Chance are, you or someone you know is that person in the gym: flexing in front of a mirror, posing for the perfect photos to show off your workout results. But finding the right picture is hard. The thing is, it doesn't need to be.
Whether gabbing via cloud chat or Secret Chat, there's no denying that private messaging is one of Telegram's strengths. Communications can often occur at night, where Telegram's default bright white theme can be a bit uncomfortable to use, but Telegram supports dark mode on Android and iOS — with a few different themes to match any late-night chatting style.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

What does mainstream augmented reality look like? I'm not talking about the stuff you see in concept videos and science fiction films. No. What does it really look like?

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Since iCloud's introduction in 2011, you get only 5 GB of complimentary cloud storage with your Apple account. With iPhone backups, app data, iCloud Drive files, and even emails (if you have a Mac, Me, or iCloud email address), you'll quickly run out of space to back up photos and videos. Fortunately, Google offers 15 GB of free storage, making it easy to upload your Camera Roll for safekeeping.

You're minding your business when your Apple Watch taps you. To your surprise, the watch claims your heart rate dipped abnormally low. The news might come as a shock — especially if you have no history of a heart condition — but before you panic, you should take the time to fully understand what this alert is really saying and what you can and should do about it.

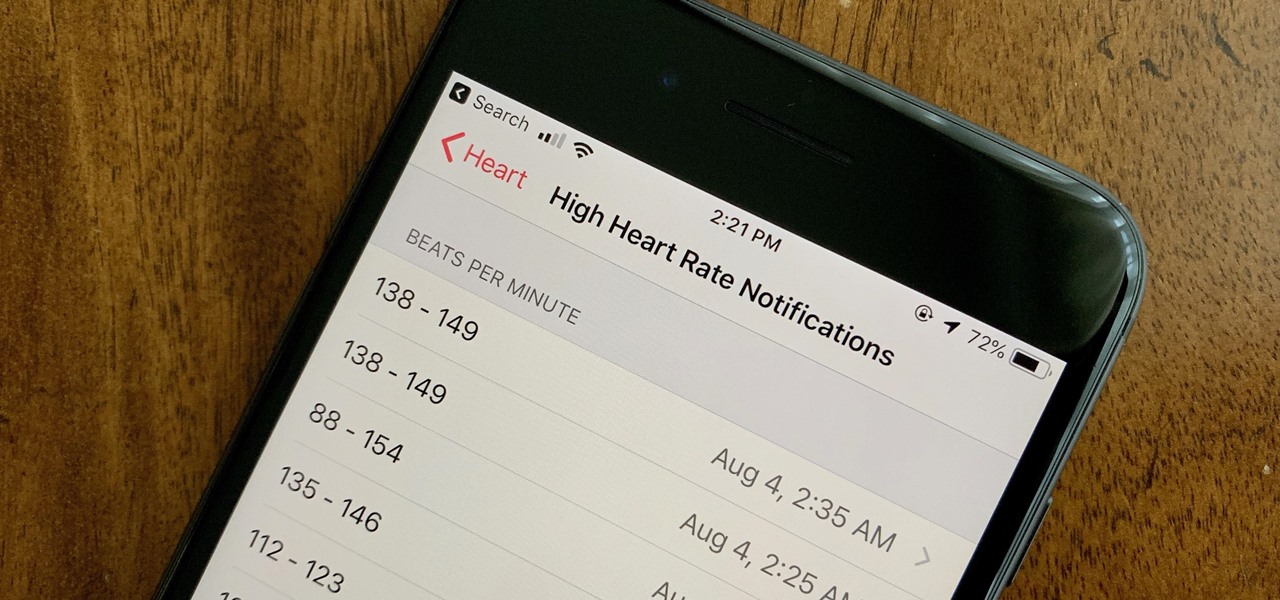
Your Apple Watch sends you notifications from friends, family, and the apps that are important to you. Occasionally, however, the watch may scare the heck out of you with a notification warning of an abnormal, elevated heart rate. If you have no history of heart conditions, this alert might come as a shock. Why do you have a high heart rate, and what are you to do with the information?

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

After the first image leaked of the upcoming successor to the Razer Phone, many were taken aback by its design, specifically how familiar it was. Last year's Razer already stood out with its boxy design and large bezels, and many thought the successor would change this. It didn't. But what if the reason for the familiar form factor is a project they teased earlier in the year?

