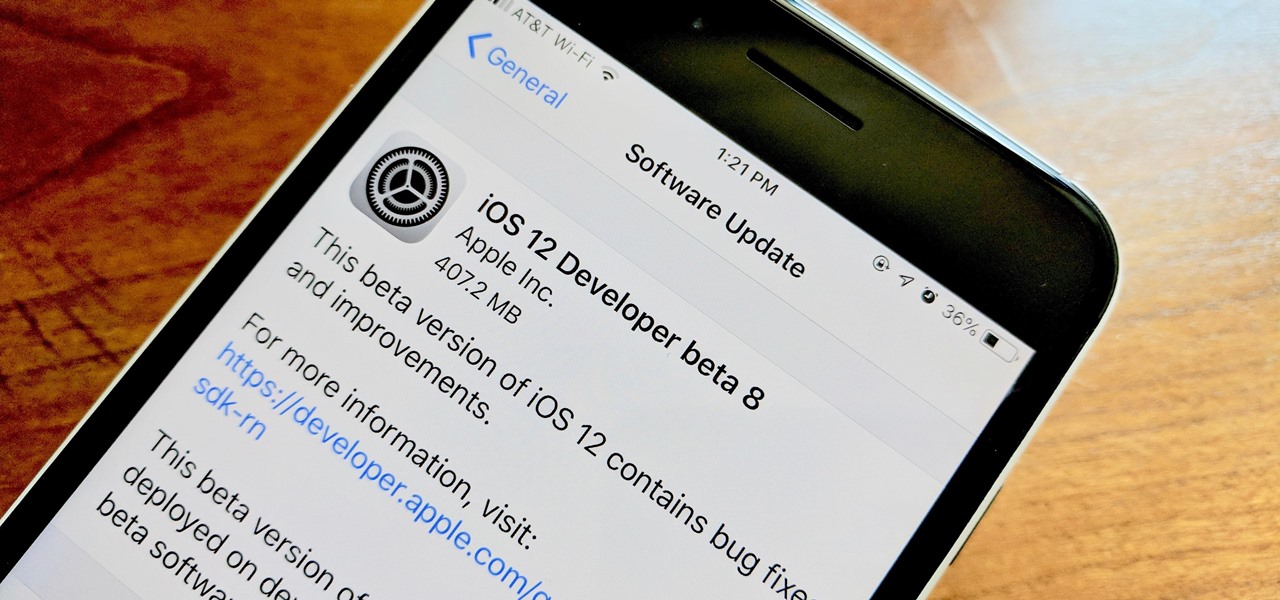
Apple developers, check your iPhones — Apple released the eighth developer beta for iOS 12 on Wednesday, August 15. This update arrives just two days after the release of dev beta 7, which Apple quickly pulled after complaints of unusual performance and stability issues.
With all Android updates, there's a considerable wait before most phones get the new version, and Android Pie is no different. Until then, most of us are stuck just looking at videos of the newest update. Well thanks to developer Trey Dev, we can enjoy the new notification shade and Quick Settings menu while we wait.

Hours after iOS 11.4.1 beta 4 was released on Monday, June 25, Apple's webpage for its public beta software programs was unavailable because of an "update." Sure enough, that meant the public beta for iOS 12 was being prepped to drop shortly thereafter, which is exactly what happened. In other words, you can now install iOS 12 on your iPhone without a developer account!

When it comes to the sub-$250 price range, the new Nokia 5.1 might be the perfect phone. Of all the new models announced at Nokia's event in Moscow, the Nokia 5.1 offers the most with the least compromises. For a third of the cost of a flagship, you get a phone with a premium build, solid specs, and good battery life.
During an event in Moscow earlier this year, Nokia announced a refresh to their Nokia 2, 3, and 5 series phones. While there is no official confirmation of a US release for the updated Nokia 2 and 5, we do know that as of July 2nd, you'll be able to snag a new Nokia 3.1.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

As manufacturers try to differentiate their smartphones from the sea of Android devices, a new genre of smartphone has emerged: gaming phones. Razer Phone was the first to gain traction, but the likes of Xiaomi, Asus, and ZTE have all announced gaming-first phones coming soon. Still, you don't really need to buy a "gaming phone" to play games like a pro on your smartphone.

