Since the release of Windows 8, Microsoft has been heavily encouraging users to use Windows with a Microsoft account. According to Microsoft, the main benefit of using a Microsoft account is the ability to sign in and sync your information across various Microsoft devices and services. Furthermore, you have access to a singular cloud storage solution which can contain documents, pictures, settings, and more on whatever system you're using with the Microsoft account.

It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

Striking up a conversation with a group of people you don't know can be an intimidating task. Come prepared with some interesting comments and ideas and you will be able to make new friends out of any crowd.

ShredBetties shows how to crochet a double crochet stitch in a round. To create the first double crochet in the second round, insert the hook of your needle into the loop at the top of the chain. Yarn over and insert your hook into the hole immediately to your left, below the three strands crossing over the hole. Yarn over and pull the yarn through the hole. You should now have three loops on the hook. Yarn over again and pull the yarn through two of the loops on your hook. You will now have ...

Congratulations, you landed a job interview! This video sequence from watchmojo.com will help you to prepare for a job interview, as well as dress for success and have appropriate conduct.

If you upgrade to an iPhone 12, 12 mini, 12 Pro, or 12 Pro Max, you can take advantage of super-fast 5G speeds, but which 5G network are you actually getting and is it better than the others? Depending on your carrier, you may see 5G, 5G+, 5G UW, or 5G E in the status bar next to the signal strength, and there's a pretty big difference between them.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Your homepage should be the site you most likely need to check whenever you start a new session with Samsung Internet. However, times change — perhaps the site you're currently browsing is just what you need to see multiple times a day. In that case, you'll want to know a quick and easy way to set it as your default homepage.

It's really easy to binge-watch episode after episode, and that's exactly what Netflix wants us to do. Before you can even think twice, the next video is playing and you're stuck wallowing in the abyss of unintentionally marathon-viewing your new favorite TV show, and there's nothing you can do. Except there is something you can do — and it's as simple as disabling one little feature.

The Augmented World Expo or AWE — if you are a big fan of AR/MR technology, that is a very fitting acronym — is the world's largest conferences dedicated to all things augmented, mixed and virtual reality. AWE is in its 8th year, and with the massive growth we have seen in the space over the last year, promises to be its biggest year yet.

I recently posted a Tutorial about setting up Dendroid: http://null-byte.wonderhowto.com/how-to/setup-dendroid-android-rat-0167299/. I have worked the last 5 days on getting the Dendroid Binder, given with the Dendroid Source, working. This solution only works on Windows systems!

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

The Pixel 4 comes with a new "Styles and wallpapers" app that lets you change icons, accent colors, and more. But if you're on a first-gen Pixel, a Pixel 2, or a Pixel 3, you don't get this feature. On the bright side, there's still a way to use it.

You can retweet on Twitter, and you can reblog on Tumblr, but you cannot regram on Instagram. Until now, that is. For years, third-party apps have made it their business to help Instagram users share content from other users. With some new developments, Instagram looks to render those apps obsolete by adding a native regram button to the official Instagram application.

The iPhone X is almost within reach. In fact, you can preorder right now. We know you've been itching to get your hands on Apple's newest iPhone, but before you give up over $1,000 of your hard-earned money, make sure your iPhone X knowledge is up-to-snuff.

James Ashley, Atlanta-based Microsoft MVP and author of Beginning Kinect Programming with Microsoft Kinect, has been running monthly challenges since around the release of the HoloLens Developers Kits. Each month, those of us who follow what happens in the community can look forward to seeing what creative ideas come out of these challenges. It has been a treat, to say the least, and who knows ... maybe one of us here at Next Reality even won one of these before his time here.

It seemed appropriate that we announce the winner of the first White Hat Award for Technical Excellence on the Academy Awards weekend. This is, in essence, our "Oscar" here at Null Byte. Remember, this contest began on January 4th, 2016 and just recently closed on February 15th. In this contest, I was looking for:

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

Yes, "Safer Internet Day" is a real thing, and it's actually been around for 12 years. This year, Google again will be commemorating the event by giving away a 2-gigabyte storage bump for their Google Drive cloud service if you simply run through a security checkup.

Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevolent dictator's computer and temporarily disabled his nuclear launch capability, we have to think about covering our tracks so that he and his minions can't track our good works back to us.

Thanks to everyone who submitted ideas in last month's Mad Science contest. The question called for your best idea for using Sugru, a temporarily malleable silicone modeling clay that self cures for a soft-touch permanent bond. It's a marvelous product for at-home quick fixes and for even making some cool DIY bumpers and grips for your electronics. William scoured through all of the comments and chose the two winners he felt best deserved a pack of Sugru.

