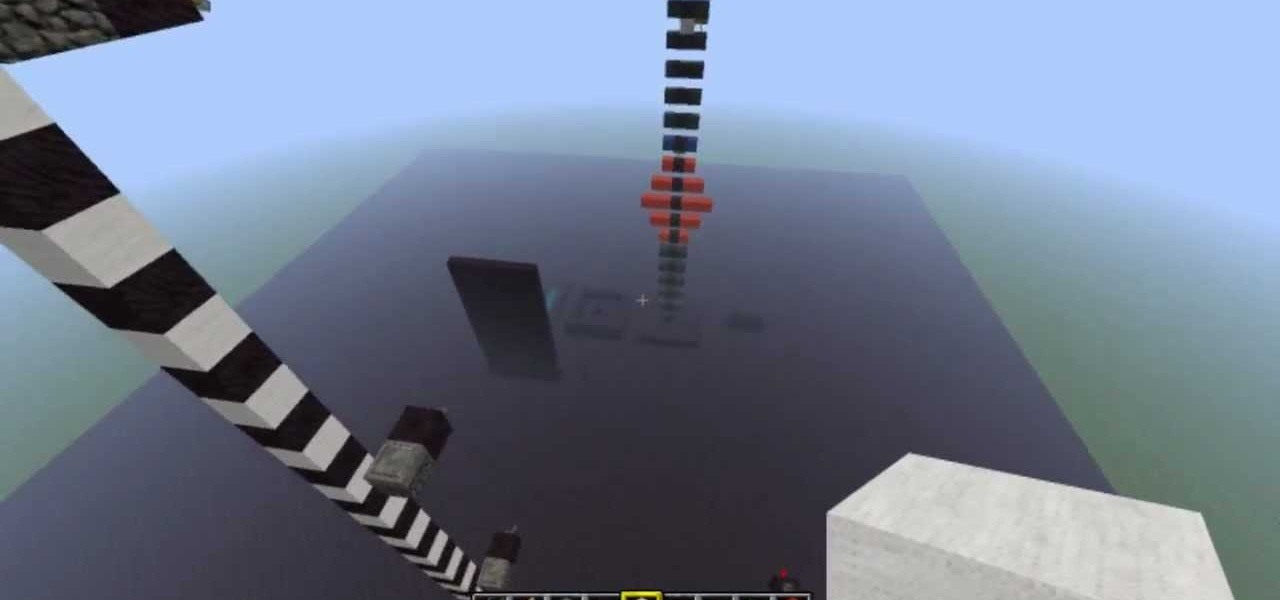
When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

I've cracked thousands of eggs in my life, yet I still usually mess up when I make my morning eggs. Sometimes I crack the egg to hard and end up leaving half of the white on the counter. Other times I don't crack the egg hard enough, and end up spending 20 seconds digging with my fingers until I can pry apart the shell. Sometimes I puncture the yolk on the shell, and other times the entire thing slips out of my hands.

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

It's 3 a.m. and you're wide awake—your mind is running wild with worries, workplace stress, and panic about the day that lies ahead. How can you possibly slip back into sleep and snag a few more hours of rest when you're so anxious?

When you're trapped at your desk before a jumble of data just waiting to be categorized, or zoning out during an important meeting, your mind wanders and, chances are, you feel a little guilty because of it. Yet you shouldn't try to reign in that distracted thinking. Instead, let your brain get distracted, and you'll unconsciously strengthen your memory.

By now, you've probably already installed 10.10 Yosemite, the newest version of Mac OS X, on your computer. While you most certainly noticed the visual changes, you might have missed some of the really cool additions.

Foodies and big-time chefs like Thomas Keller go crazy for fleur de sel. This finishing salt appears in fancy eateries and cookbooks the world over, and in the early 2000s, it was not uncommon to see diners in a high-end restaurant sprinkle a pinch of fleur de sel on their plates from their own personal stash.

Boozing it up at work might have been okay back in the days of Mad Men, but today, employers prefer that their workers stay sober. What you and your bosses probably don't know is that a little drinking on the job can actually increase your creative capacity and problem-solving skills. Alcohol Can Enhance Your Creativity at Work

Chances are you've got a bunch of wooden takeout chopsticks doing nothing but cluttering up your utensils drawer. That's a darned shame, considering that chopsticks aren't just for shoveling food into your mouth—they're actually the best cooking tools a cook can have (plus they come in handy when you run out of extra-long matches). Sautéing, Grilling, Deep Frying, & Stir-Frying

As a species, our cells are designed to use sugar for energy. Is it any wonder that as humans evolved, we grew to love the taste of sugar?

