Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

There’s a good chance that you’ll be alone in life one day, and no... I’m not talking about a couch-bound, dateless loser with a pocket pussy and a bag of potato chips. I’m talking about alone. In the wilderness. Hungry. Cold. Lost. You can’t stay in one place too long, so it would be nice to have something to carry your belongings in. Maybe it’s post-apocalyptic land where you’re the sole survivor, and all the backpacks and rucksacks in the world are but mere ash. Either way, knowing this si...

A wire mandala is basically a wire halo of sorts, meant as a geometric configuration which contains the image of a deity. For some, a wire mandala can be used for meditation and stress relief, while for others it is a beautiful religious pendant that can be attached to earring clasps and chains to make necklaces.

Watch this cinematography tutorial on how to use the microShouldermount, which can be attached onto a tripod or used in its typical configuration as a shoulder mount. You can attach a monitor along the grip rod. Learn the essentials of the Redrock mounting systems for professional digital video cameras. Interesting tutorial for professional cameramen & digital filmmakers.

Kevin Rose is joined by John Todd, a well known, leading Asterisk expert, to introduce you to the amazing VoIP (Voice over IP) world of Asterisk, the open source voip telephony toolkit. In this episode, Kevin and John take you through the installation and configuration of this powerful tool, and show how it can be used to give anyone complete control over their phone experiences, such as voice over wifi, eliminating phone costs, choosing from hundreds of VoIP providers, creating your own voic...

A video that describes how to install Google Chrome OS onto your PC without changing your current PC configuration. What this means that you can use Chrome OS without changing your current OS (Windows Linux etc) and without making any changes to your dis partition or BIOS. The first section of this video explains how to use a simple USB drive to boot into Google Chrome OS. The second section of this video explains how to install Google Chrome OS onto your computer and launch it using your hos...

The Motorola Droid is getting a little long in the tooth, but it is still a remarkably capable phone with full keyboard, which makes it almost unique among it's Android-based competition. If you've rooted your phone (good for you!) and for some reason want to go back to the stock configuration that your phone was in when you took it out of the box, this video will show you how to do it. One good reason is if you want to update your phone's firmware, which will not work if you phone is rooted ...

This video tutorial from Live Monarch shows you how to fix a live butterfly's broken wing. You can help restore flight to a butterfly in need -- you can be a hero and make a real difference.

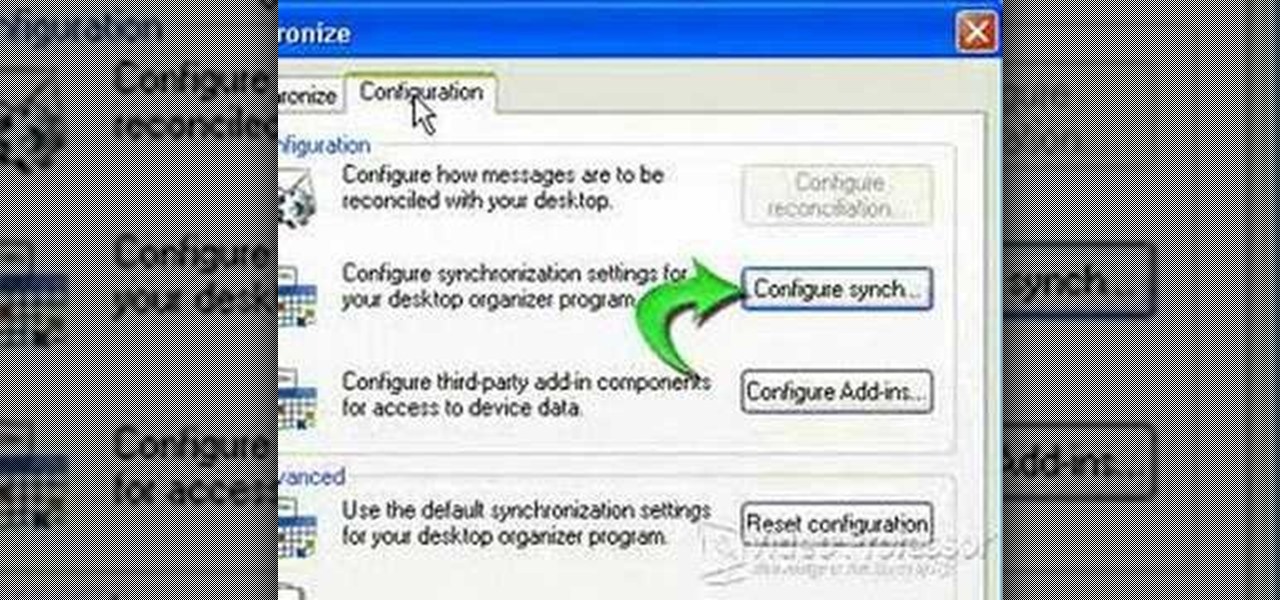
This video shows how to synchronize our blackberry smartphone with MS outlook. First open up the Blackberry Desktop Manager. Let us start by synchronizing the blackberry. Double click the synchronize button to load the synchronization settings. Here we can specify what we want to synch and where we want to synch firm. Click the configuration tab and select configure synch. Our device configuration menu let us pick which application on the black berry to synch and where to synch. Today we are ...