If you've ever connected your iPhone to a computer before, you know iOS prompts you to "Trust" the computer and enter your passcode to confirm. According to Apple, trusted computers can "sync with your iOS device, create backups, and access your device's photos, videos, contacts, and other content." That's a lot of permissions to hand off, especially if the computer's not your main laptop or desktop.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.

When it comes to technology, there are no bigger names than Google and Apple. They're the two most valuable companies in the world, and they've swapped places a few times over the last year, so they're truly neck-and-neck. But let's put business aside for a moment — which of these companies makes the better flagship phone?

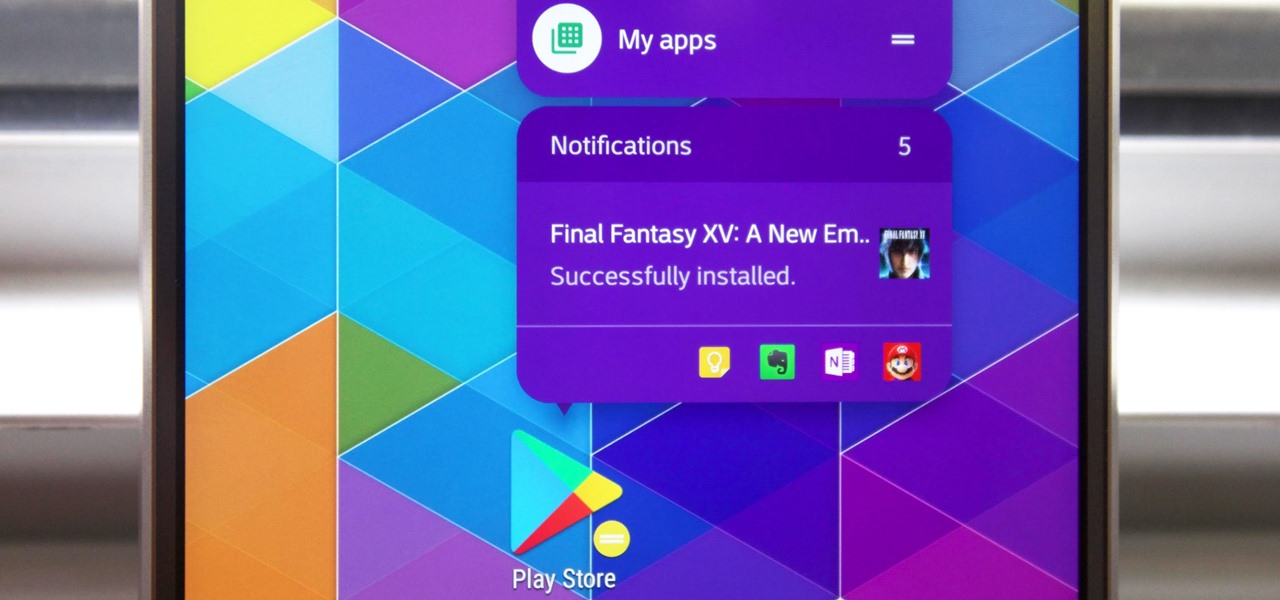
I don't know about you, but I love options. Personally, I think Android's notification system is easy to use — providing access to new notification with a swipe down from the top of the screen. But, as Android users, we like the ability to do things differently whenever we see fit, so what if you wanted a different way? Well, with Action Launcher, this is possible.

While IKEA is collaborating with Apple for its ARKit furniture app, Marxent is ready to help the rest of the interior decorating and home improvement crowd with their apps.

More than one in ten people in the US have type 2 diabetes — that's over 29 million people. It's characterized by excessive sugar (glucose) in the blood due to the development of resistance to insulin, the hormone that normally metabolizes glucose.

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

Mixed reality display manufacturer Realfiction has developed a 64-inch display capable of delivering 3D holograms without a headset.

The Samsung Galaxy S8's almost bezel-less display is truly a sight to behold, especially when set to Immersive Mode. While transparent when on the home screen, the navigation and status bars on the S8 will often turn opaque depending on what app you're using at the moment. This, in turn, can detract from the overall experience when viewing anything from the S8's display, as the bars along the top and bottom of the screen bump the phone's aspect ratio down to lower levels.