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

We've all been there. Stranded in a large lot or parking garage, braving the rows upon rows of identical cars in an endless concrete landscape because, for the very life of us, we can't remember where we stashed the very ride that brought us there.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Let's take a minute and talk about something you're doing wrong — using the restroom. Many view the subject as improper or even taboo, but why? Thanks to your upbringing, you've assumed you know the basics... But you don't. Avoiding discussion on the subject has led many of us to unwittingly interact incorrectly during our private time with our old friend, Jon.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Introduction So today and yesterday I was playing with TNT (as we all do at one point or another) and I was curious about a few things. From this curiosity, I went on to discover some of the science behind some things you may or may not have known.

Introduction So, today and yesterday I was playing with TNT (as we all do at one point or another) and was curious about a few things. From this curiosity, I went onto discover some of the science behind some things you may or may not have known.

In this video tutorial, viewers learn how to use physical exercises to help hit golf balls farther. Begin by using a weighted golf club and swing it several times a day. This will help build muscles and golf muscles. It will strengthen the users swing. Swing the weighted golf club slowly. With a regular club, take multiple swings. Golf muscles are quick-twitch muscles that help golfers develop speed and flexibility. Users can also use two golf clubs to swing. This video will benefit those vie...

In this video the instructor shows how to install a program or a game which is in ISO format. The first thing you will need is the ISO file that contains the game or program. Next you will need a program that can open the ISO file. Use the daemon tools for this purpose. Right click on the daemon tools icon in the notification area. From the menu choose the mount image option and point to the virtual disk. Now browser and select the ISO file that you want to open. This mounts the image to the ...

Learn how to care for your pet with help from VetVid. See how to recognize mast cell tumors in dogs.

Watch to learn how to replace the HEPA filter on a Dyson DC04 upright cleaner. You'll remove and replace the Pre Motor Filter and the Post Motor HEPA Filter on a Dyson DC04 vacuum cleaner. It is important to change the filter regularly as part of regular vacuum maintenance and to prevent loss of suction.

Watch to learn how to replace the HEPA filter on a Vax VEC04 vacuum cleaner. See how to remove and replace the central HEPA filter and the post motor anti-bacterial filter on a Vax VEC04 vacuum cleaner. It is important to change the filter as part of regular vacuum maintenance and to prevent loss of suction.

Have you always wanted to make a prank call but never had the guts to do it? Well, now you can because there's the Internet. In order to make a cool prank call without getting caught, first you have to choose a voice. The best one to choose is Arnold Schwarzenegger. To get his voice, go to Google and search for Arnold soundboard.

We prune roses for several reasons. Regular pruning helps to keep their size under control, though we must remember that all roses have a predetermined 'ideal' size. We also prune to shape the plant. We take out dead stems to prevent the dead area spreading back into healthy stems. But the main reason we prune is to make the rose more vigorous. This tutorial teaches you how to prune climbing roses for the best results.

Learn how to insert a reusable menstrual cup with this feminine hygiene tutorial. The menstrual cup is a great alternative to disposable tampons and pads. It is very cost effective and friendly for the environment. With regular sanitizing, the menstrual cup can last years. This video is specific to the Mooncup menstrual cup, although most menstraul cups are inserted in the same fashion. Watch this how to video and maybe you will decide to use a menstrual cup during your next period.

This is a tutorial for solving the Rubik's Cube Revenge, or the 4x4 Cube. If you don't know how to solve the regular 3x3, then you have no business here. Learn that first, then come back and watch this four-part series.

Try to get your ball in the hole in as few shots as possible - just like regular golf but with a soccer ball. The second video is a 2 player variation on soccer golf, only now the goal is to best your opponents score. The third video is a variation where the goal is to complete the course as fast you can (speed soccer golf).

This is a great twist to a regular veggie side dish. Watch and see how to cook string beans with a balsamic butter sauce and sliced almonds, yum!

This origami tutorial will show you how to fold a six pointed star out of a regular piece of 8 1/2" X 11" paper. There are verbal instructions in Japanese for those who will find it useful, but the step by step visuals are quite clear. To fold an origami six pointed star, one only needs a single piece of rectangular paper and a little patience.

