Are there any benefits to watching a movie in a holographic mixed reality headset, or should you just stick with your TV? It's not as cut and dried as you might think. While TVs have some advantages, so does the virtual screen of a Microsoft HoloLens.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

Out of nowhere, Google released a preview build of the upcoming Android N release back in March—a full two months early. As if that weren't enough excitement for one day, they topped themselves by following up that announcement with the debut of a new "Android Beta" program that allows users with eligible devices receive preview builds as a regular OTA update, meaning no losing data or manual installation.

An accelerometer/gyro goes onto an Arduino board and transmits the angular motion of the skateboard via Bluetooth to a virtual reality game I made for Android phones and Google Cardboard.

Cellular carriers like to nickel-and-dime us out of every bit of money they can feasibly justify, so as consumers, we owe it to ourselves to make sure that we're getting our money's worth.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Android 6.0 Marshmallow added a new permissions system that can make your digital life much more secure. Unlike previous versions, apps now have to ask for your consent before they can access certain data, which puts you firmly in the driver's seat.

Whether you're anxious to tune into this Sunday's Super Bowl 50 to see Cam Newton and the Carolina Panthers take on Peyton Manning and the Denver Broncos, or to see if you win some money on your silly prop bet, or just want to tune in for the commercials, there are a handful of ways to catch the Big Game without an antenna or cable/satellite subscription. When & Where

T-Mobile's "Binge On" service for streaming videos has received mixed reactions so far. On one hand, it gives any T-Mobile subscriber unlimited access to popular streaming video services like Netflix and Hulu without having to worry about going over their monthly data cap. On the other hand, it reduces video quality to 480p, which is 6 times lower than full HD.

In my last post I introduced how to use ncat to connect to your Pi remotely, but what's the point to if you can't actually hack? This tutorial I'm gonna show you how to use very simple tools for a much bigger purpose. With that said, boot up our Pi and lets wreck havoc.

Ready or not, the USB-C cable is about to take over your electronics. The new industry standard is fully reversible and packed with enough power to serve as a laptop charger or an HDMI cable, so it actually has the potential to replace every cord, wire, and connector in your house. In fact, the conversion has already started: The latest MacBook, Chromebook Pixel, and Nexus phones are sporting USB-C connectors out of the box.

I'm back. School's an ass. On my quest for knowledge, which started approximately 3 years ago, I can upon an interesting little artifact. It is called the Arduino.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

Of all the new features in Android 6.0 Marshmallow, an automatic battery-saving function called "Doze" might just be the most interesting. What it all boils down to is that if you set your phone down on a flat surface, the device uses internal sensors to detect that it's motionless and not in use, then responds by drastically scaling back battery-sucking services until the next time you pick your phone up.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

With a slab-style touchscreen device, butt dialing is always going to be a problem. While you're moving about, your phone can unlock itself and give your most recent contact a ring, leading to an awkward one-sided conversation where the other person gets to eavesdrop on everything you're doing or saying at that moment.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

Sadness won over the worried world with her downtrodden, mopey attitude in Inside Out, the widely popular animated film from Pixar and Disney. She's relatable, helping us to connect with all of our bouts of tears, sour attitudes, and blue feelings—and this Halloween, you can embody Sadness with this easy DIY makeup tutorial via Rotoscopers.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

Initially reluctant to port Firefox over to iOS, Mozilla has finally released the first public preview of their famed web browser. While this is great news for all Firefox users, the bad news is that the browser is currently available for download only in New Zealand.

