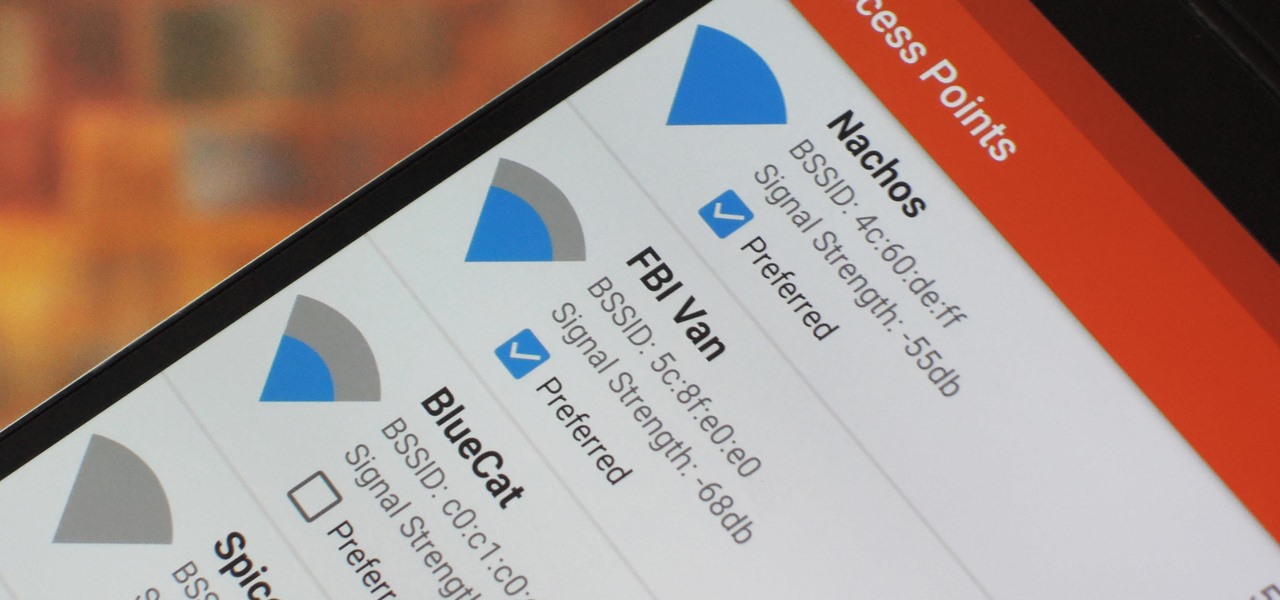
When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

Spotify integration in Bumble has been around for a few years now, allowing prospective matches to view the artists you listen to the most on the popular music streaming service. It definitely helps people connect, but sadly, it doesn't work as well as it should because it rarely updates to show what you're listening to now.

The latest version in Epson's Moverio line of smartglasses looks to offer a headworn window into the world that prioritizes versatility as well as mobility.
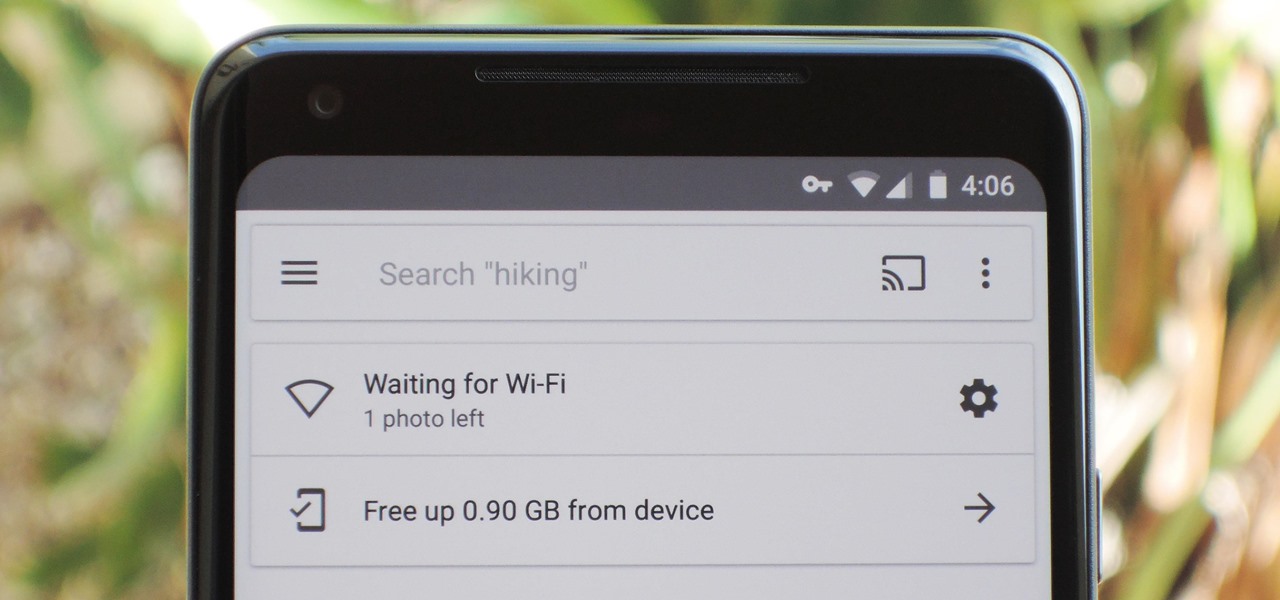
If you're on a limited data plan, you no doubt set Google Photos to only back up over Wi-Fi on your Android device. In recent months, however, there have been many complaints that Photos won't actually back up your pictures when you get back home and connect to your network. Thankfully, the fix is fairly simple.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

