Last time we took a look at some of the creatures of the pond, including the dragonfly nymph. Today, we examine the all-grown-up dragonflies in the field you are used to seeing on summer days! Dragonflies are not dangerous, but the extra large ones can bite you something fierce if you handle them wrong.

Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it.

Dreams are like an internal human holodeck. Inside your mind, anything is possible, from your grandest wishes to your worst nightmares. This is all well and good, but what if you could control your dreams and become the omniscient god of a handpicked reality whenever you go to sleep? Inception took this idea to the logical extreme by invading other people's dreams.

It turns out that the popularity of soft circuit electronics has leaked out of the interwebs and into the hands of the U.S. military. Soft circuit electronics allow you to literally sew electronics circuits into fabric using flexible conductive thread instead of wire. Soft circuits can be used for all sorts of fun projects, like the TV-B-Gone Hoodie and the Heartbeat Headband.

As hard as you try to protect your valuable information with strong passwords and anti-doxing measures, there's nothing you can really do when someone else gives up your goods. And that is the case with the recent Global Payments breach.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Last week I had a quick look at V.I.K.T.O.R, the anthropomorphized automated editing app that lives on your iPhone, and today it’s time to put it to work.

Snapseed is a highly regarded and award-winning photo-editing app for iOS devices. Originating out of image manipulation specialist Nik Software in San Diego, Snapseed is Apple’s iPad App of the Year and, after using it for the purposes of this review, I believe it points to the future of image editing.

Can a free cloud-based video editor that lives in your browser replace iMovie? In three words: yes, it can. But whether you should use it instead of iMovie or an equivalent depends not on the functionality of the editor you need, as WeVideo can do what most of what iMovie does, but on what you need to do with your videos once they're finished.

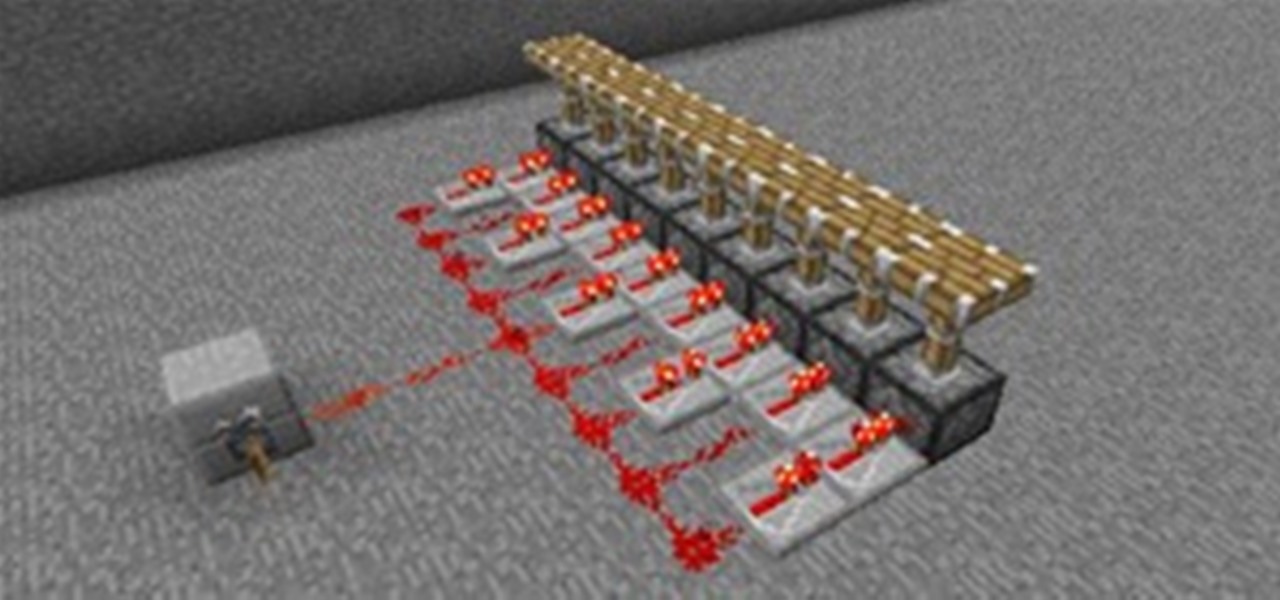
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. As we all know, redstone can be a very useful tool for make basic things in Minecraft more complex and intricate. For beginners to redstone, today's article will give you a basic understanding of how it functions, as well as its many uses.

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Carol Baldwin-Moody of Wilmington Trust describes the challenges that are present in her line of work as senior vice president and chief risk officer. There is a strong legal backing to every major issue in today’s society. Baldwin-Moody has come across several scenarios that aren’t covered by the dated constitutional law in effect today. In past years, a risk officer was thought to be a management concept that would be useful, but not worth the investment. Lately, a risk officer career has b...

