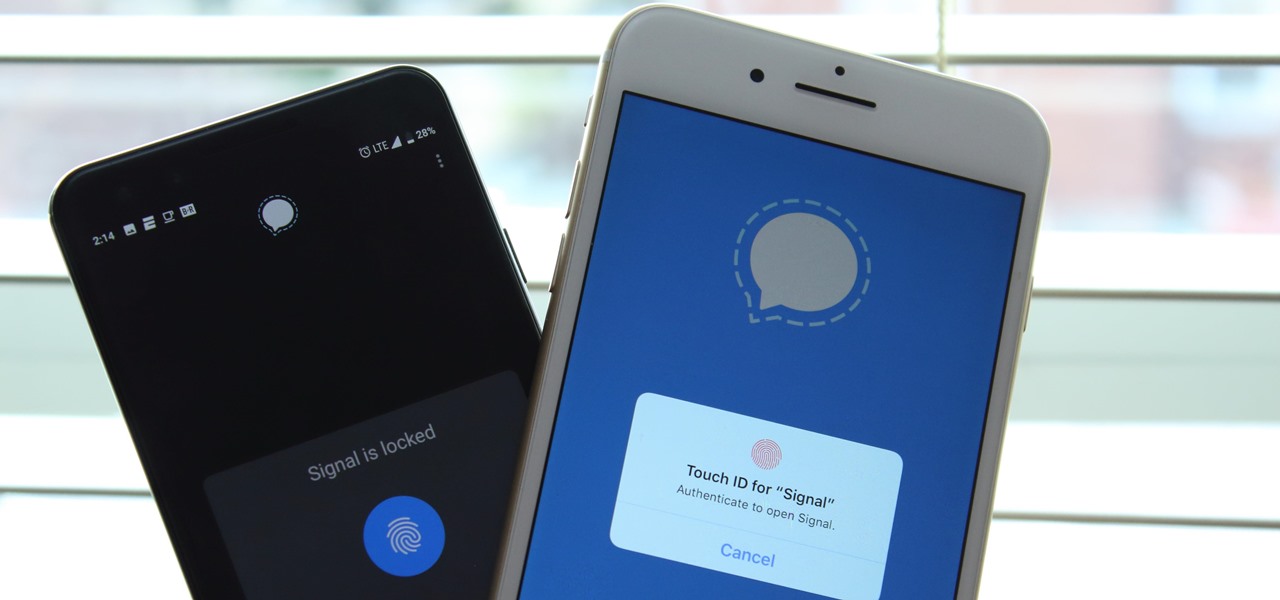
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through the process.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

We all love it when the Google logo changes to celebrate or commemorate special events— pop-culture touchstones, civic milestones, scientific achievements and holidays— their latest one for this holiday season is a Christmas card to everyone— an interactive Google Doodle with 17 artworks from different artists, each depicting a seasonal greeting from a variety of cultures and countries.

If you love action and adventure then you've come to the right place. Get ready for a red-hot science explosion as the A-TV science superstars show you how to make your very own erupting volcano!

Having a website people can easily navigate is common sense. It can save taxpayer dollars & help your agency achieve its mission. Here's how to dramatically improve your website by focusing on your customers' needs & adopting some basic usability techniques.

Soap suds aren't just for dishwashing! Blow away your family and friends with this cool science experiment.

Learn how to properly react and deal with unexpected guests. This narrated video with step-by-step subtitles discusses how to act, and how to accommodate for the surprise guest. Topics include food portioning, seating and table arrangements, and personal conduct. Deal with unexpected guests.

Do you want to create your own underwater adventure? Then let the A-TV science squad show you how to make the coolest underwater vessle around. You'll be the captain of your own submarine in no time!

What is Indirect Care? Does it affect the CNA's exam result? Indirect Care entails your behavior in terms of how you communicate with the resident, valuing residents' rights and residents' safety and security. Indirect Care is absolutely important because: (1) it is a graded performance, (2) it has separate score ratings, and (3 )it greatly affects the testees' overall performance during the clinical skills exam.

A press release should be about news. It should have a sense of urgency about it and grab the reader’s attention from the outset. A good press release must quickly answer the journalist’s immediate questions:
In late 2011, representative from China, Russia, Tajikistan and Uzbekistan submitted a proposal called the International Code of Conduct for Information Security (ICCIS) to the UN Secretary General Ban Ki-moon that called for international consensus of a global set of rules and regulations that standardize information flow on the internet.

In this article, I'll show you how to prank your friends on April Fool's Day with the very popular Google Voice, a computer to land/mobile calling feature. Basically, Google allows you to play whatever you like through the microphone port on your computer, and play it right through to your victim's phone. Whether it's Rick Astley ("Never Gonna Give You Up") or a text-to-speech application, general hilarity always follows.

The U.S. Circuit Court of Appeals for the District of Columbia has demanded that the TSA explain why it has ignored a now year old order to conduct a public comment process with regards to its use of so called naked body scanners. » Court Orders TSA To Explain Why It Continues To Defy The Law Alex Jones' Infowars: There's a war on for your mind!.

TV newscasters love to run stories about out of control parents fighting at youth sporting events. Here is an example of a story
LAKE JACKSON, Texas – 2012 Republican Presidential candidate Ron Paul was endorsed today by the Hon. Jordan Mason, City Councilman, Ward 4 of Rapid City, South Dakota.

Eric Jacqmain is one smart cookie. Borrowing from the same principles of Archimedes’ mythological death ray, the Indiana teenager used an ordinary fiberglass satellite dish and about 5,800 3/8" mirror tiles to create a solar weapon with the intensity of 5000x normal daylight. The powerful weapon can "melt steel, vaporize aluminum, boil concrete, turn dirt into lava, and obliterate any organic material in an instant."

Here at WonderHowTo, we are often presented with morally questionable HowTo's. When it comes to stocking our library, we have to weigh in the community value of indexing tutorials with potentially negative repercussions. Where is the line when it comes to areas like weapons, sex, and drugs?

For some reason, McDonald's hamburgers are mysteriously unsusceptible to Mother Nature's inevitable toll of decomposition. Yep, you pretty much have to dip a McDonald's cheeseburger in acid if you want it to decompose. So we're left with the question: Why? Why does a McDonald's hamburger retain its original shape, color and texture after 12 years?

Who knew playing SCRABBLE could lead to something like this?!? Nearly four years after he was convicted of seven counts of Internet luring, a Winnipeg man's online activities have landed him back in court.