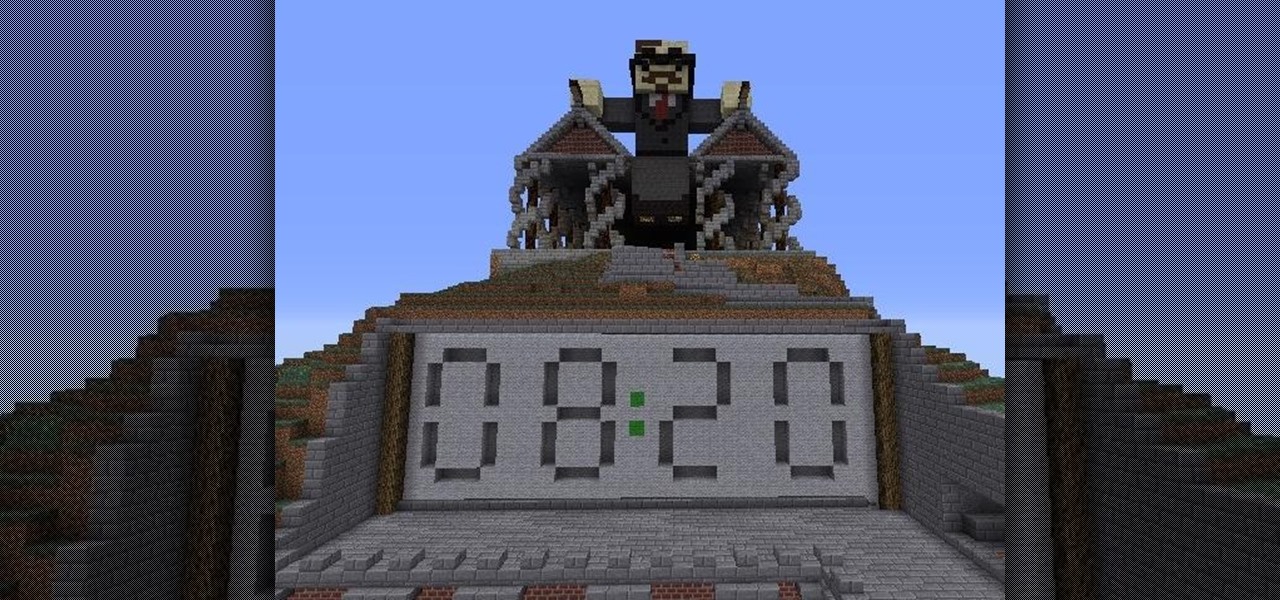
A redstone clock is a pretty easy mechanism to make. A digital readout for that redstone clock is a little harder, and that's what Lesnoydude has made that won him the staff choice award.

With all this time spent stuck at home because of the COVID-19 pandemic, HQ Trivia would be a prime way to beat the boredom. Unfortunately, HQ went belly up in February, just before everyone had stay-at-home orders. While HQ has teased a potential comeback, there are other trivia games out there that are live right now. One of those brings the spirit of HQ Trivia back to our phones.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

When you finally turn the privileged age of 21 in the U.S. (or 18 in most other countries), the first thing you'll probably do is sprint to the nearest pub, order a drink, and revel in your new freedom. Congratulations, you've survived two decades on Earth, you've earned that drink.

Aren't the weekends extra special when they include a bacon, egg, and pancake breakfast? We call it "Lazy Sunday" for a reason. Actually, who needs it to be a weekend? Monday it is!

Google's latest Nexus device is big, bold, and beautiful—and now it's got root. Thanks to some quick work by legendary Android developer Chainfire, the Nexus 6 already had a clear-cut root method before most stores even had it in stock.

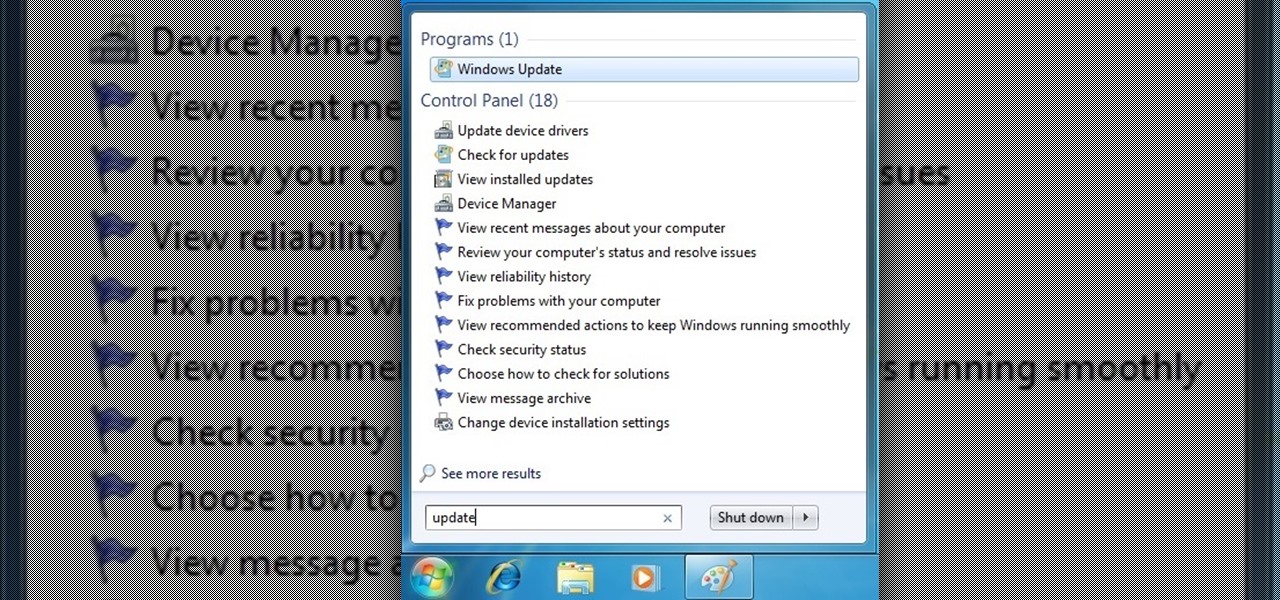
From a fresh home install of Windows 7 (not factory install) this will guide you step by step to updating your Windows 7 and getting it up and running.