This is an intensive one-day overview video tutorial of the fundamental concepts of the Ruby on Rails Web programming framework, presented by the UC Berkeley RAD Lab. The overview consists of six sections of approximately one hour each. Click through the video chapters to go through the Ruby on Rails programming course.

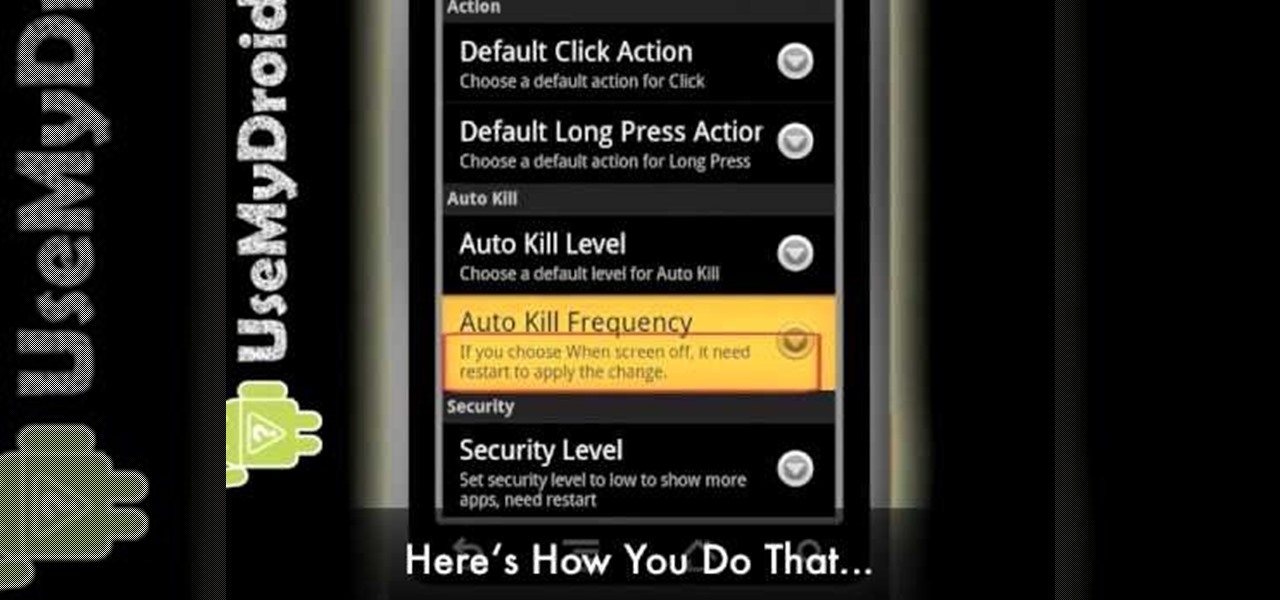
Battery drain is one of the biggest issues with Android phones, but with proper power management it is possible to do something about it. Advanced Task Killer is a free app with customizable settings that shuts down apps that are no longer being utilized. This informative video takes you step by step through the different configuration settings.

