
News: Microsoft FCC Filing Hints That the Wait for HoloLens 2 Is Almost Over
We know that Microsoft's HoloLens 2 is due to start shipping later this year, but despite the trickle of news about the device, we still don't know when.


We know that Microsoft's HoloLens 2 is due to start shipping later this year, but despite the trickle of news about the device, we still don't know when.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.
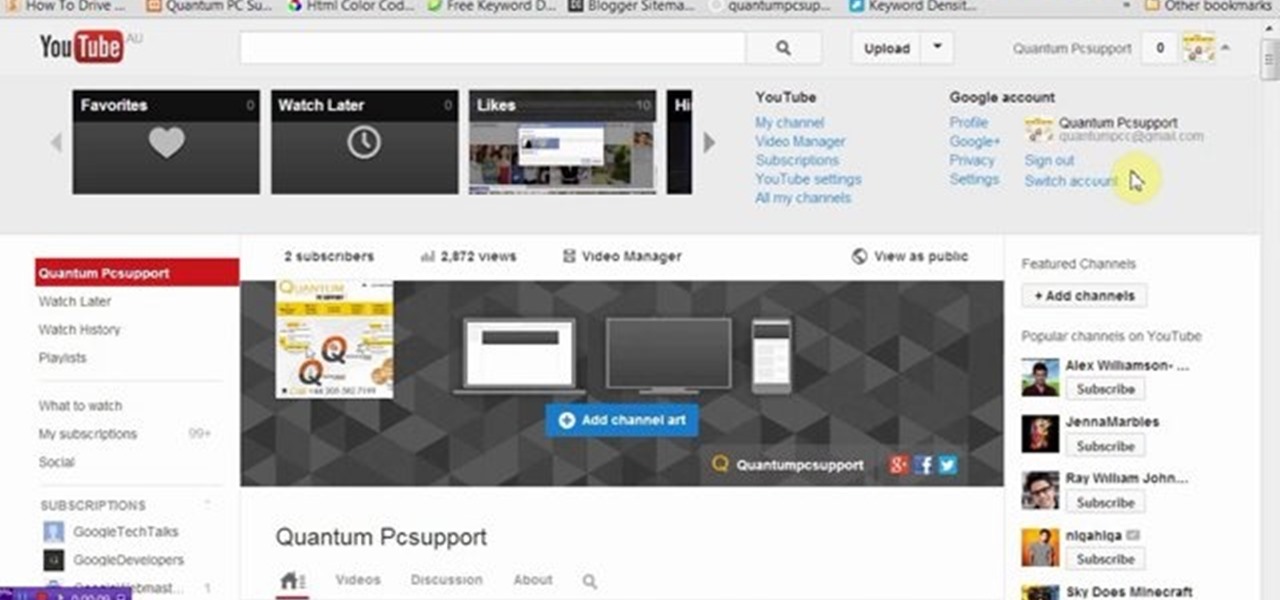
This video will guide you how to blur faces in YouTube video. Many times it’s needed to blur the faces of people in videos. In many sensitive cases faces are blur due to security or confidentiality reasons.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

A Russian augmented reality startup wants the next frontier in real estate to be augmented reality estate.

Meta Company filed suit today against a former employee and his startup DreamWorld USA, Inc. for the misappropriation of trade secrets and confidential information.

Getting support for your mental health is now as easy as opening up Facebook Messenger. By just opening up the Messenger app, you can connect to Woebot, a new chatbot developed at Stanford trained in administering cognitive behavioral therapy (CBT).

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

When it comes to the sub-$250 price range, the new Nokia 5.1 might be the perfect phone. Of all the new models announced at Nokia's event in Moscow, the Nokia 5.1 offers the most with the least compromises. For a third of the cost of a flagship, you get a phone with a premium build, solid specs, and good battery life.

In what's becoming something of a regular occurrence, Magic Leap has yet another internal, unforced error on its hands. Thankfully, this time it's not about legal skirmishes or theft, but a rather unusual break from company protocol that has been quickly swept under the rug.

Facing claims of misappropriation of trade secrets and confidential information by Meta Company, DreamWorld, led by Meta's former employee, Zhangyi "Kevin" Zhong, has fired back with a motion to dismiss the lawsuit.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

Today's WSJ takes a tour of Russian billionaire Andrey Melnichenko's 394-foot insanely luxe yacht, coined "A".