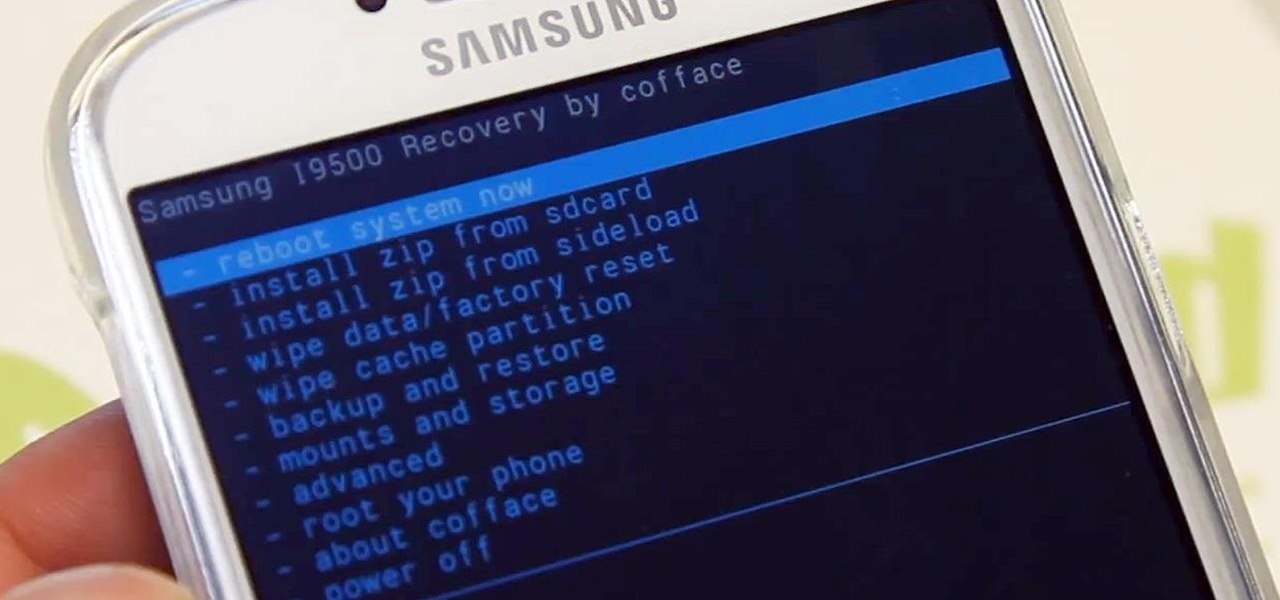
Ready to start rooting your Samsung Galaxy S4? For those of you with the GT-i9500 model GS4, this quick video will walk you through the entire rooting process using Odin and CWM.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

BUD (Block Update Detector) switches can essentially take the place of a regular switch like a lever or a button, but instead of having a "usable" function like pressing the button or flipping the lever, BUD switches trigger when a block next to a piston changes states.

There are a number of different techniques for building underwater in Minecraft. The easiest is to fill a room with wood or leaves, then set them on fire. It'll burn down, leaving a pocket of air for you.

Okay, you can't really become the king of the world by stacking three pistons. For that, you have to stack four pistons.

We've already done a tutorial explaining why buttons are superior to levers, but now I want to show you a way to make them even more useful than they already are. You can't get this sort of functionality with levers!

Congratulations, you've made it deep into the middle of flu season! If you're reading this, you're either a very smart preemptive sick day prepper, or already in the throes of fighting off a cold or flu situation.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

For some of you, whether or not to delete Facebook is a daily struggle. One reason you might not have pulled the trigger on your Facebook account yet could be because of Messenger, which provides millions of people with different devices an easy way to communicate with each other. But here's a secret you might not know: you don't need to have a Facebook account to use Facebook's popular chat app.