As a fan of the HTC One series, I almost always upgrade my phone soon after the new model becomes available. I purchased the M7 when it first came out, upgraded to the M8 shortly after its launch, and then jumped on the M9. However, I stopped right there.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

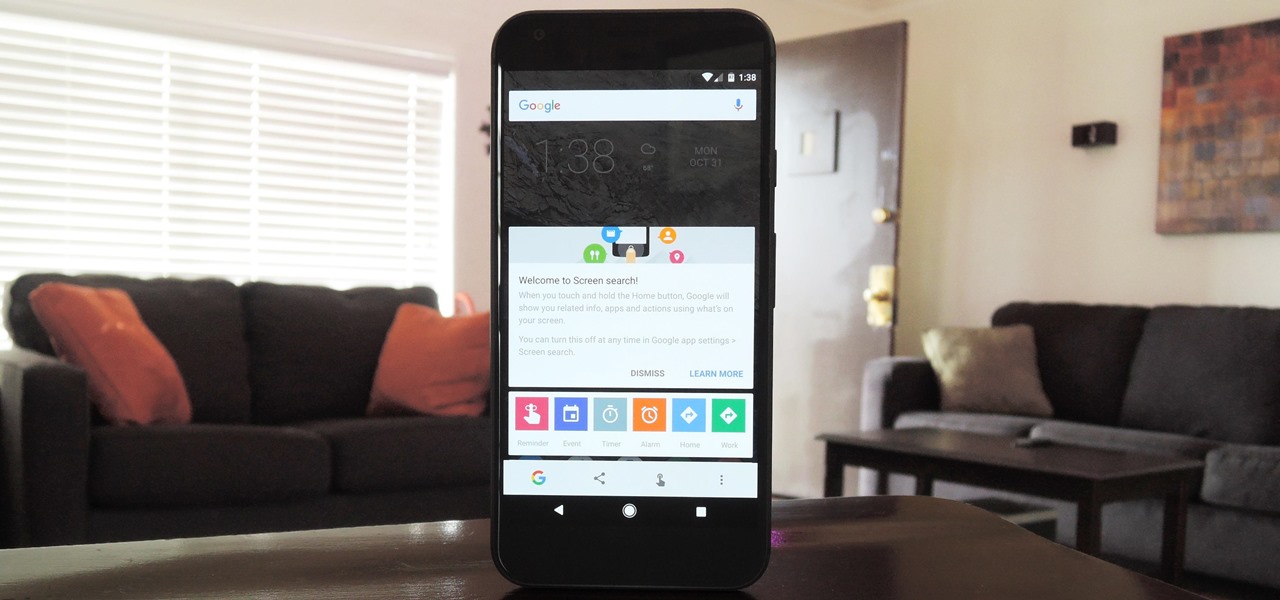
Now that Google Assistant is coming to all devices running Android Marshmallow or higher, roughly one out of every three Android users will no longer be able to access the old Google Now interface. The Assistant, which was previously exclusive to Pixel devices, takes over your home button long-press gesture and completely replaces all of the old Google voice search functionality.

Since I recently had this problem and fixed it, I might as well share the solution. This is actually REALLY simple to fix but will impact your cards' performance.

If you have no desire to get a separate Mac desktop computer, but want to either supersize your laptop's screen for gaming or need to get additional screen real estate while you work, then connecting your MacBook, MacBook Air, or MacBook Pro to an external display is the right call.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Depending on your child's age, their first smartphone may be a little too open for them, or you, to handle. With essentially a world of information—both good and bad—available at their fingertips, it can seem like a huge hurdle to instill parental controls on their device.

Why did I write this when they're tons of scanning tools available.

There are many reasons to root Android, but for me, the most important one is to have the Xposed Framework. Xposed gives you access to hundreds of modules, which take away the need to manually modify core system files to add new features and functionality to your Android device.

I picked up my Galaxy S6 Edge on release day and have loved it ever since. Did I spend an extra hundred bucks for the mostly-aesthetic Edge display? Yup! Did I have buyer's remorse about my frivolous spending? Not even a little.