To learn how stop worrying involves regular fasting from fear, learning to plan without worrying and to accept the future as it comes. Part of a Yoga class on Rasa Sadhana, the Tantric practice of emotional fasting.

Remember those old vinyl records? Remember jumping on the 8-track bandwagon? Switching over to cassette tapes? How much money you spent converting your music collection to compact discs? To MP3s?

No, not Charlton Heston. The only pudding he ever made was steak and kidney. I'm talking about Heston Blumenthal, world famous chef and pudding lover, and the man behind the "Heston"— a plum pudding with an orange hidden within, brought to you by Waitrose (see video below).

Safari's private browsing mode on your iPhone won't sync to other Apple devices or remember your search history, AutoFill data, or visited webpages. Still, it doesn't stop anyone who accesses your iPhone from opening your private tabs. If you don't want anyone snooping through your private tabs, use Chrome instead so you can lock the tabs behind biometric authentication.

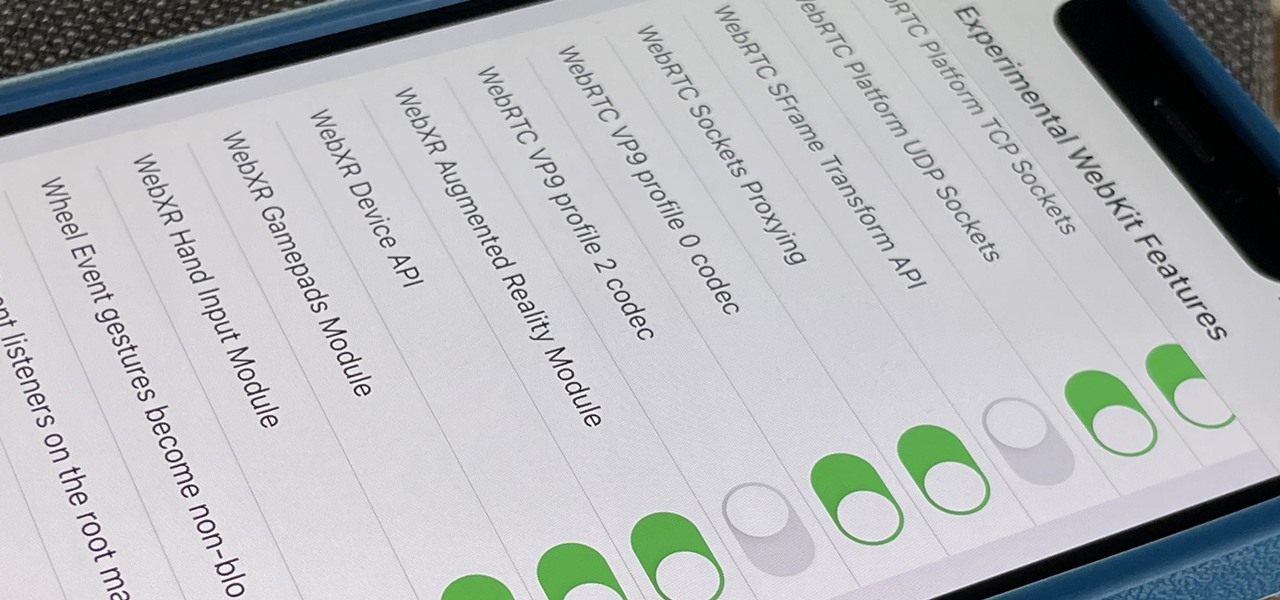
Safari's advanced experimental features give you access to new browser initiatives, upcoming web tools, element changes, behavior adjustments, and other preliminary feature tests in development by Apple. If you use them on your iPhone, you can either improve your Safari experience or wreck it. Resetting the flags provides a fresh start.

A low-key iPhone feature that's been around since iOS 10 can make the iMessages you send to family and friends more exciting overall. One particular element is, if you'll forgive my decades-old slang, "da bomb" for emoji.

We all know IT development is a valuable skill to have. But being a certified professional in the world's most in-demand project management and development tools? That's enough to get the promotion or new developer career you've been dreaming about.

If you do a lot of typing every day — writing reports, essays, emails, and whatnot — we can guarantee your day would be improved by taking less time to do it. Thankfully, we've found a super-smart AI-powered tool that will do just that, and right now, you can get an amazing 52% off a Lightkey Pro Text Prediction Software: Lifetime Subscription for the sale price of just $79.99 (regular price $169).