Zently — the mobile app for renters — is taking on Venmo with its newest feature. Traditionally used to automate rent payments, deliver rent checks for free, and communicate with your landlord, it now allows you to connect to your bank account and split bills with housemates. Following the addition of Zelle to several major banks apps — to allow users to transfer money to their contacts — the battle of the mobile payment apps is getting increasingly fierce. With this new update, Zently is als...

Wi-Fi signals have limited range, so if you live in a two-story house or work in a larger office, you may have set up multiple routers or repeaters to ensure full wireless coverage. Sadly, Android handles the transition between networks pretty poorly.
Greetings null-bytians. Say you have been able to penetrate your neighbour's AP, and of course you had spoofed your MAC address. Now you go on and test to see with excitement if the password really works and the MAC is still spoofed. You login successfully and you browse the web forgetting to check what your current MAC is. Well, if you may do an ifconfig command, you will see that your permanent MAC is being used. Oh!! and guess what, ... your real MAC has been logged. Even though there is t...

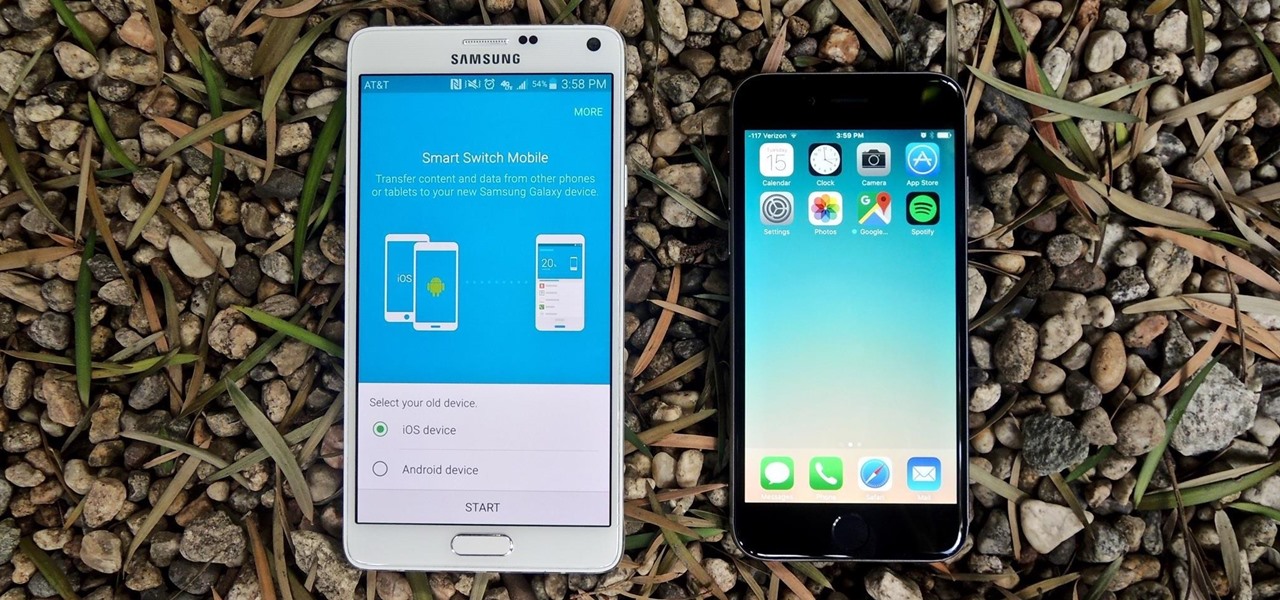
Thanks to Smart Switch, it's easier than ever now to ditch your iPhone for a brand new Samsung device, like the Galaxy S6 Edge+ or Galaxy Note 5.