Google+ is the greatest social network to emerge since Facebook annoyed everyone into joining, but that doesn't necessarily mean that our relationship with it is all rosy. Although Google+ has amazing innovations, like hangouts and circles, users are spending a lot of time begging for core features that take what seems to be an eternity to emerge.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

SHAITAN n pl. -S an evil spirit 60 points (10 points without the bingo)

Formerly ipchains, iptables is a script-based firewall that's included with both Mac and Linux operating systems. In my opinion, it's the best firewall in existence. The only downfall is that it's complicated for some people to use due to its script-based nature. But this should be disregarded, as firewalls are nearly the entire security of your computer.

Both Google+ and Facebook are competing for your time and space, and your commitment to one social network. To make their spaces more attractive to you, they've both made it easier for you to deal with people you don't like or don't care for.

Now that you can invite anyone you want to Google+, the floodgates are open. If you've been bummed out about not being able to share the joys of Google+ with your friends and acquaintances, make use of that handy envelope icon the right side of your stream page. Just enter the email addresses of the people you want to invite, and hit the "Invite" button.

The developing team Techland gets a free pass. Having thoroughly enjoyed their previous title, Call of Juarez: Bound in Blood, this sequel was bought on day one by good ol' fashion blind faith. After playing for most of today, it's still to early to tell if the game is a mess or a fun romp. Here are some first impressions.

So, you just bought Photoshop. It's time to familiarize yourself with the rudimentary tools. Let's start at the very beginning!

L.A. Noire is the newest Rockstar (GTA4, Red Dead Redemption) game created by Team Bondi ( The Getaway). The game is set in the late 1940’s in Los Angeles. The main character, Phelps, is a war veteran rising through the ranks from police officer to detective. The game is presented in mini episodes (one case per episode) and flashbacks. Once you finish a case, you go straight to the next one. Having played four cases where the character moves from police officer to detective, here are my initi...

So you want to be more involved in your community. That's great! It does not have to be super complicated to start being involved. Here are a few easy ways to go about doing so:

How to produce strange noises using your mouth and throat. Guttural Noises

Tis’ the season…for weddings! At the beginning of October, three of my college pals got married on the same day. This meant a ton of planning, parties, and presents for these three lucky ladies. This also meant that there were many a brides maid needing to make sure their bride was feeling special on such a wonderful occasion. One of the most exciting aspects of being the Maid of Honor is helping to plan the Bridal Shower, but it can also be a lot of work if you aren’t prepared. Here are 10 t...

MyShoppingGenie is an online shopping application that can help you find the best deals on products you search for.

Kurt Harris, MD, writes about paleolithic nutrition at his highly recommended blog, www.paleonu.com.

So our GUY has traded wallets with a gangster, met a beautiful Grocery Store cashier, and used the Gangsters credit card.

Here is a list of links you can use to ask for or give special gifts. First you need to find your Facebook ID number and copy it down somewhere, or memorize it if you can, then paste it into the links replacing the ###### symbols.

For a shorter and very basic video, watch this one. Watch the video to see how I get calfs or read the step by step directions below the video for more information. Place 5 dairies on your farm and put one bull in each.

Both on and off the set, the Gaffer or Chief Lighting Technician is one of the most important positions around. Though the average movie goer most likely has no idea the job even exists, they probably don't know what 99% of the other crew is/does either.

It's 1976. The hottest arcade game on the market is Blockade (or Blokade), an 8-bit maze game for 2 players. You and your opponent must move your characters around the screen in 90-degree angles, leaving a solid line behind them. Whoever runs into one of the solid lines first, loses. But soon you'll be able to play this fascinating game from the comfort of your own home—

WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.

What's a jig worm? Well, it's exactly what the name implies: a jig rigged with a trailing plastic worm. If you're not a seasoned fisherman, the answer might not have been so obvious, but that doesn't matter when you find out how important this jig worm is. Wade Bourne of MyOutdoorTV shows you how to fish a jig worm.

The entire Jackass gang are seated around a large conference table. They are seriously strapped down in the chairs and wires & electrodes are attached to all of them. In front of each them is are large unmarked push buttons. Each umarked button is linked to a certain Jackass member. When any button is pushed, some serious voltage is sent to a specific person. However the juice will be turned off, for most of the time, for a preceding event will be taking place will be well, SOME WEIRD STRANGE...

I recently thought about playing the game of basketball but with a twist. The game is called "Tacksketball." Of course, this is an idea that I can only see #TeamJackass handling. Basically, you need to place tacks on specific areas of the area/basketball court. If their was a way to keep these tacks positioned that would be even better. However, the catch is tacks will also be placed on the basketball, so beware of passes from your team-mates. This game must be played barefoot, as salt will b...

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

People sometimes ask me about the IT industry here in the states. These folks are usually either trying to get into a certain field, or looking to switch or move into another one. Right now, you may currently be a Computer Science major that will be graduating shortly and are interested in the current state of IT security.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three!