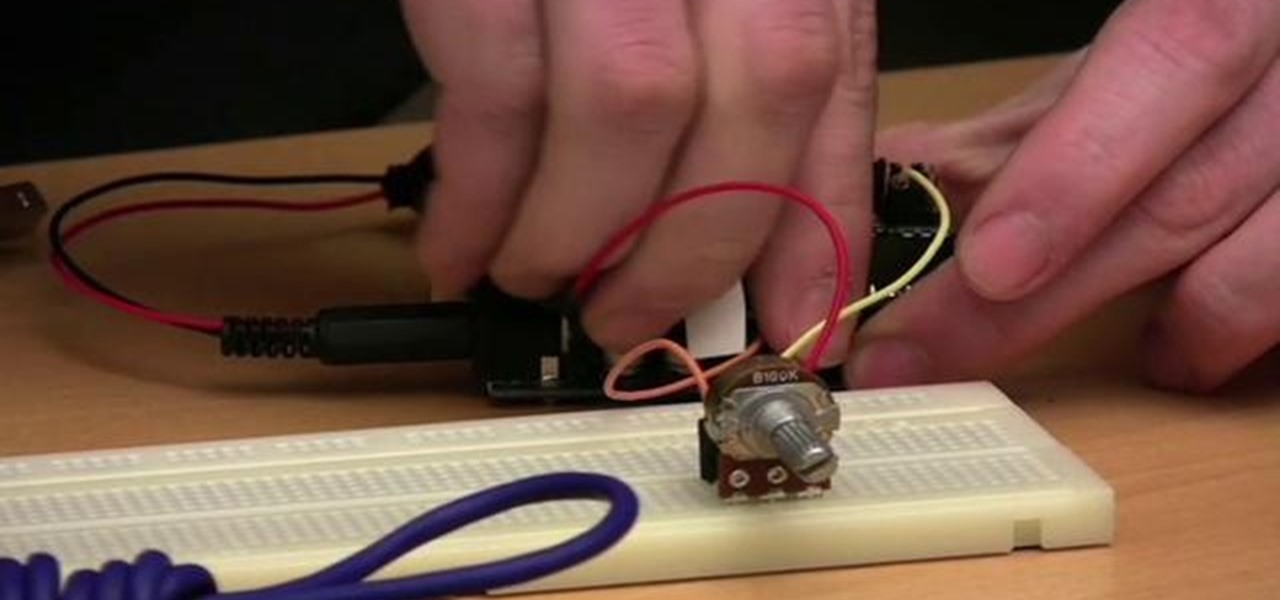
The XBee is a wireless radio module that allows you to implement a cheap and easy wirelss interface between two kinds of devices. This video will walk you through each step of configuration for your XBee. Modify it and add it to your next creation, whether it's a robot, machine, or something else from your imagination. The possibilities are endless!

This music production software tutorial is on the use of the BV512 vocoder as a frequency specific effects gate in Reason. This way, it is quite easy to draw a frequency curve to delay only your treble, distort your midrange, and reverb your bass, or any configuration imaginable. See how to use vocoders as effect control units in this video.

Mastering the concepts of the BOOT.INI file (the boot loader) in Windows XP to better control your Windows configuration.

In this video tutorial, Chris Pels will show how to extend the standard set of ASP.NET configuration settings with your own XML configuration elements. First, see how to create a configuration section handler which is required to interpret and process the information in custom XML configuration elements. During this learn how to use declarative model for defining the behavior of a configuration section handler. Next, see how to add a custom section handler and custom elements to an ASP.NET co...

In this video tutorial from Get Connected TV, hosts AJ Vickery and Mike Agerbo, will show you how to extend Widows Media Center to your XBox 360 using Windows 7. This video assumes that your XBox is already connected to your home network, so you may want to be sure to do that first. With this configuration, you will be able to not only watch movies, but view, pause and record TV on your personal computer, as well. You will learn how to access the Media Center section of your XBox, and get the...

This video shows you how to fix a Windows "Blue Screen of Death". You should know what to look for when you get the BSOD. You should look for the error code first and then the stock code. You should hit the F8 button upon start up to go to the last known good configuration and it will boot your computer to the last time it booted correctly. You can also start in safe mode. You will need to do a system restore. If that doesn't work do a Google search for the file name that is causing the probl...

Without looking, peeking, or even cheating, you will be able to figure out who will win in a virtual game of rock-paper-scissors.

