Chromecasts can make for some fun nights. Whether you're setting up a collaborative YouTube watch list, letting everyone add to a giant party playlist, or playing games like Cardcast and Big Web Quiz, Google's streaming media stick is a hit by all accounts.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

No matter how much of a gamer you are, typing with your PS4 controller is a bitch. Let's just be real. Having to move left, then right, then down, for every single letter can make writing a message very time consuming; so much so that I usually avoid messaging altogether.

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

To really customize your Samsung Galaxy S3, you'll need to be rooted, because most of the coolest mods and hacks require root access. If you haven't rooted yet, you're just barely touching the surface of what your GS3 can do for you.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Welcome back, my neophyte hackers! As part of my series on Wi-Fi hacking, I want to next look at denial-of-service (DoS) attacks, and DoSing a wireless access point (AP). There are a variety of ways to do this, but in this tutorial we'll be sending repeated deauthentication frames to the AP with aircrack-ng's aireplay. Remember, hacking wireless networks isn't all just cracking Wi-Fi passwords! Our Problem Scenario

Tethering your Android phone basically turns it into a mobile hotspot, allowing you to funnel a 3G or 4G internet connection from your phone into your PC or laptop via USB. As you might expect, phone carriers brought the hammer down in an effort to stop users from getting around the fees they charge to normally allow you to do this.

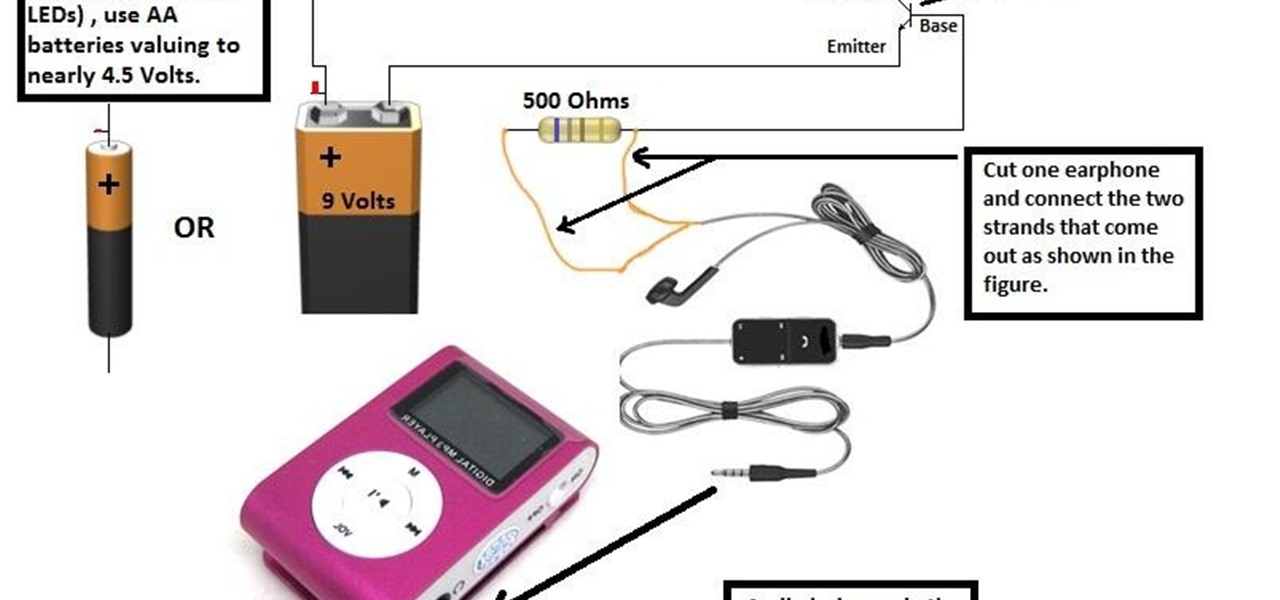
You must have seen some expensive mp3 players and CD players which have LEDs fixed on them and they dance to the tune looking really pretty.

Gary Clark shows you what it takes to hang a beautiful new chandelier in your home, and believe it or not, the installation is simple! No matter what kind of hanging light fixture you're installing in your ceiling, the process is generally the same, where you first need to cut a hole in the drywall and run some wire to the panel. Then make sure you have a junction box that can support the weight of the fixture.