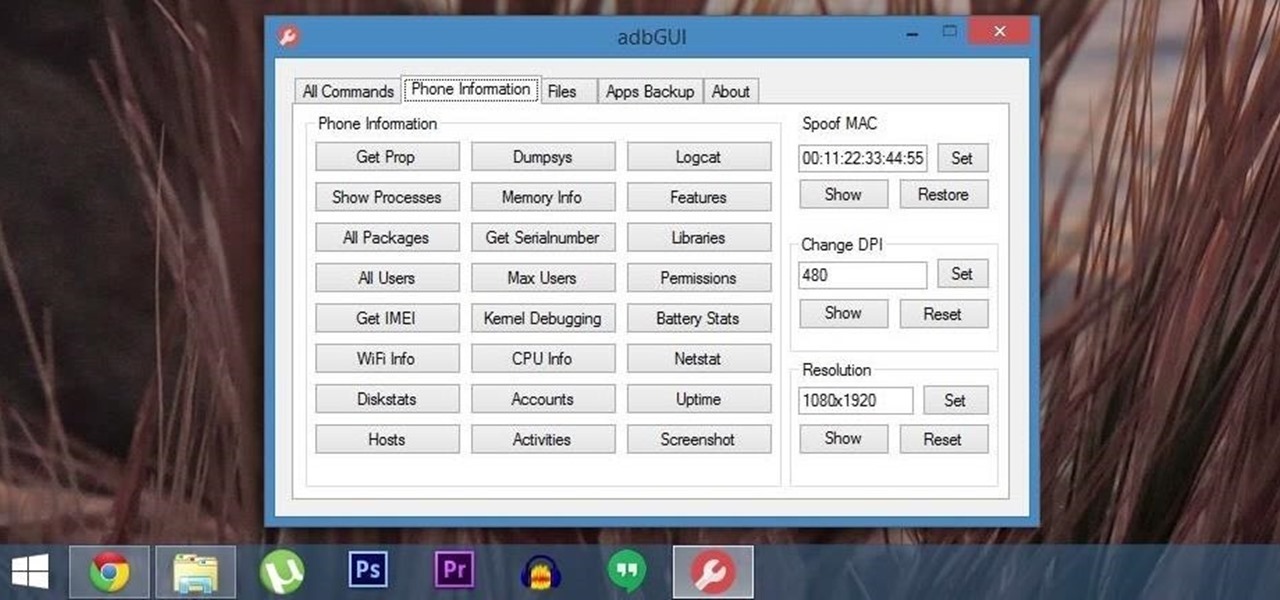
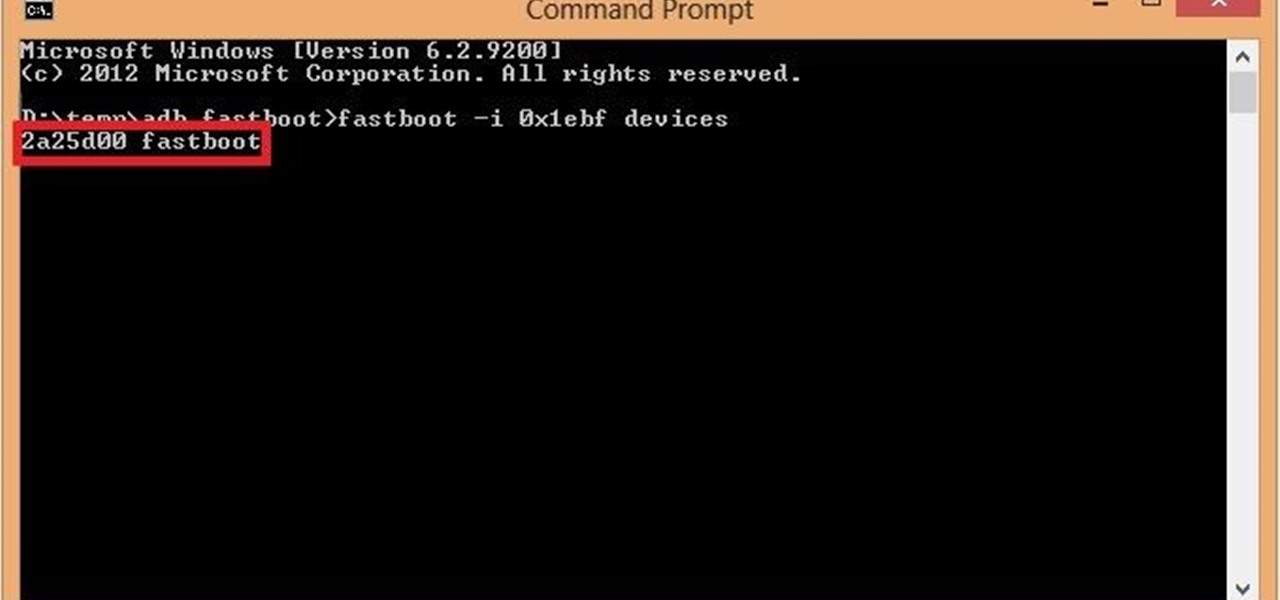
ADB and Fastboot are probably the most essential tools for any Android aficionado. They can do everything from backing up your device to unlocking your bootloader with a few simple steps. This paves the way for many new tweaks and customizations that weren't possible before. The required platform works with the three most popular computer operating systems, too, which is good news for everyone.