One of the latest home-improvement gadgets out there today, smart lighting, has become more popular as prices come down. That being said, its still quite a penny to shell out. In this article, I'll go through a few of the top products out there today, including the Philips Hue, Belkin WeMo, and Lifx.

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

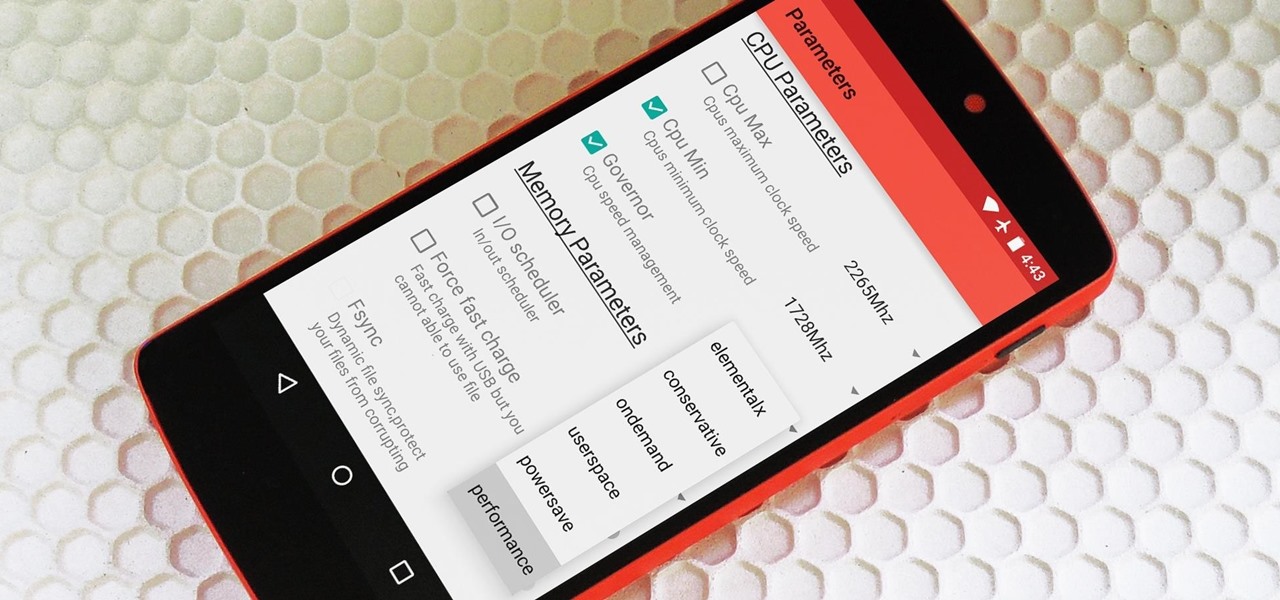
Deep down at the core of Android lies the system kernel, which serves as a bridge between software and hardware. Custom kernels can be installed in place of the stock offering, and these are generally optimized for better performance or increased battery efficiency.

The long-awaited Apple Watch is ready for retail, with pricing and availability announced at Apple's Spring Forward event. Each of the three variants—Apple Watch Sport, Apple Watch, and Apple Watch Edition—will be available in two sizes, 32mm and 44mm, with preorders beginning on April 10th and the retail launch on April 24th. The Watches will initially be available nine countries: Australia, Canada, China, France, Germany, Hong Kong, Japan, the United Kingdom, and the United States. You'll b...

One of the more talked-about features of Google's new flagship device is the fact that all of the data on the Nexus 6 is encrypted by default. At face value, this certainly seems like an added bonus for the 6-inch phablet, especially in this day and age with growing security concerns abound. It's definitely something that the FBI is none too pleased about.

Arcades have long faded away from popularity, but their legacy is being kept alive thanks to emulators and the avid fans who grew up loading quarters into all of those coin-op games. Although nothing beats an actual arcade environment, my favorite emulator from the early 2000s has found a new home on Android, and with it a second life.

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

A rooted Android device means we're on our way to some truly amazing customization options. But there may be a few steps left to completing that journey, and a major one is installing a custom recovery.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

One of the most heated topics in the Android community now (and probably forever) is stock Android, with lots of users requesting the ability to use it rather than the manufacturer's skin.