Here's a fun experiment you can do that will demonstrate the effects that pressure has on the freezing point of a liquid. You will amaze your friends as you do what seems to be impossible, turning water into ice without sticking it in the freezer.

Microcontrollers like ESP8266-based boards have built-in Wi-Fi, and that's really cool, but what's even cooler is that certain pro models of the D1 Mini also have a port where you can connect a directional antenna. This can give you exceptional range, but if you were to just plug one in after opening the package, it most likely wouldn't work.

The Nintendo Switch and Switch Lite are console gaming on the go — with zero regards for modern audio features. Headphone jack? Check. Bluetooth connectivity? Not so much. While Nintendo seems to think we're all happy to live like it's 2015, there's a way to use your AirPods with your Switch or Switch Lite for wireless and convenient entertainment.

In the case of Apple Watch v. Fitbit, the winner comes down to the judge at hand. Apple currently offers two smartwatches — the Series 5 and the Series 3 — while Fitbit offers three models — the Fitbit Versa 2, Fitbit Ionic, and Fitbit Versa Lite. Whatever your assumptions about these devices are, throw them out the window, as each has something unique to bring to the table.

For many of us, our work phone and our personal phone are one and the same. Just any old phone isn't going to cut it when you need to meet a deadline — a phone with built-in features that make it easier to get things done is almost a must.

In the last decade, the number of people working remotely in the US has increased dramatically, and so has their need for technology and software to supplement that remote work. Whether you work from home or a coworking office space, the requirement for highly compatible and helpful productivity apps is a must if you want to get things done successfully.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Word games fit perfectly with the on-the-go nature of mobile gaming. They're easy to pick up whenever you feel like exercising your brain, but they're also fairly easy to put down when you need to get back to the real world.

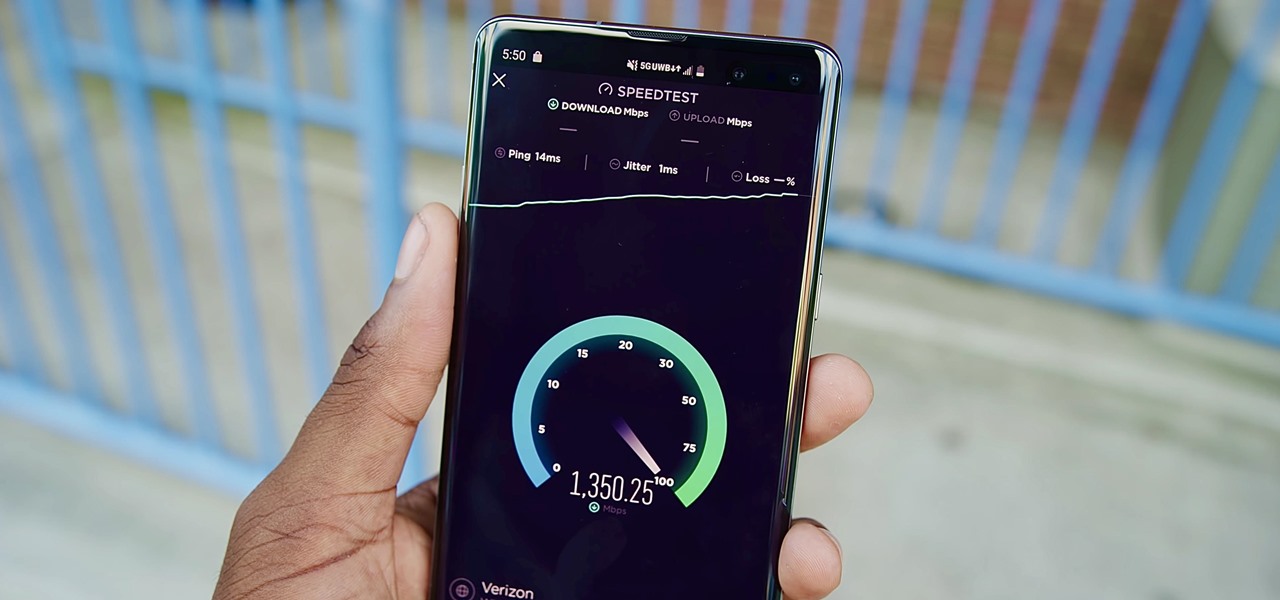
Not all 5G is equal. Even if you dropped the cash on a true 5G phone and you see it's connected to 5G in the status bar, that doesn't mean you're surfing the web, streaming Spotify, and binging Netflix faster than your friends with LTE phones.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

You send out a lot of emails, but probably get very few responses. How can you be sure those emails are even opened?