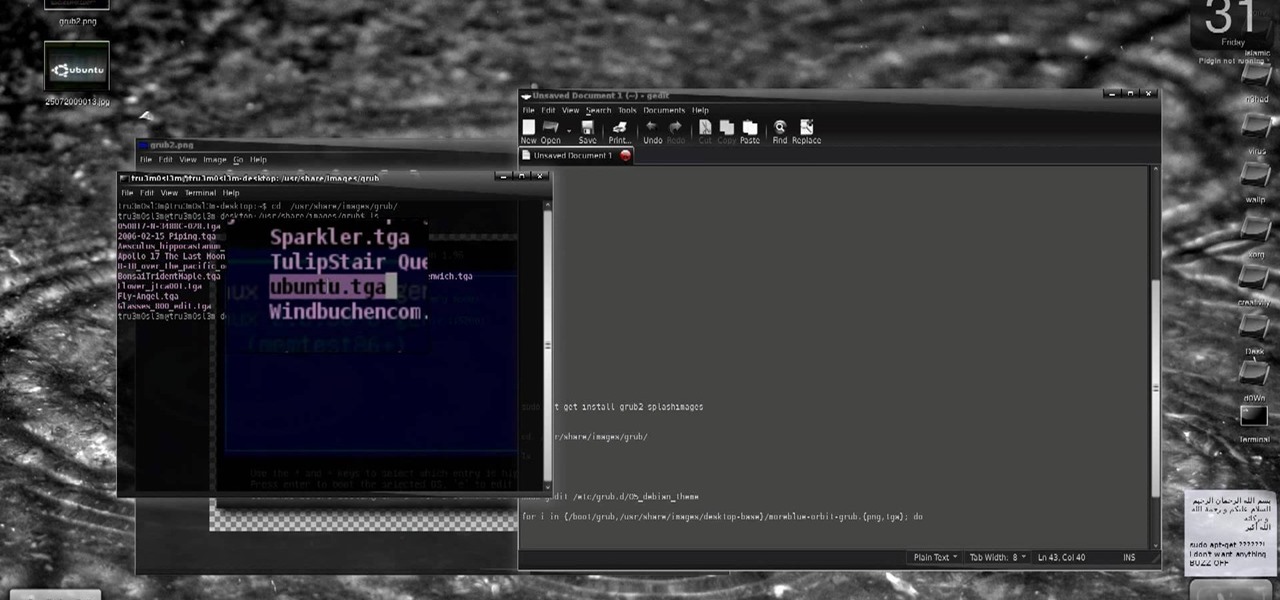
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install GRUB 2 and apply themes on Ubuntu Linux.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

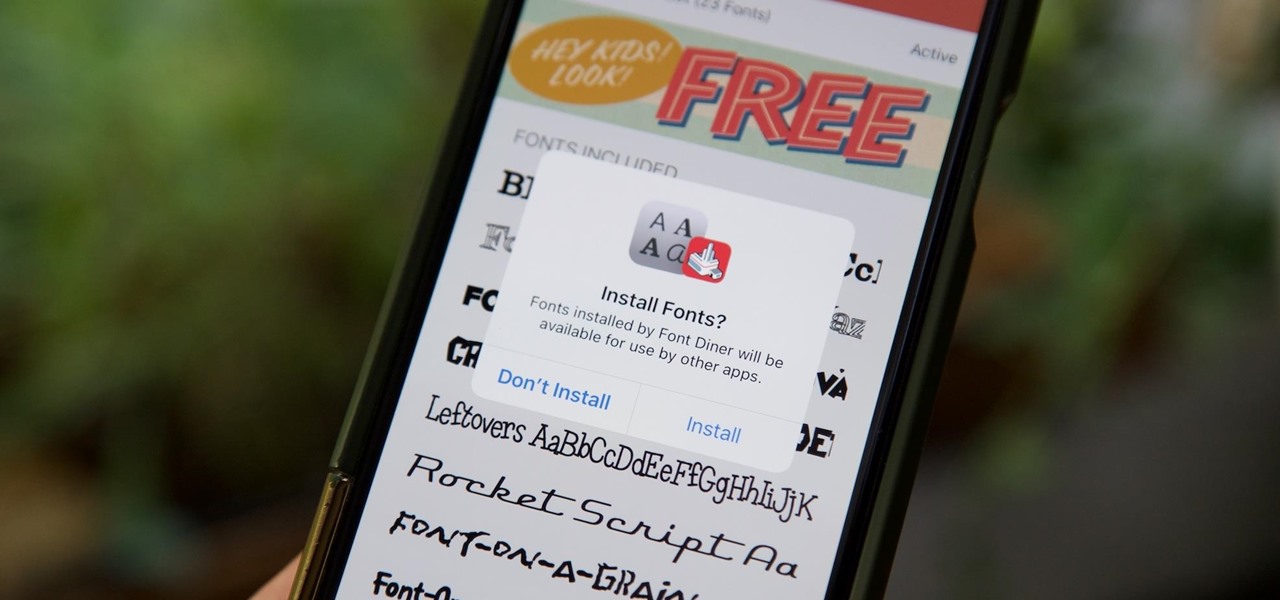
Apple added the option to install custom fonts and use them in different apps on iOS 13. The rollout has been a bit confusing, with Apple announcing partnerships with vendors such as Adobe, but also limiting the feature to work with only certain apps. Nonetheless, you can now download and install custom fonts on your iPhone.

Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

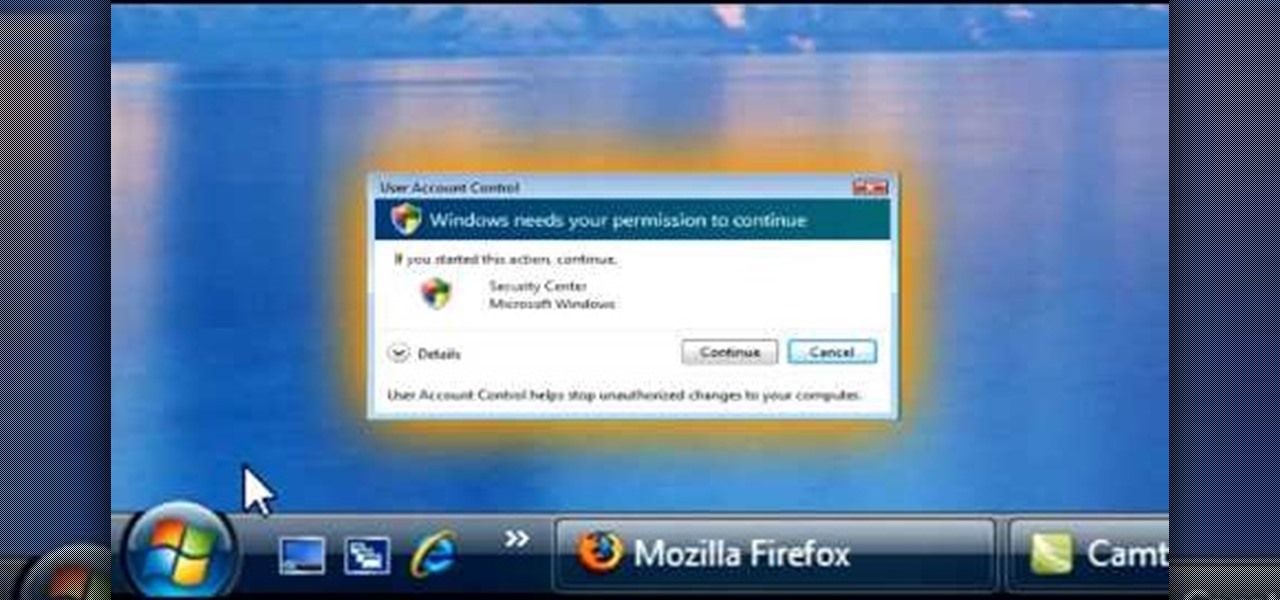
1. To disable the UAC (User Account Controls), first click start button and type "msconfig" into the start search text box.

If you don't have Adobe Flash, you can still edit Flash content on your websites. All you need is to know how to use external configuration, which you can do just from Notepad and a few .txt files. This tutorial demostrates how you can edit Flash content without having Flash Builder.