Hi guys, I'm gonna keep this short because I got assignments and a lot of notes to study and also other how-tos and forums to reads. lol...Since I'm keeping this short...no story time just scenario. And I want to thank n3stor for giving me the idea to post this.

For all of the flak that Windows 8 received from desktop users, it certainly had some interesting and unique features. For instance, the "Charms" bar allowed you to easily access several key menus by simply hovering your mouse pointer in the top- or bottom-right corner of the screen.

There are many apps and features on your iPhone that you may never use, and therefore don't need. A great illustration of this is the Apple Watch app. You might have no interest in ever getting an expensive smartwatch, yet you're stuck with the Apple Watch app on your home screen.

In the past, updating a rooted Samsung Galaxy device has always involved the complicated process of downloading the proper firmware for your variant, installing device drivers, then sideloading the update with Odin.

If you've updated your iPhone 4S or iPad 2 to a version of iOS 7, iOS 8, or even iOS 9, you've probably noticed that its performance is a little more sluggish than it was back when it had iOS 6 and lower on it.

If you couldn't wait to test drive iOS 9 before its official release this fall, you probably have the beta software on your iPhone right now. However, if you're not a fan of all the bugs and glitches that accompanies it, it's not too late—you can still downgrade back to the latest version of iOS 8.

There are several reasons that you might want to restore the factory firmware on your device—maybe you need to send your phone back for warranty purposes, or perhaps you're getting ready to accept an over-the-air update and need to unroot first. In some cases, reverting to the stock firmware can even resurrect a soft-bricked phone.

bObi has four floor detection sensors on her underside that warn her not to drive over ledges and stop her from falling down stairs.

Android Debug Bridge (or ADB for short) serves as a remote terminal interface for executing shell commands on any Android device. Put simply, ADB lets you send commands from your computer to your phone or tablet, some of which would require root access if they were performed on the Android side of the connection.

If you are among those lucky ones who got a chance to pickup the Yu Yureka from Amazon and looking for a detailed guide on how to root your yureka, then I doubt that there is any better place than this. You might have visited some XDA threads for the same but those are generally brief explanations and you might miss something or the other. Moreover, in most of them, ported Clockworkmod recovery has been used which is less stable and lacks features. So keeping your worries aside, look nowhere ...

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

2015 is quickly shaping up to be the year of the cord cutter, with various media companies finally warming up to the concept of offering live streaming content. In the wake of Dish Network announcing a streaming cable service called Sling TV and Sony unveiling a similar platform in PlayStation Vue, NBC has decided to stream the Super Bowl and all of its festivities online. Before we get to all of the many ways you can stream Super Bowl 49 between the New England Patriots and Seattle Seahawks ...

From parents and other family members to friends and peers, personalities are built by environment. Though people are important in the development of our own individual personality, there are other, different influences, including what you choose to read. The books you take the time to enjoy can make you nicer and more understanding, or leave you overall unchanged.

With its white Apple logo on a plain black background, iOS 8's animated boot screen isn't very interesting. While there is no built-in way to change this boring animation, you can customize this boot screen animation if you have a jailbroken iPhone, and the process is fairly easy. You can even create your own using your favorite GIF file.

One of the few areas where Android lags behind iOS is a comprehensive backup solution for apps. Root tools, such as the popular Titanium Backup, are capable of backing up all of your apps and their data, but not everyone wants to root their device and potentially run into issues with voided warranties.