Facebook will let you do pretty much anything via a text message, but unless you still have a flip phone, it's more of a novelty than actually useful.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

Video: . Recycle your hard drive into a hidden flash memory device that only you know how to turn on and use in secret. This DIY hack project allows you to recycle your broken hard drives back to life and turn them into something useful.

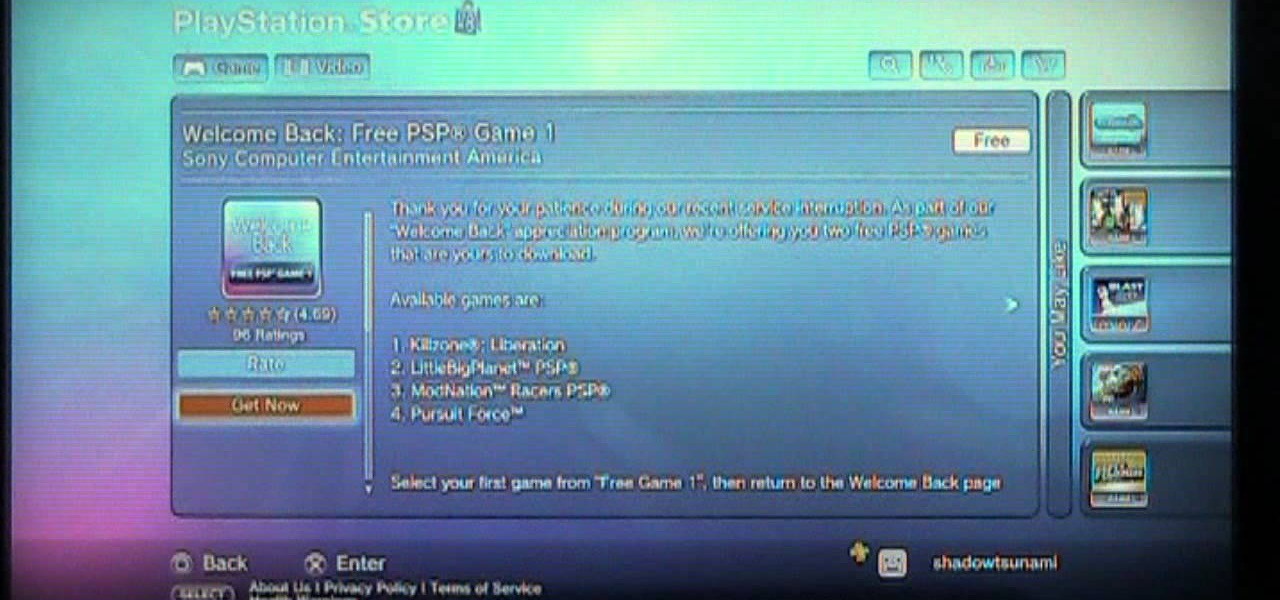
Looking forward to the Welcome Back Package Sony is offering PlayStation network members? Watch this video to learn how to connect to the PlayStation store and retrieve the Welcome Back Package from Sony. PSN members can download two free games!

Trying to get more traffic for your Wordpress blog? Looking to connect with the people who visit you online? This video will show you how to facilitate web interactions by adding social media icons to your blog's header. This video uses the 2010 theme to demonstrate. CSS may be intimidating, but this video will show you exactly what to do.

Having a backup sump pump is integral in making sure your basement is always protected from water, and if you have the Basement Watchdog battery backup sump pump system, this video will show you the complete installation procedure. Find out how to build a pipe connection to the discharge pipe, install check valves, connect to the backup system and more.

