In the summer of 1976, 4,000 American Legionnaires descended upon the Bellevue-Stratford Hotel in Philadelphia, Pennsylvania, for a four-day convention. Several days later, many of the attendees experienced symptoms of severe pneumonia. By the beginning of August, 22 people had died. The Centers for Disease Control and Prevention (CDC) estimate that about 180 people were sickened and 29 people died before this mysterious outbreak burnt out.

Garlic is a key ingredient in many delicious meals, and if you've been a fan of our site for even a short while, it's no secret that we love to share tricks and tips to make cooking with garlic even easier than you first assumed.

Why, for the love of God, do people keep inventing ridiculous devices that make the simplest things more complicated in the name of convenience? This may be a rhetorical question that will forever go unanswered—because these crazy gadgets just keep rolling out, one after the other.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.
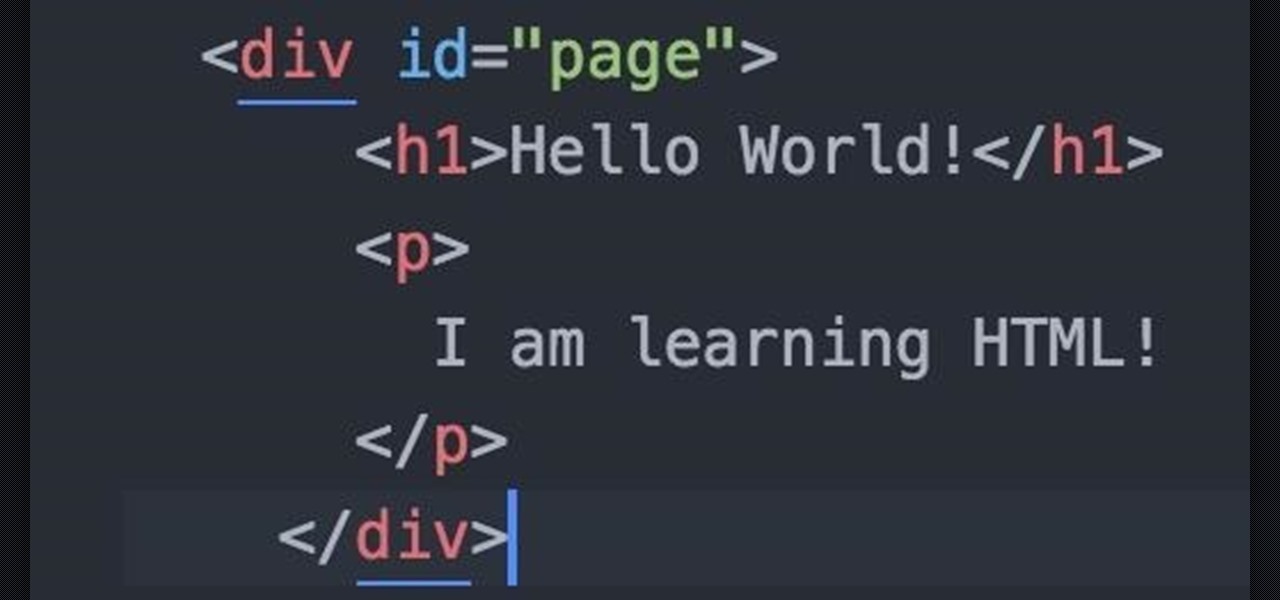
Welcome fellow Null-Byters! Sorry for the delay, this time of the year can be hectic for all of us. Hopefully this will not happen again. In this "tutorial" we will go over more styling and make our page look even better!

A friend of mine is a classically trained chef, and she often invites me over to her house to eat whatever goodies she has concocted. A few years ago I asked her the cliché question that every chef is sick of answering: "What's your favorite food?"

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.

No offense to water, but if I could survive on coffee alone, I would. I swear I'm not addicted... I just really, really, really love the taste of a cuppa joe, whether it's hot, cold, frothed, milked, flavored, plain, whatever! And while my favorite thing to do with coffee will always be to drink it, recently I've become crazy about using coffee in cooking.