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

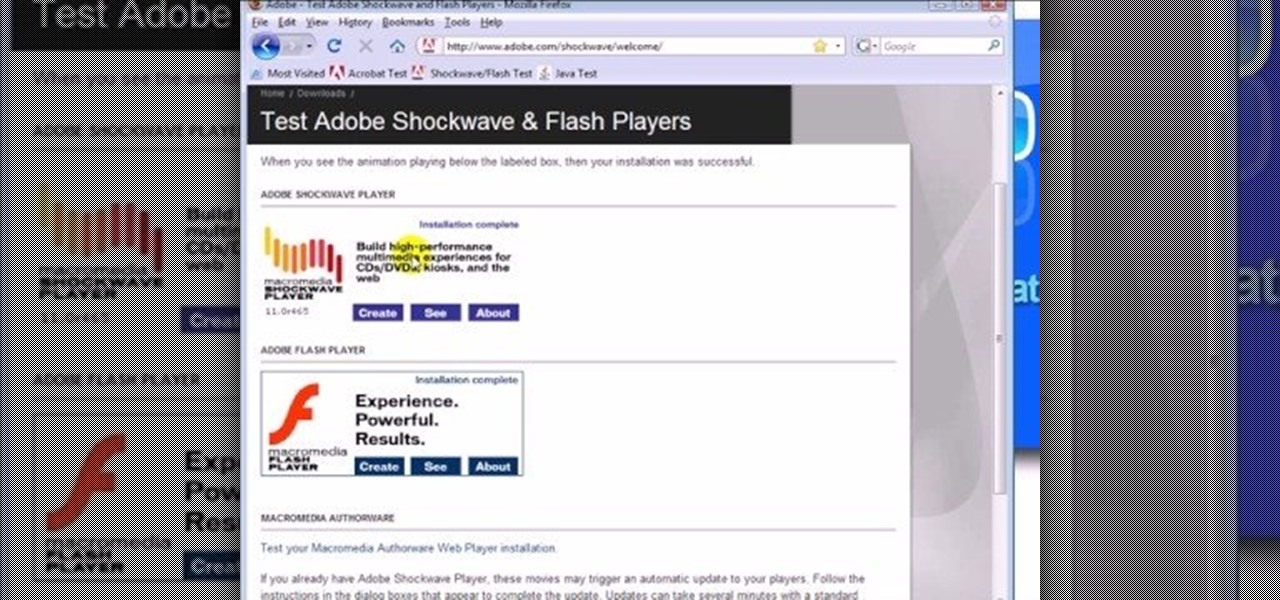
In this video, we learn how to test Adobe Flash, Shockwave, Acrobat & Java. First, see if you have Acrobat Reader installed and working properly by reading this PDF. If you have it installed properly, you will see a PDF with a configuration guide. To see if Shockwave works, go to: Shockwave. If working properly, you will see a "create, see, about" link, not one asking you to install it. Last, to test Java you will go to: Java Test. If you have installed this properly, you will see an animatio...

First of all, feel free to disregard the first 2:05 of this video, it is not a how-to but behind-the-scenes footage of this guy's short film. After 2:05, however, you will get a great tutorial on how to make a set of prop Wolverine claw quickly, easily, and cheaply. They are made out of cardboard and spraypaint, and as long as you don't do any closeups on them or require you Wolverine to open his hands with the claws out at any point (impossible in this configuration) they look plenty real. Y...