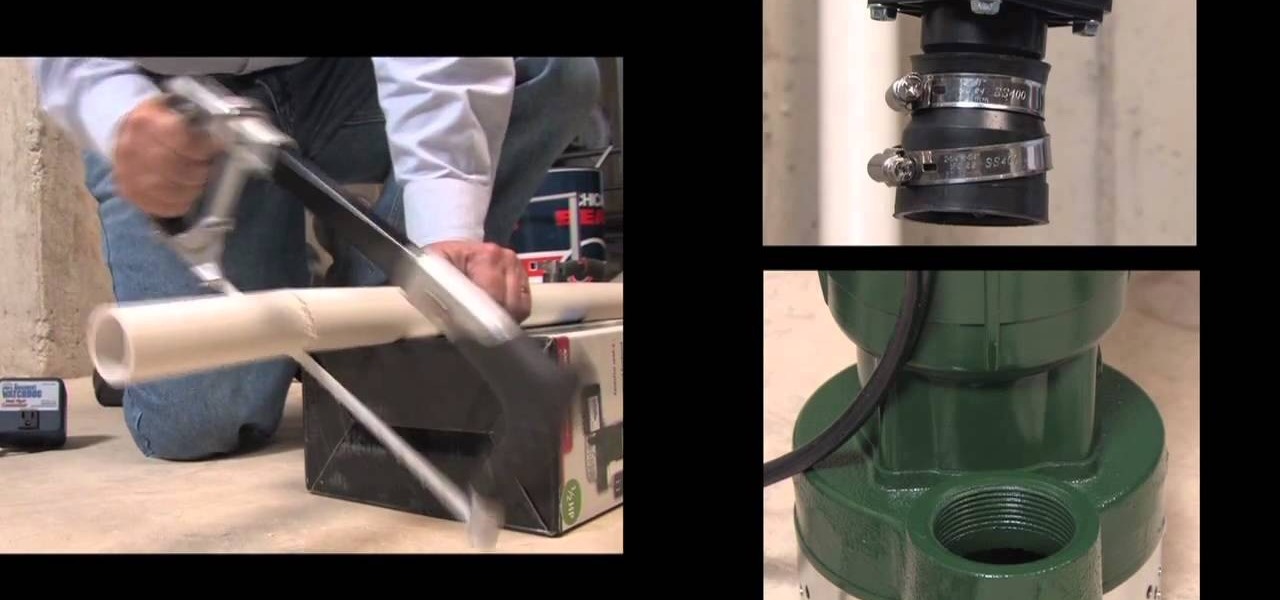
A sump pump is a necessity for most homeowners with basements, and if you've just gotten yourself a Basement Watchdog AC sump pump, this video will show you how to install it. This is a full sump pump, AC-powered, that you can install in your basement, either as a first time sump pump or a replacement sump pump. Find out how to remove the old sump pump, prevent air locks, insert the AC pump and connect it to the discharge pipe correctly.

Learn the art of notation in Pizzicato. Pizzicato has three different levels of music software: Light, Pro and Beginner. And with this video tutorial you can learn about entering notes with a MIDI keyboard. You just have to have a MIDI keyboard and the right hardware to connect it to your computer, then learn about all the shortcuts and tools to get your music on the page quickly.

Meital demonstrates how to do camel undulation for belly dancing. You have to push your chest forward, up, down, and back. Then, you connect the four points. The camel undulation can be combined with other belly dancing moves to create a truly spectacular performance.

In this video podcast you will learn how to use the vanishing point filter in CS3. The filter has gotten even better in Photoshop CS3. Now you can connect non-perpendicular surfaces and wrap an image around multiple surfaces at a time.

This may be an alternative to the traditional sheetbend knot, but it works. Try it out-- it's best used to connect two ends of rope together for a strong hold.

This video demonstrates how to breath correctly when doing Pilates exercises. The video walks you through the proper breathing technique and explains how to connect to your lower abdomen.

There's a hidden feature on iOS that will turn your iPhone or Apple Watch into a remote control for your nearby iPad or other Apple devices — and it's nowhere near as complicated as Switch Control.

True home automation doesn't require interaction from the user. But let's be real, no system is going to be 100% autonomous. You'll always need a manual override for situations programming can't account for. So what's the best manual override system? I'll tell you right now, it doesn't involve yelling at Alexa or Google.