If you're a fan of Thai food, I'm sure you're familiar with sticky rice. There is something so special about its chewy texture and sweet flavor. If you have a desire to make it in your own kitchen but don't have the proper tools such as a traditional bamboo basket or stackable steamer, there are several other methods that work just as well. Once you try these alternative methods, I'm sure you'll be "sticking" to them for a while. What Makes Sticky Rice So Sticky?

Recently, there have been some questions regarding networking popping up and we have decided to put together this series to try and cover this gap.

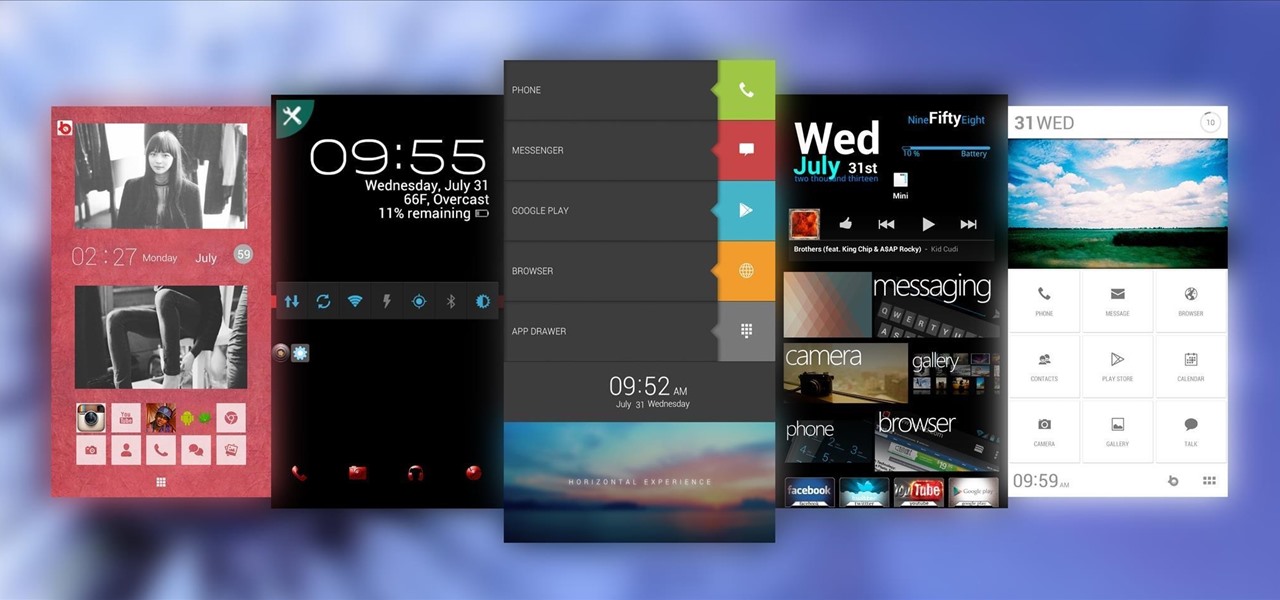
Customizing isn't all rooting and ROMs—there are plenty of ways to customize your Samsung Galaxy Note 2 or other Android device without gaining superuser access. One of the easiest ways is to install an Android launcher, sometimes called a home launcher, that matches your style.

If you haven't heard of Korean pop sensation, PSY, then you really have been living under a rock. Or, you've just never run across any other human. Or, this is your first time on the Internet.

With this article, I'll be continuing the series I started with my recent plague doctor article. That is, examining tropes that may at first appear to not fit into Steampunk.

Religion is one of the most-ignored topics when it comes to Steampunk, which is surprising given how important religion was in Victorian England. Even the hot-button issues of race and gender are confronted with a greater awareness than religion.

One of the greatest consoles ever to exist in the world of gaming is the PlayStation 3, which even lets you do a million different things unrelated to games. But no matter how big of PS3 fan you are, you have to admit that the internal browser is not the greatest. Far from it. While you can access most websites from the PS3, a lot of those site's functions are limited, including Facebook. After reaching over one billion users earlier this month, Facebook is undoubtedly one of the most popular...