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

If you want to use your iPhone with another carrier, all you have to do is contact the original carrier to request an unlock, which is usually granted in a few days. Unfortunately, you need to meet specific criteria to officially carrier-unlock your iPhone, like paying off the device in full and completing any contracts. But that doesn't mean there isn't a workaround you can use beforehand.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

During its presentation at Unite Berlin, Magic Leap gave attendees a crash course in developing experiences for Magic Leap One (ML1), we found out quite a bit more about how the device works and what we can expect to experience with the device.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

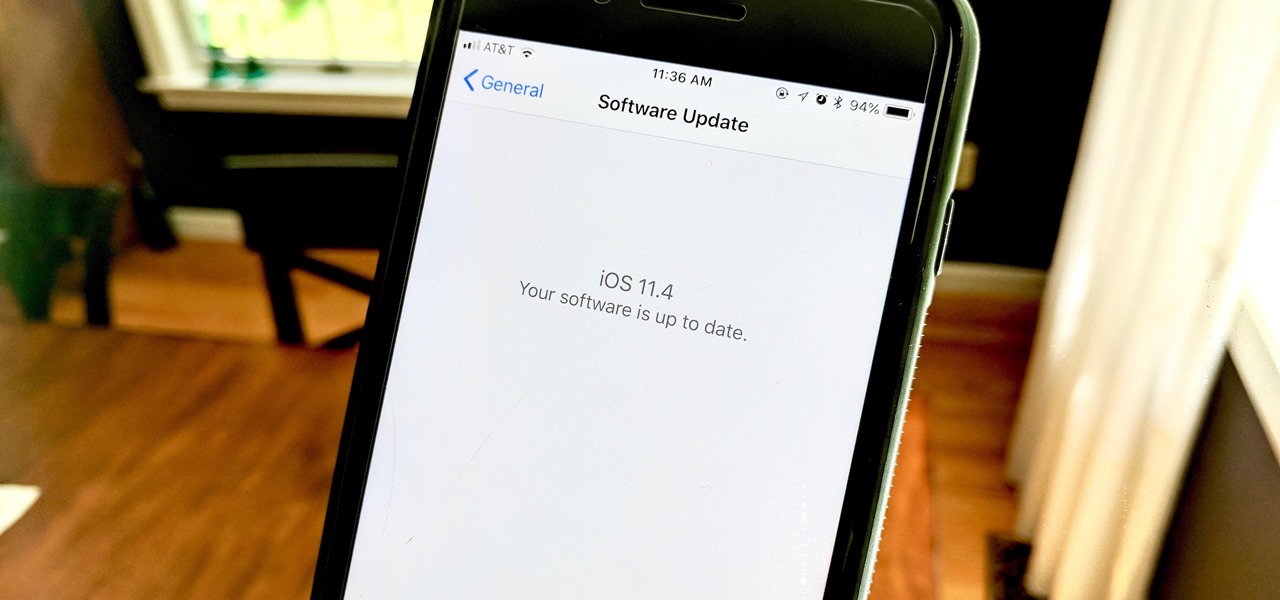
While there are at least five cool things coming in iOS 11.4, they may not be enough to get you to install the iOS 11.4 beta on your iPhone. Since its initial beta release at the start of April, there have been plenty of known issues and user-reported bugs to deal with. While bugs are to be expected with a beta, you may want to read these before installing this one on your iPhone.

| Update: ZTE's issues with the US government have finally been resolved. Check out the details below.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

At this point, we've seen Samsung's vision for Android Oreo on both the Galaxy S8 and Galaxy Note 8. Just last month, Samsung opened its Oreo Beta Program for the S8 to the public. A few days ago, we obtained and detailed a leaked beta build of Oreo for the Note 8. While both of these updates have some compelling new features, there are always tweaks we hoped to see that didn't make the cut.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Apple has something big in store for consumers in 2017 to mark the 10th anniversary of the iPhone. One major surprise is that Apple has decided to forgo on releasing a 7S in favor of a redesigned iPhone 8 and 8 Plus. To further commemorate its 10-year milestone, the Cupertino-based company has released the very exclusive iPhone X, garnering much excitement in the process.

On the airplane, in the middle of cold and flu season, your seatmate is spewing, despite the clutch of tissues in their lap. Your proximity to an infectious person probably leaves you daydreaming (or is it a nightmare?) of pandemics and estimating how likely it is that this seatmate's viral or bacterial effusions will circulate throughout the plane and infect everyone on board.

As the fish farming industry struggles to become more environmentally friendly, it just gained another problem. Fish food loaded with antibiotic-resistant genes.

Blowing dust and fungal spores are creating a public health problem that could be just a slice of what's to come with climate change.

If you have a taste for sweets, you have at least one thing in common with mosquitoes. While too much sugar is unhealthy for humans, a new product makes sweets deadly to mosquitoes.

One of the most popular things to do on Snapchat is to earn a Snapstreak. This occurs when you and one other friend have sent snaps (not chatted) to each other within 24 hours for at least three consecutive days. One you've passed the three-day mark, then you and your friend will receive a fire emoji next to your names.

DownToDash, an app from an NYC-based startup, connects students to other students who want to hang out the same way they do. The social networking app has gained increasing popularity since its launch in October 2016 and looks ready to become even more available. The app was founded by Sama Jashnani and Anuja Shah, both recent students themselves.

By connecting the dots between theory and real-life effect, two new studies offer more proof that neonicotinoid insecticides are causing extensive damage to honeybee colonies.