If beauty is in the eye of the beholder, music lies in the ear. Even within a group of friends who share enough common interests to sit around and socialize over, music tastes can vary dramatically.

AllCast, from renowned developer Koushik Dutta (better known as Koush), allows users to stream personal media, such as movies, photos, and music from mobile devices to Chromecast and other streaming devices.

Investing is like exercise—we all know we should be doing more of it, but we often just can't find the time. I mean, really, who's got the hours, inclination, and skill to pour through volumes of data and put together a balanced yet sophisticated portfolio of investment vehicles tailored specifically to optimize their returns while mitigating potential risks. Not me, that's for sure.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

The majority of our documents and music are digital, which is great for convenience, but it presents a problem for those with a lot of stuff—where do you store it all? There are tons of sites that offer cloud storage, like Dropbox, SkyDrive, and even Flickr, but most of them have limits unless you want to pay, and no way to connect them all.

Every once in a while, Minecrafters want to create a simple hidden piston door to secretly hide all their valuable items. Now, it's possible with only 18 redstone, 2 repeaters, 12 sticky pistons, and ONLY 20 blocks of any kind!

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

It can be very frustrating: You open your Messages app, send an iMessage, and then see that dreaded red exclamation point or horrible green SMS bubble. At this point, you may be curious whether it's just your iPhone or whether iMessage is broken for everyone, but how do you find out?

The PlayStation 4 has been around since 2013 and has brought with it countless game releases since then. One thing that hasn't changed, though, is the strict device restrictions on the PS4 Remote Play feature for streaming your games. The capability has always been there, but you still had to have an iPhone or Sony smartphone to get the best experience possible — until now.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

A new telemedicine application for the Microsoft HoloLens is promising paramedics and EMTs a new tool for diagnosis and treatment of patients in the field.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

One of the major criticisms of virtual reality, and much modern technology in general, is the antisocial nature it creates. But vTime wants to overcome the isolating nature of VR headsets with a virtual hangout space for you and your friends.

A lot more people are about to be able to use Android Auto. Google announced at I/O 2016 that you'll soon be able to use the app with only your phone, so you won't need a compatible car or third-party display unit. And if (or more likely, when) Google brings the app to iOS, Apple may lose the precious "infotainment" system battle very early in the game. The update isn't coming until later this year, but once it arrives, you'll be able to mount your phone and use Android Auto the same way that...

It's hard to believe it's already been a year since I was frantically searching every Best Buy in the Los Angeles metropolitan area to find one with a Chromecast in stock.

Jailbreaking gives you root access to the iOS file system, allowing you to install third-party apps and tweaks on your iPhone that aren't available in the App Store. It opens up a whole new realm for what your device can do, but it can also cause instability across the system and can dissuade you from getting future updates from Apple that have important features, bug fixes, and security enhancements.

Just like some of its popular puzzle predecessors, 2048 is an extremely simple yet insanely addicting game that pits you against a slew of blocks, to be configured into increasing sums with fervid, high-paced moves. If you have yet to play it, check out either the iOS (by Ketchapp) or Android (by Estoty) versions of the game. Due to its overwhelming popularity, dev TalkLittle has ported the puzzle game as 2048 for Chromecast (available for Android only), which lets you play the game solo or b...

Just 94 days after the release of iOS 7, the team over at evasi0n have once again gifted us with their latest jailbreaking software for the newest version of iOS. The first iteration of evasi0n7 contained Chinese malware, but the subsequent release removed the malicious Chinese app store, so this evasi0n7 jailbreak should be just as safe as previous evasi0n jailbreaks were for iOS 6.

Thanks to the popularity of casual gaming on smartphones, handheld gaming consoles like Sony's PlayStation Vita have been on the decline. But if you own a new PlayStation 4, the Vita is a nice thing to have, since you can easily connect it to your PS4 for Remote Play.

Instructions to make 3D origami of airplane similar to Airbus A380. It's self standing, made only with a folded paper (triangles). In video I tried to give instructions for every detail.

Welcome back my fellow hackerians, Today i'm going to tell a bit more about the famous DDOS thing. And on top of that we're going to DDOS a website.

While it's not a highlight of the PlayStation 3, you can actually control the video game console with your smartphone. However, only certain aspects of the PS3 can be controlled from your iPhone, and it's not very obvious what you can and can't do — but that's where we come in.

Since the emergence of GoPro, the company's cameras have been been on a steady incline for the past several years. Adventure enthusiasts had difficulty recording their extreme activities without a huge price tag before the GoPro came along in 2002.

The Samsung Galaxy S III is undoubtedly a great phone, but still has some minor issues to work out.