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

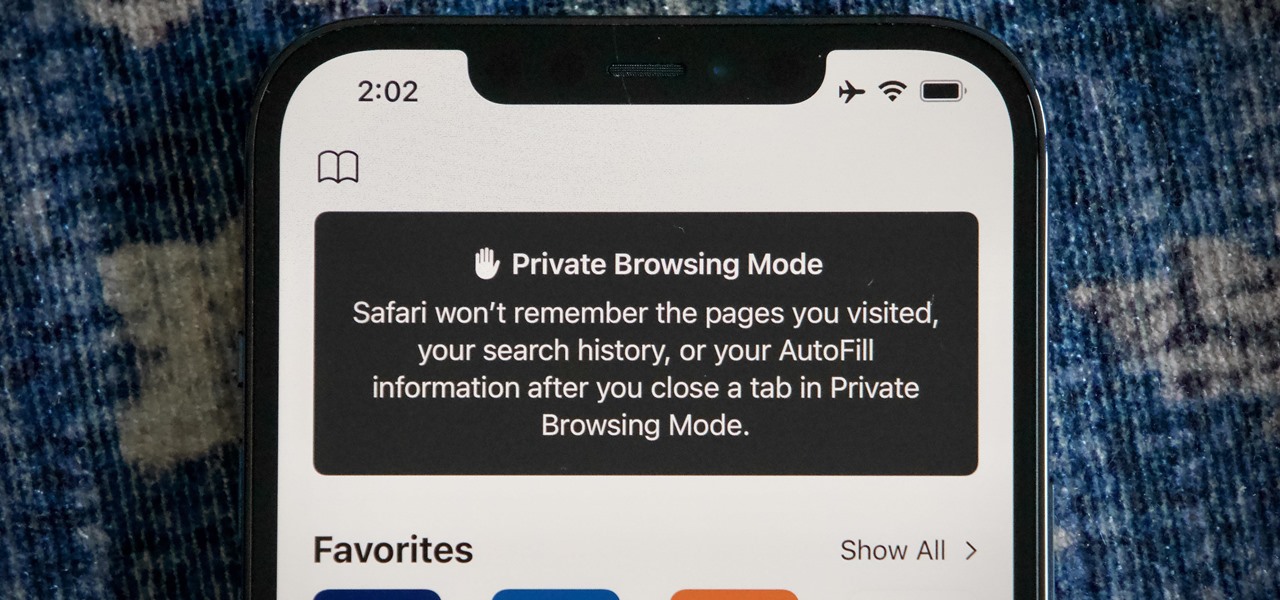
When you open Safari for the first time after updating to iOS 15, you'll instantly notice its search bar is now at the bottom, and its Page Settings menu has moved with it. For tabs, moving between them is as easy as swiping on the Tab Bar or selecting one from the new grid view, but you may get confused whenever it's time to open a private window.

The iPhone 11, 11 Pro, and 11 Pro Max introduced a new rear camera system to the iOS ecosystem. Each model has a new ultra-wide lens in addition to the wide one, and the Pros have a telephoto lens. Both have improved selfie cams too. With so many lenses, it can be challenging to choose which to film with, but why pick when you could shoot with two at once?

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

If you like the "Street View" feature in Google Maps, you'll love "Look Around" in iOS 13's Apple Maps. Overall, Look Around has more details than Street View and the animations are super smooth as you navigate down streets and pedestrian areas. While Look Around isn't available in every city yet, it'll work the same way no matter which iPhone you're using.

The updated Reminders app in iOS 13 makes productivity a little bit more seamless on the iPhone. The overhauled user interface makes it easier to find your reminders, the new Messages integration makes it simpler to remember to-dos regarding your contacts, and the new toolbar provides shortcuts to tasks that were once clunky and confusing.

The world finally received its first official look at the iPhone XR, XS, and XS Max, Apple's 2018 suite of smartphones, on Wednesday, Sept. 12. If you're someone looking to get their hands on one, two, or three of these new iPhones as soon as possible, you'll need to know all of the important dates so you don't end up missing out to others ahead of the line.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Sure, emojis are all the rage, but there's not an emoji for every emotion or feeling just yet. That's where emoticons come into play, emoji's older typographical sibling. Unfortunately, emoticons can be hard to type out, easy to forget, and ASCII art, in general, can be pretty time-consuming to create from scratch — but there's an easy way to forgo all these issues — make keyboard shortcuts.