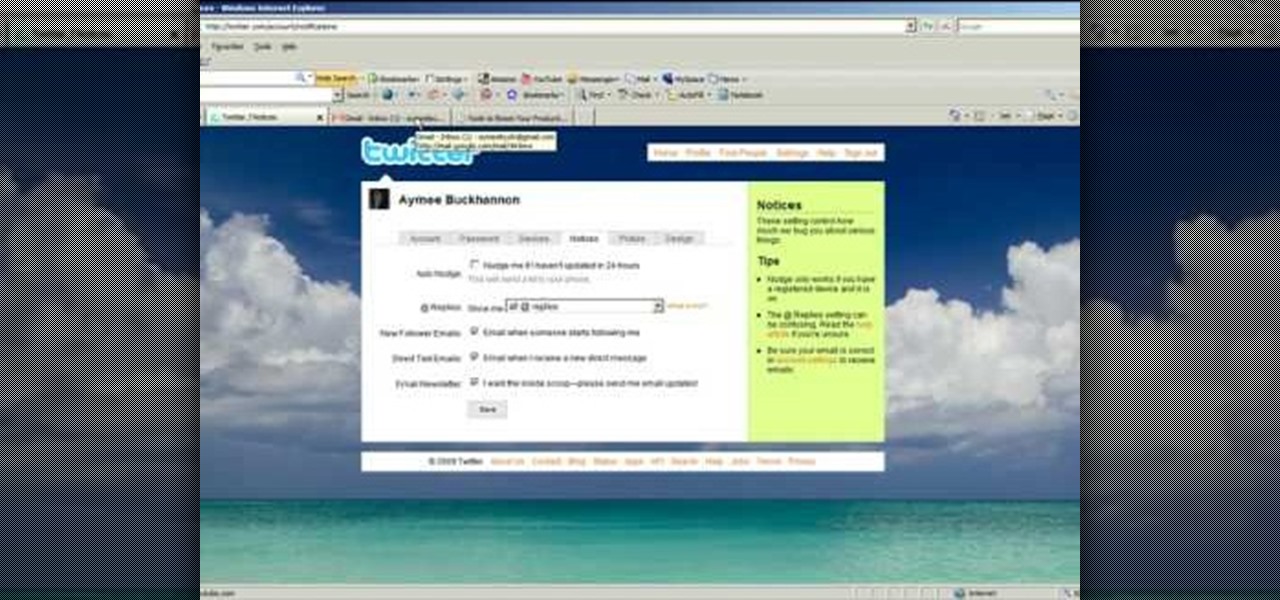
Twitter is the latest popular social networking forum. Twitter is used to keep your friends updated with what you are doing using 140 character messages called tweets. In twitter you can follow your friends and you will be notified when ever your friends posts a new message. Similarly other people can follow you on twitter to know what you are doing. In twitter you can customize to send an automatic private response to your new followers. To do this open your twitter account. Go to the notice...

In this video, it demonstrate how to check and configure Windows firewall. In order to check to see if firewall is enable or not. You would click on start which locate bottom left corner of the screen. Then you would click on control panel. On this screen you would see an option for firewall, and click on it. When you click on firewall, it will let you view all the description about firewall configuration. There are also many other option which locate on the left hand side. If you are an adva...

If you're into arts and crafts then you know that there is more that you can do with a long piece of string than just tie your shoes. On this TyingitAllTogether video you have the opportunity to tie the teacup decorative knot using one long piece of string folded in half. The author of the video first shows you what the end product will look like then methodically begins to walk you through setting up the string in Y-configuration to "crossing each bights crook" which involves overlapping and...

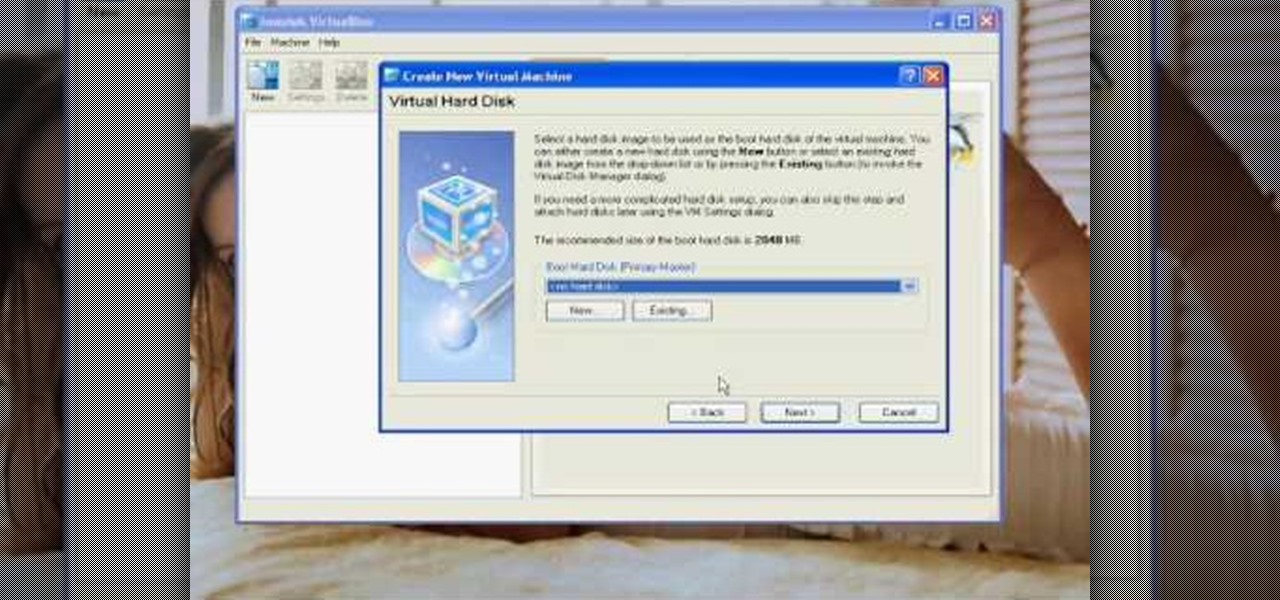
The author shows how to install Puppu Linux 4.3.1 in Innotek VirtualBox 1.5.2. He shows steps to create a new virtual machine in Innotek VirtualBox, by showing the various configuration settings like the RAM size, hard disk space etc. He shows how to boot the virtual machine with the Puppy Linux installation ISO file. Next, during boot up, he shows how to set the language and regional settings, resolution settings etc. In the next screen he shows how to access the local drive and partition it...