Every other year, Apple comes out with "S" model iPhones that enhance and speed up their main series models from the previous year. This year, however, because of the highly-anticipated 10th anniversary iPhone, aka the iPhone X, Apple has dropped the "S" and moved straight to the iPhone 8 and 8 Plus.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

It's that time of year when high school students say goodbye the their past four years of coddling, ready to enter the "real world" and the next chapter of their lives—college.

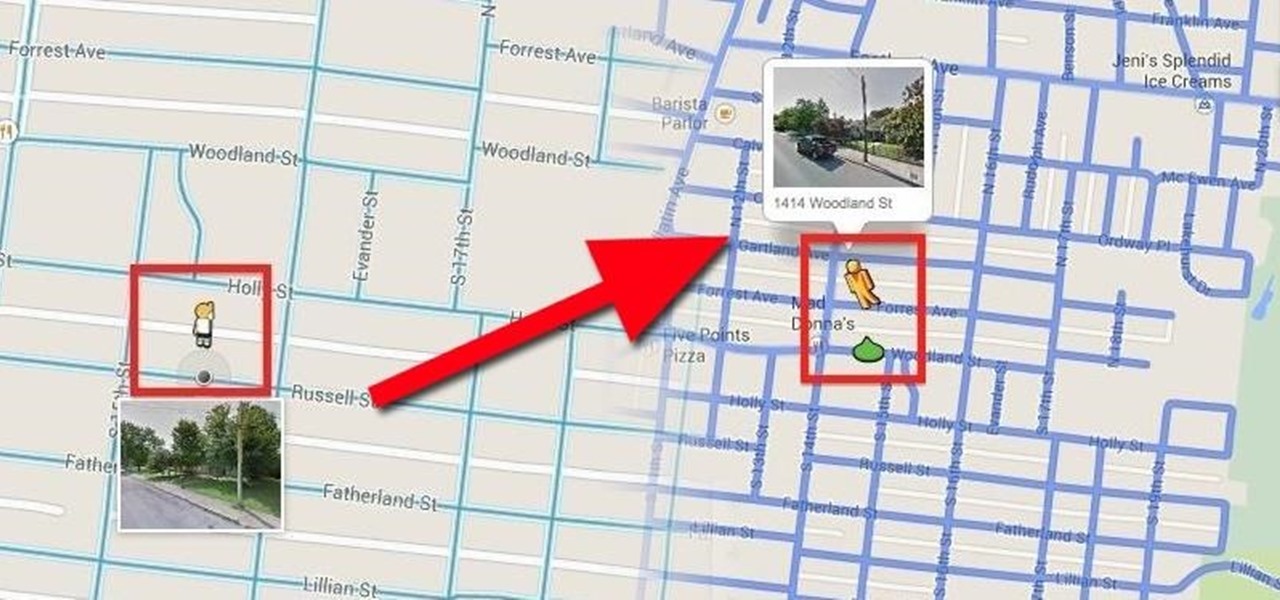
When the Google Maps web app got a massive redesign earlier this year, I was pretty excited to try it out, but it was a fairly disappointing update for me. The slower load times, confusing street view, and bicyclist neglect are just a few of the reasons I don't enjoy it over the old classic Google Maps. The brand new drag-and-drop measuring tool released this week is actually pretty useful, but not enough to change my mind.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

You'd think the ability to block calls from certain numbers would be built in to most phones by now, but that's certainly not the case with the iPhone.

The vast majority of people involved in Steampunk are interested in history but, like with science, there's something about history that we don't talk about very often: The holes.

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

A travelator, also known as a moving walkway or moving sidewalk, seems like a tricky thing to build in Minecraft, especially when it's zigzagging, but there are really simple autowalks out there (like this one).

The most viral internet cat of the moment is a virtual kitty trapped in a billboard in the Shinjuku district of Tokyo, Japan.

When you think about your Apple Watch, what comes to mind? Fitness tracking? Replying to texts? There are a lot of things Apple Watch is good for, but social media doesn't appear to be one of them based on the App Store. If that's your perception, however, it's time for a reality check because you can start browsing Twitter and Reddit on your Apple Watch right now.