Instructional video of Buttonwillow Raceway in a stock RSX type S race car. This is on a clockwise track configuration. This Buttonwillow Raceway video shows you how to handle the turns and race the track well. They describe the pit lane as well as the protocol of leaving the pit. Stay on the left hand side when you enter. There are several 90 degree turns.

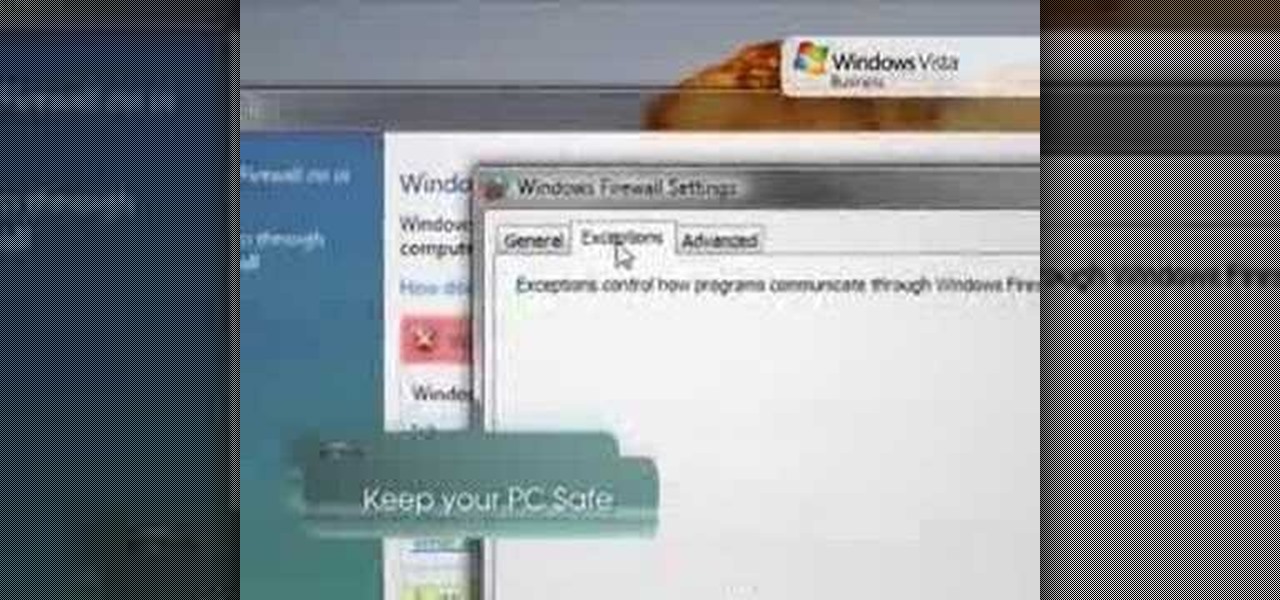
In order to keep your PC safe from annoying or potentially dangerous threats on the Internet, a properly-configured firewall is a crucial item in helping prevent your system from becoming compromised. The Windows Firewall in Windows Vista™ is the first line of defense in helping to keep your computer safe. By preventing your computer from being infected by malware, Windows Firewall is designed to be easy to use and is automatically enabled to protect your computer as soon as Windows starts. T...